Ethical Hacking - NETWORK PENETRATION TESTING(13)
Nmap
Nmap is a network discovery tool that can be used to gather detailed information about any client or network.
We shall have a look at some of its uses to discover connected clients and gather information about them.
We are going to use Zenmap - the GUI for Namp.
1. Ping scan: Very quick - only shows connected clients.

2. Quick scan plus: Quick - shows MAC and open clients.
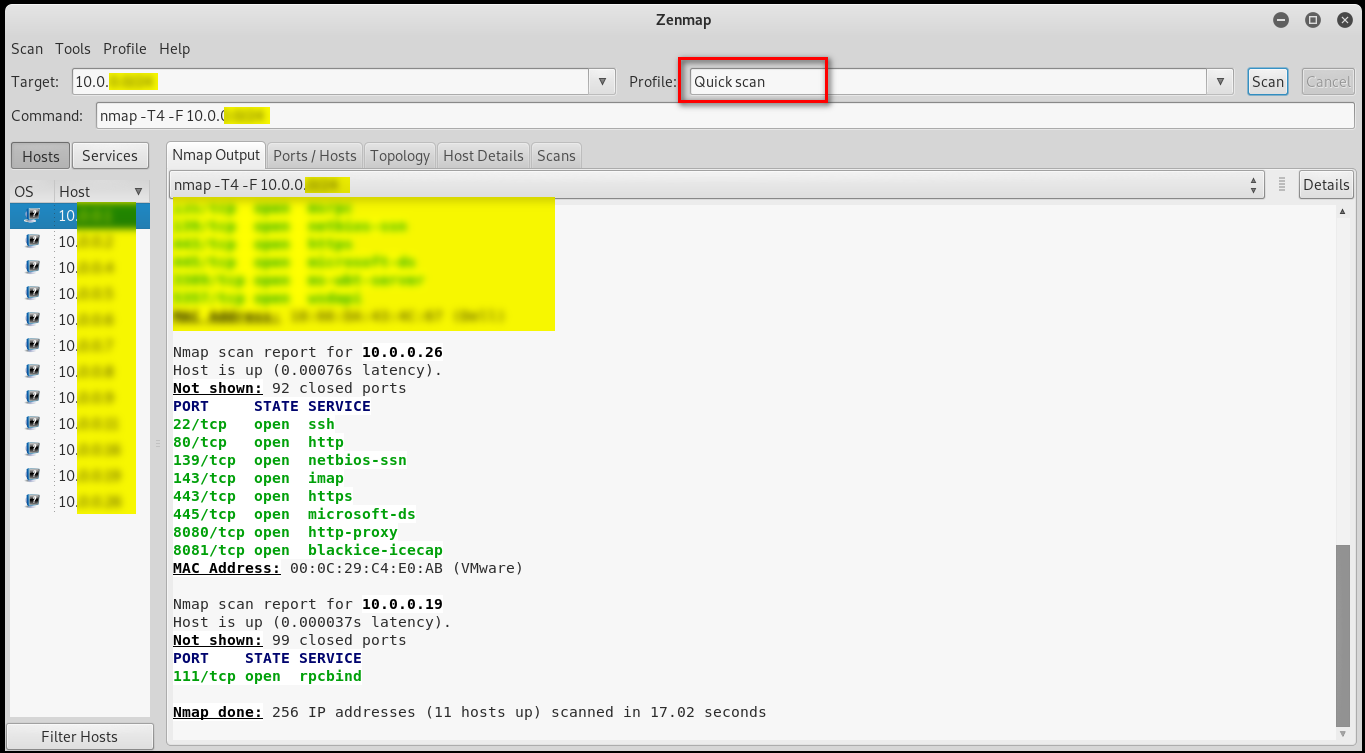
3. Quick scan plus: Slower than the 2 above, more detailed info.

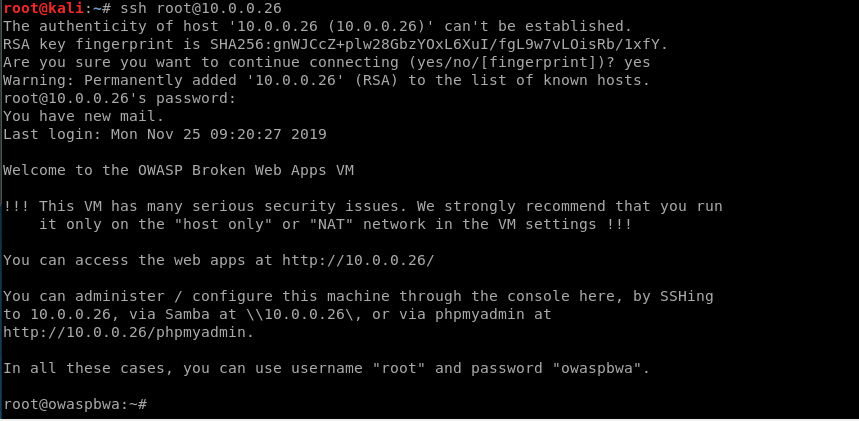
Many people are too lazy to change the password, so I log in to the target victim pc through default username/password.
Ethical Hacking - NETWORK PENETRATION TESTING(13)的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - Web Penetration Testing(13)
OWASP ZAP(ZED ATTACK PROXY) Automatically find vulnerabilities in web applications. Free and easy to ...
- Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark WIreshark is a network protocol analyser that is designed to help network administa ...
- Ethical Hacking - NETWORK PENETRATION TESTING(14)
MITM - ARP Poisoning Theory Man In The Middle Attacks - ARP Poisoning This is one of the most danger ...
- Ethical Hacking - NETWORK PENETRATION TESTING(12)
Post Connection Attacks Sophisticated attacks that can be used after connecting to the target AP. Ga ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
- Ethical Hacking - NETWORK PENETRATION TESTING(10)
WPA Craking WPA was designed to address the issues in WEP and provide better encryption. The main is ...
- Ethical Hacking - NETWORK PENETRATION TESTING(8)
WEP Cracking Basic case Run airdump-ng to log all traffic from the target network. airodump-ng --cha ...
- Ethical Hacking - NETWORK PENETRATION TESTING(7)
Gaining Access to encrypted networks Three main encryption types: 1. WEP 2.WPA 3.WPA2 WEP Cracking W ...
随机推荐
- 使用IDEA+Gradle构建Spring5源码并调试(手把手教程全图解)
一.前言 说一说我要写这篇文章的初衷吧,前段时间有小伙伴在微信群求教怎样构建spring源码,他在网上找了n个教程跟着后面花了两天时间都没构建好,正好我最近因工作原因从mac换成windows,开 ...
- GitHub 热点速览 Vol.25:距离优雅编程你差个它
作者:HelloGitHub-小鱼干 摘要:如何优雅地夸一个程序员呢?vscode-rainbow-fart 作为一个彩虹屁的项目,深得程序员心,能在你编程时疯狂称赞你的除了你自己,还有它.除了鼓励之 ...
- elk3
视频来自: bootstrap.memory_lock要设置为true,默认使用物理内存 mini_mum_nodes:1表示es集群中最小的matser节点数目,默认就是1,当es集群数目较少的时候 ...
- 利用EasyMock生成数据库连接简单测试示例
package demo.mock; import java.sql.Connection; import java.sql.PreparedStatement; import java.sql.Re ...
- 【Python3爬虫】模拟实现小牛在线登录过程
一.站点分析 小牛在线的登录入口地址为:https://www.xiaoniu88.com/user/login. 用户登录时除了需要输入用户名和密码,还要输一个验证码.我们可以先任意输入一个用户名. ...
- postman不能启动的问题解决
1.postman启动不了,启动时提示“postman resolving transporter buffer”,不能正常启动 第一步,删除:在chrome-更多工具-扩展程序里面删除了postma ...
- 洛谷 P1314 【聪明的质监员】
二分 思路: 这道题思路还是蛮好想的,一开始想的是暴力枚举w,然后再仔细一看,w增长时,y肯定减小,那么思路出来了: 二分 但是在时二分时,分得是左右端点lr,做错了 求出w的上下界,然后二分 只二分 ...
- C program Language 'EOF' and 'getchar()'
#include <stdio.h> void main() { int c; c=getchar(); while(c!=EOF) { putchar(c); c=getchar(); ...
- ORA-04063: package body "DBSNMP.BSLN" has errors
ORA-04063: package body "DBSNMP.BSLN" has errors 问题描述: 警告日志出现报错: Sun Jun 28 00:00:01 2020 ...
- Oracle 11gR2 待定的统计信息(Pending Statistic)
Oracle 11gR2 待定的统计信息(Pending Statistic) 官档最权威: 发布优化器统计信息的用户界面 管理已发布和待处理的统计信息 实验先拖着.
