Ethical Hacking - GAINING ACCESS(7)
Server Side Attacks - NEXPOSE
NeXpose is a vulnerability management framework, it allows us to discover, assess and act on discovered vulnerabilities, it also tells us a lot of info about the discovered vulnerabilities, whether they are exploitable and helps us write a report at the end of the assessment.
Installation Steps:
1. Download it from http://download2.rapid7.com/download/NeXpose-v4/NeXposeSetup-Linux64.bin
2. Stop postgresql > service postgresql stop
3. Change permissions to executable. > chmod +x [installer file name]
4. Run installer > ./[installer file name]
Install Nexpose step by step:



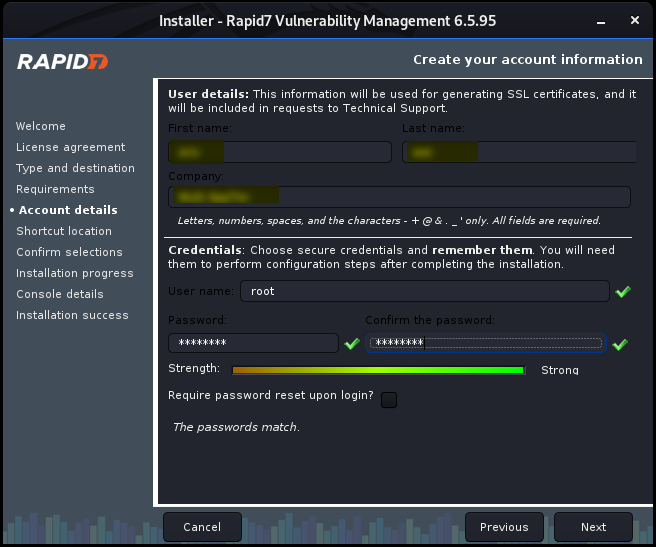
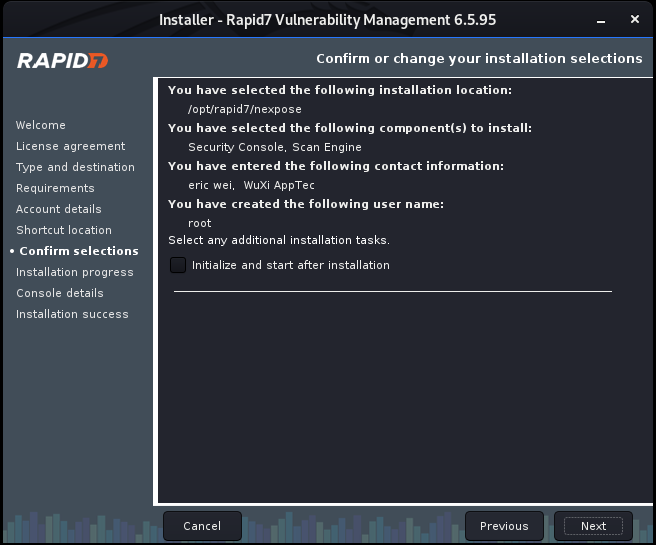
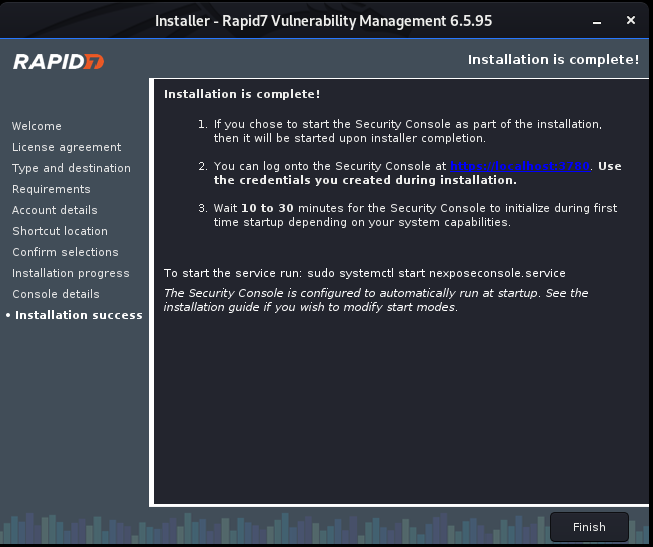
Ethical Hacking - GAINING ACCESS(7)的更多相关文章
- Ethical Hacking - GAINING ACCESS(1)
Gaining Access Introduction Everything is a computer Two main approaches (1)Server Side Do not requi ...
- Ethical Hacking - GAINING ACCESS(23)
CLIENT SIDE ATTACK - BeEF Framework Hooking targets using MITMF Tools: MITMF and BeEF Start BeEF and ...
- Ethical Hacking - GAINING ACCESS(6)
Server Side Attack Analysing scan results and exploiting target system. Go to the Analysis page and ...
- Ethical Hacking - GAINING ACCESS(24)
CLIENT SIDE ATTACKS - Detecting Trojan manually or using a sandbox Analyzing trojans Check the prope ...
- Ethical Hacking - GAINING ACCESS(22)
CLIENT SIDE ATTACKS - BeEf Framework Browser Exploitation Framework allowing us to launch a number o ...
- Ethical Hacking - GAINING ACCESS(21)
CLIENT SIDE ATTACKS - Trojan delivery method - using email spoofing Use gathered info to contract ta ...
- Ethical Hacking - GAINING ACCESS(20)
CLIENT SIDE ATTACKS - Spoofing backdoor extension Change the extension of the trojan from exe to a s ...
- Ethical Hacking - GAINING ACCESS(19)
Client-Side Attacks - Social Engineering Tool: The FAT RAT Just like Veil, it generates Undetectable ...
- Ethical Hacking - GAINING ACCESS(18)
CLIENT SIDE ATTACKS Backdooring ANY file Combine backdoor with any file - Generic solution. Users ar ...
- Ethical Hacking - GAINING ACCESS(17)
CLIENT SIDE ATTACKS - Backdooring exe' s Download an executable file first. VEIL - FRAMEWORK A backd ...
随机推荐
- Java 源码刨析 - HashMap 底层实现原理是什么?JDK8 做了哪些优化?
[基本结构] 在 JDK 1.7 中 HashMap 是以数组加链表的形式组成的: JDK 1.8 之后新增了红黑树的组成结构,当链表大于 8 并且容量大于 64 时,链表结构会转换成红黑树结构,它的 ...
- 008.OpenShift Metric应用
一 METRICS子系统组件 1.1 metric架构介绍 OpenShift metric子系统支持捕获和长期存储OpenShift集群的性能度量,收集节点以及节点中运行的所有容器的指标. metr ...
- 单元测试中使用mock最好不要使用easymock而应该使用powermock
视频参考汪文君powermock视频教程相当的经典
- AbstractQueuedSynchronizer和ReentranLock基本原理
先把我主要学习参考的文章放上来先,这篇文章讲的挺好的,分析比较到位,最好是先看完这篇文章,在接下去看我写的.不然你会一脸懵逼,不过等你看完这篇文章,可能我的文章对你也用途不大了 深入分析Abstrac ...
- 入门大数据---基于Zookeeper搭建Spark高可用集群
一.集群规划 这里搭建一个 3 节点的 Spark 集群,其中三台主机上均部署 Worker 服务.同时为了保证高可用,除了在 hadoop001 上部署主 Master 服务外,还在 hadoop0 ...
- 在linux裸机部署springBoot项目
一.项目创建及打包 创建项目,打jar包 二.安装JDK 1.在/usr目录下床架java文件夹,将 2.下载jdk8,并上传linux服务器(/usr/java) 下载地址:https://www. ...
- Postman之API测试使用全指南
Postman Postman是一个可扩展的API开发和测试协同平台工具,可以快速集成到CI/CD管道中.旨在简化测试和开发中的API工作流. Postman 工具有 Chrome 扩展和独立客户端, ...
- 洛谷 P1025 【数的划分】
进入正题 思路:递归 这道题有点像放苹果: 把M个同样的苹果放在N个同样的盘子里,允许有的盘子空着不放,问共有多少种不同的分发(5,1,1和1,1,5是同一种方法) 转化一下就有: 把n个苹果放在k个 ...
- 什么是EL表达式?
1.什么是EL表达式? EL(Expression Language) 是为了使JSP写起来更加简单.表达式语言的灵感来自于 ECMAScript 和 XPath 表达式语言,它提供了在 JSP 中简 ...
- 解决移动端点击穿透问题_h5实现移动端点击事件穿透的多种解决方案
移动端点透点透现象出现的场景: 当A/B两个层上下z轴重叠,上层的A点击后消失或移开(这一点很重要),并且B元素本身有默认click事件(如a标签)或绑定了click事件.在这种情况下,点击A/B重叠 ...
