Kubernetes web界面kubernetes-dashboard安装【h】
本文讲述的是如何部署K8s的web UI,前提是已经有一个k8s集群后,按照如下步骤进行即可。(如下步骤都是在master节点上进行操作)
1、下载kubernetes-dashboard.yaml文件
2、修改kubernetes-dashboard.yaml文件

# ------------------- Dashboard Deployment ------------------- # kind: Deployment
apiVersion: apps/v1beta2
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
spec:
containers:
- name: kubernetes-dashboard
image: registry.cn-hangzhou.aliyuncs.com/kube_containers/kubernetes-dashboard-amd64
ports:
- containerPort: 8443
protocol: TCP
args:
- --auto-generate-certificates


# ------------------- Dashboard Service ------------------- # kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
spec:
type: NodePort
ports:
- port: 443
targetPort: 8443
nodePort: 30001
selector:
k8s-app: kubernetes-dashboard

上面代码红色字为kubernetes-dashboard.yaml文件中需要修改的地方,不然拉取不了镜像,以及使用Nodeport方式做映射,使其他主机能够访问该dashboard。
3、创建kubernetes-dashboard.yaml
kubectl create -f kubernetes-dashboard.yaml
4、查看kubernetes-dashboard容器是否已经运行

[root@docker-master1 ~]# kubectl get pods -n kube-system
NAME READY STATUS RESTARTS AGE
coredns-576cbf47c7-l5wlh 1/1 Running 1 3d8h
coredns-576cbf47c7-zrl66 1/1 Running 1 3d8h
etcd-docker-master1 1/1 Running 1 3d8h
kube-apiserver-docker-master1 1/1 Running 2 3d8h
kube-controller-manager-docker-master1 1/1 Running 2 3d8h
kube-flannel-ds-amd64-c7wz6 1/1 Running 0 3d8h
kube-flannel-ds-amd64-hqvz9 1/1 Running 0 3d8h
kube-flannel-ds-amd64-w7n4s 1/1 Running 2 3d8h
kube-proxy-8gj2w 1/1 Running 1 3d8h
kube-proxy-mt6dk 1/1 Running 0 3d8h
kube-proxy-qtxz7 1/1 Running 0 3d8h
kube-scheduler-docker-master1 1/1 Running 2 3d8h
kubernetes-dashboard-5f864b6c5f-5s2rw 1/1 Running 0 62m

如上红色字体已经显示kubernetes-dashboard已经成功在node节点上运行。当然,你也可以前往node节点上执行docker ps查看kubernetes-dashboard容器是否已经启动,netstat -ptln命令查看30001端口是否已经开放。
5、创建kubernetes-dashboard管理员角色

[root@docker-master1 ~]# vi k8s-admin.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: dashboard-admin
namespace: kube-system
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: dashboard-admin
subjects:
- kind: ServiceAccount
name: dashboard-admin
namespace: kube-system
roleRef:
kind: ClusterRole
name: cluster-admin
apiGroup: rbac.authorization.k8s.io

6、加载管理员角色
kubectl create -f k8s-admin.yaml
7、获取dashboard管理员角色token

#获取dashboard secret
kubectl get secret -n kube-system
[root@docker-master1 ~]# kubectl get secret -n kube-system
NAME TYPE DATA AGE
attachdetach-controller-token-d9w8c kubernetes.io/service-account-token 3 3d8h
bootstrap-signer-token-jdjwt kubernetes.io/service-account-token 3 3d8h
bootstrap-token-9n6rpz bootstrap.kubernetes.io/token 6 149m
bootstrap-token-n962df bootstrap.kubernetes.io/token 7 3d8h
certificate-controller-token-lktt8 kubernetes.io/service-account-token 3 3d8h
clusterrole-aggregation-controller-token-7stf6 kubernetes.io/service-account-token 3 3d8h
coredns-token-kbz5z kubernetes.io/service-account-token 3 3d8h
cronjob-controller-token-b647q kubernetes.io/service-account-token 3 3d8h
daemon-set-controller-token-tzlpk kubernetes.io/service-account-token 3 3d8h
dashboard-admin-token-jc8t5 kubernetes.io/service-account-token 3 17m


#获取token
[root@docker-master1 ~]# kubectl describe secret dashboard-admin-token-jc8t5 -n kube-system
Name: dashboard-admin-token-jc8t5
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: dashboard-admin
kubernetes.io/service-account.uid: cdfb442a-f48b-11e8-80e8-000c29c3dca5 Type: kubernetes.io/service-account-token Data
====
namespace: 11 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tamM4dDUiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiY2RmYjQ0MmEtZjQ4Yi0xMWU4LTgwZTgtMDAwYzI5YzNkY2E1Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.FZCsonMyEdcDDvbzIz7rMxm8vvlk0Ck6O5ooqzaJRWkggwMoqf92qYBsNxMxxT5BdAtxB_iPUD7rEagR7sLTqixHeC0HdTnGCcTnNU1fq2KJA5ssNyi9P4XGJqsGuf4mAmF5L56uBh43X4hQ41rFYPQwIrmVnknTAbAWf3biiKWkN9Az8NsCulRSSCsJSOwfPoGlo7aSbMYTyRXlmzLuLbkMpMvyMHChBJ_MIYbH9dBj_hL3L9iwo9gpNTfB-0_uYHPEPdQcib8qUkC5NxgXdBuQPug5y1kLUVFNgq45ozLTibZuVihK_gza-WKVpBRPY5PaYCN1Gu0-tFObUYDUow

8、使用管理员角色登陆kubernetes-dashboard web界面
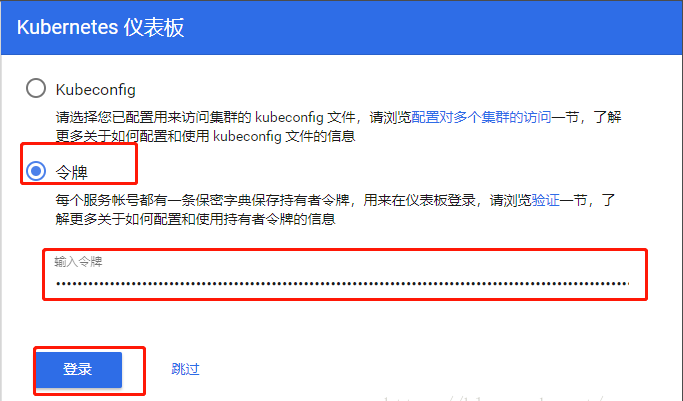
客户端浏览器输入:https://nodeIP:nodeport ,也就是kubernetes-dashboard容器在哪台node节点上跑,以及上面设置的nodeport端口(我这里是https://192.168.20.214:30001)
出现如下界面,选择令牌——输入令牌,(令牌为上面的token)
9、dashboard访问方式
根据官方文档,目前访问Dashboard有四种方式:
- NodePort
- API Server
- kubectl proxy
- Ingress
以上四种方式,我测试了前三种,目前只有NodePort和kubectl proxy可用,API Server暂时没有解决。
- 使用NodePort
为kubernetes-dashboard.yaml添加Service后,就可以使用NodePort访问Dashboard。在我们的物理机上,使用Chrome访问https://192.168.20.214:30001/,如上2步骤。(2步骤使用的就是nodeport方式访问)
如访问提示了证书错误NET::ERR_CERT_INVALID,原因是由于物理机的浏览器证书不可用。我们可以生成一个私有证书或者使用公有证书,下面开始配置证书。

#1、查看kubernetes-dashboard 容器跑在哪台node节点上,这里跑在docker-slave2上
root@docker-master1 pki]# kubectl get pod -n kube-system -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE
coredns-576cbf47c7-l5wlh 1/1 Running 1 9d 10.244.0.5 docker-master1 <none>
coredns-576cbf47c7-zrl66 1/1 Running 1 9d 10.244.0.4 docker-master1 <none>
etcd-docker-master1 1/1 Running 1 9d 192.168.20.210 docker-master1 <none>
kube-apiserver-docker-master1 1/1 Running 2 9d 192.168.20.210 docker-master1 <none>
kube-controller-manager-docker-master1 1/1 Running 2 9d 192.168.20.210 docker-master1 <none>
kube-flannel-ds-amd64-c7wz6 1/1 Running 0 9d 192.168.20.213 docker-slave1 <none>
kube-flannel-ds-amd64-hqvz9 1/1 Running 0 9d 192.168.20.214 docker-slave2 <none>
kube-flannel-ds-amd64-w7n4s 1/1 Running 2 9d 192.168.20.210 docker-master1 <none>
kube-proxy-8gj2w 1/1 Running 1 9d 192.168.20.210 docker-master1 <none>
kube-proxy-mt6dk 1/1 Running 0 9d 192.168.20.213 docker-slave1 <none>
kube-proxy-qtxz7 1/1 Running 0 9d 192.168.20.214 docker-slave2 <none>
kube-scheduler-docker-master1 1/1 Running 2 9d 192.168.20.210 docker-master1 <none>
kubernetes-dashboard-5f864b6c5f-5s2rw 1/1 Running 0 5d21h 10.244.3.9 docker-slave2 <none>

#2、在docker-slave2节点上查看kubernetes-dashboard容器ID
root@docker-slave2 ~]# docker ps | grep dashboard
384d9dc0170b registry.cn-hangzhou.aliyuncs.com/kube_containers/kubernetes-dashboard-amd64 "/dashboard --insecu…" 5 days ago Up 44 hours k8s_kubernetes-dashboard_kubernetes-dashboard-5f864b6c5f-5s2rw_kube-system_94c8c50b-f484-11e8-80e8-000c29c3dca5_0

#3、查看kubernetes-dashboard容器certs所挂载的宿主主机目录
[root@docker-slave2 ~]# docker inspect -f {{.Mounts}} 384d9dc0170b
"Mounts": [
{
"Type": "bind",
"Source": "/var/lib/kubelet/pods/94c8c50b-f484-11e8-80e8-000c29c3dca5/volumes/kubernetes.io~empty-dir/tmp-volume",
"Destination": "/tmp",
"Mode": "",
"RW": true,
"Propagation": "rprivate"
},
{
"Type": "bind",
"Source": "/var/lib/kubelet/pods/94c8c50b-f484-11e8-80e8-000c29c3dca5/volumes/kubernetes.io~secret/kubernetes-dashboard-token-tbctd",
"Destination": "/var/run/secrets/kubernetes.io/serviceaccount",
"Mode": "ro",
"RW": false,
"Propagation": "rprivate"
},
{
"Type": "bind",
"Source": "/var/lib/kubelet/pods/94c8c50b-f484-11e8-80e8-000c29c3dca5/etc-hosts",
"Destination": "/etc/hosts",
"Mode": "",
"RW": true,
"Propagation": "rprivate"
},
{
"Type": "bind",
"Source": "/var/lib/kubelet/pods/94c8c50b-f484-11e8-80e8-000c29c3dca5/containers/kubernetes-dashboard/0e84c511",
"Destination": "/dev/termination-log",
"Mode": "",
"RW": true,
"Propagation": "rprivate"
},
{
"Type": "bind",
"Source": "/var/lib/kubelet/pods/94c8c50b-f484-11e8-80e8-000c29c3dca5/volumes/kubernetes.io~secret/kubernetes-dashboard-certs",
"Destination": "/certs",
"Mode": "ro",
"RW": false,
"Propagation": "rprivate"
}
],

#4、这里以私有证书配置,生成dashboard证书
openssl genrsa -des3 -passout pass:x -out dashboard.pass.key 2048
openssl rsa -passin pass:x -in dashboard.pass.key -out dashboard.key
openssl req -new -key dashboard.key -out dashboard.csr
openssl x509 -req -sha256 -days 365 -in dashboard.csr -signkey dashboard.key -out dashboard.crt
#5、将生成的dashboard.crt dashboard.key放到certs对应的宿主主机souce目录
scp dashboard.crt dashboard.key 192.168.20.214:/var/lib/kubelet/pods/94c8c50b-f484-11e8-80e8-000c29c3dca5/volumes/kubernetes.io~secret/kubernetes-dashboard-certs
#6、重启kubernetes-dashboard容器
docker restart 384d9dc0170b
完成以上步骤即可访问kubernetes-dashboard web了,由于使用的是私有证书,所以还是会弹出不安全的连接,需要添加例外。
2、使用API Server
在我们的物理机上,使用Chrome访问地址:https://192.168.20.210:6443/api/v1/namespaces/kube-system/services/https:kubernetes-dashboard:/proxy/,返回如下错误:

{
"kind": "Status",
"apiVersion": "v1",
"metadata": {
},
"status": "Failure",
"message": "services \"https:kubernetes-dashboard:\" is forbidden: User \"system:anonymous\" cannot get resource \"services/proxy\" in API group \"\" in the namespace \"kube-system\"",
"reason": "Forbidden",
"details": {
"name": "https:kubernetes-dashboard:",
"kind": "services"
},
"code": 403
}

原因是由于kube-apiserver使用了TLS认证,而我们的真实物理机上的浏览器使用匿名证书(因为没有可用的证书)去访问Dashboard,导致授权失败而不无法访问。官方提供的解决方法是将kubelet的证书转化为浏览器可用的证书,然后导入进浏览器。但是该方法目前似乎不适用于kubeadm方式安装的集群,参见:https://github.com/opsnull/follow-me-install-kubernetes-cluster/issues/5 。看来,无论物理机还是K8S节点上的浏览器,都需要导入这个证书,暂时无解。
3、使用kubectl proxy
这里,我主要介绍一下最便捷的kubectl proxy方式。在Master上执行nohup kubecll proxy &,然后使用如下地址访问Dashboard:
http://localhost:8001/api/v1/namespaces/kube-system/services/https:kubernetes-dashboard:/proxy
但限制就是必须在Master上访问,这显然是个坑,我们的目标是在我们真实的物理机上去访问Master的Dashboard。
所以,在主节点上,我们执行nohup kubectl proxy --address=192.168.20.210 --disable-filter=true & 开启代理。
其中:
address表示外界可以使用192.168.20.210来访问Dashboard,我们也可以使用0.0.0.0disable-filter=true表示禁用请求过滤功能,否则我们的请求会被拒绝,并提示Forbidden (403) Unauthorized。- 我们也可以指定端口,具体请查看
kubectl proxy --help
此时proxy默认对Master的8001端口进行监听:
这样,我们就可以使用如下地址访问登录界面:
http://192.168.20.210:8001/api/v1/namespaces/kube-system/services/https:kubernetes-dashboard:/proxy/#!/login
Kubernetes web界面kubernetes-dashboard安装【h】的更多相关文章
- Kubernetes web界面kubernetes-dashboard安装
本文讲述的是如何部署K8s的web UI,前提是已经有一个k8s集群后,按照如下步骤进行即可.(如下步骤都是在master节点上进行操作) 1.下载kubernetes-dashboard.yaml文 ...
- Kubernetes入门(二)——Dashboard 安装
Kubernetes集群搭建完成后,可以通过命令行方式可以了解集群资源的使用情况,但是这种方式比较笨拙且不直观,因此考虑给集群安装Dashboard,这样能更直观了解集群状态.本文Dashboard的 ...
- Centos7.2/7.3集群安装Kubernetes 1.8.4 + Dashboard(转)
原文https://www.cnblogs.com/burningTheStar/p/7865998.html 1.环境配置 结点数量:3 结点系统:CentOS 7.2 / 7.3 2.效果展示 3 ...
- kubernetes dashboard 安装
环境:CentOS Linux release 7.3.1611 (Core)IP:192.168.0.103 [1]组件安装yum install device-mapperyum install ...
- kubernetes系列(十七) - 通过helm安装dashboard详细教程
1. 前提条件 2. 配置https证书为secret 3. dashboard安装 3.1 helm拉取dashboard的chart 3.2 配置dashboard的chart包配置 3.3 he ...
- Kubernetes 部署Web UI (Dashboard)
Kubernetes 部署Web UI (Dashboard) 项目下载地址:https://github.com/kubernetes/kubernetes/tree/master/cluster/ ...
- kubernetes实战篇之dashboard搭建
系列目录 kubernetes dashboard是kubernetes官方提供的web管理界面,通过dashboard可以很方便地查看集群的各种资源.以及修改资源编排文件,对集群进行扩容操作,查看日 ...
- centos7.3 kubernetes/k8s 1.10 离线安装 --已验证
本文介绍在centos7.3使用kubeadm快速离线安装kubernetes 1.10. 采用单master,单node(可以多node),占用资源较少,方便在笔记本或学习环境快速部署,不适用于生产 ...
- [原]CentOS7安装Rancher2.1并部署kubernetes (二)---部署kubernetes
################## Rancher v2.1.7 + Kubernetes 1.13.4 ################ ##################### ...
随机推荐
- c语言1-2019秋作业02
格式: 这个作业属于那个课程 C语言程序设计I 这个作业要求在哪里 http://edu.cnblogs.com/campus/zswxy/SE2019-3/homework/8688 我在这个课程的 ...
- js原型补充
js定义函数: <script> function A() {} let a1 = new A(); let a2 = new A(); // 为A类添加原型 => 类似于类属性 A ...
- HDU 6060 - RXD and dividing | 2017 Multi-University Training Contest 3
/* HDU 6060 - RXD and dividing [ 分析,图论 ] | 2017 Multi-University Training Contest 3 题意: 给一个 n 个节点的树, ...
- 写出一条SQL语句:取出表A中第31到40行记录(SQLserver,以自增长的ID作为主键,注意: 一条Sql语句:取出表A中第31到第40记录
解1: select top 10 * from A where id not in (select top 30 id from A) 解2: select top 10 * from A wher ...
- 南京IT公司
公司 (排名不分前后,有好的公司可以@我,及时更新) 1.中兴软创 http://www.ztesoft.com/cn/index.html 2.华为 http://www.huawei.com/cn ...
- IntelliJ IDEA 运行项目的时候提示 Command line is too long 错误
在 IntelliJ IDEA 项目运行的时候收到了下面的错误提示: Error running 'Application': Command line is too long. Shorten co ...
- hdu 1133 卡特兰 高精度
Buy the Ticket Time Limit: 2000/1000 MS (Java/Others) Memory Limit: 65536/32768 K (Java/Others) T ...
- codeforces163D
Large Refrigerator CodeForces - 163D 给定一个长方体的体积V,求出这个长方体的最小表面积. 输入 第一行有一个整数t (1 ≤ t ≤ 500) — 测试数据的组数 ...
- [笔记]C++声明返回数组指针的函数
数组指针的声明:type (*name)[size]; 由于数组不能拷贝,所以函数不能返回数组.但是函数可以返回指针和引用,所以函数可以返回数组指针或引用. 和数组指针的声明类似: type (*fu ...
- python获取最大值
python2 中获取int最大值 import sys print sys.maxint 但是在python3中,报错: AttributeError: module 'sys' has no at ...
