Ethical Hacking - GAINING ACCESS(5)
Server Side Attack
Install Metasploit cummunity/pro and active it.
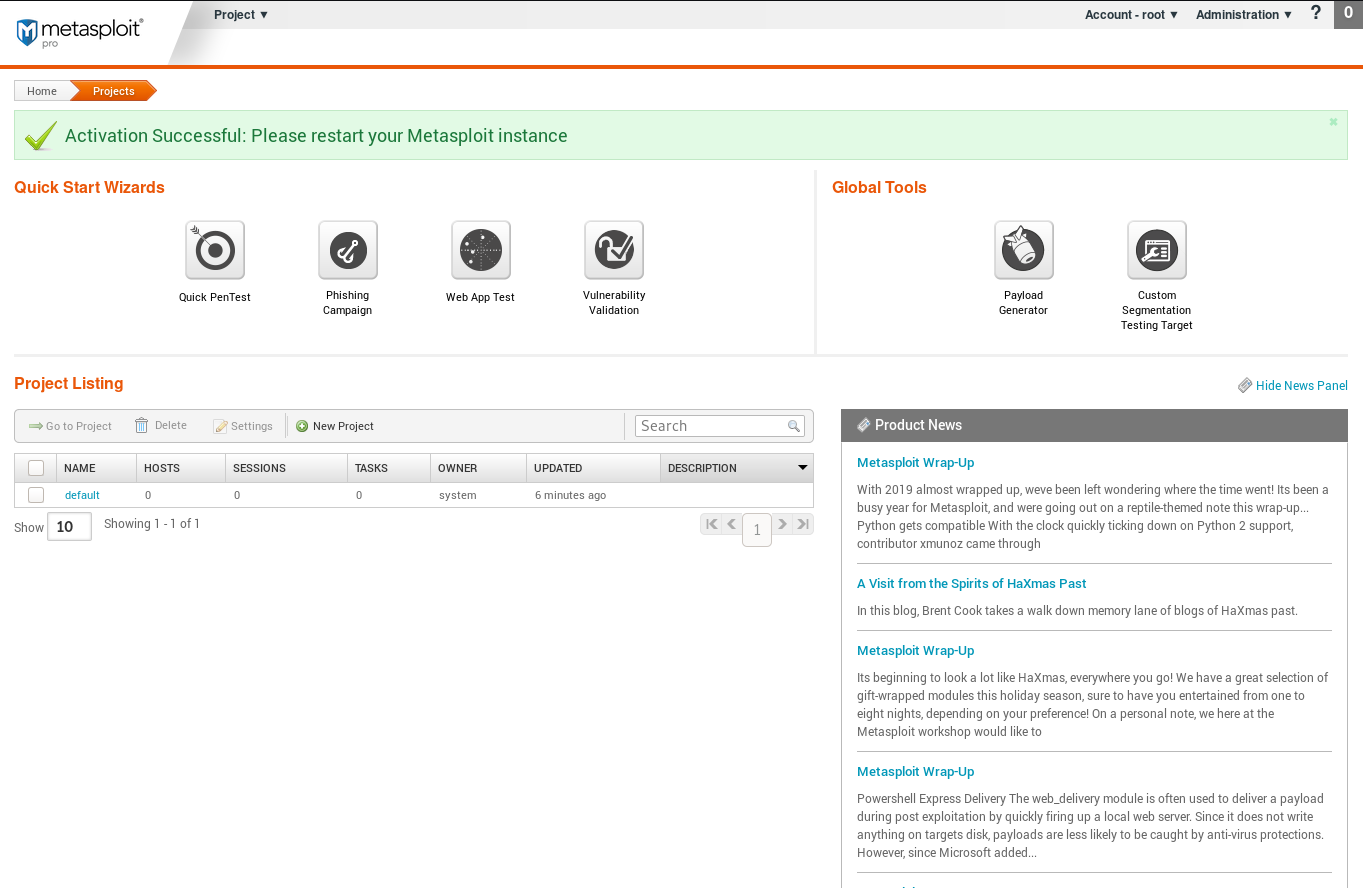
Create a new project for the target - Mestaploitable machine and start the scan.
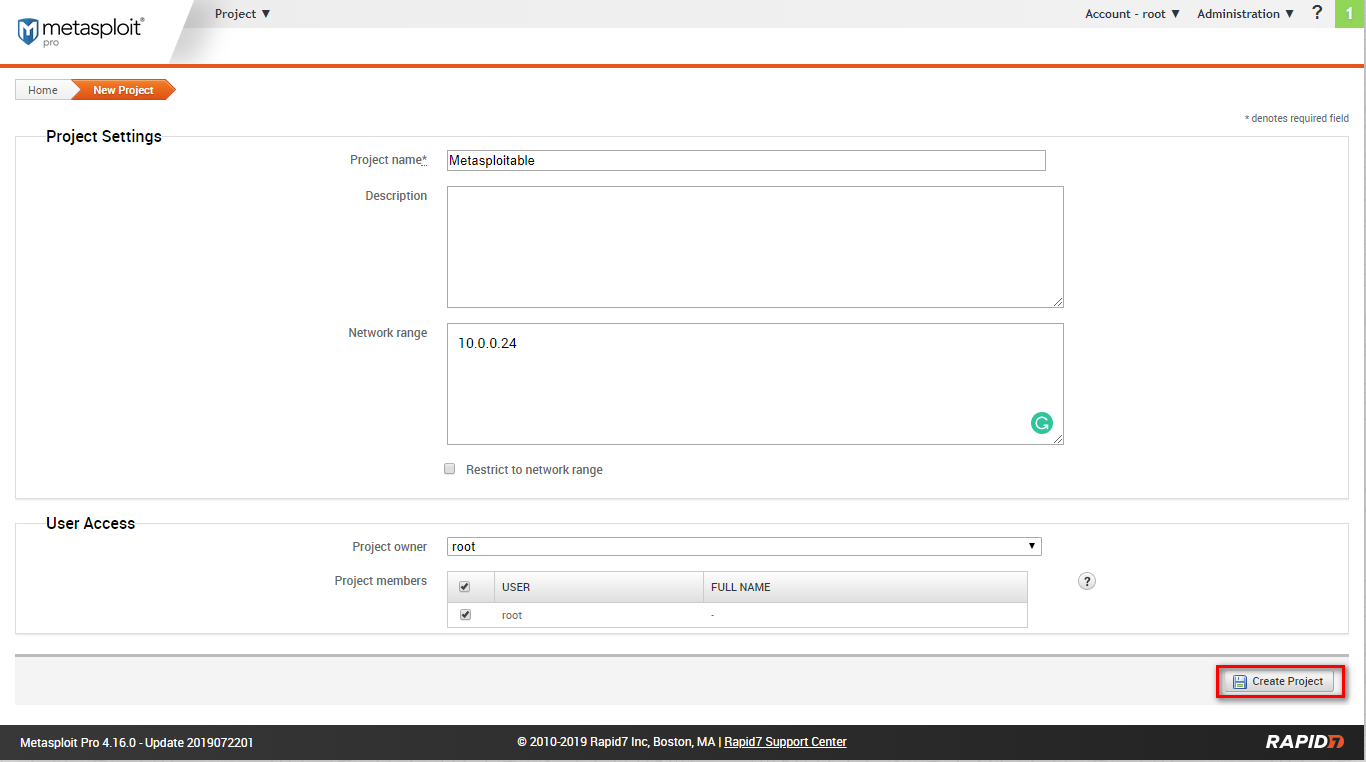
Start the scan task.

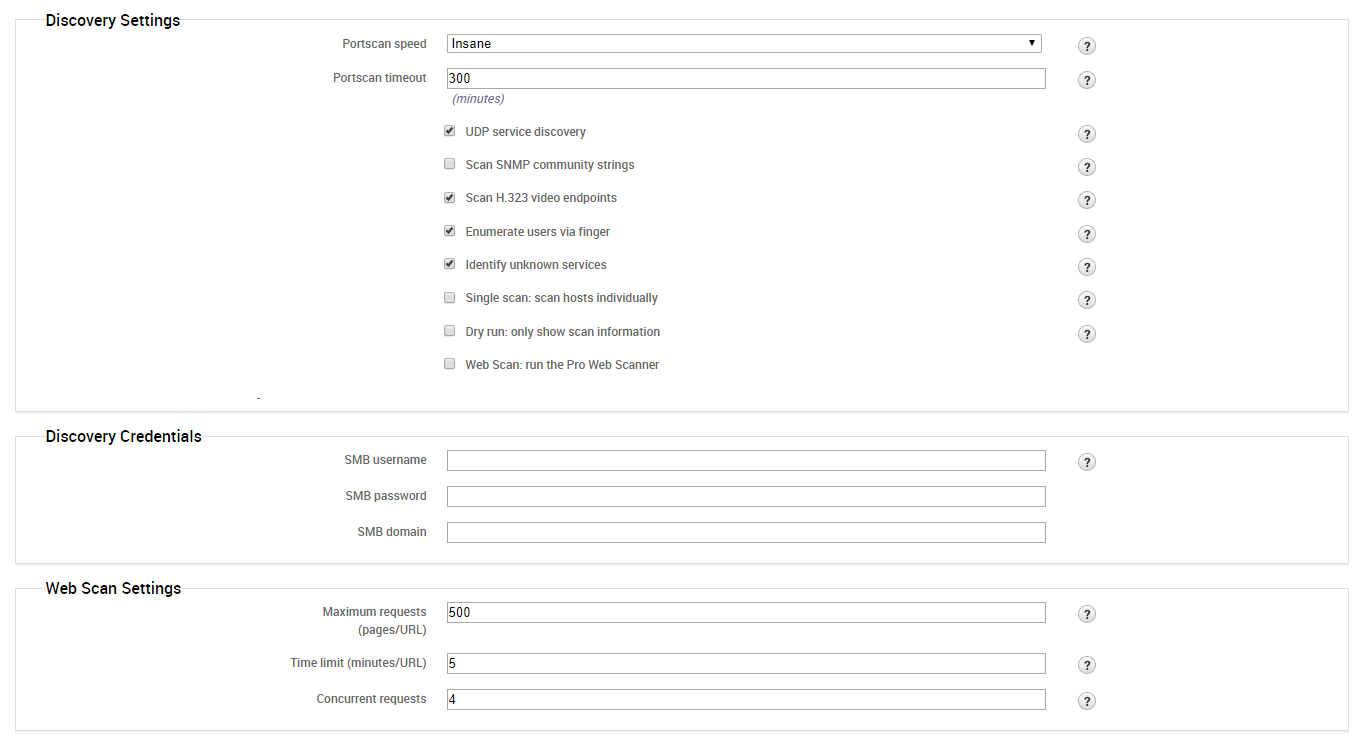
You can modify the advanced settings. But it is not a must.


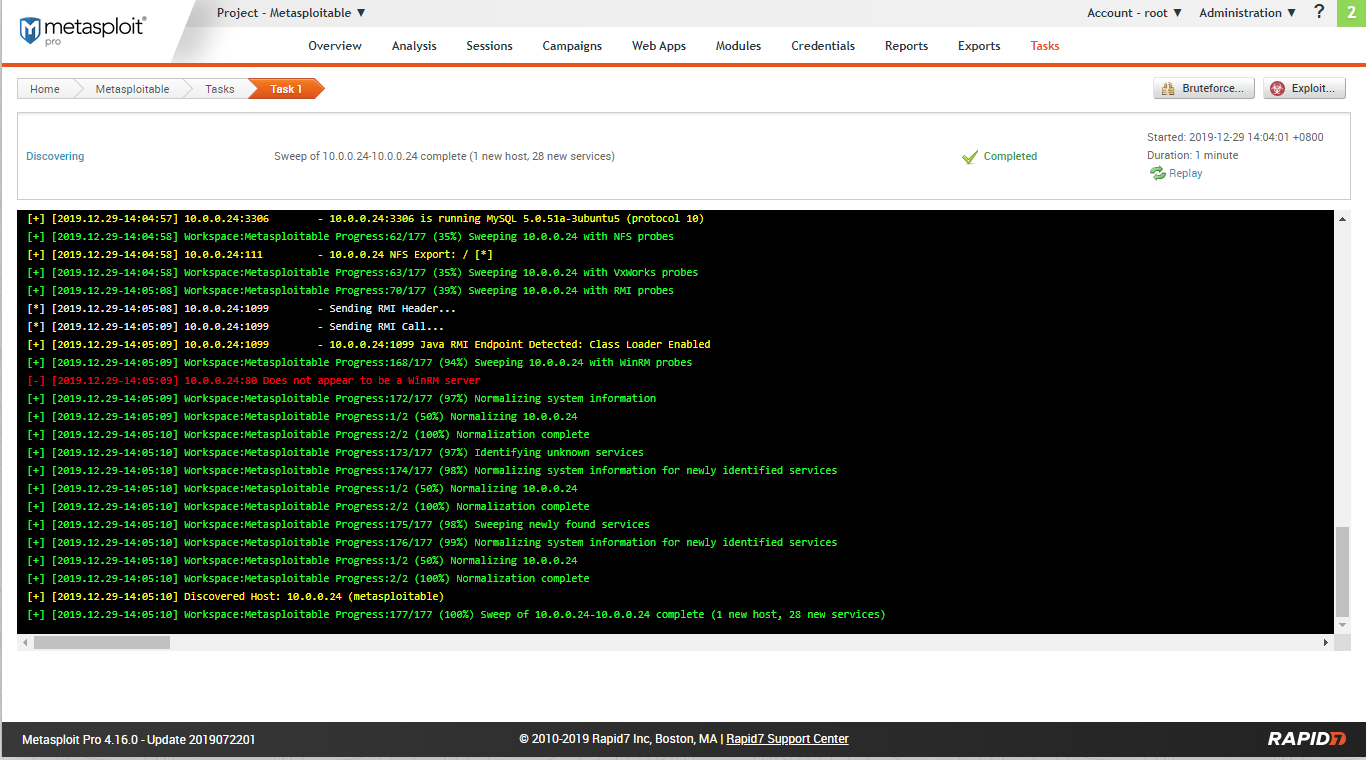
Launch scan and wait for the results.
Ethical Hacking - GAINING ACCESS(5)的更多相关文章
- Ethical Hacking - GAINING ACCESS(1)
Gaining Access Introduction Everything is a computer Two main approaches (1)Server Side Do not requi ...
- Ethical Hacking - GAINING ACCESS(23)
CLIENT SIDE ATTACK - BeEF Framework Hooking targets using MITMF Tools: MITMF and BeEF Start BeEF and ...
- Ethical Hacking - GAINING ACCESS(6)
Server Side Attack Analysing scan results and exploiting target system. Go to the Analysis page and ...
- Ethical Hacking - GAINING ACCESS(24)
CLIENT SIDE ATTACKS - Detecting Trojan manually or using a sandbox Analyzing trojans Check the prope ...
- Ethical Hacking - GAINING ACCESS(22)
CLIENT SIDE ATTACKS - BeEf Framework Browser Exploitation Framework allowing us to launch a number o ...
- Ethical Hacking - GAINING ACCESS(21)
CLIENT SIDE ATTACKS - Trojan delivery method - using email spoofing Use gathered info to contract ta ...
- Ethical Hacking - GAINING ACCESS(20)
CLIENT SIDE ATTACKS - Spoofing backdoor extension Change the extension of the trojan from exe to a s ...
- Ethical Hacking - GAINING ACCESS(19)
Client-Side Attacks - Social Engineering Tool: The FAT RAT Just like Veil, it generates Undetectable ...
- Ethical Hacking - GAINING ACCESS(18)
CLIENT SIDE ATTACKS Backdooring ANY file Combine backdoor with any file - Generic solution. Users ar ...
- Ethical Hacking - GAINING ACCESS(17)
CLIENT SIDE ATTACKS - Backdooring exe' s Download an executable file first. VEIL - FRAMEWORK A backd ...
随机推荐
- cb34a_c++_STL_算法_查找算法_(7)_lower_bound
cb34a_c++_STL_算法_查找算法_(7)_lower_bound//针对已序区间的查找算法,如set,multiset关联容器-自动排序lower_bound()--第一个可能的位置uppe ...
- Linux常用命令之文件磁盘管理
前言 本文知识点是曾经学习过程中收录整理的,方便学习使用. 一>Linux常用基本命令 Linux命令格式:command [-options] [parameter1] ... command ...
- nuget 包是如何还原包的
nuget 是如何还原包的 Intro 一直以来从来都是用 nuget 包,最近想折腾一个东西,需要自己搞一个 nuget 包的解析,用户指定 nuget 包的名称和版本,然后去解析对应的 nuget ...
- .NET Core Hangfire周期性作业调度问题
前言 四月中旬Hangfire团队发布了1.7.11版本,在使用周期性作业调度过程中发现一个问题,这个问题应该一直未解决,故做此记录,希望遇到的童鞋根据项目业务而避开这个问题. 周期性作业调度 我们依 ...
- 用Map+函数式接口来实现策略模式
用Map+函数式接口来实现策略模式 目前在魔都,贝壳找房是我的雇主,平时关注一些 java 领域相关的技术,希望你们能在这篇文章中找到些有用的东西.个人水平有限,如果文章有错误还请指出,在留言区一起交 ...
- el-table表头与内容右边框错位问题
在用element写一个后台管理系统时遇到一个坑,el-table标签渲染出数据后表头th和内容会有错位,之前没有的 修改大小都没用 于是看百度搜索一波最终解决修改之前 虽然不大 但是别扭 在全局添加 ...
- [源码解析]Oozie来龙去脉之提交任务
[源码解析]Oozie来龙去脉之提交任务 0x00 摘要 Oozie是由Cloudera公司贡献给Apache的基于工作流引擎的开源框架,是Hadoop平台的开源的工作流调度引擎,用来管理Hadoop ...
- Pop Sequence 题解
Pop Sequence(PAT) https://www.nowcoder.com/pat/5/problem/4090 前言: PAT上一道Stack的应用题,简化版的有<信息学一本通·普及 ...
- JVM源码分析之堆内存的初始化
原创申明:本文由公众号[猿灯塔]原创,转载请说明出处标注 “365篇原创计划”第十五篇. 今天呢!灯塔君跟大家讲: JVM源码分析之堆内存的初始化 堆初始化 Java堆的初始化入口位于Univ ...
- 二叉树的深度(剑指offer-38)
题目描述 输入一棵二叉树,求该树的深度.从根结点到叶结点依次经过的结点(含根.叶结点)形成树的一条路径,最长路径的长度为树的深度. 递归解析: 思路: 从根节点出发,查询左子树的深度,获取右子树的深度 ...
