Cyber Security - Palo Alto Firewall V-Wires
Leveraging V-Wires
- Bridge two physical connections and apply security
- Policies without influencing any routing decision(transparent Firewall inspection)
- Inspect per VLAN traffic by creating V-Wire sub interfaces.
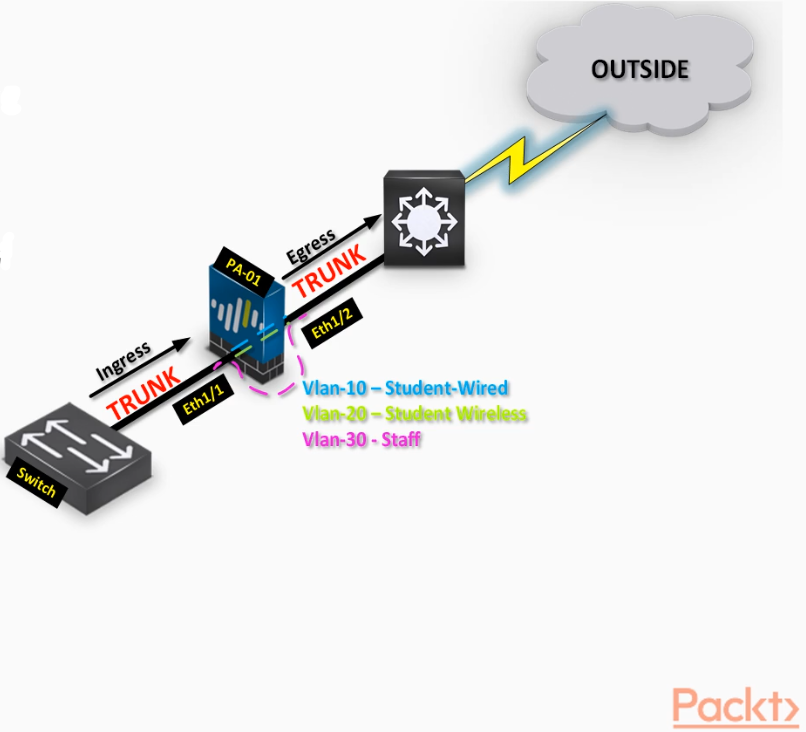
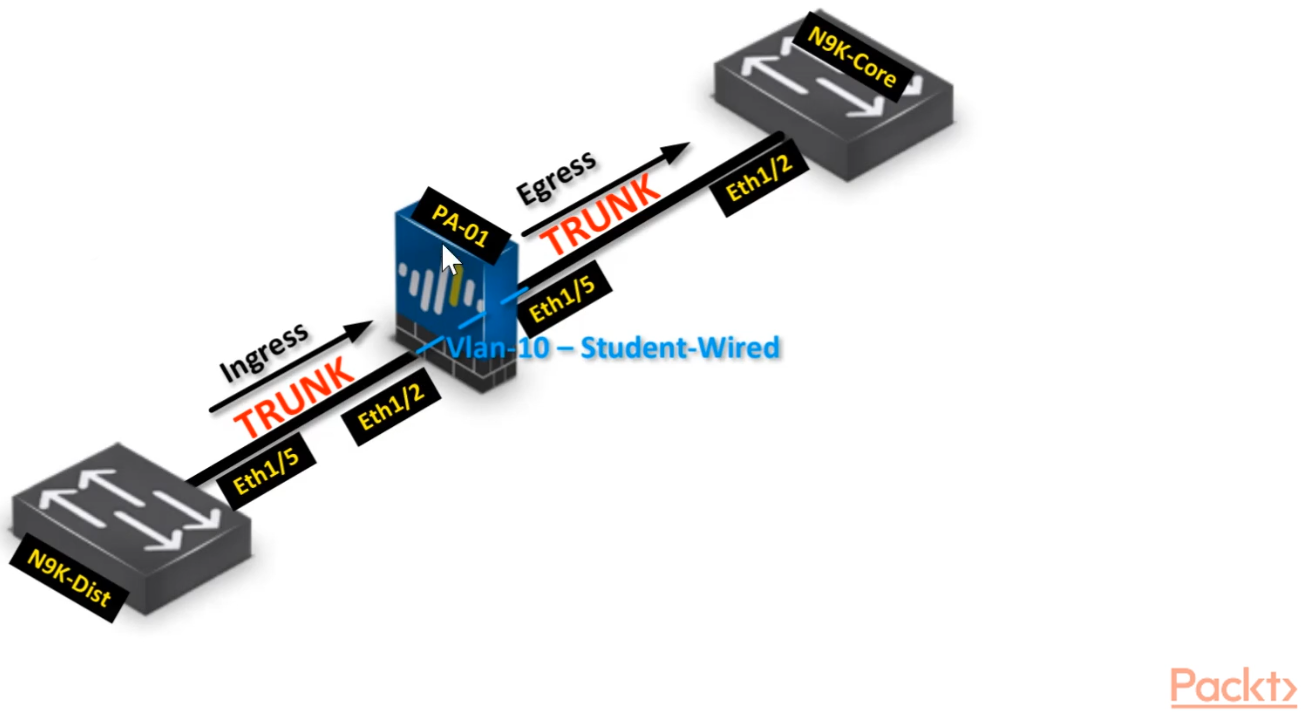
Interface configuration>>
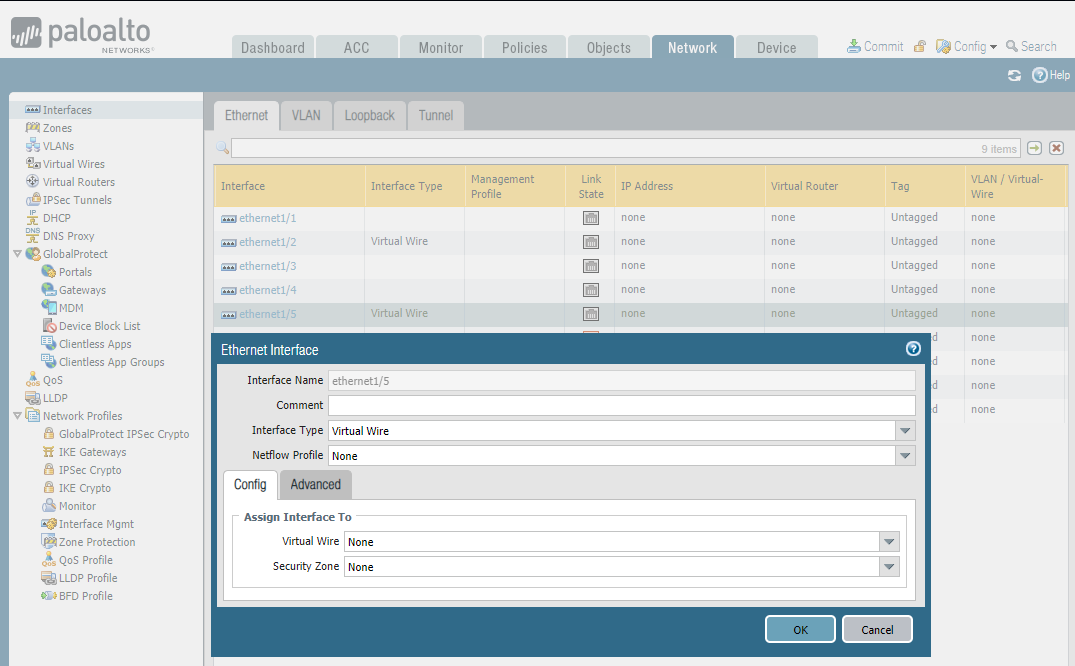
STEP1: Configure parent Virtual Wire interfaces - ethernet 1/2 and ethernet 1/5
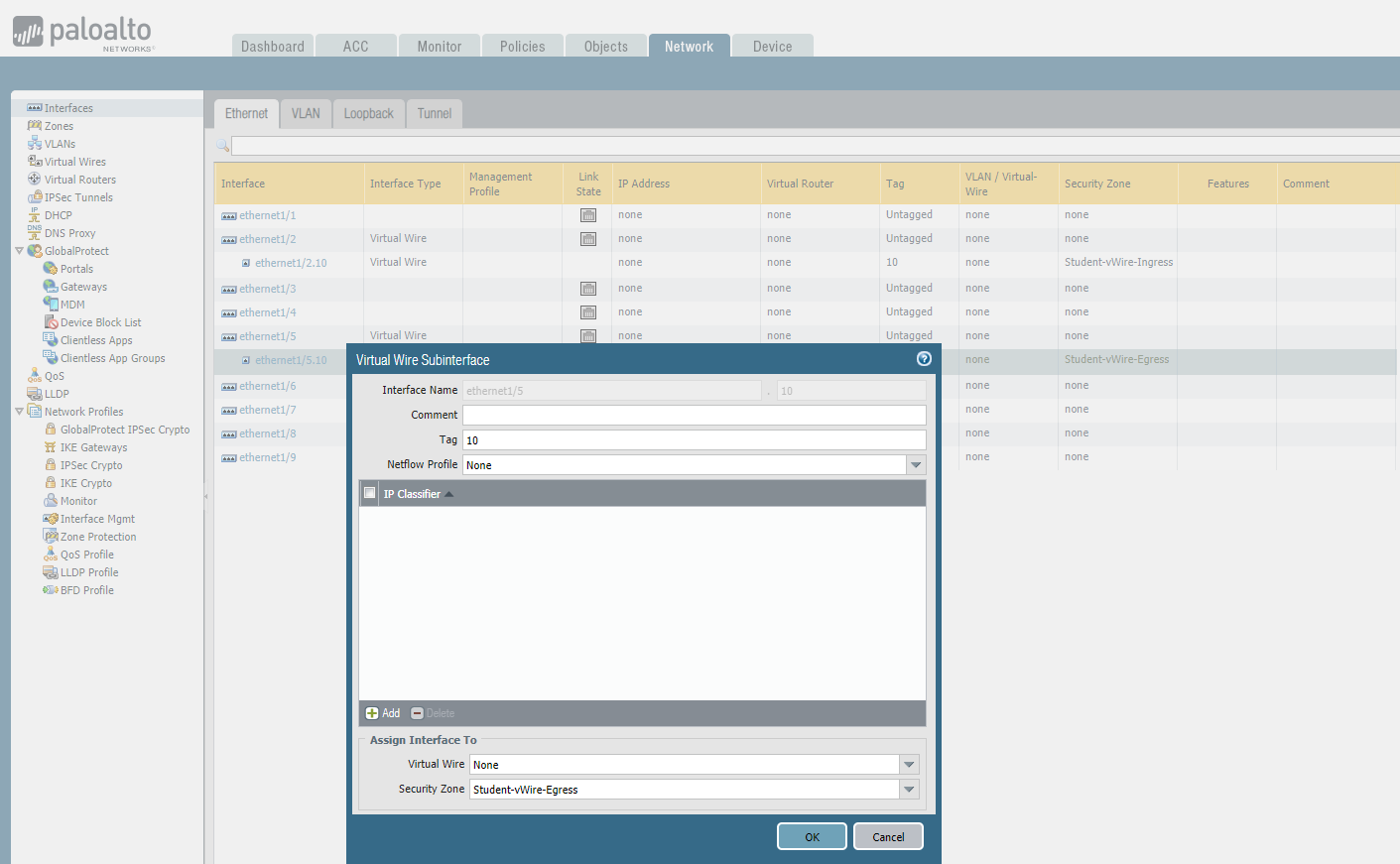
STEP2: Configure subinterface - ethernet1/2.10 and ethernet 1/5/10
STEP3: Connect virtual wires - Parent-vWire
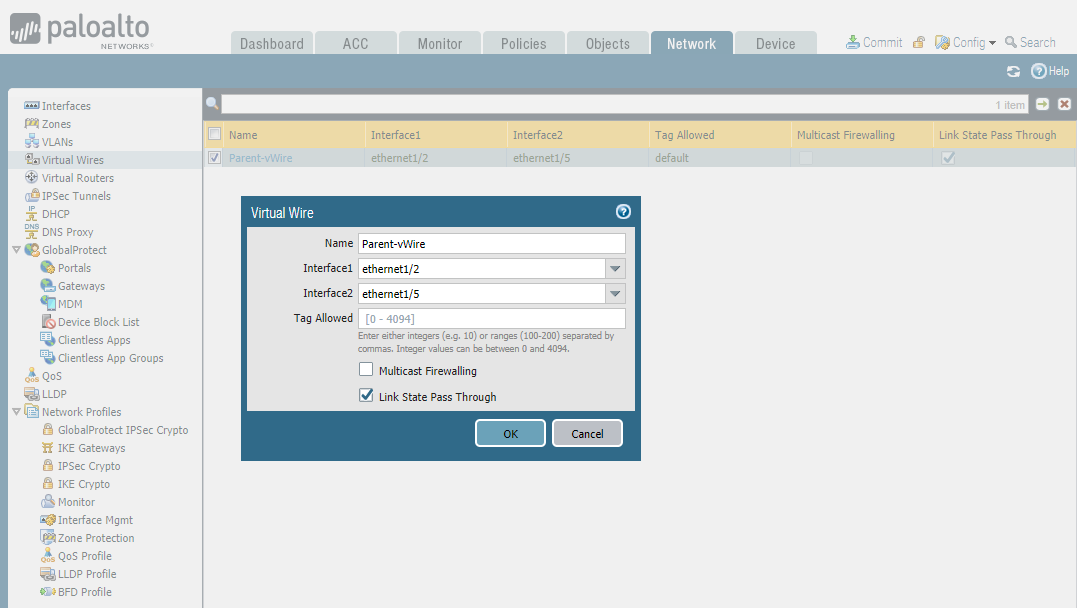
STEP4: Connect virtual wires - Sub-vWire
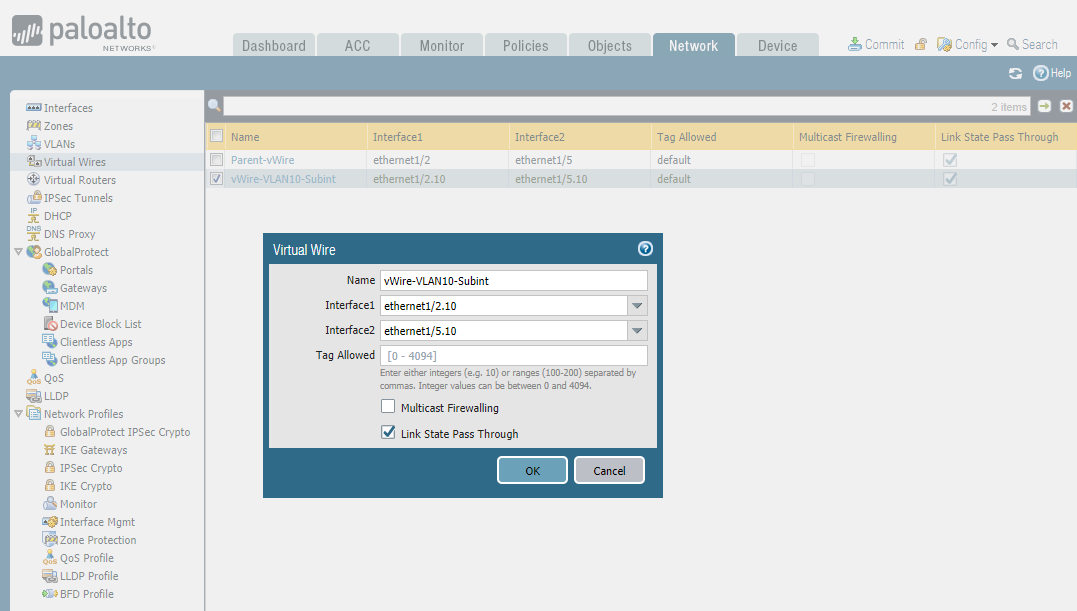
STEP5: Configure security policies.
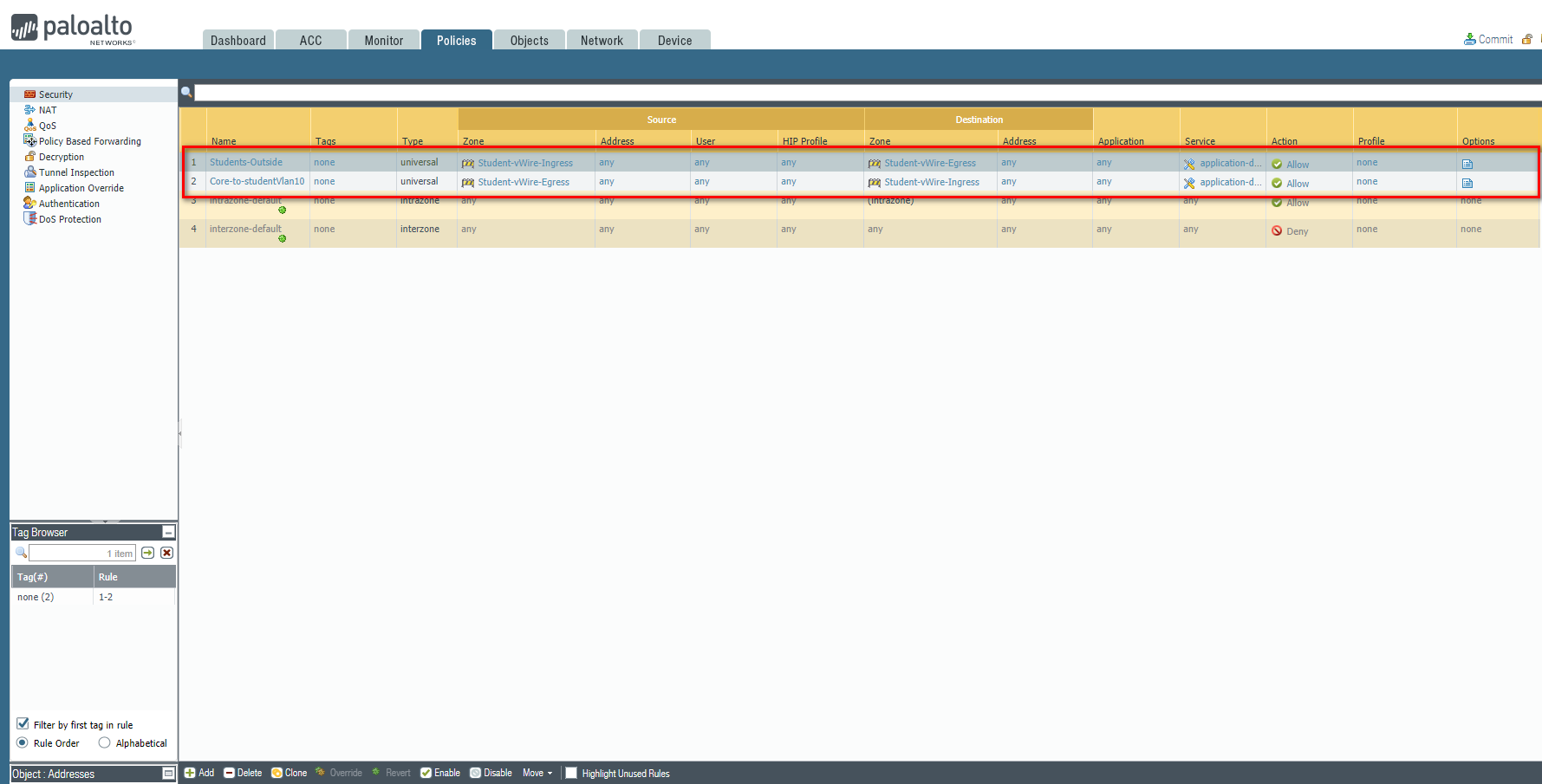
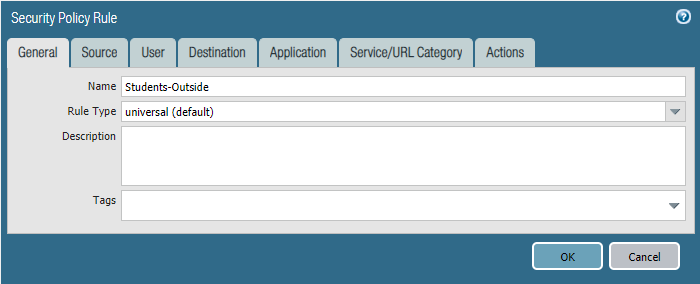
Students-Outside
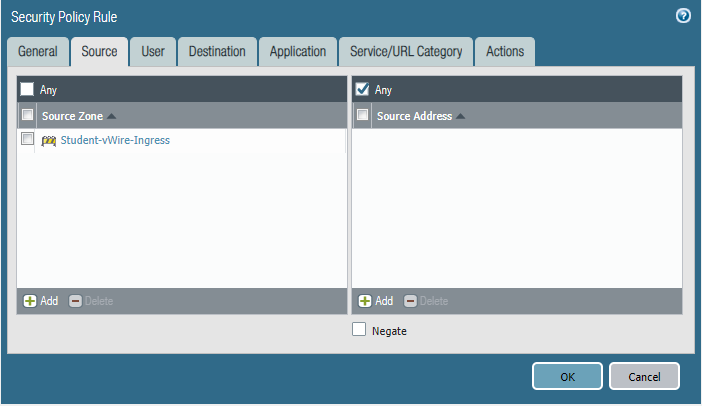
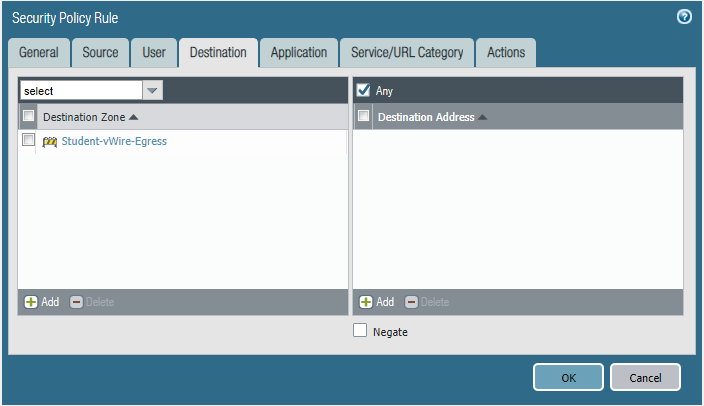
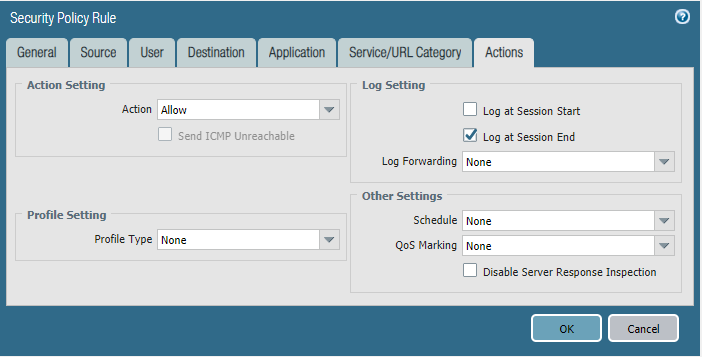
Core-to-studentVlan10
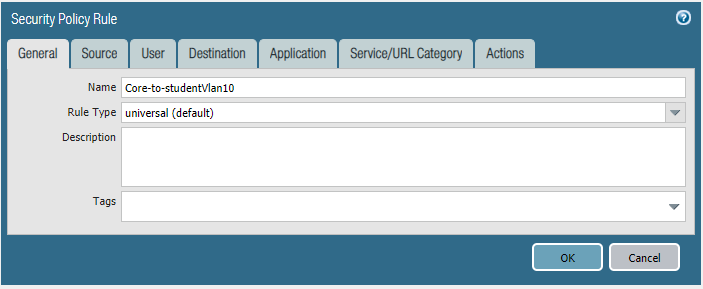
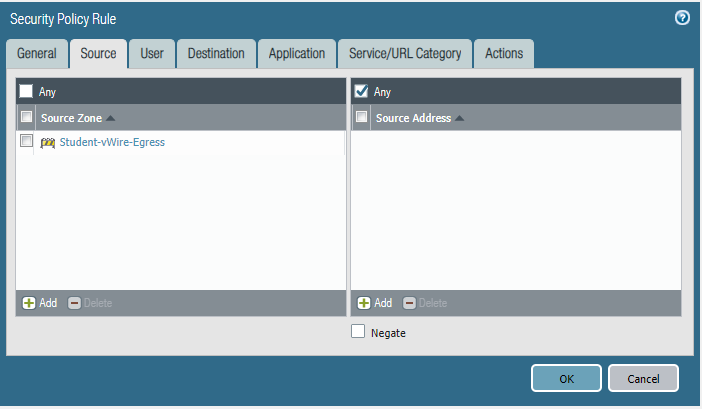
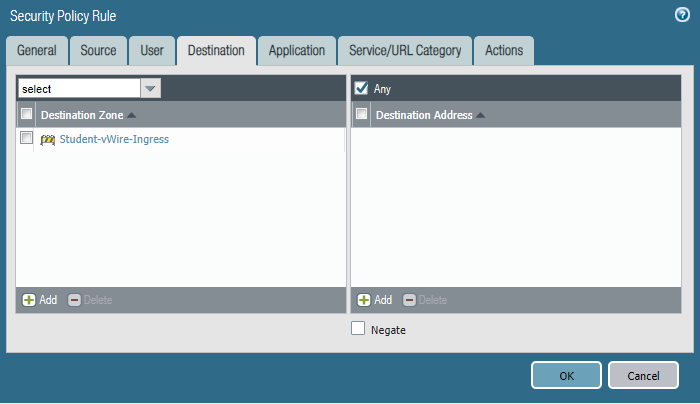
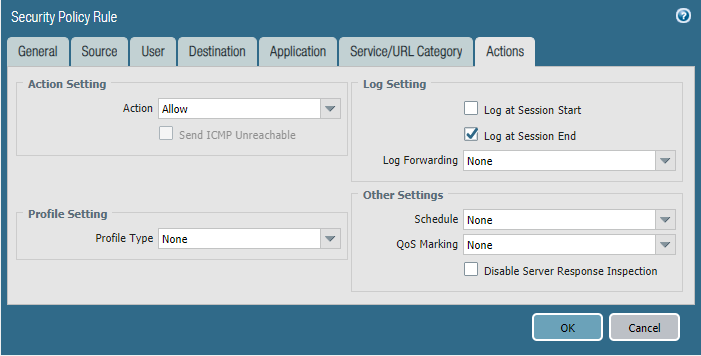
Commit the configuration and test.
Students-Outside
Cyber Security - Palo Alto Firewall V-Wires的更多相关文章
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(3)
LDAP Authentication and Remote Users and Groups Create Remote User Objects and LDAP Integration: sam ...
- Cyber Security - Palo Alto Firewall Interface Types
Multiple options to integrate the Palo Alto Firewall into your: Network Layer 2 interfaces and VLAN ...
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(1)
Address Objects and Groups Creating address objects. Organizing address objects with address groups ...
- Cyber Security - Palo Alto Firewall Security Zones
Firewall Security Zones Zones: The foundational aspect of every Firewall. Police network traffic Enf ...
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(2)
Users Objects and Groups Creating local user objects. Creating local user groups. https://docs.paloa ...
- Cyber Security - Palo Alto Security Policies(2)
Task 3 The SOC(Security Operation Center) monitoring team dashboard reported more 1,000 requests to ...
- Cyber Security - Palo Alto Security Policies(1)
Security policies: Enforcing network traffic by configuring rules of what is allowed or denied to co ...
- Cyber Security - Palo Alto Basic Introduction
Preparation of the Lab Environment: Download and Install Pan-OS from the following website https://d ...
- Palo Alto GlobalProtect上的PreAuth RCE
0x00 前言 SSL VPN虽然可以保护企业资产免受互联网被攻击的风险影响,但如果SSL VPN本身容易受到攻击呢?它们暴露在互联网上,可以可靠并安全地连接到内网中.一旦SSL VPN服务器遭到入侵 ...
随机推荐
- 剑指 Offer 09. 用两个栈实现队列
剑指 Offer 09. 用两个栈实现队列 用两个栈实现一个队列.队列的声明如下,请实现它的两个函数 appendTail 和 deleteHead ,分别完成在队列尾部插入整数和在队列头部删除整数的 ...
- 富文本插件tinymce初始化配置参数说明
{ language: _this.language, // 显示语种 selector: #${_this.tinymceId}, // 容器的id height: _this.height, // ...
- elasticSearch插件的安装以及使用nginx的modles收集nginx的日志
1.首先在windows环境上搭建es的集群 集群的配置如下 #node01的配置: cluster.name: es-itcast-cluster node.name: node01 node.ma ...
- PHP 多维数组转json对象
PHP 多维数组转json对象 php 数组转json对象,可能大家都知道要用json_encode,但是转换出来的格式多有不同,此处做个小小的记录! 1. 一维数组转json对象 <?php ...
- Freemarker在replace替换是对NULL值的处理
freemarker的对象调用内建函数时,比如userInfo对象的birthDay函数,页面${userInfo.birthDay}调用,当我想将birthDay值中的“-”替换为“/”时,${us ...
- webpack入门进阶(3)
1.11.预处理器文件处理 1.sass文件 sass这种css预处理器是以.scss结尾,需要用node-sass和sass-loader来处理 安装loader npm i node-sass s ...
- 不错的UI设计
- 浅谈MySQL数据库
目录 什么是数据库 定义 发展现状 数据库基本概念 数据库分类 关系数据库 非关系型数据库(NoSQL) 数据库启动与连接 启动服务端 连接数据库 用户信息查看 数据库的基本操作 表的基本操作 记录的 ...
- Linux中more和less的区别
more的源码量大约2000行: less的源码量大约27000行: more历史比less久: less功能比more多: 其实本质没啥太大区别,都是为了查看文件方便. (完)
- kibana限制用户只具备读图的权限
假设需求 因为业务需要将日志系统收集到的信息进行图表化展示并交付到用户进行业务交流. 解决方案 这个需求看着似乎蛮简单的,如何解决? 1.对需要的数据进行过滤制作图表 2.对用户的权限限制为只读级别, ...
