SPRING IN ACTION 第4版笔记-第九章Securing web applications-009-拦截请求()
一、
对特定的请求拦截
For example, consider the requests served by the Spittr application. Certainly, the
home page is public and doesn’t need to be secured. Likewise, since all Spittle
objects are essentially public, the pages that display Spittle s don’t require security.
Requests that create a Spittle , however, should only be performed by an authenti-
cated user. Similarly, although user profile pages are public and don’t require authen-
tication, if you were to handle a request for /spitters/me to display the current user’s
profile, then authentication is required to know whose profile to show.
The key to fine-tuning security for each request is to override the configure
(HttpSecurity) method. The following code snippet shows how you might override
configure(HttpSecurity) to selectively apply security to different URL paths.
@Override
protected void configure(HttpSecurity http) throws Exception {
http
.authorizeRequests()
.antMatchers("/spitters/me").authenticated()
.antMatchers(HttpMethod.POST, "/spittles").authenticated()
.anyRequest().permitAll();
}
The HttpSecurity object given to configure() can be used to configure several
aspects of HTTP security. Here you’re calling authorizeRequests() and then calling
methods on the object it returns to indicate that you want to configure request-level
security details. The first call to antMatchers() specifies that requests whose path is
/spitters/me should be authenticated. The second call to antMatchers() is even
more specific, saying that any HTTP POST request to /spittles must be authenticated.
Finally, a call to anyRequests() says that all other requests should be permitted, not
requiring authentication or any authorities.
(1)用通配符
.antMatchers("/spitters/**").authenticated();
(2)写多个路径
.antMatchers("/spitters/**", "/spittles/mine").authenticated();
(3)Whereas the antMatchers() method works with paths that may contain Ant-style wild-
cards, there’s also a regexMatchers() method that accepts regular expressions to
define request paths. For example, the following snippet uses a regular expression
that’s equivalent to /spitters/** (Ant-style):
.regexMatchers("/spitters/.*").authenticated();
(4)全部可配置的方法
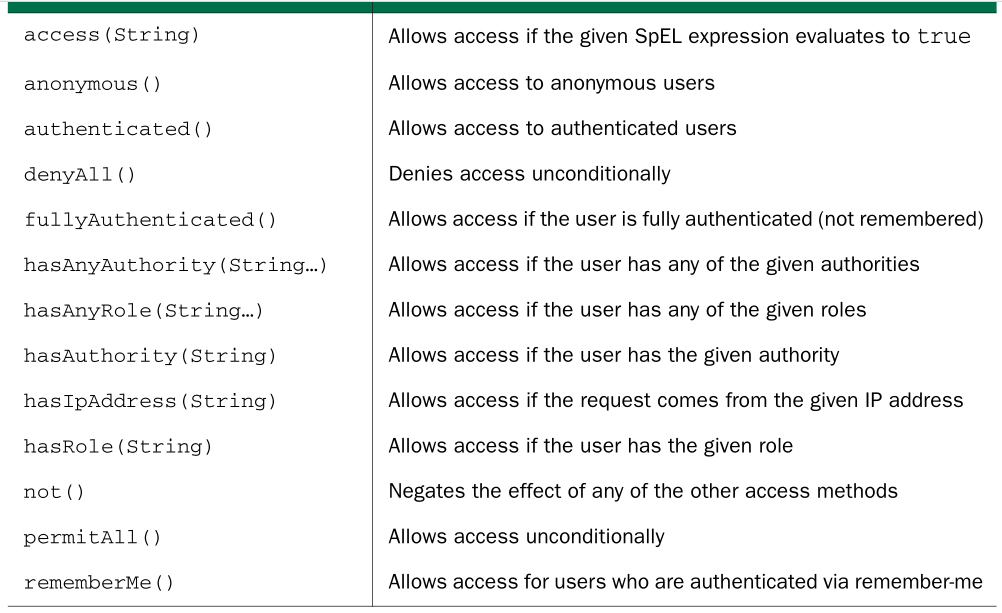
(1)you could change the previous configure() method to require that the user not only be authenticated, but also have ROLE_SPITTER authority:
@Override
protected void configure(HttpSecurity http) throws Exception {
http
.authorizeRequests()
.antMatchers("/spitters/me").hasAuthority("ROLE_SPITTER")
.antMatchers(HttpMethod.POST, "/spittles")
.hasAuthority("ROLE_SPITTER")
.anyRequest().permitAll();
}
或
@Override
protected void configure(HttpSecurity http) throws Exception {
http
.authorizeRequests()
.antMatchers("/spitter/me").hasRole("SPITTER")
.antMatchers(HttpMethod.POST, "/spittles").hasRole("SPITTER")
.anyRequest().permitAll();
}
You can chain as many calls to antMatchers() , regexMatchers() , and anyRequest()
as you need to fully establish the security rules around your web application. You
should know, however, that they’ll be applied in the order given. For that reason, it’s
important to configure the most specific request path patterns first and the least spe-
cific ones (such as anyRequest() ) last. If not, then the least specific paths will trump
the more specific ones.
SPRING IN ACTION 第4版笔记-第九章Securing web applications-009-拦截请求()的更多相关文章
- SPRING IN ACTION 第4版笔记-第九章Securing web applications-011-把敏感信息请求转为https(requiresChannel())
1.把包含敏感信息的请求转为https请求,则较为安全,但如何只把有需要安全的请求转为https,而不是不加分辩就把所有请求都转为https呢?可以用requiresChannel() @Overri ...
- SPRING IN ACTION 第4版笔记-第九章Securing web applications-001-SpringSecurity简介(DelegatingFilterProxy、AbstractSecurityWebApplicationInitializer、WebSecurityConfigurerAdapter、@EnableWebSecurity、@EnableWebMvcS)
一.SpringSecurity的模块 At the least, you’ll want to include the Core and Configuration modules in your ...
- SPRING IN ACTION 第4版笔记-第九章Securing web applications-010-拦截请求
一. What if you wanted to restrict access to certain roles only on Tuesday? Using the access() method ...
- SPRING IN ACTION 第4版笔记-第九章Securing web applications-008-使用非关系型数据库时如何验证用户(自定义UserService)
一. 1.定义接口 Suppose that you need to authenticate against users in a non-relational database suchas Mo ...
- SPRING IN ACTION 第4版笔记-第九章Securing web applications-007-设置LDAP server比较密码(contextSource、root()、ldif()、)
一.LDAP server在哪 By default, Spring Security’s LDAP authentication assumes that the LDAP server is li ...
- SPRING IN ACTION 第4版笔记-第九章Securing web applications-004-对密码加密passwordEncoder
一. 1.Focusing on the authentication query, you can see that user passwords are expected to be stored ...
- SPRING IN ACTION 第4版笔记-第九章Securing web applications-003-把用户数据存在数据库
一. 1.It’s quite common for user data to be stored in a relational database, accessed via JDBC . To c ...
- SPRING IN ACTION 第4版笔记-第九章Securing web applications-002-把用户数据存在memory里(AuthenticationManagerBuilder、 UserDetailsManagerConfigurer.UserDetailsBuilder)
Spring Security is extremely flexible and is capable of authenticating users against virtually any d ...
- SPRING IN ACTION 第4版笔记-第九章Securing web applications-006-用LDAP比较密码(passwordCompare()、passwordAttribute("passcode")、passwordEncoder(new Md5PasswordEncoder()))
一. The default strategy for authenticating against LDAP is to perform a bind operation,authenticatin ...
随机推荐
- requirejs实验001.对我来说,用AMD的方式来组织代码并不轻松.
http://www.requirejs.org/ http://www.requirejs.cn/ http://requirejs.readthedocs.org/en/1.0.1/ 目录结构: ...
- Contest1065 - 第四届“图灵杯”NEUQ-ACM程序设计竞赛(个人赛)C粉丝与汉诺塔
题目描述 苟利国家生死以,岂因福祸避趋之?作为ACM真正的粉丝,应该都听闻过汉诺塔问题,汉诺塔问题是这样的: 有三根柱子,编号A,B,C柱,初始情况下A柱上有n个盘子,小盘子在上大盘子在下,n个盘子大 ...
- VS代码模板
Microsoft Visual Studio 11.0\Common7\IDE\ItemTemplates\Csharp\Code\2052\Class
- windows phone URI映射
UriMapping用于在一个较短的URI和你项目中的xaml页的完整路径定义一个映射(别名).通过使用别名URI,开发者可以在不改变导航代码的情况下来改变一个项目的内部结构.该机制还提供了一个简单的 ...
- DataGridView显示时间格式
默认显示时间不显示秒yyyy-MM-dd HH:mm dataGridView.Columns["日期时间字段"].DefaultCellStyle.Format = " ...
- PHP、Java、C#实现URI参数签名算法,确保应用与REST服务器之间的安全通信,防止Secret Key盗用、数据篡改等恶意攻击行为
简介 应用基于HTTP POST或HTTP GET请求发送Open API调用请求时,为了确保应用与REST服务器之间的安全通信,防止Secret Key盗用.数据篡改等恶意攻击行为,REST服务器使 ...
- [OpenXml] Generate excel in memory and dump to file
public static void GenerateExcelFromStream() { using (MemoryStream memoryStream = new MemoryStream() ...
- jQueryr .on方法解析
.On() 其实.bind(), .live(), .delegate()都是通过.on()来实现的,.unbind(), .die(), .undelegate(),也是一样的都是通过.off()来 ...
- mvc 之 @Html.DropDownList
Dictionary<string, string> myDic = new Dictionary<string, string>(); myDic.Add(System.DB ...
- Spark Streaming揭秘 Day26 JobGenerator源码图解
Spark Streaming揭秘 Day26 JobGenerator源码图解 今天主要解析一下JobGenerator,它相当于一个转换器,和机器学习的pipeline比较类似,因为最终运行在Sp ...
