Python Ethical Hacking - Malware Packaging(2)
PACKAGING FOR WINDOWS FROM LINUX
- For best results package the program from the same OS as the target.
- EG if the target is Windows then package the program from a Windows computer with a python interpreter.
- Install Windows python interpreter on Linux.
- Use it to convert python programs to Windows executables.
Install wine tool on Kali Linux:
dpkg --add-architecture i386 && apt-get update &&
apt-get install wine32
Install Python 3.7.4 using wine.
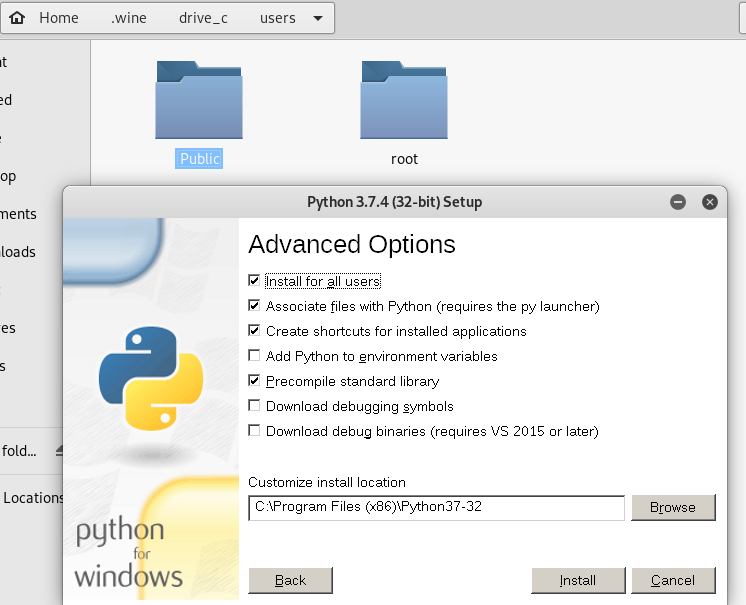
Install PyInstaller on Kali Linux.
wine python.exe -m pip install /root/Downloads/PyInstaller-3.5.tar.gz

To package the keylogger program, we need to install the pynput module first.
wine python.exe -m pip --default-time= install pynput
Convert the python program to windows executable.
wine ~/.wine/drive_c/'Program Files (x86)'/Python37-/Scripts/pyinstaller.exe zkeylogger.py --onefile --noconsole


Test the zkeylogger.exe file on the Windows 10 PC. It works perfectly.

Python Ethical Hacking - Malware Packaging(2)的更多相关文章
- Python Ethical Hacking - Malware Packaging(1)
PACKAGING Convert python program into an executable that: Packages all program files into a single e ...
- Python Ethical Hacking - Malware Packaging(4)
Converting Python Programs to Linux Executables Note: You can not execute the program on Linux by do ...
- Python Ethical Hacking - Malware Packaging(3)
Convert Python Programs to OS X Executables https://files.pythonhosted.org/packages/4a/08/6ca123073a ...
- Python Ethical Hacking - Malware Analysis(1)
WRITING MALWARE Download file. Execute Code. Send Report. Download & Execute. Execute & Repo ...
- Python Ethical Hacking - Malware Analysis(4)
DOWNLOAD_FILE Download files on a system. Once packaged properly will work on all operating systems. ...
- Python Ethical Hacking - Malware Analysis(3)
Stealing WiFi Password Saved on a Computer #!/usr/bin/env python import smtplib import subprocess im ...
- Python Ethical Hacking - Malware Analysis(2)
Filtering Command Output using Regex #!/usr/bin/env python import smtplib import subprocess import r ...
- Python Ethical Hacking - TROJANS Analysis(2)
DOWNLOAD & EXECUTE PAYLOAD A generic executable that downloads & executes files. Disadvantag ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
随机推荐
- 如何在VMware虚拟机中安装CentOS6.7系统(上篇)
之前给大家分享了在VMware中如何创建CentOS虚拟机,今天给大家分享一下如何在虚拟机中安装CentOS系统,以CentOS6.7系统为例,其他的系统版本也可以参考该教程进行类似处理,具体的流程如 ...
- 001.OpenShift介绍
一 OpenShift特性 1.1 OpenShift概述 Red Hat OpenShijft Container Platform (OpenShift)是一个容器应用程序平台,它为开发人员和IT ...
- WeChair项目Beta冲刺(8/10)
团队项目进行情况 1.昨日进展 Beta冲刺第八天 昨日进展: 前后端并行开发,项目按照计划有条不絮进行 2.今日安排 前端:扫码占座功能和预约功能并行开发 后端:扫码占座后端逻辑开发,编码使用 ...
- 代码规范与计划(Beta阶段)
这个作业属于哪个课程 软件工程 (福州大学至诚学院 - 计算机工程系) 团队名称 WeChair 这个作业要求在哪里 Beta冲刺 这个作业的目标 代码规范与计划 作业正文 如下 其他参考文献 代码规 ...
- Python 简明教程 --- 7,Python 字符串
微信公众号:码农充电站pro 个人主页:https://codeshellme.github.io 过早的优化代码是罪恶之源. -- Donald Knuth 目录 无论哪种编程语言,字符串处理都是最 ...
- 05【掌握】 SpringBoot 清空Redis所有缓存
package top.yangbuyi.system.controller; import org.springframework.beans.factory.annotation.Autowire ...
- 入门大数据---Hbase_Java_API
一.简述 截至到目前 (2019.04),HBase 有两个主要的版本,分别是 1.x 和 2.x ,两个版本的 Java API 有所不同,1.x 中某些方法在 2.x 中被标识为 @depreca ...
- 入门大数据---Python基础
前言 由于AI的发展,包括Python集成了很多计算库,所以淡入了人们的视野,成为一个极力追捧的语言. 首先概括下Python中文含义是蟒蛇,它是一个胶水语言和一个脚本语言,胶水的意思是能和多种语言集 ...
- 深入理解RocketMQ(一)---阅读源码准备
本文主要描述使用Idea获取rocketMQ源码及源码的读取. 在演示搭建源码环境前,先简要描述一下RocketMQ的设计目标. 1.架构模式 和大多数消息中间件一样,采用的是发布订阅模式,基本组件包 ...
- mackdown基础语法
目录 前言 二.Markdown基本语法 前言 由于有些语法无法在博客园展示,推荐使用Typora解锁全套,下载地址:https://www.typora.io/ Markdown是一种可以使用普通文 ...
