A simple introduction to Three kinds of Delegation of Kerberos
1.What is Delegation?
Just like the name. Delegation is that a server pretend to behalf of a user and to authenticate with kerberos protocol.There are three kinds of delegations.
| Kinds of Delegations | Limitions | Protocol | Note |
|---|---|---|---|
| Unconstrained Delegation | None | Just forward the TGT ticket which is able to be forwarded | None |
| Constrained Delegation | Front-End Server decide which Back-End service can receive delegation | 1.S4U2Proxy -> Forward the TGT ticket 2.S4U2Self -> Receive information of NTLM Authentication(Username&NTLM-Hash) And use that to get TGT and send TGT and receive TGS from KDC |
AD administrator account |
| Resource-Based Constrained Delegation | Back-End Services decide which Front-End service's delegation can be received | The same as Constrained Delegation | 1.S4U2Proxy -> Can Forward TGT ticket which is not to be able to forwarded. 2.You can use this cross the domain. 3.Service administrator account |
2.Unconstrained Delegation
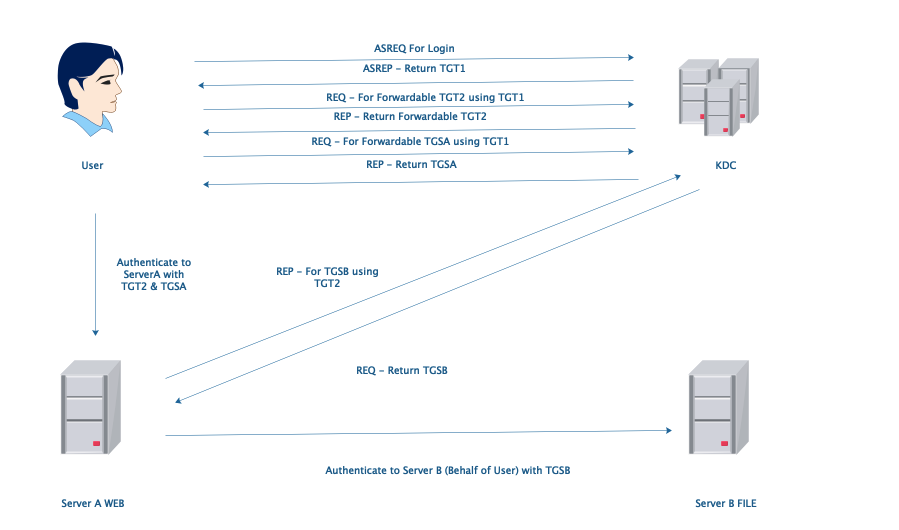
Unconstrained Delegation: ServerA can authenticate to any server in this domain behalf of user with TGT2. It is too dangerous.
3.Constrained Delegation
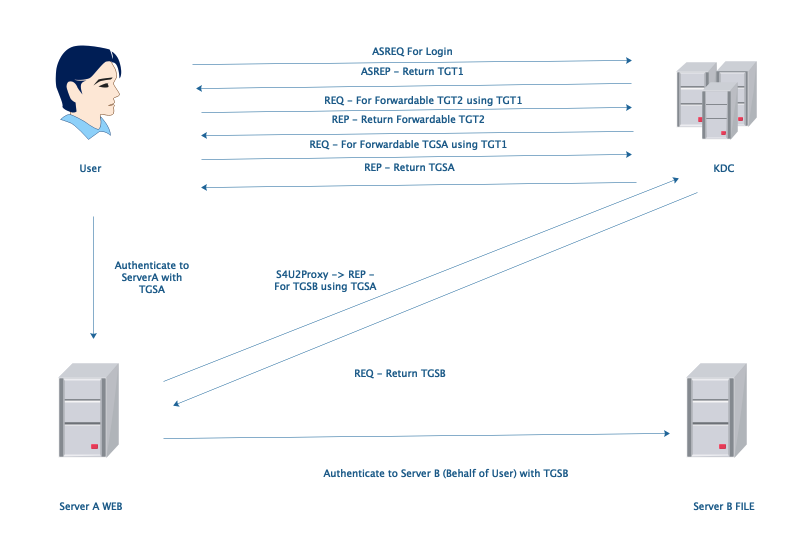
Only S4U2Proxy is what we need, if user use kerberos ticket to authenticate. Otherwise we need both S4U2Self and S4U2Proxy if user use NTLM hash to authenticate. In this condition, AD administrators can configure which service(SPNs) can receive ServerA’s delegation in ServerA's msDC-AllowedToDelegateTo property.
4.Resource-Based Constrained Delegation
There is one important difference between Constrained Delegation and Resource-Based Constrained Delegation. In Constrained Delegation, administrators of AD can configure which service can receive ServerA's delegation in their msDS-AllowedToActOnBehalfOfOtherIdentity properties. However, In Resource-Based Constrained Delegation, administrators of services can decide if those service will receive the ServerA's delegation or not. And it should be configured on the computers which is running those services. Do you think Resource-Based Constrained Delegation is much more safe than Constrained Delegation? No, Resource-Based Constrained Delegation has a big problem. In this condition, S4U2Proxy can forward unforwardable TGT and KDC will return TGS back. So if we could get the TGT which is not able to forward, We also could use it to do something bad.
5. What we can do to make it a little more safe?
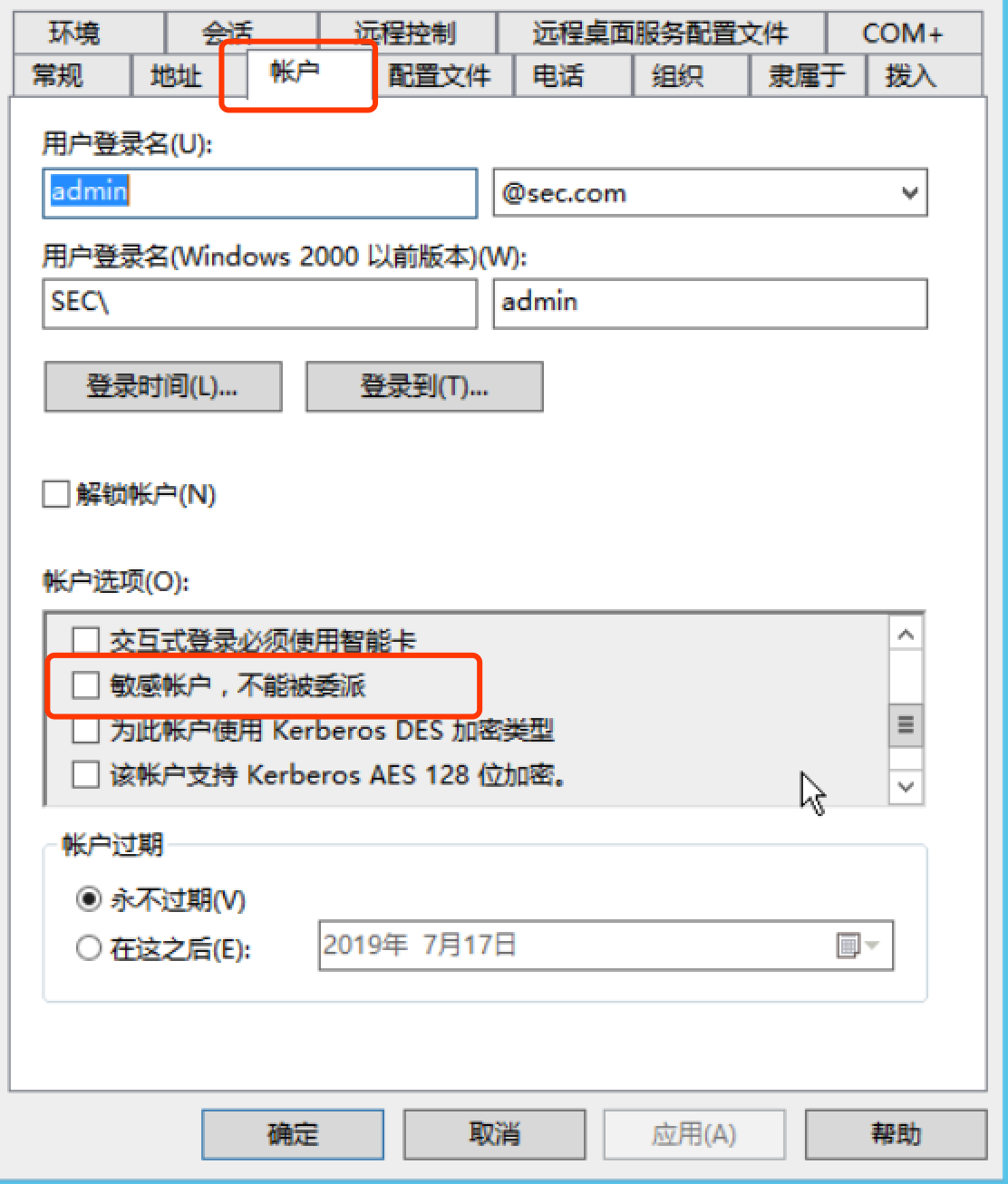
** We can do a lot of things to make it more safe. Plus, the first one is to configure like this.**
A simple introduction to Three kinds of Delegation of Kerberos的更多相关文章
- A Simple Introduction To Computer Networking
Most networking discussions are a jumble of acronyms. Forget the configuration details - what are th ...
- The Most Simple Introduction to Hypothesis Testing
https://www.youtube.com/watch?v=UApFKiK4Hi8
- 转:Simple Introduction to Dirichlet Process
来源:http://hi.baidu.com/vyfrcemnsnbgxyd/item/2f10ecc3fc35597dced4f88b Dirichlet Process(DP)是一个很重要的统计模 ...
- An Introduction to Variational Methods (5.1)
在这篇文章中,我引用Bishop书中的一个例子,来简单介绍一下Variational Methods的应用.想要更详细地理解这个例子,可以参考Bishop的书Pattern Recongnition ...
- 深度强化学习(Deep Reinforcement Learning)入门:RL base & DQN-DDPG-A3C introduction
转自https://zhuanlan.zhihu.com/p/25239682 过去的一段时间在深度强化学习领域投入了不少精力,工作中也在应用DRL解决业务问题.子曰:温故而知新,在进一步深入研究和应 ...
- ML Lecture 0-1: Introduction of Machine Learning
本博客是针对李宏毅教授在Youtube上上传的课程视频<ML Lecture 0-1: Introduction of Machine Learning>的学习笔记.在Github上也po ...
- CI Weekly #6 | 再谈 Docker / CI / CD 实践经验
CI Weekly 围绕『 软件工程效率提升』 进行一系列技术内容分享,包括国内外持续集成.持续交付,持续部署.自动化测试. DevOps 等实践教程.工具与资源,以及一些工程师文化相关的程序员 Ti ...
- 理解callback function in javascript
以下内容主要摘自[1,2] (1)In javascript, functions are first-class objects, which means functions can be used ...
- Discovering the Computer Science Behind Postgres Indexes
This is the last in a series of Postgres posts that Pat Shaughnessy wrote based on his presentation ...
随机推荐
- VUE小练习(按钮颜色,数组映射)
VUE小练习(按钮颜色,数组映射) ## 1.有红.黄.蓝三个按钮,以及一个200x200矩形框box, 点击不同的按钮,box的颜色会被切换成指定的颜色 ''' 解法一:我本来的思路,把三个按钮绑定 ...
- pycharm访问mysql数据库
不需要像eclipse那样添加驱动包,在pycharm里面下载一个pymysql包即可. 然后链接自己电脑的mysql并进行访问即可. 源码如下(参考博客:https://blog.csdn.net/ ...
- 使用CSS来渲染HTML的表单元素
效果: 实现: <!DOCTYPE html> <html> <head> <title>使用CSS来渲染HTML的表单元素</title> ...
- Codechef Prime Distance On Tree
[传送门] FFT第四题! 暑假的时候只会点分,然后合并是暴力合并的...水过去了... 其实两条路径长度的合并就是卷积的过程嘛,每次统计完路径就自卷积一下. 刚开始卷积固定了值域.T了.然后就不偷懒 ...
- [LeetCode] 141. Linked List Cycle 单链表中的环
Given a linked list, determine if it has a cycle in it. To represent a cycle in the given linked lis ...
- [LeetCode] 96. Unique Binary Search Trees 独一无二的二叉搜索树
Given n, how many structurally unique BST's (binary search trees) that store values 1 ... n? Example ...
- 15 张 Vim 速查表奉上,帮你提高N倍效率!
阅读本文大概需要 2.8 分钟. 去年上半年开始全面使用linux进行开发和娱乐了,现在已经回不去windows了. 话归正传,在linux上一直使用vim,慢慢熟悉了它的命令,才终于领悟了什么是编辑 ...
- iphone 移动端操作记录
iPhone和Safari浏览器的后退按钮操作,是直接载入缓存中的页面,不会加载js文件,不会执行ready,onload函数,但是加载html页面会跑pageshow事件,因此有回退动作需要重新加载 ...
- sql server 2019 & spark
https://cloudblogs.microsoft.com/sqlserver/2019/04/01/how-to-develop-and-submit-spark-jobs-to-sql-se ...
- idea类存在找不到解决办法
清除idea缓存,
