Kubernetes之dashboard
部署dashboard
$ wget https://raw.githubusercontent.com/kubernetes/dashboard/master/src/deploy/recommended/kubernetes-dashboard.yaml
#修改文件内容
默认kubernetes-dashboard是官网默认镜像地址,需要翻墙,咱们这里用阿里云的镜像就可以。
.....
spec:
containers:
- name: kubernetes-dashboard
image: registry.cn-hangzhou.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.0
imagePullPolicy: IfNotPresent
....
修改svc的类型
.....
spec:
type: NodePort
ports:
.....
启动dashboard
$ kubectl apply -f kubernetes-dashboard.yaml
查看是否启动成功
$ kubectl get pod -n kube-system
....
NAME READY STATUS RESTARTS AGE
kubernetes-dashboard-64767d465c-xgxhr / Running 17h
查看访问地址
$ kubectl get svc -n kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubernetes-dashboard NodePort 10.103.15.27 <none> :/TCP 17h
随意一个node节点加暴露端口通过https访问访问。
如何生成一个dashboard专用证书
创建一个dashboard的私钥
(umask ; openssl genrsa -out dashboard.key )
生成一个证书签署请求
openssl req -new -key dashboard.key -out dashboard.crs -subj "/O=jaxzhai/CN=dashboard"
通过ca.key和ca.crt签署证书
openssl x509 -req -in dashboard.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out dashboard.crt -days
通过签署证书创建一个sercert
kubectl create secret generic dashboard-cert -n kube-system --from-file=dashboard.crt=./dashboard.crt --from-file=dashboard.key=./dashboard.key
kubernetes-dashboard有两种认证方式,一个token认证,另一个是Kubeconfig文件的认证。这个时候的认证不是UserAccount而是获取kubernetes集群资源信息的serviceAccount,下面演示两种认证
token认证
创建一个serviceaccount并绑定集群管理员角色
$ vim serviceaccount-rbac.yaml
# ------------------- Dashboard Service Account ------------------- #
apiVersion: v1
kind: ServiceAccount
metadata:
name: dashboard-admin
namespace: kube-system
---
# -------------------Dashboard Service Account rbac ------------------- #
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRoleBinding
metadata:
name: dashboard-cluster-admin
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: dashboard-admin
namespace: kube-system $ kubectl apply -f serviceaccount-rbac.yaml
serviceaccount/dashboard-admin created
clusterrolebinding.rbac.authorization.k8s.io/dashboard-cluster-admin created
查看serviceaccount 的token
$ kubectl describe secret dashboard-admin-token-n7z7p -n kube-system
Name: dashboard-admin-token-n7z7p
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name=dashboard-admin
kubernetes.io/service-account.uid=3b1aa9ff-e25c-11e8-b8c9- Type: kubernetes.io/service-account-token Data
====
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tbjd6N3AiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiM2IxYWE5ZmYtZTI1Yy0xMWU4LWI4YzktMDA1MDU2OTMwMTI2Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.V3hE7CTjopp8QpoPsArLH5jhLiiQChbrDT88ksb8lpAKfQMKeTjqmsVKYo6Li1HxOYH85m6n6E2f6q25PDsU0hfWEWSXvVYB5vRF-wC1ty5VqcpVIBqbEZAa9kbwaEyI8PeFgDiP1v_eHXgbBRvXoEWCl1Rg5x5Tqy0ov5ezFov-ohMAiibl0q_97eKXHQKTptdzqrSak_TeB2IDywpeKJOi4jaadVA8SZDRMf7wy7NPF5gNUK39M9XmFyNk6V07sDWY8t3wRTrxZFSAY7xTJTZFy3-D49WJ9QKYRSZlAHn7UD7TJ35HnH1XbApAiR4j0yZo9mTH2aSWIkABZ3N86w
ca.crt: bytes
namespace: bytes
登录一下
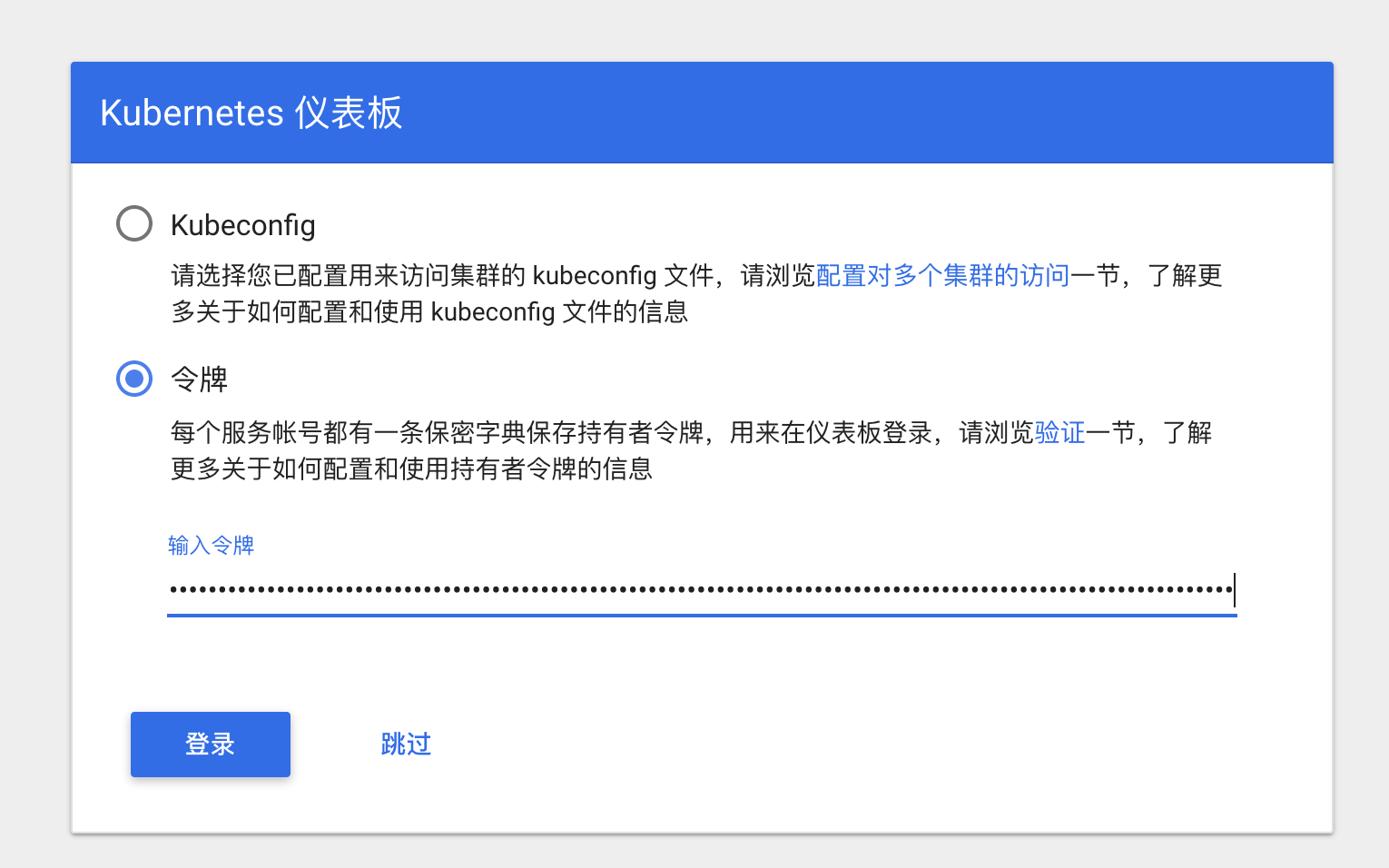
Kubeconfig文件认证
创建一个只对default命令空间有权限的账号
创建一个serviceaccount授权给admin
# ------------------- Dashboard Service Account ------------------- #
apiVersion: v1
kind: ServiceAccount
metadata:
name: def-ns-admin
namespace: default
---
# -------------------Dashboard Service Account rbac ------------------- #
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
creationTimestamp: null
name: def-ns-admin
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: admin
subjects:
- kind: ServiceAccount
name: def-ns-admin
namespace: default
创建一个kubeconfig配置文件(基于token配置)
$ kubectl config set-cluster kubernetes --certificate-authority=/etc/kubernetes/pki/ca.crt --server=https://172.16.138.44:8443 --embed-certs=true --kubeconfig=/root/dashboard/def-ns-admin.conf
查看一下证书主体
$ kubectl config view --kubeconfig=./def-ns-admin.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: REDACTED
server: https://172.16.138.44:8443
name: kubernetes
contexts: []
current-context: ""
kind: Config
preferences: {}
users: []
通过user的token认证
对token进行转码
$ DEF_NS_ADMIN_TOKEN=$(kubectl get secret def-ns-admin-token-4txrk -o jsonpath={.data.token} | base64 -d)
$ kubectl config set-credentials def-ns-admin --token=$DEF_NS_ADMIN_TOKEN --kubeconfig=/root/dashboard/def-ns-admin.conf
配置上下文
$ kubectl config set-context def-ns-admin@kubernetes --cluster=kubernetes --user=def-ns-admin --kubeconfig=./def-ns-admin.conf
查看配置文件
$ kubectl config view --kubeconfig=./def-ns-admin.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: REDACTED
server: https://172.16.138.44:8443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: def-ns-admin
name: def-ns-admin@kubernetes
current-context: ""
kind: Config
preferences: {}
users:
- name: def-ns-admin
user:
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi00dHhyayIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiJhMzA5M2ZhOC1lMjVlLTExZTgtODI1Ni0wMDUwNTY5MzRiZTciLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.TsUqPXzgqzZE2QggL_N4-LDMxw0zxeCIHuhT0_Tua8K76BXlzl1XLk0Dwvqh_MjwkJVdXRKARWjm0mA2SWIp-3vRs6TaaeKK94uMd9BtnWe-j9LPMpbll5h-DJIP1DWm0MraXAO65x-QpjlzsjUSr555rpMLSZfioWSaG4w7eHLT4XR2EoLJqtwkAKTk_zFfv3h_26eSXgul204hxO9Nde6474QUKeugdFHAFrRgmyLM4HTSKoRvo12BvD5npIIzFCN76PYXaJxEwSgKtIffuj0XyvfdvAkRmcxoGaFfbeIGYdi0nZ06u1Q0ydfkZzK1s8aE7CaxU7OV3Hp8O0MqfA
#配置当前上下文
$ kubectl config use-context def-ns-admin@kubernetes --kubeconfig=/root/dashboard/def-ns-admin.conf
#查看配置文件
$ kubectl config view --kubeconfig=/root/dashboard/def-ns-admin.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: REDACTED
server: https://172.16.138.44:8443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: def-ns-admin
name: def-ns-admin@kubernetes
current-context: def-ns-admin@kubernetes
kind: Config
preferences: {}
users:
- name: def-ns-admin
user:
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi00dHhyayIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiJhMzA5M2ZhOC1lMjVlLTExZTgtODI1Ni0wMDUwNTY5MzRiZTciLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.TsUqPXzgqzZE2QggL_N4-LDMxw0zxeCIHuhT0_Tua8K76BXlzl1XLk0Dwvqh_MjwkJVdXRKARWjm0mA2SWIp-3vRs6TaaeKK94uMd9BtnWe-j9LPMpbll5h-DJIP1DWm0MraXAO65x-QpjlzsjUSr555rpMLSZfioWSaG4w7eHLT4XR2EoLJqtwkAKTk_zFfv3h_26eSXgul204hxO9Nde6474QUKeugdFHAFrRgmyLM4HTSKoRvo12BvD5npIIzFCN76PYXaJxEwSgKtIffuj0XyvfdvAkRmcxoGaFfbeIGYdi0nZ06u1Q0ydfkZzK1s8aE7CaxU7OV3Hp8O0MqfA
登录
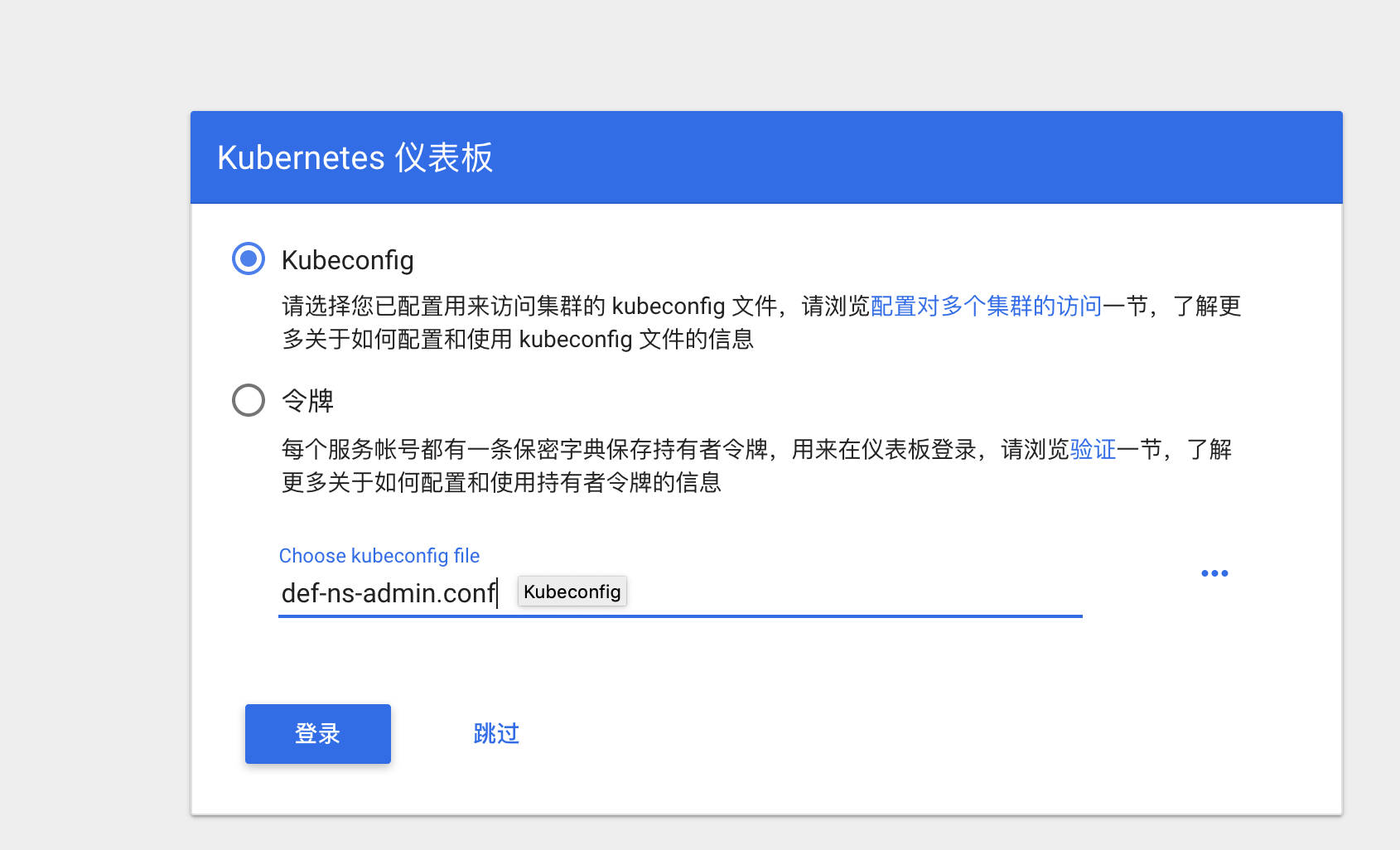
而且这里只能操作default命令空间

Kubernetes之dashboard的更多相关文章
- 一文吃透如何部署kubernetes之Dashboard
kubernetes Dashboard是什么? Dashboard是kubernetes的Web GUI,可用于在kubernetes集群上部署容器化应用,应用排错,管理集群本身及其附加的资源等,它 ...
- Kubernetes及Dashboard详细安装配置(Ubuntu14.04)
前些日子部门计划搞并行开发,需要对开发及测试环境进行隔离,所以打算用kubernetes对docker容器进行版本管理,搭建了下Kubernetes集群,过程如下: 本流程使用了阿里云加速器,配置流程 ...
- Helm 安装部署Kubernetes的dashboard
Kubernetes Dashboard 是 k8s集群的一个 WEB UI管理工具,代码托管在 github 上,地址:https://github.com/kubernetes/dashboard ...
- Kubernetes 配置管理 Dashboard(十三)
目录 一.安装配置 1.1 下载 镜像 1.2.安装 1.3.修改 NodePort 二.配置授权 Kubernetes 所有的操作我们都是通过命令行工具 kubectl 完成的.为了提供更丰富的用户 ...
- kubernetes安装dashboard步骤 【h】
本篇文章参考kubernetes---dashboardv1.8.3版本安装详细步骤及 kubernetes-dashboard(1.8.3)部署与踩坑这两篇文章,详细写了自己部署过程中的操作.遇到的 ...
- 11、kubernetes之dashboard
一.准备dashboard使用的证书 # cd /etc/kubernetes/pki/ pki]# (umask 077; openssl genrsa -out dashboard.key 204 ...
- kubernetes搭建dashboard报错
warningconfigmaps is forbidden: User "system:serviceaccount:kube-system:kubernetes-dashboard&qu ...
- Kubernetes学习之路(七)之Coredns和Dashboard二进制部署
一.CoreDNS部署 在 Cluster 中,除了可以通过 Cluster IP 访问 Service,Kubernetes 还提供了更为方便的 DNS 访问. (1)编辑coredns.yaml文 ...
- Kubernetes 1.5 配置dashboard
配置kubernetes的dashboard相对简单.同样的,只需要从源码中获取到dashboard-controller.yaml及dashboard-service.yaml文件,稍加修改即可: ...
随机推荐
- MQTT简单介绍与实现
1. MQTT 介绍它是一种 机器之间通讯 machine-to-machine (M2M).物联网 Internet of Things (IoT)常用的一种轻量级消息传输协议适用于网络带宽较低的场 ...
- js 学习之路9:运算符
1. 算数运算符 运算符 描述 例子 结果 + 加 x=y+2 x=7 - 减 x=y-2 x=3 * 乘 x=y*2 x=10 / 除 x=y/2 x=2.5 % 求余数 (保留整数) x=y%2 ...
- scrapy formRequest 表单提交
scrapy.FormRequest 主要用于提交表单数据 先来看一下源码 参数: formdata (dict or iterable of tuples) – is a dictionary ( ...
- 前端部署ant+yuicompressor文件压缩+获取版本+SSH公布(部分代码)
文件压缩: <apply executable="java" parallel="false" failonerror="true" ...
- from语法导入
"""# 在执行文件中能不能直接使用模块中的名字 # import m1# import m1 as m# print(m1.a)# print(m1.b)# print ...
- 宝塔服务器面板 部署 thinkphp5 坑
thinkphp5 在宝塔服务器上部署,出现的问题: 1. File not found. 原因: 宝塔服务器默认不支持 pathinfo 的路径访问:需要在软件 - PHP - 管理里面,安装php ...
- PHP实现部分字符隐藏
/** * 隐藏部分字符串 * # 此方法多用于手机号码或身份证号.银行卡号的中间部分数字的隐藏 */ function func_substr_replace($str, $replacement ...
- vscode 打开多个标签页
默认只打开2个,按如下设置可以支持多开: 路径C:\Users\admin\AppData\Roaming\Code\User下的settings.json添加一条配置:"workbench ...
- Windows之常用命令
1. 重启/关机 shutdown命令 #关机 shutdown -s -t -f #重启 shutdown -r -t //30秒之后,重启 00是立即 #注销 shutdown -l -t #休眠 ...
- P2023 [AHOI2009]维护序列
震惊,双倍经验,依旧是线段树的乘法修改 #include<bits/stdc++.h> using namespace std; ; struct sege_tree { int l; i ...
