SPRING IN ACTION 第4版笔记-第九章Securing web applications-001-SpringSecurity简介(DelegatingFilterProxy、AbstractSecurityWebApplicationInitializer、WebSecurityConfigurerAdapter、@EnableWebSecurity、@EnableWebMvcS)
一、SpringSecurity的模块

At the least, you’ll want to include the Core and Configuration modules in your application’s classpath. Spring Security is often used to secure web applications, and that’s certainly the case with the Spittr application, so you’ll also need to add the Web module. We’ll also be taking advantage of Spring Security’s JSP tag library, so you’ll need to add that module to the mix.
二、开启SpringSecurity的DelegatingFilterProxy
Spring Security employs several servlet filters to provide various aspects of security.You might be thinking that means you’ll need to configure several filters in a web.xml file, or perhaps in a WebApplicationInitializer class. But thanks to a little Spring magic, you’ll only need to configure one of those filters.
DelegatingFilterProxy is a special servlet filter that, by itself, doesn’t do much.Instead, it delegates to an implementation of javax.servlet.Filter that’s registered as a <bean> in the Spring application context, as illustrated in figure 9.1.
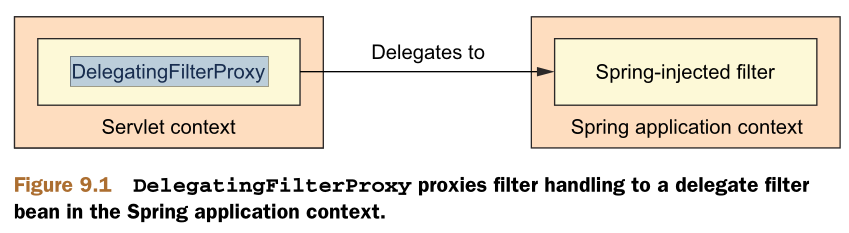
1.Java形式
If you'd rather configure DelegatingFilterProxy in Java with a WebApplicationInitializer , then all you need to do is create a new class that extends AbstractSecurityWebApplicationInitializer
package spittr.config;
import org.springframework.security.web.context.AbstractSecurityWebApplicationInitializer;
public class SecurityWebInitializer extends AbstractSecurityWebApplicationInitializer {
}
AbstractSecurityWebApplicationInitializer implements WebApplicationInitializer , so it will be discovered by Spring and be used to register DelegatingFilterProxy with the web container. Although you can override its appendFilters() or insertFilters() methods to register filters of your own choosing, you need not override anything to register DelegatingFilterProxy
2.xml形式
<filter>
<filter-name>springSecurityFilterChain</filter-name>
<filter-class>
org.springframework.web.filter.DelegatingFilterProxy
</filter-class>
</filter>
The most important thing here is that the <filter-name> be set to springSecurityFilterChain . That’s because you’ll soon be configuring Spring Security for web security, and there will be a filter bean named springSecurityFilterChain that
DelegatingFilterProxy will need to delegate to.
Whether you configure DelegatingFilterProxy in web.xml or by subclassing AbstractSecurityWebApplicationInitializer , it will intercept requests coming into the application and delegate them to a bean whose ID is springSecurityFilterChain .
As for the springSecurityFilterChain bean itself, it’s another special filter known as FilterChainProxy . It’s a single filter that chains together one or more additional filters. Spring Security relies on several servlet filters to provide different security features, but you should almost never need to know these details, as you likely won’t need to explicitly declare the springSecurityFilterChain bean or any of the filters it chains together. Those filters will be created when you enable web security.
三、编写简单的SpringSecurity配置
1.Java形式
(1)一般应用,@EnableWebSecurity
package spitter.config;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity;
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter; @Configuration
@EnableWebSecurity
public class SecurityConfig extends WebSecurityConfigurerAdapter {}
As its name suggests, the @EnableWebSecurity annotation enables web security. It is useless on its own, however. Spring Security must be configured in a bean that implements WebSecurityConfigurer or (for convenience) extends WebSecurityConfigurerAdapter . Any bean in the Spring application context that implements WebSecurityConfigurer can contribute to Spring Security configuration, but it’s often most convenient for the configuration class to extend WebSecurityConfigurerAdapter , as shown in listing 9.1. @EnableWebSecurity is generally useful for enabling security in any web application. But if you happen to be developing a Spring MVC application, you should consider using @EnableWebMvcSecurity instead
(2)SpringMVC应用@EnableWebMvcSecurity
package spitter.config;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.config.annotation.web.
configuration.WebSecurityConfigurerAdapter;
import org.springframework.security.config.annotation.web.servlet.
configuration.EnableWebMvcSecurity; @Configuration
@EnableWebMvcSecurity
public class SecurityConfig extends WebSecurityConfigurerAdapter {
}
Among other things, the @EnableWebMvcSecurity annotation configures a Spring MVC argument resolver so that handler methods can receive the authenticated user’s principal (or username) via @AuthenticationPrincipal -annotated parameters. It also configures a bean that automatically adds a hidden cross-site request forgery ( CSRF ) token field on forms using Spring’s form-binding tag library.
It may not look like much, but the security configuration class in listings 9.1 and 9.2 packs quite a punch. Either one will lock down an application so tightly that nobody can get in!
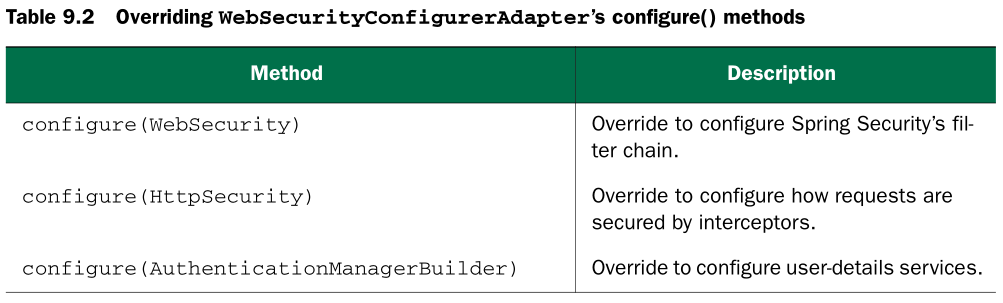
Although it’s not strictly required, you’ll probably want to specify the finer points of web security by overriding one or more of the methods from WebSecurityConfigurerAdapter . You can configure web security by overriding WebSecurity-
ConfigurerAdapter ’s three configure() methods and setting behavior on the parameter passed in. Table 9.2 describes these three methods.
四、重写WebSecurityConfigurerAdapter ’s configure()
1.
2.默认的方法如下:
protected void configure(HttpSecurity http) throws Exception {
http
.authorizeRequests()
.anyRequest().authenticated()
.and()
.formLogin().and()
.httpBasic();
}
This simple default configuration specifies how HTTP requests should be secured and what options a client has for authenticating the user. The call to authorizeRequests() and anyRequest().authenticated() demands that all HTTP requests coming into the application be authenticated. It also configures Spring Security to support authentication via a form-based login (using a predefined login page) as well as HTTP Basic.
Meanwhile, because you haven’t overridden the configure(AuthenticationManagerBuilder) method, there’s no user store backing the authentication process.With no user store, there are effectively no users. Therefore, all requests require
authentication, but there’s nobody who can log in.You’re going to need to add a bit more configuration to bend Spring Security to fit your application’s needs. Specifically, you’ll need to…
Configure a user store
Specify which requests should and should not require authentication, as well as what authorities they require
Provide a custom login screen to replace the plain default login screen In addition to these facets of Spring Security, you may also want to selectively render certain content in your web views based on security constraints.
SPRING IN ACTION 第4版笔记-第九章Securing web applications-001-SpringSecurity简介(DelegatingFilterProxy、AbstractSecurityWebApplicationInitializer、WebSecurityConfigurerAdapter、@EnableWebSecurity、@EnableWebMvcS)的更多相关文章
- SPRING IN ACTION 第4版笔记-第九章Securing web applications-011-把敏感信息请求转为https(requiresChannel())
1.把包含敏感信息的请求转为https请求,则较为安全,但如何只把有需要安全的请求转为https,而不是不加分辩就把所有请求都转为https呢?可以用requiresChannel() @Overri ...
- SPRING IN ACTION 第4版笔记-第九章Securing web applications-010-拦截请求
一. What if you wanted to restrict access to certain roles only on Tuesday? Using the access() method ...
- SPRING IN ACTION 第4版笔记-第九章Securing web applications-008-使用非关系型数据库时如何验证用户(自定义UserService)
一. 1.定义接口 Suppose that you need to authenticate against users in a non-relational database suchas Mo ...
- SPRING IN ACTION 第4版笔记-第九章Securing web applications-007-设置LDAP server比较密码(contextSource、root()、ldif()、)
一.LDAP server在哪 By default, Spring Security’s LDAP authentication assumes that the LDAP server is li ...
- SPRING IN ACTION 第4版笔记-第九章Securing web applications-004-对密码加密passwordEncoder
一. 1.Focusing on the authentication query, you can see that user passwords are expected to be stored ...
- SPRING IN ACTION 第4版笔记-第九章Securing web applications-003-把用户数据存在数据库
一. 1.It’s quite common for user data to be stored in a relational database, accessed via JDBC . To c ...
- SPRING IN ACTION 第4版笔记-第九章Securing web applications-002-把用户数据存在memory里(AuthenticationManagerBuilder、 UserDetailsManagerConfigurer.UserDetailsBuilder)
Spring Security is extremely flexible and is capable of authenticating users against virtually any d ...
- SPRING IN ACTION 第4版笔记-第九章Securing web applications-009-拦截请求()
一. 对特定的请求拦截 For example, consider the requests served by the Spittr application. Certainly, thehome ...
- SPRING IN ACTION 第4版笔记-第九章Securing web applications-006-用LDAP比较密码(passwordCompare()、passwordAttribute("passcode")、passwordEncoder(new Md5PasswordEncoder()))
一. The default strategy for authenticating against LDAP is to perform a bind operation,authenticatin ...
随机推荐
- (转) 读取xml文件转成List<T>对象的两种方法
读取xml文件,是项目中经常要用到的,所以就总结一下,最近项目中用到的读取xml文件并且转成List<T>对象的方法,加上自己知道的另一种实现方法. 就以一个简单的xml做例子. xml格 ...
- CSS笔记---文字两边对齐
<style> .box{ width: 1000px; height: 500px; background-color: #aa0000; margin:0 auto; } .teste ...
- 简介spring中MethodReplacer的用法
欢迎转载交流:个人博客地址http://www.cnblogs.com/shizhongtao/p/3468713.html org.springframework.beans.factory.sup ...
- WaitForSingleObject用法
对应函数 编辑 VC声明 DWORD WaitForSingleObject( HANDLE hHandle, DWORD dwMilliseconds ); 参数 编辑 hHandle[in]对 ...
- js异步收集
http://www.cnblogs.com/rubylouvre/archive/2011/03/18/1984336.html http://www.cnblogs.com/hustskyking ...
- antuomake 生成configure的使用
configure 作为编译配置脚本,有大量选项可供不同编译需求,这些选项直 接作用到最终生成的Makefile文件 问题:automake默认的gcc编译选项为-Wall -O2 -g,怎么改为我们 ...
- Linux系统下安装rz/sz命令及使用说明(转载)
对于经常使用Linux系统的人员来说,少不了将本地的文件上传到服务器或者从服务器上下载文件到本地,rz / sz命令很方便的帮我们实现了这个功能,但是很多Linux系统初始并没有这两个命令.今天,我们 ...
- [Linux] Linux学习笔记(5)-文件与目录管理
1.Linux目录结构为树状结构,最顶层的目录为跟目录"/",其它目录通过挂载可以将它添加到目录树中,通过解除挂载移除它们. 2.绝对路径与相对路径 绝对路径写法:由根目录&quo ...
- Dapper full example
Skip to content Sign up Sign in This repository Explore Features Enterprise Blog Watch Star , Fork S ...
- Delphi Variant oleVariant
The OleVariant type exists on both the Windows and Linux platforms. The main difference between Vari ...
