Python Ethical Hacking - VULNERABILITY SCANNER(9)
Automatically Discovering Vulnerabilities Using the Vulnerability Scanner
1. Modify the run_scanner method in the scanner class.
#!/usr/bin/env python import requests
import re
from bs4 import BeautifulSoup
from urllib.parse import urljoin class Scanner:
def __init__(self, url, ignore_links):
self.session = requests.Session()
self.target_url = url
self.target_links = []
self.links_to_ignore = ignore_links def extract_links_from(self, url):
response = self.session.get(url)
return re.findall('(?:href=")(.*?)"', response.content.decode(errors='ignore')) def crawl(self, url=None):
if url == None:
url = self.target_url
href_links = self.extract_links_from(url)
for link in href_links:
link = urljoin(url, link) if "#" in link:
link = link.split("#")[0] if self.target_url in link and link not in self.target_links and link not in self.links_to_ignore:
self.target_links.append(link)
print(link)
self.crawl(link) def extract_forms(self, url):
response = self.session.get(url)
parsed_html = BeautifulSoup(response.content, features="lxml")
return parsed_html.findAll("form") def submit_form(self, form, value, url):
action = form.get("action")
post_url = urljoin(url, action)
method = form.get("method") inputs_list = form.findAll("input")
post_data = {}
for input in inputs_list:
input_name = input.get("name")
input_type = input.get("type")
input_value = input.get("value")
if input_type == "text":
input_value = value post_data[input_name] = input_value
if method == "post":
return requests.post(post_url, data=post_data)
return self.session.get(post_url, params=post_data) def run_scanner(self):
for link in self.target_links:
forms = self.extract_forms(link)
for form in forms:
print("[+] Testing form in " + link)
is_vulnerable_to_xss = self.test_xss_in_form(form, link)
if is_vulnerable_to_xss:
print("\n\n[***] XSS discovered in " + link + " in the following from")
print(form) if "=" in link:
print("\n\n[+] Testing " + link)
is_vulnerable_to_xss = self.test_xss_in_link(link)
if is_vulnerable_to_xss:
print("[***] Discovered XSS in " + link) def test_xss_in_link(self, url):
xss_test_script = "<sCript>alert('test')</scriPt>"
url = url.replace("=", "=" + xss_test_script)
response = self.session.get(url)
return xss_test_script in response.content.decode() def test_xss_in_form(self, form, url):
xss_test_script = "<sCript>alert('test')</scriPt>"
response = self.submit_form(form, xss_test_script, url)
return xss_test_script in response.content.decode()
2. Test this new automatically vulnerability scanner.
#!/usr/bin/env python import scanner target_url = "http://10.0.0.45/dvwa/"
links_to_ignore = "http://10.0.0.45/dvwa/logout.php" data_dict = {"username": "admin", "password": "password", "Login": "submit"} vuln_scanner = scanner.Scanner(target_url, links_to_ignore)
vuln_scanner.session.post("http://10.0.0.45/dvwa/login.php", data=data_dict) vuln_scanner.crawl()
vuln_scanner.run_scanner()
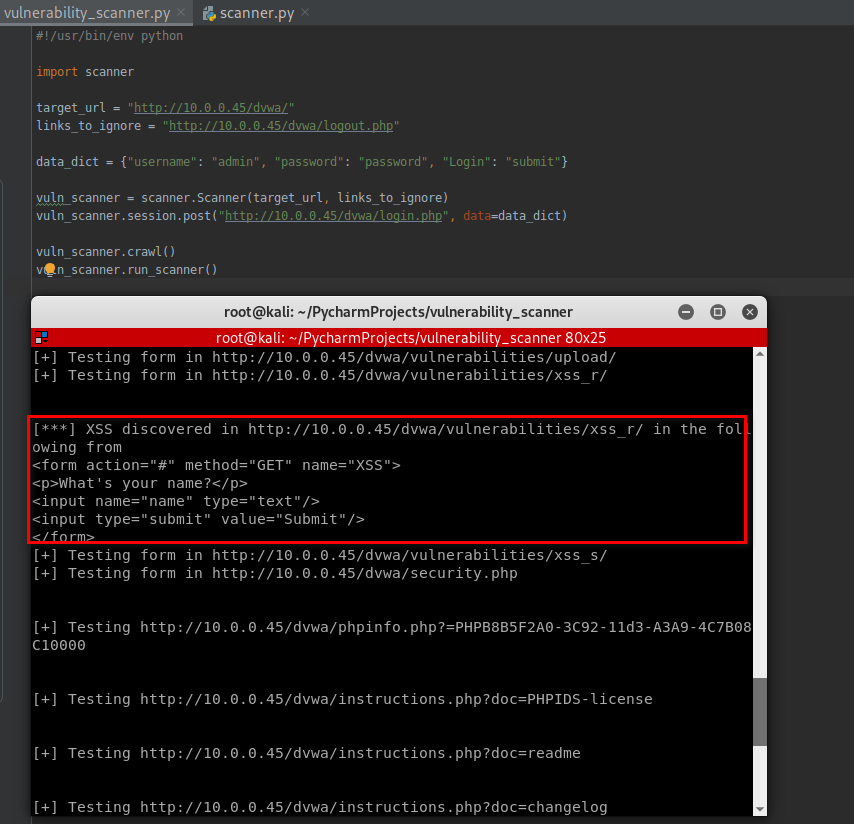
Following is the full test result.
root@kali:~/PycharmProjects/vulnerability_scanner# python3 vulnerability_scanner.py
http://10.0.0.45/dvwa/dvwa/css/main.css
http://10.0.0.45/dvwa/favicon.ico
http://10.0.0.45/dvwa/instructions.php
http://10.0.0.45/dvwa/setup.php
http://10.0.0.45/dvwa/vulnerabilities/brute/
http://10.0.0.45/dvwa/vulnerabilities/exec/
http://10.0.0.45/dvwa/vulnerabilities/csrf/
http://10.0.0.45/dvwa/vulnerabilities/fi/?page=include.php
http://10.0.0.45/dvwa/vulnerabilities/sqli/
http://10.0.0.45/dvwa/vulnerabilities/sqli_blind/
http://10.0.0.45/dvwa/vulnerabilities/upload/
http://10.0.0.45/dvwa/vulnerabilities/xss_r/
http://10.0.0.45/dvwa/vulnerabilities/xss_s/
http://10.0.0.45/dvwa/security.php
http://10.0.0.45/dvwa/phpinfo.php
http://10.0.0.45/dvwa/phpinfo.php?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000
http://10.0.0.45/dvwa/about.php
http://10.0.0.45/dvwa/instructions.php?doc=PHPIDS-license
http://10.0.0.45/dvwa/instructions.php?doc=readme
http://10.0.0.45/dvwa/instructions.php?doc=changelog
http://10.0.0.45/dvwa/instructions.php?doc=copying
http://10.0.0.45/dvwa/security.php?phpids=on
http://10.0.0.45/dvwa/security.php?phpids=off
http://10.0.0.45/dvwa/security.php?test=%22><script>eval(window.name)</script>
http://10.0.0.45/dvwa/ids_log.php
[+] Testing form in http://10.0.0.45/dvwa/setup.php
[+] Testing form in http://10.0.0.45/dvwa/vulnerabilities/brute/
[+] Testing form in http://10.0.0.45/dvwa/vulnerabilities/exec/
[+] Testing form in http://10.0.0.45/dvwa/vulnerabilities/csrf/ [+] Testing http://10.0.0.45/dvwa/vulnerabilities/fi/?page=include.php
[+] Testing form in http://10.0.0.45/dvwa/vulnerabilities/sqli/
[+] Testing form in http://10.0.0.45/dvwa/vulnerabilities/sqli_blind/
[+] Testing form in http://10.0.0.45/dvwa/vulnerabilities/upload/
[+] Testing form in http://10.0.0.45/dvwa/vulnerabilities/xss_r/ [***] XSS discovered in http://10.0.0.45/dvwa/vulnerabilities/xss_r/ in the following from
<form action="#" method="GET" name="XSS">
<p>What's your name?</p>
<input name="name" type="text"/>
<input type="submit" value="Submit"/>
</form>
[+] Testing form in http://10.0.0.45/dvwa/vulnerabilities/xss_s/
[+] Testing form in http://10.0.0.45/dvwa/security.php [+] Testing http://10.0.0.45/dvwa/phpinfo.php?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000 [+] Testing http://10.0.0.45/dvwa/instructions.php?doc=PHPIDS-license [+] Testing http://10.0.0.45/dvwa/instructions.php?doc=readme [+] Testing http://10.0.0.45/dvwa/instructions.php?doc=changelog [+] Testing http://10.0.0.45/dvwa/instructions.php?doc=copying
[+] Testing form in http://10.0.0.45/dvwa/security.php?phpids=on [+] Testing http://10.0.0.45/dvwa/security.php?phpids=on
[+] Testing form in http://10.0.0.45/dvwa/security.php?phpids=off [+] Testing http://10.0.0.45/dvwa/security.php?phpids=off
[+] Testing form in http://10.0.0.45/dvwa/security.php?test=%22><script>eval(window.name)</script> [+] Testing http://10.0.0.45/dvwa/security.php?test=%22><script>eval(window.name)</script>
[+] Testing form in http://10.0.0.45/dvwa/ids_log.php
You can add new methods in the scanner class to find more vulnerabilities.
Python Ethical Hacking - VULNERABILITY SCANNER(9)的更多相关文章
- Python Ethical Hacking - VULNERABILITY SCANNER(7)
VULNERABILITY_SCANNER How to discover a vulnerability in a web application? 1. Go into every possibl ...
- Python Ethical Hacking - VULNERABILITY SCANNER(4)
Extracting & Submitting Forms Automatically Target website:http://10.0.0.45/dvwa/vulnerabilities ...
- Python Ethical Hacking - VULNERABILITY SCANNER(2)
VULNERABILITY_SCANNER How to discover a vulnerability in a web application? 1. Go into every possibl ...
- Python Ethical Hacking - VULNERABILITY SCANNER(8)
Implementing Code To Discover XSS in Parameters 1. Watch the URL of the XSS reflected page carefully ...
- Python Ethical Hacking - VULNERABILITY SCANNER(3)
Polish the Python code using sending requests in a session Class Scanner. #!/usr/bin/env python impo ...
- Python Ethical Hacking - VULNERABILITY SCANNER(1)
HTTP REQUESTS BASIC INFORMATION FLOW The user clicks on a link. HTML website generates a request(cli ...
- Python Ethical Hacking - VULNERABILITY SCANNER(6)
EXPLOITATION - XSS VULNS EXPLOITING XSS Run any javascript code. Beef framework can be used to hook ...
- Python Ethical Hacking - VULNERABILITY SCANNER(5)
EXPLOITATION - XSS VULNS XSS - CROSS SITE SCRIPTING VULNS Allow an attacker to inject javascript cod ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
随机推荐
- c++逻辑与或非优先级
按优先级从高到低排列:!.&&.||,!的优先级最高,&&的优先级居中,||的优先级最低.
- 详述@Responsebody和HTTP异步请求的关系
Map.ModelAndView.User.List等对象都可以作为返回值.上述这两种对象都可以使用此注解.使用此注解即表示是在同一次请求的响应体里返回.浏览器以异步http的方式来接收.比如后端的M ...
- java 基本类型详解 及 常见问题
鄙人不才,基础不好,趁着闲时简单学习一下,仅作学习分享,如有不正确地方还请各位看客不吝指出. 常用的基本类型有:byte(8).short(16).char(16,取值从0-65535[2^16-1] ...
- 入门大数据---Spark_Streaming整合Kafka
一.版本说明 Spark 针对 Kafka 的不同版本,提供了两套整合方案:spark-streaming-kafka-0-8 和 spark-streaming-kafka-0-10,其主要区别如下 ...
- npm安装加速
1.通过config命令 npm config set registry https://registry.npm.taobao.org npm info underscore (如果上面配置正确这个 ...
- Redis系列(九):数据结构Hash之HDEL、HEXISTS、HGETALL、HKEYS、HLEN、HVALS命令
1.HDEL 从 key 指定的哈希集中移除指定的域.在哈希集中不存在的域将被忽略. 如果 key 指定的哈希集不存在,它将被认为是一个空的哈希集,该命令将返回0. 时间复杂度:O(N) N是被删除的 ...
- 【CSGRound1】天下第一 题解
[CSGRound1]天下第一 https://www.luogu.com.cn/problem/P5635 分析题目: 题目中说明,有T组数据,但是mod只有一个.很显然,这道题可以用记忆化搜索嘛! ...
- AdminLTE 2.4
https://jeesite.gitee.io/front/AdminLTE/2.4/index2.html
- 【秒懂Java】【02_搭建开发环境】01_Java开发必备
这篇文章主要讲解:要想使用Java来开发软件,需要做哪些准备工作? 配置电脑 作为一名开发人员,对文件的类型.大小等信息是比较敏感的,所以建议你的电脑做2个配置: 显示文件扩展名 文件扩展名(File ...
- 一个JSON解构赋值给另一个字段不同的JSON
往数据里添加JSON字符串 // 往数据里添加JSON字符串 var arr = []; var json ={"name":"liruilong"," ...
