Cyber Security - Palo Alto Security Policies(1)
Security policies:
- Enforcing network traffic by configuring rules of what is allowed or denied to communicate between logical network segments (zones)
- Traffic can be policed with the following parameters:
- IP Address (source and/or destination)
- Users
- Services(ports)
- Applications

(From Packt)
- Enforcement hierarchy:
- Is essential to understand the security policy order of enforcement to avoid policy overruling
- "A clean policy table limits the possibility of policy overruling"
Task 1
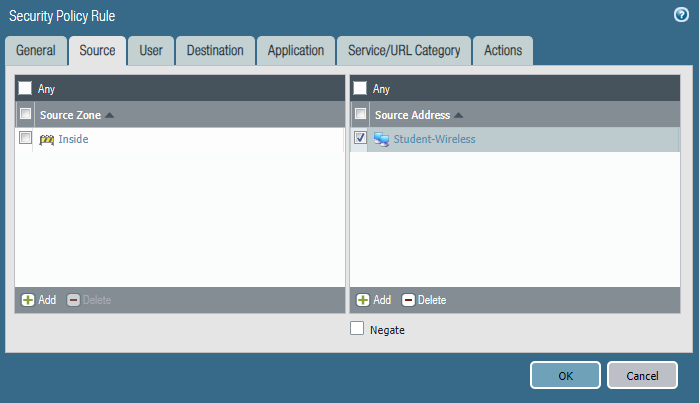
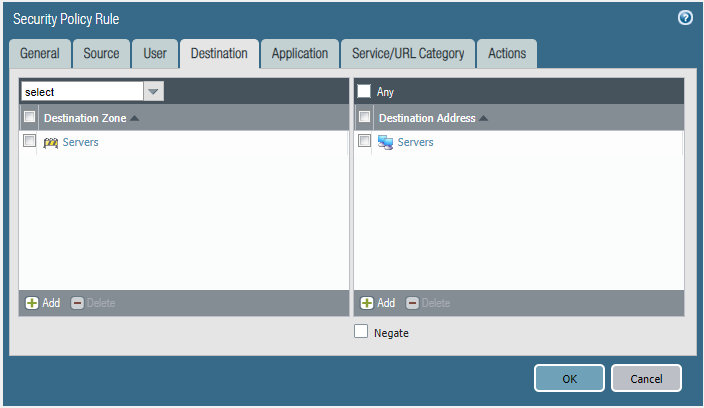
Please block the student wireless network from reaching the server subnet.
Source Zone Source Address Student Wireless: 10.10.0.0/22 Server Subnet: 10.30.0.0/23 Destination Zone Destination Address
Configure the firewall policy.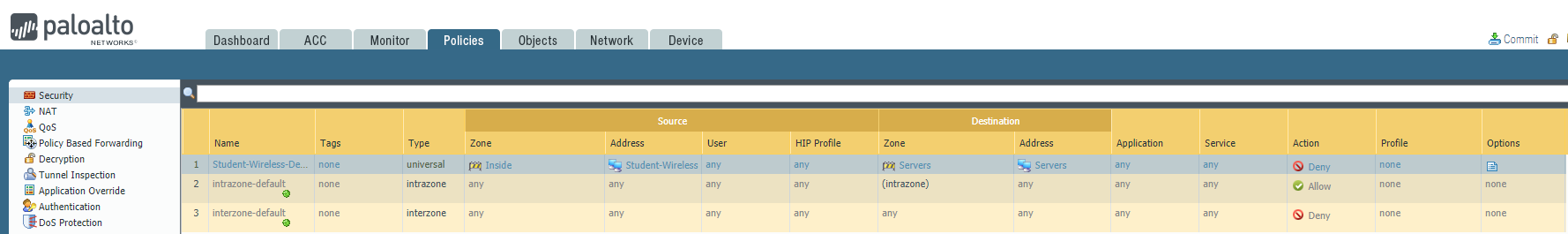


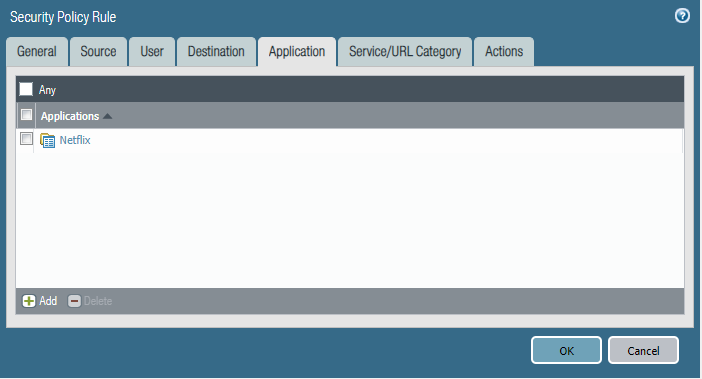
Task 2
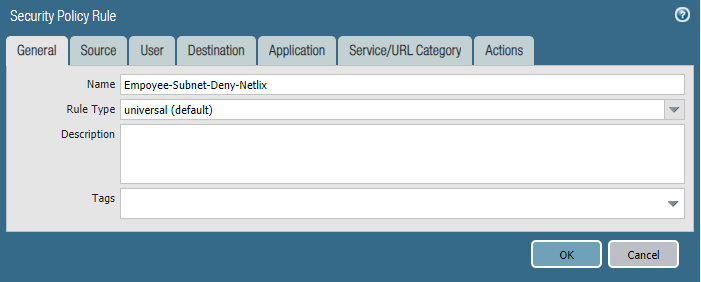
We are getting complaints of employees watching Netflix during work hours and it's causing our internet connection to crawl.
- Please block the employee subnet 10.25.0.0/23 from accessing Netflix.
Configure the firewall policy.


Cyber Security - Palo Alto Security Policies(1)的更多相关文章
- Cyber Security - Palo Alto Security Policies(2)
Task 3 The SOC(Security Operation Center) monitoring team dashboard reported more 1,000 requests to ...
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(3)
LDAP Authentication and Remote Users and Groups Create Remote User Objects and LDAP Integration: sam ...
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(1)
Address Objects and Groups Creating address objects. Organizing address objects with address groups ...
- Cyber Security - Palo Alto Firewall Interface Types
Multiple options to integrate the Palo Alto Firewall into your: Network Layer 2 interfaces and VLAN ...
- Cyber Security - Palo Alto Firewall V-Wires
Leveraging V-Wires Bridge two physical connections and apply security Policies without influencing a ...
- Cyber Security - Palo Alto Basic Introduction
Preparation of the Lab Environment: Download and Install Pan-OS from the following website https://d ...
- Cyber Security - Palo Alto Firewall Security Zones
Firewall Security Zones Zones: The foundational aspect of every Firewall. Police network traffic Enf ...
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(2)
Users Objects and Groups Creating local user objects. Creating local user groups. https://docs.paloa ...
- Palo Alto GlobalProtect上的PreAuth RCE
0x00 前言 SSL VPN虽然可以保护企业资产免受互联网被攻击的风险影响,但如果SSL VPN本身容易受到攻击呢?它们暴露在互联网上,可以可靠并安全地连接到内网中.一旦SSL VPN服务器遭到入侵 ...
随机推荐
- 开源一款超实用的 Dubbo 测试工具,已用半年,感觉很有feel~
不知道你是否在工作中有遇到过类似情况: dubbo接口调试复杂,需要通过telnet命令或者通过consumer调用来触发. telnet语句参数格式复杂,每次编写都要小心谨慎,一旦出错又需重来. 复 ...
- vc6.0创建文件时,出现很多烫烫烫解决方法
vc6.0创建文件时,出现很多烫烫烫烫解决方法 SWM2烫烫烫烫烫烫烫烫烫烫烫烫烫烫烫烫烫烫烫烫烫烫.IA 如果项目文件放在桌面上 如:C:\Documents and Settings\txwtec ...
- 团队Github实践训练
这个作业属于哪个课程 软件工程 (福州大学至诚学院 - 计算机工程系) 团队名称 WeChair 这个作业要求在哪里 团队Github实践训练 这个作业的目标 通过github实现团队协作编码 作业正 ...
- 键盘侠Linux干货| 使用SSH方式推送文件至github仓库
前言 作为一名优秀的计算机从业人员,相信大家github应该都知道吧.(优秀的代码托管工具) 但是由于平常使用的https方式克隆的本地仓库,每次git push时都需要输入帐号密码才能将我们修改的文 ...
- localStorage. sessionStorage、 Cookie不共同点:(面试题)
●存储大小的不同: localStorage的大小一般为5M sessionStorage的大小一般为5M cookies的大小一般为4K ●有效期不同: 1.localStorage的有效期为永久有 ...
- vipkid 面试经历
今天下午去了位于钟鼓楼旁边的 vipkid 研发部进行了面试,面试过程中的回答只能说一般,面试官问的问题大概分为: 实际项目的设计问题 mysql的使用优化问题 多线程与锁的问题 JVM底层原理的问题 ...
- android自定义控件onLayout方法
onLayout设置子控件的位置,对应一些普通的控件例如Button.TextView等控件,不存在子控件,所以可以不用复写该方法. 向线性布局.相对布局等存在子控件,可以覆写该方法去控制子控件的位置 ...
- Codeforces Round #652 (Div. 2) 总结
A:问正n边形的一条边和x轴平行的时候有没有一条边和y轴重合,直接判断n是否是4的倍数 #include <iostream> #include <cstdio> #inclu ...
- 《UNIX环境高级编程》(APUE) 笔记第一章 - UNIX基础知识
1 - UNIX基础知识 Github 地址 1. 操作系统 可将操作系统定义为一种软件,它控制计算机硬件资源,提供程序运行环境.通常将这种软件称为 内核 (kernel) .( Linux 是 GN ...
- 记一次WIN10 WLAN消失修复
事故现场:在win10自动更新后 在网路和Internet中WLAN消失 无法发现wifi了 设备管理器中wireless驱动上有黄色感叹号 解决办法: 右键有感叹号的wireless驱动,选择属性, ...
