PolarD&N2023秋季个人挑战赛—Misc全解
签个到叭
题目信息

压缩包带密码,放到010查看PK头错误,改回去。。


解压后得到
562+5Yiw5Lmf5LiN6IO96L+Z5LmI566A5Y2V5ZGA77yM5b+r5p2l55yL55yL6L+Z5piv5LuA5LmI5Yqg5a+GOglVMkZzZEdWa1gxOHRLZU02bjY4Q3NkRGphWkFZaTlJY1lGMkxNd3FOYzFVPQ==
注意文档里还藏有一段文字,在第一页下方,改下颜色就可以看到

base64解码

AES解码,但需要key,从图片获取,根据提示key为长春某地点名称MD5加密
百度识图可知图片上地点是“净月潭”,MD5加密后为:98f1ecdceaa0f4d6445f48287802dfd9

得到前缀,然后懵了。。。。该干什么呢?回去看了看没修改的压缩包又研究了一下,发现一个可疑之处,我们虽然不能解压但可以点进去看看里面是啥

发现txt里面有
扫二维码关注公众号在公众号回复flag,即可拿到flag好了,可别说了,做过MISC签到的,懂的都懂。。。兄弟们上公众号(当然还有一个图片由于我们没解压不知道图片是啥,但看名字肯定是可以扫的东西)
大胆搜一波PolarCTF回复一下得到
flag{polarD&N666}哈哈还真是,提交就完事。
。。。。。那我之前获得前缀有个毛用。。。这真的是签到吗?
按无脑的来说题都不看,看到压缩包打开后一个扫一扫名字的文件,直接一手公众号岂不快哉。哎!!!纯属大冤种了。。
三段密码
放到010,PK头,然后改后缀解压


flag3.txt
ZmM3ZTNi\MzJiMX0=仔细分析题目可以知道我们需要通过这三条信息分别获取flag的三段最后拼接
首先,第一段
把2.jpg放到010查看,文件尾藏有flag1.txt

kali直接分离,得到一个含有flag1.txt的压缩包,也是带密码的。。。
binwalk -e 2.jpg
伪加密直接修改发现此方法行不通,没办法暴力破解吧。。
破解后可以得到flag1.txt里面内容为
flag{7782bbc5接下来分析第二张图,因为打不开肯定有所损坏,放到010发现是PK头

修改图片后缀名压缩打开
6f03fabe56689b第三部分很奇葩,我们可以想到base64,但中间多了一个\,索性把\删去看看能不能解,不能的话在考虑换表。

可以解,那真是太好了。
最后拼接flag
flag{7782bbc56f03fabe56689bfc7e3b32b1}狗狗重生
题目信息
你消费了吗 要什么密码要密码 5269惯不了你一点
压缩后一个视频,5269像是密码。

我们需要用到ourSecret来解,选择右边部分UNHIDE把视频放进去,密码为5269,解出来一个1.txt文件,然后保存
想了解这个工具的可以百度了解,这里就不说了。

打开文件进行解码
Wm14aFozdHZhMjlyWDJ0dmRXMXZhMjkxYlc5ZllYbGxZWGxsZlE9PQ==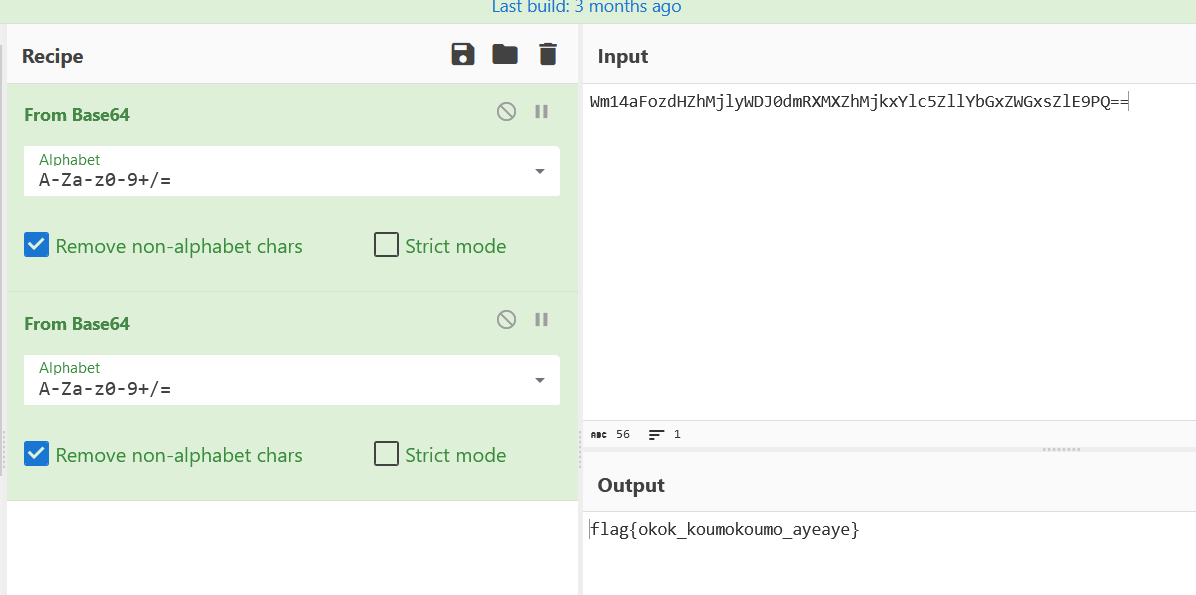
四选其二
题目信息:三个文件
Content_Types.xlsx

另外两个压缩包

我们先可以分析awsd.zip对它进行爆破,时间也是比较长的,长度选择6(这个无所谓可以猜测),选择全部可打印字符进行爆破
最后得到密码为nopass
解压后得到四个文件

看到xml很熟悉,我们可以猜想是Excel表格分成了四份,而且这个猜测正好跟Content_Types.xlsx吻合,虽然不知道有什么用,但可以先看看。
把四个文件全选进行压缩修改后缀名为xlsx


害!跟Content_Types.xlsx一样。。。。。看来是把Content_Types.xlsx拆成了四份来迷惑人
其实直接看Content_Types.xlsx就行,看到表格里有0和1最重要的是有个“起”字,那么可以想到是走迷宫来得到一串01组成的二进制。最后需要对二进制进行转换。
这是一个简单的思路,更何况有想象力的话看到文件awsd这个名字就知道,玩游戏我们离不开这四个移动键啊哈哈哈。看来猜测是正确的,那么如何实现呢?
感觉这应该是最后一步的思路,我们还有一个文件没分析,分析一下,把flag6.3.zip放到010看看

确实没什么可以发现的实质问题,在分析下题目名“四选其二”,意思是四个字节为一组选其第二个,但我们可以看到这样选的话得到的内容没什么意义,再仔细观察压缩包每个字节发现一个有意思的情况,就拿50 4B 03 04 来说,本来是03变成了00也就是把它的第二个位置变成了0,再往后面观察,会发现整体上整个压缩包每个字节的第二位为0或者1的情况很多,那么可以猜想四选其二意味着每四个字节为一组,而且每个字节的第二位都变成0或1,写一个脚本提取变换的0和1,看看会出现什么
脚本
import binascii
with open('flag6.3.zip','rb') as file:
hex_content = binascii.hexlify(file.read()).decode()
grouped_content = [hex_content[i:i+4] for i in range(0 , len(hex_content), 4)]
second_digits = [group[1] for group in grouped_content]
with open('1.txt', 'w') as file:
file.write(''.join(second_digits))得到1.txt
000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001111111111111001100110011111111111111111111111110010011111100001100110001111110011000000111111111111100001111111111111001100110011111111111111111111111110010011111100001100110001111110011000000111111111111100001100000000011001100111111111101100110011110011001111100000000111111001100000001111110000110000000001100001100000000011001100111111111101100110011110011001111100000000111111001100000001111110000110000000001100001100111110011001100111100111100000000000000011001101111000011111111111110000001100110000110011111001100001100111110011001100111100111100000000000000011001101111000011111111111110000001100110000110011111001100001100111110011001100110000110000000000011001100110010011001111000011000011100110011001100110011111001100001100111110011001100110000110000000000011001100110010011001111000011000011100110011001100110011111001100001100111110011000000110000000010011000011001111111111111111111111100110001111111111000000110011111001100001100000000011001111111111111111111000011110000110000011000000111111001110011001111000000110000000001100001100000000011001111111111111111111000011110000110000011000000111111001110011001111000000110000000001100001111111111111001100110011001101100110011001100110010011001100110011001101100110011001100111111111111100001111111111111001100110011001101100110011001100110010011001100110011001101100110011001100111111111111100000000000000000000011001111110011111110000000000110000011000011110011001110000000000000000000000000000000000000000000000000011001111110011111110000000000110000011000011110011001110000000000000000000000000000000001111000011111000011000011111110011001111000011111111111001100111111111100011000011110000001101111111100001111000011111000011000011111110011001111000011111111111001100111111111100011000011110000001101111111100001111000001100001100111100001100000110000000011110010011111100001100110001111111111001111001100011111100001111000001100001100111100001100000110000000011110010011111100001100110001111111111001111001100011111100001100111100011000011111100000001111000011111100110000011111100000000110011111110011111111001101111001100001100111100011000011111100000001111000011111100110000011111100000000110011111110011111111001101111001100000011110011100110000000011111111100111111001100001100000000000111111001100000001100110000110011100000000000011110011100110000000011111111100111111001100001100000000000111111001100000001100110000110011100000000000011001100011001111110011001111111111100110000111100000001100111111111101111001100110011111110000000000000011001100011001111110011001111111111100110000111100000001100111111111101111001100110011111110000000000001100000010000111111000000110010011000011001111110010011111100001100110001100001111001111000011111111100001100000010000111111000000110010011000011001111110010011111100001100110001100001111001111000011111111100000000001100011110000001100111111111001100000000110000011111111001100000001100110011110000000001111001100000000001100011110000001100111111111001100000000110000011111111001100000001100110011110000000001111001100001100111111100000011110011001101100000000110000001100000000011111111001110000000000000000110011100111100001111110011111001111001111000000000110011111111001101100001100111111111100011001100000000001110000110000001111110011111001111001111000000000110011111111001101100001100111111111100011001100000000001110000110000001100001111100111100000011111111111111111000011110011111111100001100110001111111111001111001100011111100001100001111100111100000011111111111111111000011110011111111100001100110001111111111001111001100011111100001111110011111000011000000000010011001100111111110000011001100000000000001100110011111100000001111001100001111110011111000011000000000010011001100111111110000011001100000000000001100110011111100000001111001100001111000010000110011110011110000000110000001100001100000000011110011001100011000000000011111111100000000001111000010000110011110011110000000110000001100001100000000011110011001100011000000000011111111100000000001111000010011110000001100001101111111100110000110000000001100110000111101111001100110011111110000110000001111000010011110000001100001101111111100110000110000000001100110000111101111001100110011111110000110000000000000000000111111001100110010011000011001111111111111111100001100110001100001111001111000010011001100000000000000000111111001100110010011000011001111111111111111100001100110001100001111001111000010011001100001111111100011111111110000000011100111111111100111100011001111001100000001100111111111100000001111001100001111111100011111111110000000011100111111111100111100011001111001100000001100111111111100000001111001100000000001110000000000000011110001111110000001100001100000000011110011001100000001100000011110011100111100000000001110000000000000011110001111110000001100001100000000011110011001100000001100000011110011100111100000011000011111111100111111111110011001111000011111111111110000111111111101111001100001111111110000110000000011000011111111100111111111110011001111000011111111111110000111111111101111001100001111111110000110000000000001110000001100110000001100000110000110011110000011111100001100001101100001111001100000010011111100000000001110000001100110000001100000110000110011110000011111100001100001101100001111001100000010011111100001100000010011001111000011000001111000011111100110010011111111001100000001100111111111100110011111001100000011111110000001100110000110011100111111001111110000011000011110011001100011001100001100000011100111100000011111110000001100110000110011100111111001111110000011000011110011001100011001100001100000011100111100001111111111111111111110011001101111110000110000111111111110000110000111101111001111111111111110000110000001111111111111111111110011001101111110000110000111111111110000110000111101111001111111111111110000110000001100110011100000011000000110010011000011111111000001100111111111100111101111111111110011111110011001100001100110011100000011000000110010011000011111111000001100111111111100111101111111111110011111110011001100001100110001111000011001100111111111001111000011111100000001111000000110011100110011001100110011111001100001100110001111000011001100111111111001111000011111100000001111000000110011100110011001100110011111001100000000001101100001100001111001101100001100110011001110011000011110011111100011000000111100000001100111100000000001101100001100001111001101100001100110011001110011000011110011111100011000000111100000001100111100000011000011111000000111100000000000110011111100000011111001100110000111101111000011110000000000000110000000011000011111000000111100000000000110011111100000011111001100110000111101111000011110000000000000110000001111000011100111111000000111111111111111000011000000000111111111100110001111111111001111111110011001100001111000011100111111000000111111111111111000011000000000111111111100110001111111111001111111110011001100001100110011111111100000000000010011001100001111110000000001111000000000001100110011000000111101111001100001100110011111111100000000000010011001100001111110000000001111000000000001100110011000000111101111001100000000001100000110000110011110000000110000000011001110011110000111111111110000000000111111000001100000000000000001100000110000110011110000000110000000011001110011110000111111111110000000000111111000001100000000000000000001111111111111111001101111110000110000110011111110000111111111100011001100111100001100000110000000000000001111111111111111001101111110000110000110011111110000111111111100011001100111100001100000110000001111110011100111111000000000010000000011001111000001100111111111100111101100001111110011111111111001100000011001111111001111110000000000000111100111111111100000111111000000110011100110011001100110011111001100000011001111111001111110000000000000111100111111111100000111111000000110011100110011001100110011111001100000000110011100110000000000110011111110000001111001110011000000110011001100000001100111100000001100000000000000110011100110000000000110011111110000001111001110011000000110011001100000001100111100000001100000000001111001110011000000000011111110011001111000000110011100110000111111111101111001100110000000001100110000001111001110011000000000011111110011001111000000110011100110000111111111101111001100110000000001100110000001100110001100110000000011001100000110000110011001100000111100001100110001111111111001111001110011111100001100110001100110000000011001100000110000110011001100000111100001100110001111111111001111001110011111100001111001111111111111000011110001100000011111111110000000001111000000110011111111111000000111101111001100001111001111111111111000011110001100000011111111110000000001111000000110011111111111000000111101111001100000011110000000000011001100000011111001111001111001110011110000110011111110011001100111111000001100111100000011110000000000011001100000011111001111001111001110011110000110011111110011001100111111000001100111100000000001100011000011000000110011111111100110000111111111111100111111111100011001100111111111110000001100000000001100011000011000000110011111111100110000111111111111100111111111100011001100111111111110000001100000000000000000001100110000001110011000011001100110000011111100001100111101111111111111100000010011111100000000000000000001100110000001110011000011001100110000011111100001100111101111111111111100000010011111100001111111111111000000001100001100011001111000000110010011111111001100110011100110011001100110010000001100001111111111111000000001100001100011001111000000110010011111111001100110011100110011001100110010000001100001100000000011001100110011000011100001100110000110000011000011111111001110000000000111100000011100000000001100000000011001100110011000011100001100110000110000011000011111111001110000000000111100000011100000000001100111110011001100110000111100000110011111100111111111110000111111111100011000011111111111110000000000001100111110011000000111100001111111111111000011000011111111100001100110001100001111000000001101111000000001100111110011000000111100001111111111111000011000011111111100001100110001100001111000000001101111000000001100111110011000000110000000010011001100111111001110011001100000000000011100111111110000000001111000000001100111110011000000110000000010011001100111111001110011001100000000000011100111111110000000001111000000001100000000011001111110000000000000110000001111110001100110011111111111110000001100110000110011100111100001100000000011001111110000000000000110000001111110001100110011111111111110000001100110000110011100111100001111111111111001111000011000011111110000110011110011100111100111100111100011001100111100110011100110000001111111111111001111000011000011111110000110011110011100111100111100111100011001100111100110011100110000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
好好好!!又是我们熟悉的二维码来了,上脚本
from PIL import Image
with open('1.txt', 'r') as file:
content = file.read()
width = int(len(content) ** 0.5)
height = (len(content) + width - 1) // width
image = Image.new('1', (width, height), color=255)
pixels = image.load()
for i in range(len(content)):
x = i % width
y = i // width
if content[i] == '1':
pixels[x, y] = 0
image.save('222222.png')得到二维码

扫码得到
wdwsswwsdswwwsdsssdddswdwsdsddswdwsswwaaawwswdwsswswdwsswdwsswddwdwwwwwwdddwwaaawwwwaaawaawawsaaassssdsssdddsssaaaswdddwwwwwsddddwssaasssaaswawsswdwddwwaaawwwaaawwsasddswawddwwdwddwsaaasssddasssaaddsw不难想到这串就是走迷宫的顺序,正好吻合我们一开始的猜想,下面就按这个顺序来走迷宫吧,可以得到0和1组成的二进制,估计解码就是flag。。
我们先把上面扫码的结果转化成文字这样好查
上右上下下上上下右下上上上下右下下下右右右下上右上下右下右右下上右上下下上上左左左上上下上右上下下上下上右上下下上右上下下上右右上右上上上上上上右右右上上左左左上上上上左左左上左左上左上下左左左下下下下右下下下右右右下下下左左左下上右右右上上上上上下右右右右上下下左左下下下左左下上左上下下上右上右右上上左左左上上上左左左上上下左下右右下上左上右右上上右上右右上下左左左下下下右右左下下下左左右右下上然后走迷宫得到二进制
0010 0100 01 110 1111011 11000 0010 01111 0 0010 0 0010 0010 00011 01 01111 00001 01111 00011 11110 100 10000 10000 00001 01 11111 1000 1000 0010 00111 00001 00001 11000 00111 00111 11110 11110 1111101看这种形式尝试二进制解码是不行的,因此想到可能是摩斯电码
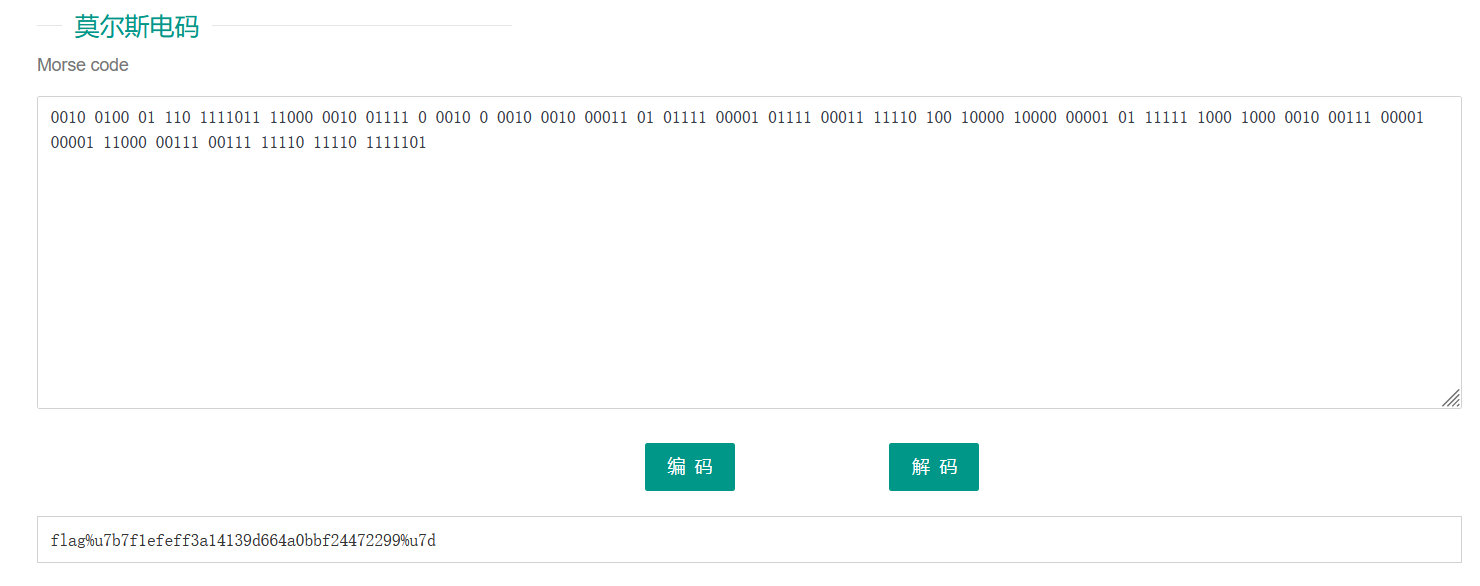
最后得到flag
flag{7f1efeff3a14139d664a0bbf24472299}data藏起来了
题目信息
得到的flag的内容进行MD532位小写加密后套上flag{}即可

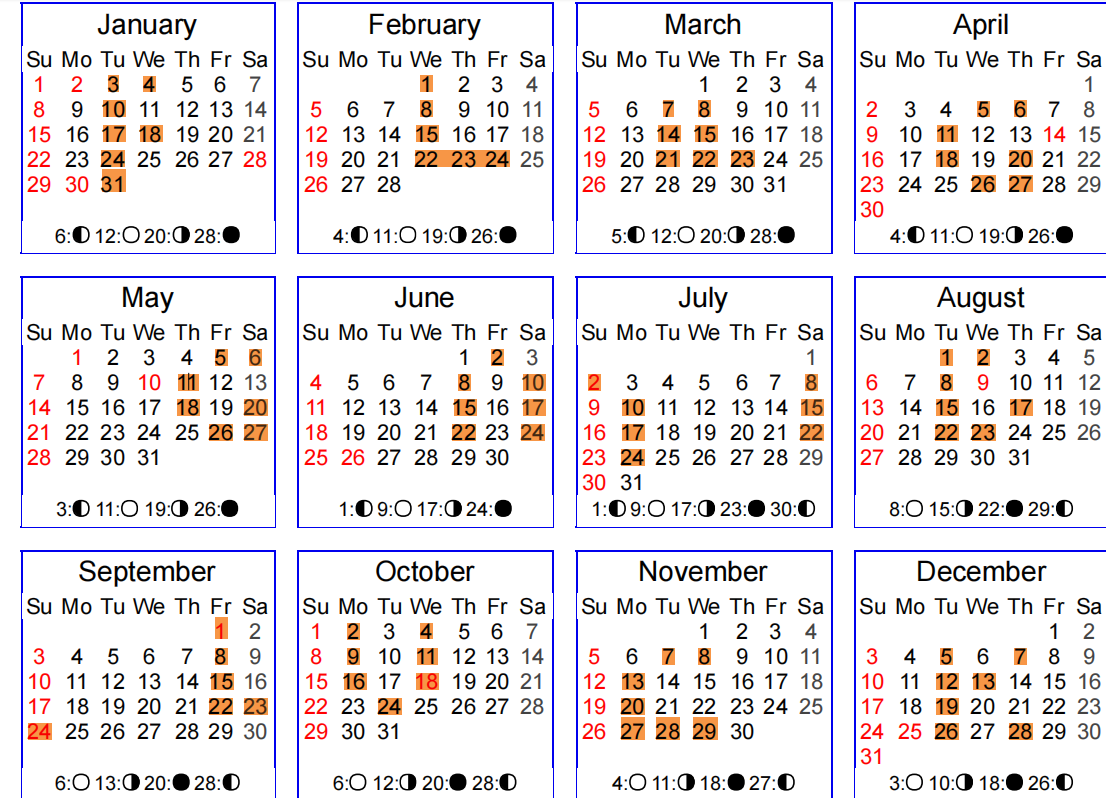
PDF里面是新加坡日历,没有想法,先分析rar吧,放到010分析

文件头反了,改成52 61 然后保存打开
解压后是一个文档,看名字date藏起来了,那就是docx隐写,文档隐写就不多说了比较基础,解决后里面是
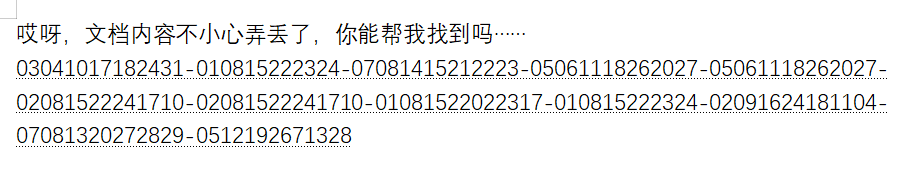
可以看到文档内容被加密了分啦12部分,正好对应PDF里面的十二个月

下面来分析一下数据,首先来看第一份数据,给它分成两个一组03 04 10 17 18 24 31,
因为它在第一位所以可以当做一月份来看对应日历表,我们可以根据这些日期的位置不难发现结果,如下图:
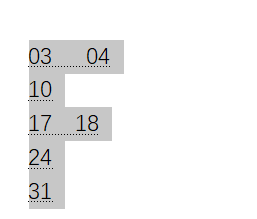
所以可以肯定后面的内容应该就是答案。我们一 一转化一下,可以得到结果为GOODLUCK,半转半猜吧!这个真的很无语,
但是看后面四个月份很明显是LUCK再加上五月份的G就能想到是GOODLUCK了。。。哎
MD5加密后为:
flag{7dcb9bc0c7e6055b544c78c0e3e4d4a5}鎏金哇开呀库裂!
修改文件后缀为png,打开是一张守望先锋的图片,010分析

尾部有一串base64,解一下得到
仔细看看图片。。。。没什么用,但尾部还有隐藏的txt,kali分离一下得到两个加密的压缩包,一个里面有flag.txt,另一个里面有ctf.txt,所以我们肯定要先破解ctf.txt所在的压缩包
因为flag.txt不可能这么容易得到。。。因此想到用爆破解决ctf.txt所在的压缩包但失败了,010也找不到密码,最后找了好久才发现一个细节,原本的图片左下方有东西
蛙趣,真的不仔细看还真看不出来。。。然后发现是owForever,这个应该就是密码了,然后解压打开
查看代码
.git
.git/HEAD
.git/index
.git/config
.git/description
source
source.php
source.php.bak
.idea/workspace.xml
.source.php.bak
source.php.swp
README.MD
README.md
README
.gitignore
.svn
.svn/wc.db
.svn/entries
user.php.bak
.hg
.DS_store
WEB-INF/web.xml
WEB-INF/src/
WEB-INF/classes
WEB-INF/lib
WEB-INF/database.propertie
CVS/Root
CVS/Entries
.bzr/
%3f
%3f~
.%3f.swp
.%3f.swo
.%3f.swn
.%3f.swm
.%3f.swl
_viminfo
.viminfo
%3f~
%3f~1~
%3f~2~
%3f~3~
%3f.save
%3f.save1
%3f.save2
%3f.save3
%3f.bak_Edietplus
%3f.bak
%3f.back
phpinfo.php
robots.txt
.htaccess
.bash_history
.svn/
.git/
.index.php.swp
index.php.swp
index.php.bak
.index.php~
index.php.bak_Edietplus
index.php.~
index.php.~1~
index.php
index.php~
index.php.rar
index.php.zip
index.php.7z
index.php.tar.gz
index.php.txt
login.php
register
register.php
test.php
upload.php
phpinfo.php
t.php
www.zip
www.rar
www.zip
www.7z
www.tar.gz
www.tar
web.zip
web.rar
web.zip
web.7z
web.tar.gz
web.tar
plus
qq.txt
log.txt
wwwroot.rar
web.rar
dede
admin
edit
Fckeditor
ewebeditor
bbs
Editor
manage
shopadmin
web_Fckeditor
login
flag
webadmin
admin/WebEditor
admin/daili/webedit
login/
database/
tmp/
manager/
manage/
web/
admin/
shopadmin/
wp-includes/
edit/
editor/
user/
users/
admin/
home/
test/
administrator/
houtai/
backdoor/
flag/
upload/
uploads/
download/
downloads/
manager/
root.zip
root.rar
wwwroot.zip
wwwroot.rar
backup.zip
backup.rar
.svn/entries
.git/config
.ds_store
flag.php
fl4g.php
f1ag.php
f14g.php
admin.php
4dmin.php
adm1n.php
4dm1n.php
admin1.php
admin2.php
adminlogin.php
administrator.php
login.php
register.php
upload.php
home.php
log.php
logs.php
config.php
member.php
user.php
users.php
robots.php
info.php
phpinfo.php
backdoor.php
fm.php
example.php
mysql.bak
a.sql
b.sql
db.sql
bdb.sql
ddb.sql
users.sql
mysql.sql
dump.sql
data.sql
backup.sql
backup.sql.gz
backup.sql.bz2
backup.zip
rss.xml
crossdomain.xml
1.txt
flag.txt
/wp-config.php
/configuration.php
/sites/default/settings.php
/config.php
/config.inc.php
/conf/_basic_config.php
/config/site.php
/system/config/default.php
/framework/conf/config.php
/mysite/_config.php
/typo3conf/localconf.php
/config/config_global.php
/config/config_ucenter.php
/lib
/data/config.php
/data/config.inc.php
/includes/config.php
/data/common.inc.php
/caches/configs/database.php
/caches/configs/system.php
/include/config.inc.php
/phpsso_server/caches/configs/database.php
/phpsso_server/caches/configs/system.php
404.php
index.html
user/
users/
admin/
home/
test/
administrator/
houtai/
backdoor/
flag/
uploads/
download/
downloads/
manager/
phpmyadmin/
phpMyAdmin/看到内容后应该想起来是字典爆破,得到密码.gitignore

打开flag.txt
21世纪20年代初,人类设计了由人工智能创造的智能机械(简称为智械),其旨在加强生产和创造世界经济繁荣。然而,令人难以置信的事情发生了,智械变得充满恶意,并开始大量生产军用机器人试图毁灭人类。各国政府未能阻止智能机械的进攻,因此联合国创建了一个国际维和组织,以反抗智能机械。汇集全世界最优秀最精英的组织被命名为“守望先锋”,其将围绕机器人军队展开一场实力不对称的战争。最初的守望先锋队伍有:来自德国的士兵莱因哈特·威尔海姆,瑞典武器工程师托比昂·林德霍姆,两名美国的强化试验士兵——军中至交好友——加布里埃尔·莱耶斯(死神)和杰克·莫里森(士兵:76),廖,以及安娜·艾玛莉(法老之鹰的母亲)。莱耶斯被选为守望先锋的领导者,但这个领袖称号实际上有名无实,莫里森磨合了所有人使之成为一个强大战斗力团队。智械危机持续了很多年,一种自适应海洋型机器人杀害了大量印度人民,肆虐澳大利亚,几近毁灭了西伯利亚和朝鲜半岛。但是尽管无比艰难,守望先锋也取得了一些胜利。俄国人击败并且关闭了他们的智能中心,韩国派出了电竞职业选手们,包括世界冠军D.va,他们以新的机甲套装对抗海洋型机器人。危机造成两边的大量伤亡和损失,人类赢得了最终的胜利,这在很大程度上要归功于守望先锋。在危机被终结后莫里升任守望先锋指挥官,莱耶斯则负责“暗影守望”——一个潜伏在暗处的秘密行动组织,而且该组织不受官方明文制约。随着岁月的流逝,守望先锋掌握的资源和能量日益增加,组织招收了更多的成员,并从突击组织转化成一个世界性维和组织,一些有才华的人加入了守望先锋。看到这么一段文字,能想到是零宽字节,解码即可

flag{hegesh1jiexuyaogengduodeingxi0ng}PolarD&N2023秋季个人挑战赛—Misc全解的更多相关文章
- 第48章 MDK的编译过程及文件类型全解—零死角玩转STM32-F429系列
第48章 MDK的编译过程及文件类型全解 全套200集视频教程和1000页PDF教程请到秉火论坛下载:www.firebbs.cn 野火视频教程优酷观看网址:http://i.youku.co ...
- 易全解token获取
//易全解app string strClientID = "2016061711434943493606"; string str ...
- IOS-UITextField-全解
IOS-UITextField-全解 //初始化textfield并设置位置及大小 UITextField *text = [[UITextField alloc]initWithFrame: ...
- 什么是JavaScript闭包终极全解之一——基础概念
本文转自:http://www.cnblogs.com/richaaaard/p/4755021.html 什么是JavaScript闭包终极全解之一——基础概念 “闭包是JavaScript的一大谜 ...
- Sql Server函数全解<五>之系统函数
原文:Sql Server函数全解<五>之系统函数 系统信息包括当前使用的数据库名称,主机名,系统错误消息以及用户名称等内容.使用SQL SERVER中的系统函数可以在需要的时候获取这些 ...
- Sql Server函数全解<四>日期和时间函数
原文:Sql Server函数全解<四>日期和时间函数 日期和时间函数主要用来处理日期和时间值,本篇主要介绍各种日期和时间函数的功能和用法,一般的日期函数除了使用date类型的参数外, ...
- 九度oj题目&吉大考研11年机试题全解
九度oj题目(吉大考研11年机试题全解) 吉大考研机试2011年题目: 题目一(jobdu1105:字符串的反码). http://ac.jobdu.com/problem.php?pid=11 ...
- js系列教程2-对象、构造函数、对象属性全解
全栈工程师开发手册 (作者:栾鹏) 快捷链接: js系列教程1-数组操作全解 js系列教程2-对象和属性全解 js系列教程3-字符串和正则全解 js系列教程4-函数与参数全解 js系列教程5-容器和算 ...
- js系列教程1-数组操作全解
全栈工程师开发手册 (作者:栾鹏) 快捷链接: js系列教程1-数组操作全解 js系列教程2-对象和属性全解 js系列教程3-字符串和正则全解 js系列教程4-函数与参数全解 js系列教程5-容器和算 ...
- css系列教程1-选择器全解
全栈工程师开发手册 (作者:栾鹏) 一个demo学会css css系列教程1-选择器全解 css系列教程2-样式操作全解 css选择器全解: css选择器包括:基本选择器.属性选择器.伪类选择器.伪元 ...
随机推荐
- Asp.net core Webapi 项目如何优雅地使用内存缓存
前言 缓存是提升程序性能必不可少的方法,Asp.net core 支持多级缓存配置,主要有客户端缓存.服务器端缓存,内存缓存和分布式缓存等.其中客户端缓和服务器端缓存在使用上都有比较大的限制,而内存缓 ...
- Redis 的主从复制
Redis 主从复制是指:将一台 Redis 服务器的数据复制到其它的 Redis 服务器,前者所在的 Redis 服务器也被称为 "主节点"(Master / Leader),后 ...
- 在线录屏-通过Web API接口轻松实现录屏
在线录屏是指在互联网上进行屏幕录制的过程.它允许用户通过网络连接,将自己的屏幕活动记录下来,并可以在需要时进行播放.共享或存档.在线录屏常用于教育.培训.演示.游戏等场景,可以帮助用户展示操作步骤.解 ...
- Flutter Getx 状态管理 --- (依赖管理) GetxController
Flutter Getx 简单的状态管理(依赖管理) GetxController Getx 依赖管理简介 Get有一个简单而强大的依赖管理器,它允许你只用1行代码就能检索到与你的Bloc或Contr ...
- 共赴元宇宙新纪元,华为云VR开发应用大赛总决赛倒计时7天!
摘要:"第三届华为云VR开发应用暨沈阳元宇宙开发应用大赛"总决赛即将于2月13日在沈阳市和平区揭幕. 由沈阳市和平区人民政府.华为技术有限公司共同主办的"第三届华为云VR ...
- 为AR&VR黑科技:以“自由视角”360度尽展舞台唯美
摘要:看华为的黑科技,如何用"自由视角"让观众感受舞台"风暴"的魅力所在. "风暴"降临 2021年1月9日晚上,我坐在电视机前,等待湖南卫 ...
- 将模型转为NNIE框架支持的wk模型第一步:tensorflow->caffe
摘要:本系列文章旨在分享tensorflow->onnx->Caffe->wk模型转换流程,主要针对的是HI3516CV500, Hi3519AV100 支持NNIE推理框架的海思芯 ...
- Open Serverless Benchmark Initiative: 华为云联合上海交大发布ServerlessBench 2.0
Key Takeaways 华为云联合上海交大,首次提出 Open Serverless Benchmark Initiative (OSBI) ,推动Serverless基准测评规范化.标准化: O ...
- GIS常用npm包:GeoJSON文件合并与元素过滤\属性过滤\图形合并
GeoJSON文件合并 普通的geoJSON文件合并,只需geojson-merge插件就够了,https://www.npmjs.com/package/@mapbox/geojson-merge ...
- AcWing 第 13 场周赛 补题记录
比赛链接:Here AcWing 3811. 排列 签到题, 先输出 \(n\) 然后输出 \(1\sim n -1\) 即可 AcWing 3812. 机器人走迷宫 不会什么特别高级的方法 qaq, ...
