Cyber Security - Palo Alto Security Policies(2)
Task 3
The SOC(Security Operation Center) monitoring team dashboard reported more 1,000 requests to one of our eCommerce Server HTTPS portals in a matter of minutes. The source address identified by our SOC came from Africa and we only serve customers in the United States, China, and Europe.
Please block access to our DMZ from all the internet but allow the USA, China, and Europe.
Configure the firewall policy. Please mind that the order of this policy may affect the effect.
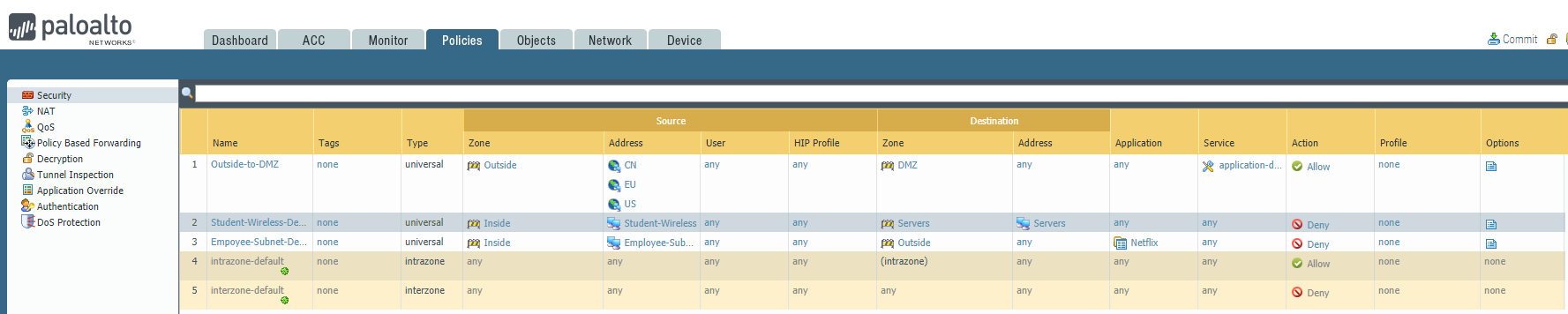

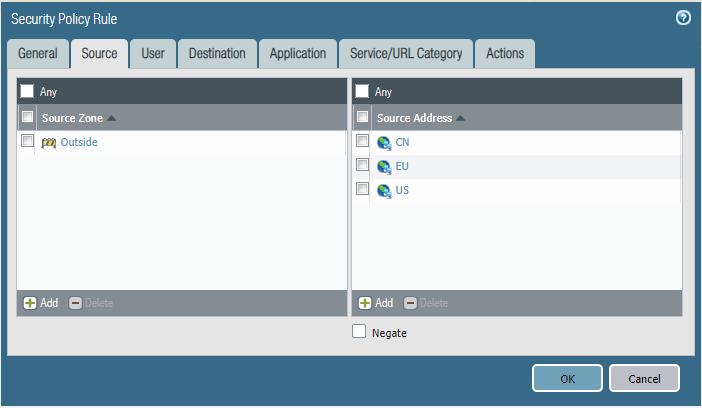
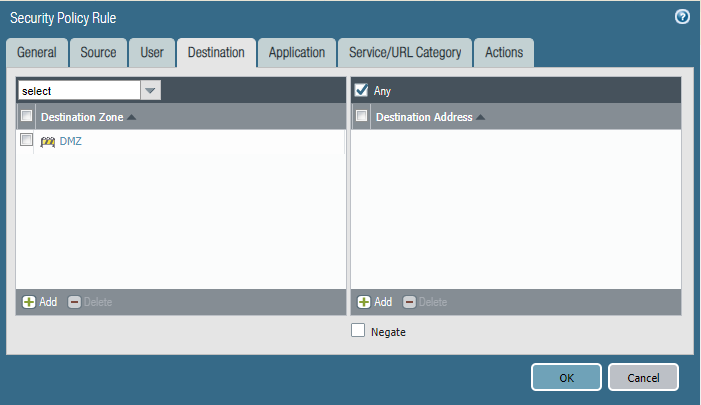

Task 4
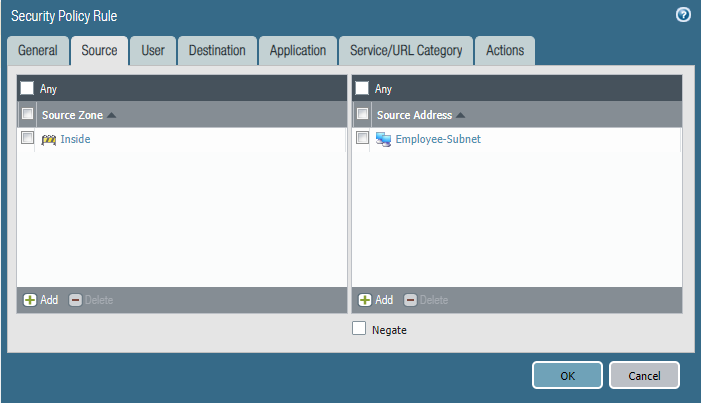
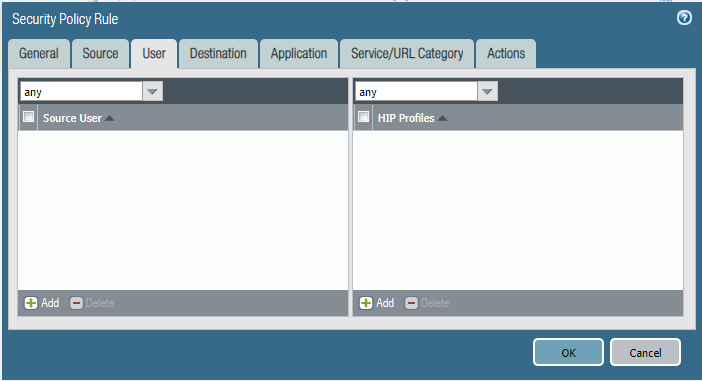
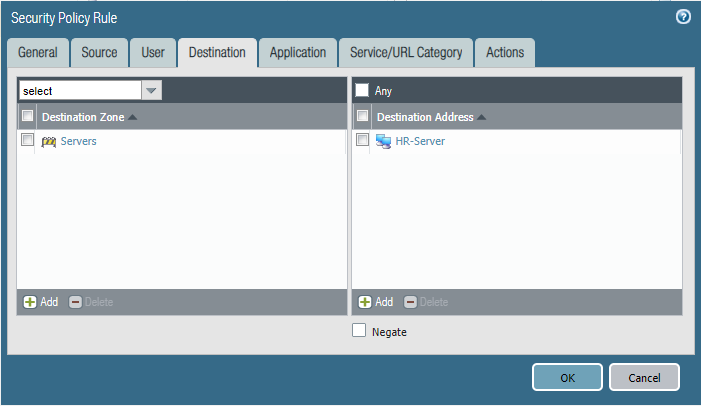
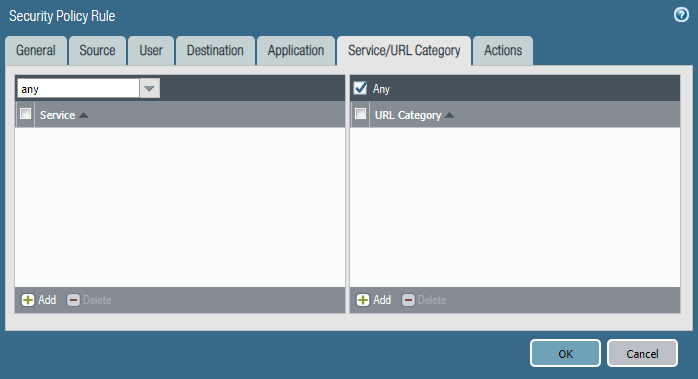
Last week after a policy change by another engineer, users from the marketing department were able to access the HR Fileserver shares.
Can you identify the root cause and remediate this issue asap?
Configure firewall policies.
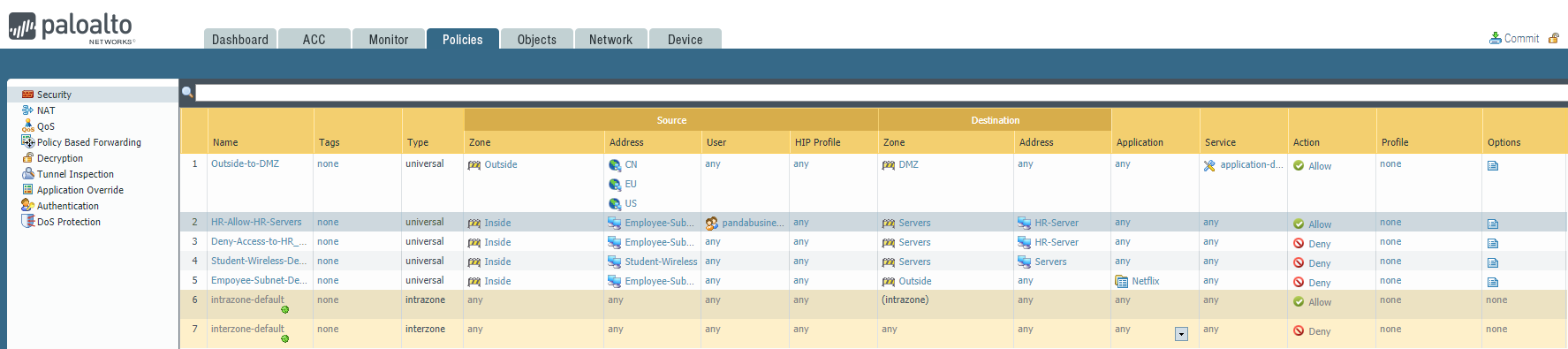
Policy one: HR-Allow-HR-Servers


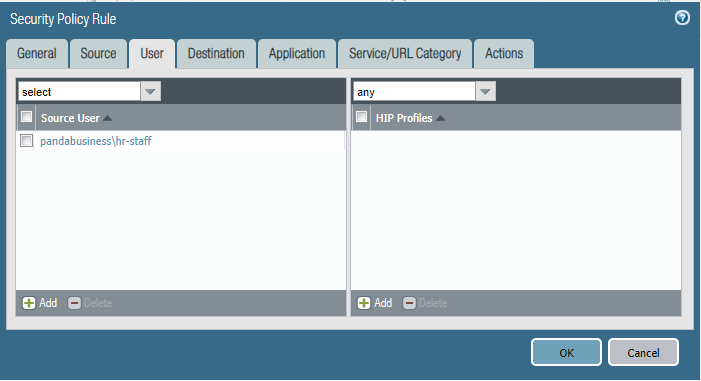
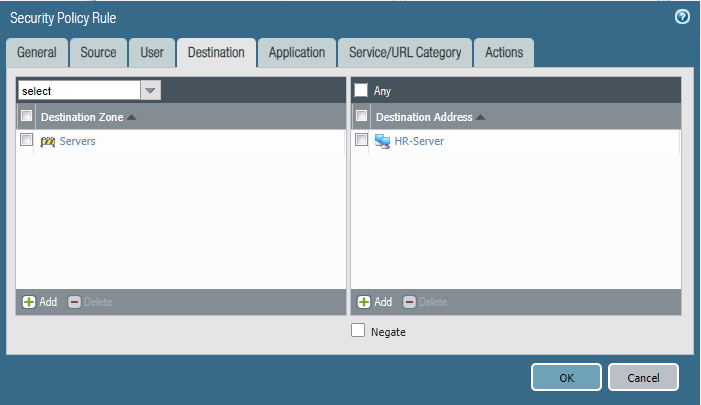
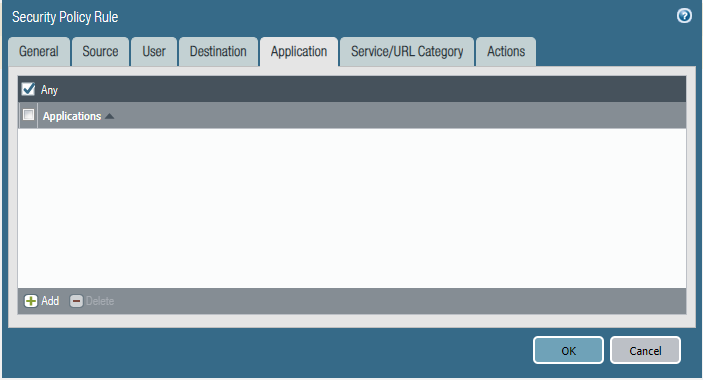
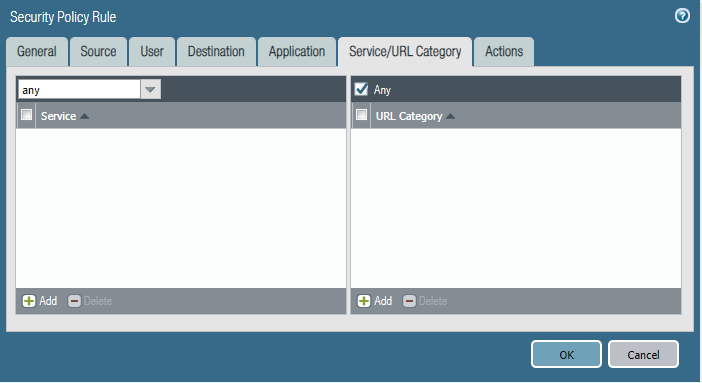

Policy Two: Deny-Access-to-HR_Servers



Cyber Security - Palo Alto Security Policies(2)的更多相关文章
- Cyber Security - Palo Alto Security Policies(1)
Security policies: Enforcing network traffic by configuring rules of what is allowed or denied to co ...
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(3)
LDAP Authentication and Remote Users and Groups Create Remote User Objects and LDAP Integration: sam ...
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(1)
Address Objects and Groups Creating address objects. Organizing address objects with address groups ...
- Cyber Security - Palo Alto Firewall Interface Types
Multiple options to integrate the Palo Alto Firewall into your: Network Layer 2 interfaces and VLAN ...
- Cyber Security - Palo Alto Firewall V-Wires
Leveraging V-Wires Bridge two physical connections and apply security Policies without influencing a ...
- Cyber Security - Palo Alto Basic Introduction
Preparation of the Lab Environment: Download and Install Pan-OS from the following website https://d ...
- Cyber Security - Palo Alto Firewall Security Zones
Firewall Security Zones Zones: The foundational aspect of every Firewall. Police network traffic Enf ...
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(2)
Users Objects and Groups Creating local user objects. Creating local user groups. https://docs.paloa ...
- Palo Alto GlobalProtect上的PreAuth RCE
0x00 前言 SSL VPN虽然可以保护企业资产免受互联网被攻击的风险影响,但如果SSL VPN本身容易受到攻击呢?它们暴露在互联网上,可以可靠并安全地连接到内网中.一旦SSL VPN服务器遭到入侵 ...
随机推荐
- 【JMeter_07】JMeter逻辑控制器__循环控制器<Loop Controller>
循环控制器<Loop Controller> 业务逻辑: 根据所填写的循环次数,对当前节点下的取样器进行响应次数的循环请求,这里可以填写变量.整数.小数.字母.负数.各种符号等: 当填写整 ...
- java-递归(文件查找)
import java.io.File; /** * @Author: heq * @Date: 2020/6/23 20:51 */ public class Test { public stati ...
- 微信开发_Exception_02_"errcode":40164,"errmsg":"invalid ip 61.172.68.219, not in whitelist hint
ip查询网址: http://www.ip.cn/ 一.异常现象 今天开始做微信开发,在办公室时能正常获取access_token,晚上回家之后获取access_token时却报出下列错误信息: {& ...
- 浅谈auth模块
目录 auth模块 什么是Auth模块 auth模块的常用方法 用户注册 扩展默认的auth_user表 auth模块 什么是Auth模块 auth模块是对注册登录认证注销修改密码等方法的一种封装 ...
- Linux中快捷生成自签名ssl证书_113资讯网
一.生成CA私钥 mkdir ca cd ca #创建私钥 (建议设置密码) openssl genrsa -des3 -out myCA.key 2048 生成CA证书 # 20 年有效期 open ...
- Java 内存分析之mat安装
有三款内存分析的工具 免费 VisualVM MAT 下载地址https://www.eclipse.org/mat/ mac 下面 under the current working directo ...
- python中的守护线程
什么是守护线程:在后台运行,为其他线程提供服务的线程成为守护线程. 为什么要引入守护线程: thread模块不支持守护线程的概念,当主线程退出时,所有的子线程都将终止,不管它们是否仍在工作, 如果你不 ...
- c语言学习笔记第三章———数据和C
B站有视频演示 本章将会讲解c语言的数据定义和使用,您将会了解int.float.double.char的含义,了解命名的规则,对c语言会有更加深刻的认识. 变量命名: 我们先讲上次视频没讲的变量命名 ...
- .Net Core微服务入门全纪录(七)——IdentityServer4-授权认证
前言 上一篇[.Net Core微服务入门全纪录(六)--EventBus-事件总线]中使用CAP完成了一个简单的Eventbus,实现了服务之间的解耦和异步调用,并且做到数据的最终一致性.这一篇将使 ...
- .NET Core使用AngleSharp网络数据采集
环境: vs2019 .net core 3.1 angleSharp winform 安装:angleSharp 有这么一本Python的书: <<Python 网络数据采集>&g ...
