Ethical Hacking - GAINING ACCESS(2)
Server Side Attacks - INFORMATION GATHERING
- Need an IP address.
- Very simple if target is on the same network (netdiscover or zenmap).
- If target has a domain, then a simple ping will return its IP.
> ping www.XXXX.com
- Getting the IP is tricker if the target is a personal computer, might be useless if the target is accessing the internet through a network as the IP will be the router IP and not the targets, client side attacks are more effective in this case as reverse connetcion can be use.
INFORMATION GATHERING
- Try default password(ssh iPad case).
- Services might be mis-configured, such as the "r" service. Ports 512, 513, 514
- Some might even contain a back door!
- Code execution vulnerabilites.
CASE:
Target - Server Metasploitable
Tool - Zenmap on Kali Linux
Start the metasploit server first.(The same network with Kali Linux)
Input the target IP and click start button.
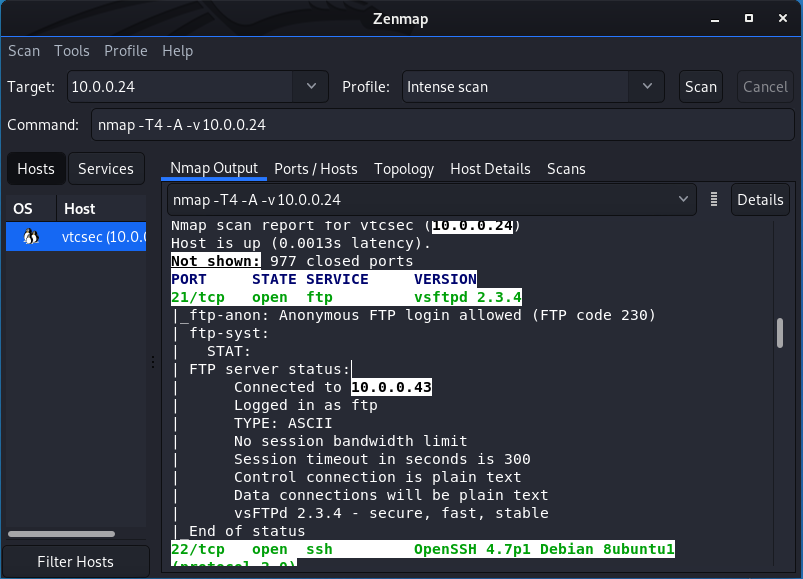
After scan is finished, we need to analyse the scan result.
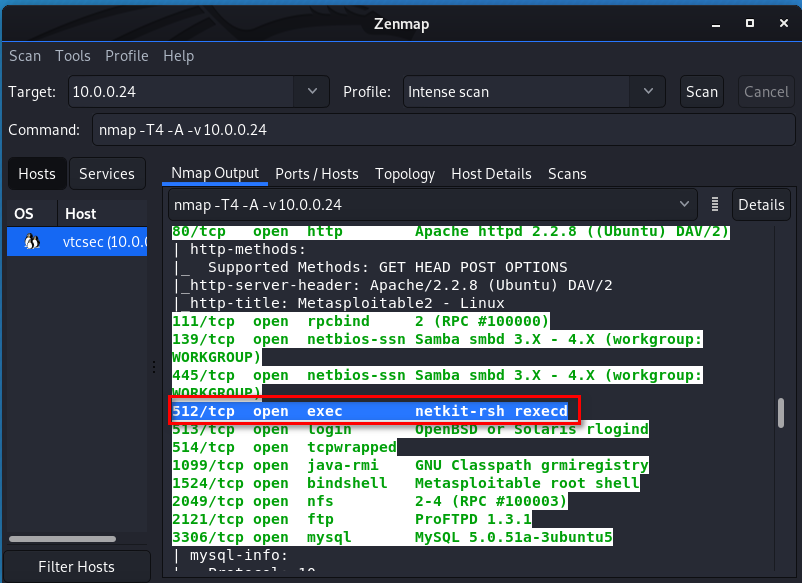
We find netkit-rsh and google it. It maybe interesting.
Install rsh-client firstly.
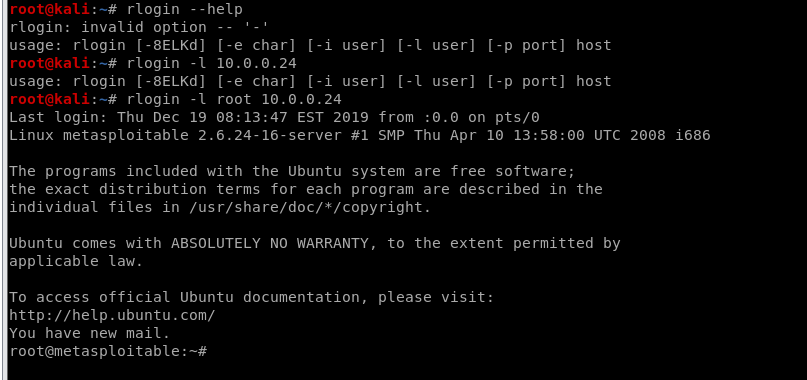
We login the target server with default account - root.
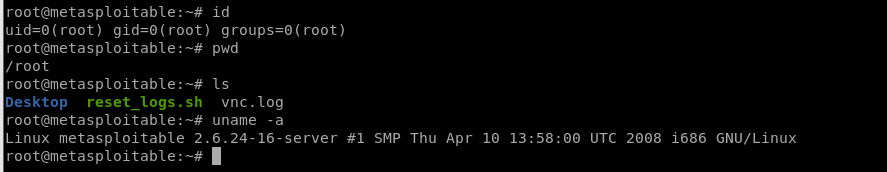
We have the root right now, so can find many useful information about this target server.
Ethical Hacking - GAINING ACCESS(2)的更多相关文章
- Ethical Hacking - GAINING ACCESS(1)
Gaining Access Introduction Everything is a computer Two main approaches (1)Server Side Do not requi ...
- Ethical Hacking - GAINING ACCESS(23)
CLIENT SIDE ATTACK - BeEF Framework Hooking targets using MITMF Tools: MITMF and BeEF Start BeEF and ...
- Ethical Hacking - GAINING ACCESS(6)
Server Side Attack Analysing scan results and exploiting target system. Go to the Analysis page and ...
- Ethical Hacking - GAINING ACCESS(24)
CLIENT SIDE ATTACKS - Detecting Trojan manually or using a sandbox Analyzing trojans Check the prope ...
- Ethical Hacking - GAINING ACCESS(22)
CLIENT SIDE ATTACKS - BeEf Framework Browser Exploitation Framework allowing us to launch a number o ...
- Ethical Hacking - GAINING ACCESS(21)
CLIENT SIDE ATTACKS - Trojan delivery method - using email spoofing Use gathered info to contract ta ...
- Ethical Hacking - GAINING ACCESS(20)
CLIENT SIDE ATTACKS - Spoofing backdoor extension Change the extension of the trojan from exe to a s ...
- Ethical Hacking - GAINING ACCESS(19)
Client-Side Attacks - Social Engineering Tool: The FAT RAT Just like Veil, it generates Undetectable ...
- Ethical Hacking - GAINING ACCESS(18)
CLIENT SIDE ATTACKS Backdooring ANY file Combine backdoor with any file - Generic solution. Users ar ...
- Ethical Hacking - GAINING ACCESS(17)
CLIENT SIDE ATTACKS - Backdooring exe' s Download an executable file first. VEIL - FRAMEWORK A backd ...
随机推荐
- 【JMeter_09】JMeter逻辑控制器__临界部分控制器<Critical Section Controller>
临界部分控制器<Critical Section Controller> 业务逻辑: 根据锁名来控制并发,同一个锁名之下,在同一时间点只能存在一个运行中,适用于控制并发的场景 锁名类型: ...
- 学习 SQL Server (5) :视图,索引,事务和锁+T_SQL
--=============== 视图的创建 =================. --create view 视图名 as 查询语句--注意:视图查询中的字段不能重名-- 视图中的数据是‘假数据’ ...
- Spring boot+Mybatisplus用AR模式实现逻辑删除操作
Mybatisplus的AR模式 Active Record(活动记录),是一种领域模型模式,特点是一个模型类对应关系型数据库中的一个表,而模型类的一个实例对应表中的一行记录.ActiveRecord ...
- python实现简单的SVM
# -*- coding: utf-8 -*- from sklearn.svm import SVC import numpy as np print(X.shape,Y.shape) X = np ...
- Python实用笔记——错误处理
让我们用一个例子来看看try的机制: try: print('try...') r = 10 / 0 print('result:', r) except ZeroDivisionError as e ...
- Nginx之upstream的四种配置方式
1.轮询(weight) 指定轮询几率,weight和访问比率成正比,用于后端服务器性能不均的情况.默认当weight不指定时,各服务器weight相同,每个请求按时间顺序逐一分配到不同的后端服务 ...
- Taro 3 正式版发布:开放式跨端跨框架解决方案
作者:凹凸曼 - yuche 从 Taro 第一个版本发布到现在,Taro 已经接受了来自于开源社区两年多的考验.今天我们很高兴地在党的生日发布 Taro 3(Taro Next)正式版,希望 Tar ...
- js写一个简单的九九乘法表
<!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8&quo ...
- 手写一个Redux,深入理解其原理
Redux可是一个大名鼎鼎的库,很多地方都在用,我也用了几年了,今天这篇文章就是自己来实现一个Redux,以便于深入理解他的原理.我们还是老套路,从基本的用法入手,然后自己实现一个Redux来替代源码 ...
- Java并发编程(06):Lock机制下API用法详解
本文源码:GitHub·点这里 || GitEE·点这里 一.Lock体系结构 1.基础接口简介 Lock加锁相关结构中涉及两个使用广泛的基础API:ReentrantLock类和Condition接 ...
