Cyber Security - Palo Alto Basic Introduction
Preparation of the Lab Environment:
Download and Install Pan-OS from the following website https://docs.gns3.com/appliances/pan-vm-fw.html or https://me.csdn.net/download/hotbrandon

URL https://IP
Default Username/Password: admin/admin
PAN-OS 8 Configuration Tabs:
- Object tab: Configure Firewall objects(address - services - object groups)
- Policy tab: Configure Firewall policies(security -NAT -QoS - PBR)
- Network tab: Configure Firewall interfaces and routing settings
- Device tab: Perform maintenance tasks and administrative tasks.
- Configuration backup and restore.
- High availability.
- Users and administrators.
- Directory synchronization(Active Directory)
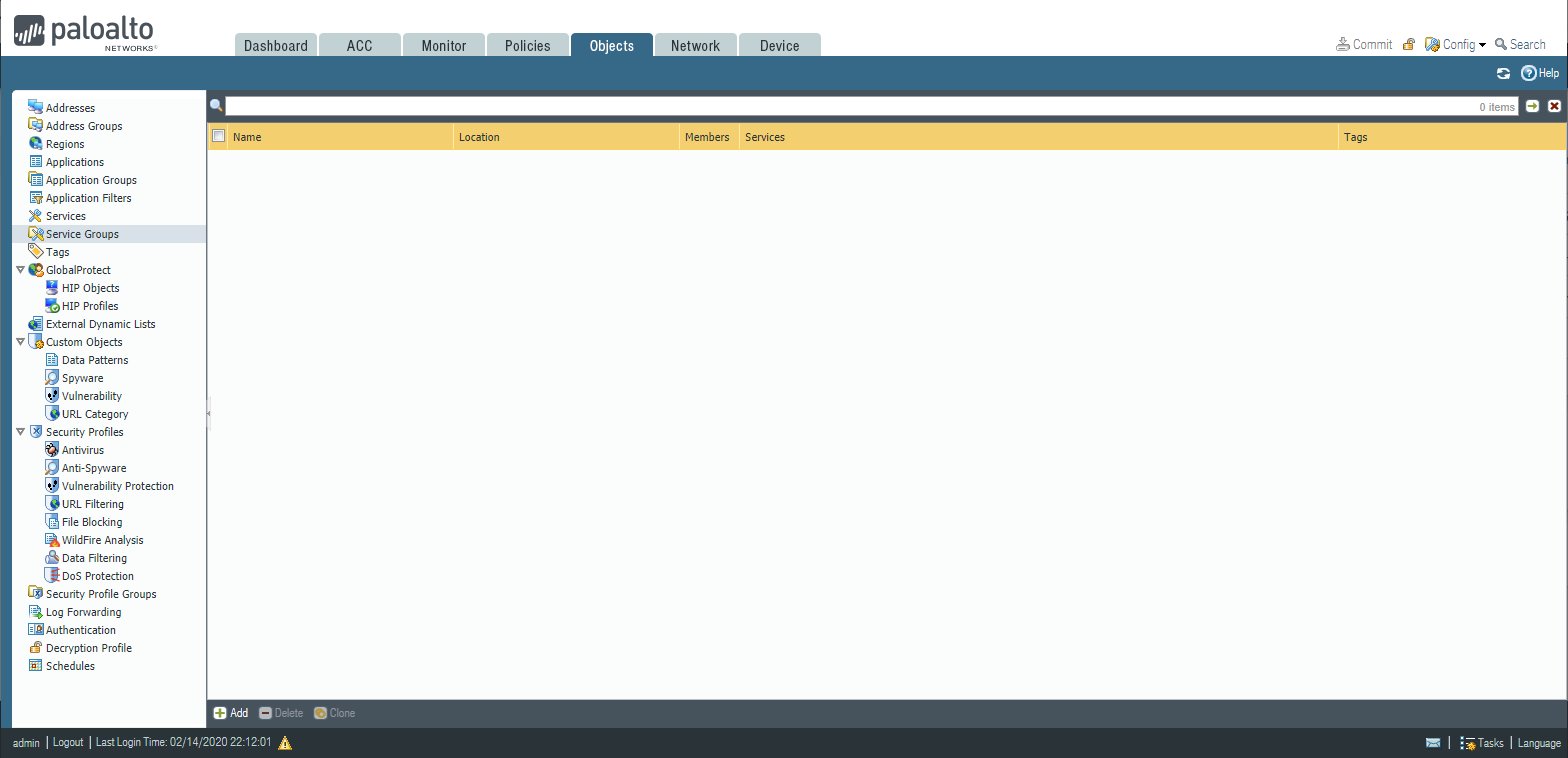
PAN-OS 8 Monitoring Tabs:
- ACC Tab: Application command center overview
- Monitor tab: User traffic monitoring based on applied policies
Dashboard:
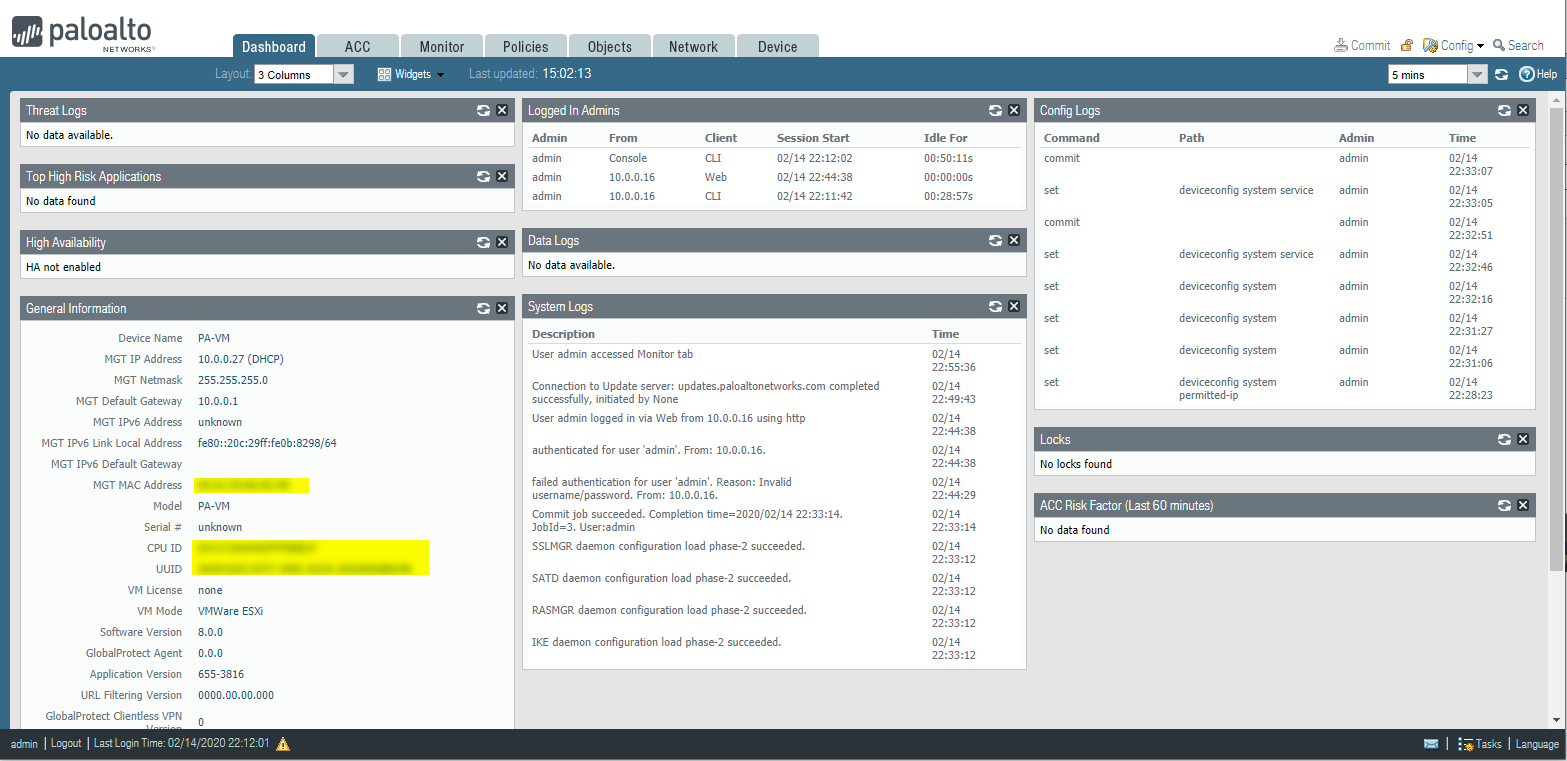
Console - Based Administration
Action commands - show, request, test, configure
CLI structure:{action}{section}{element}
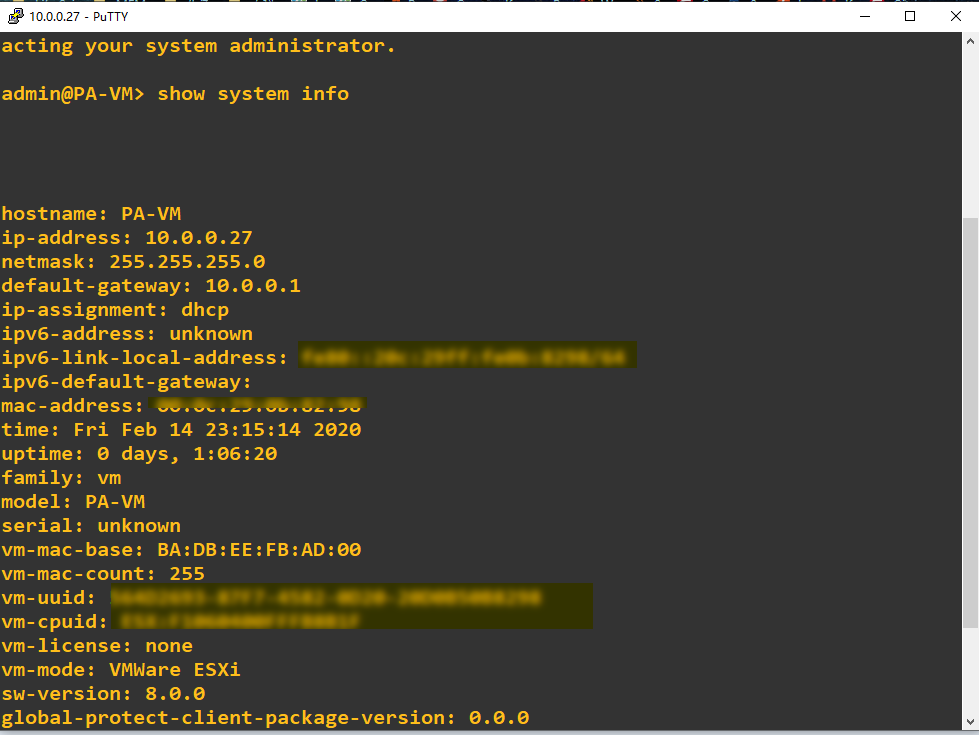
show:
show system info
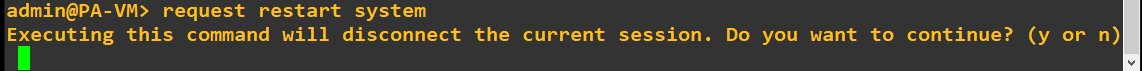
request:
request system restart
Test:
test vpn ike-sa gateway {name}
test vpn ipsec-sa gateway {name}
Device Management Overview
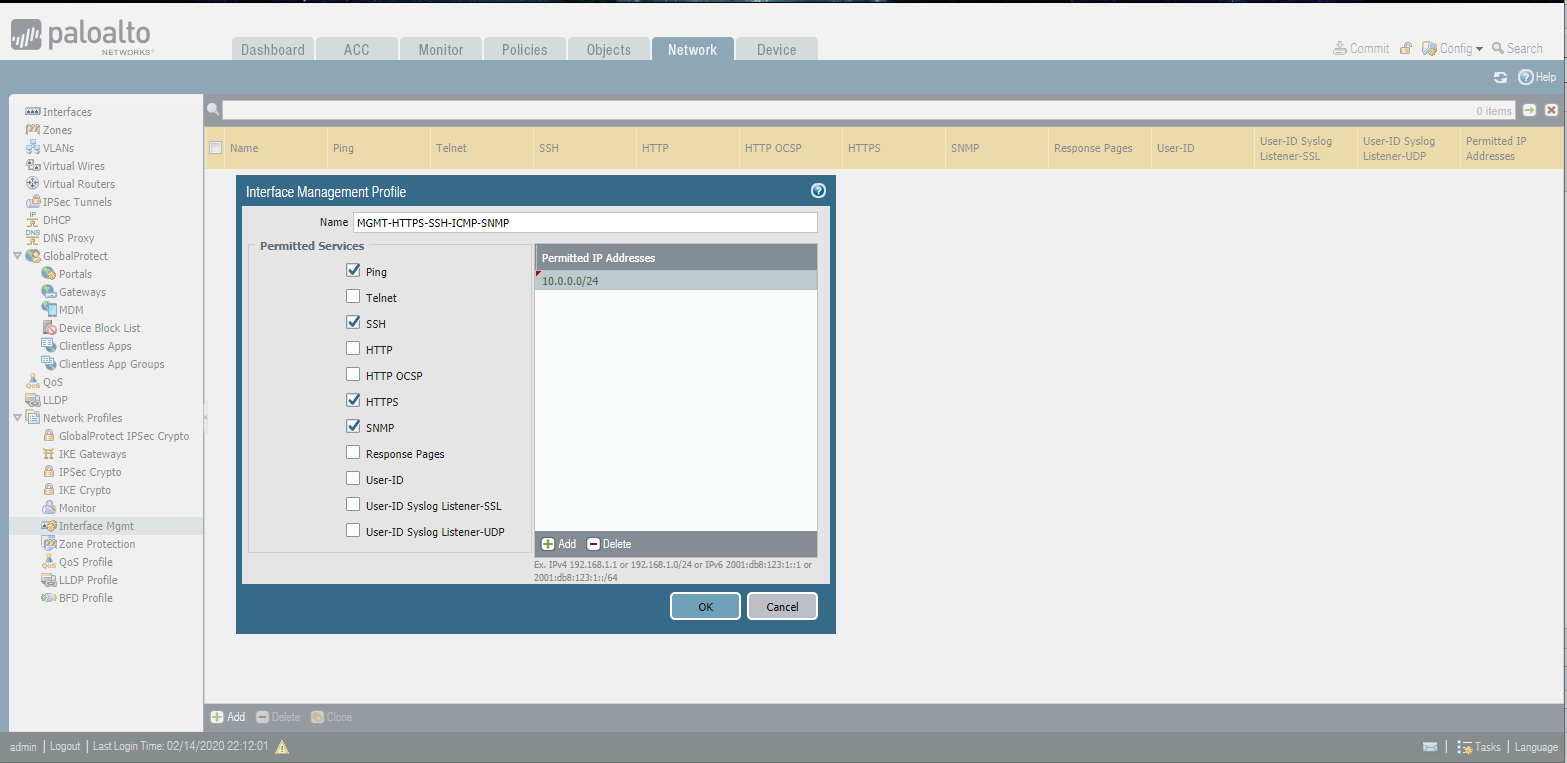
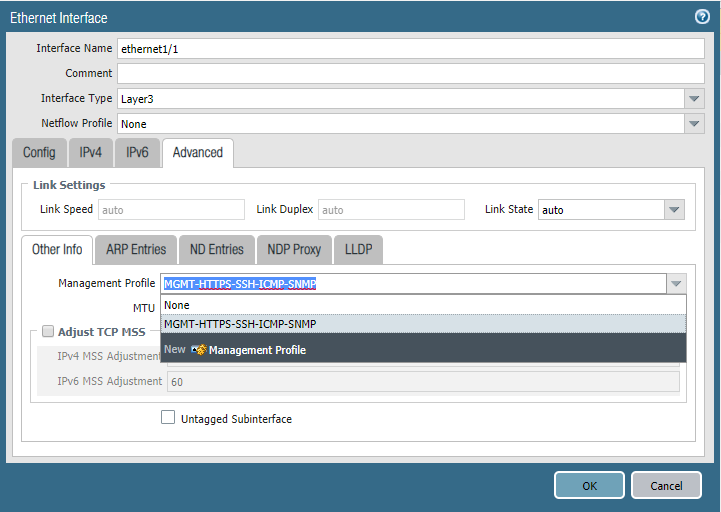
Interface Management Profile
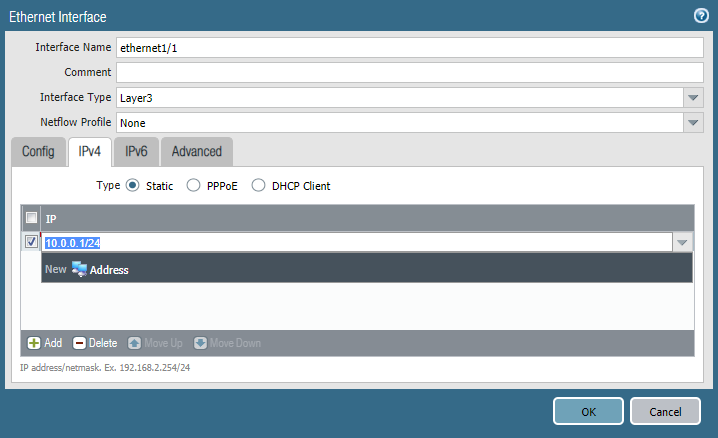
Ethernet Interface
Local admin
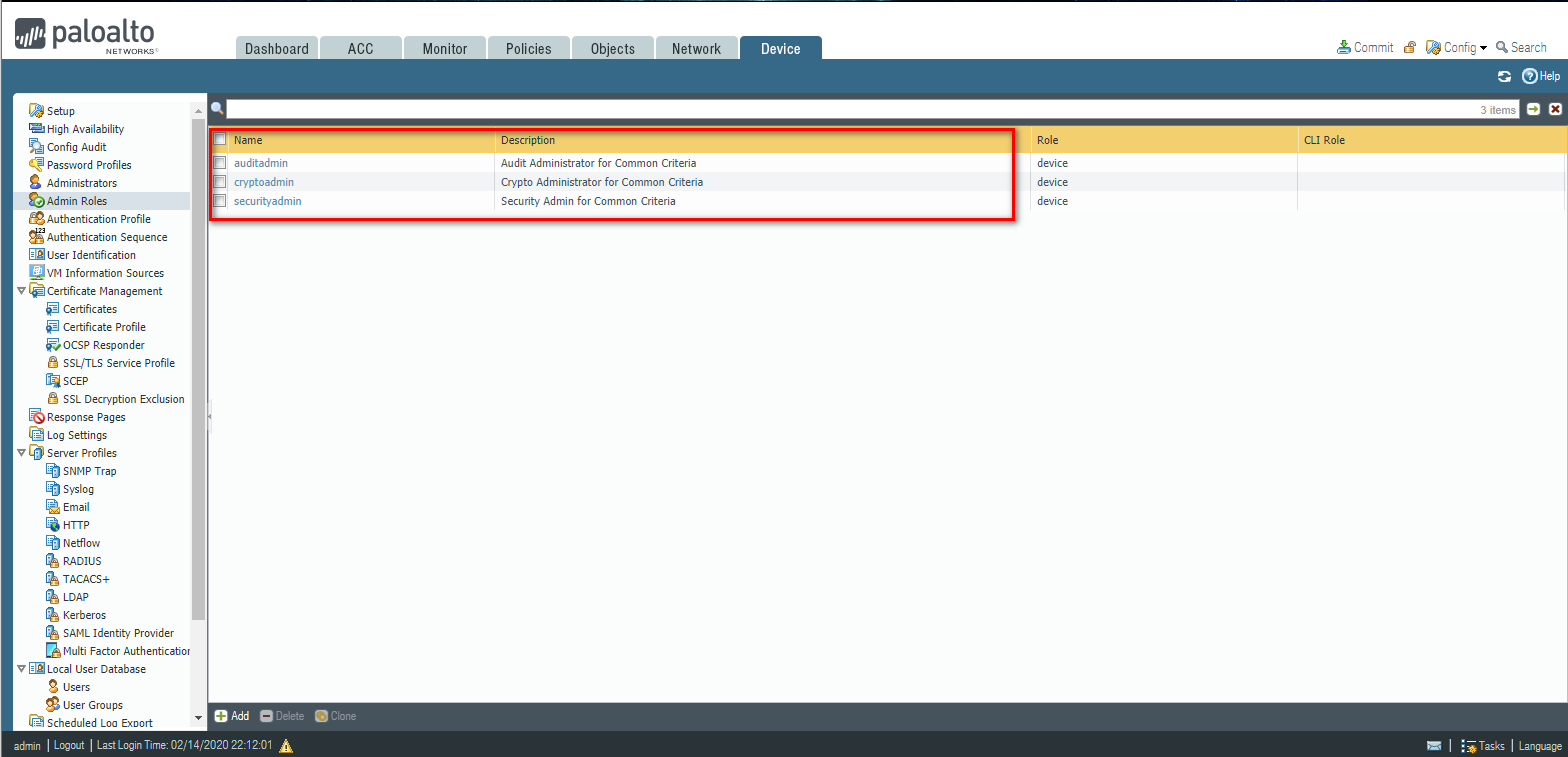
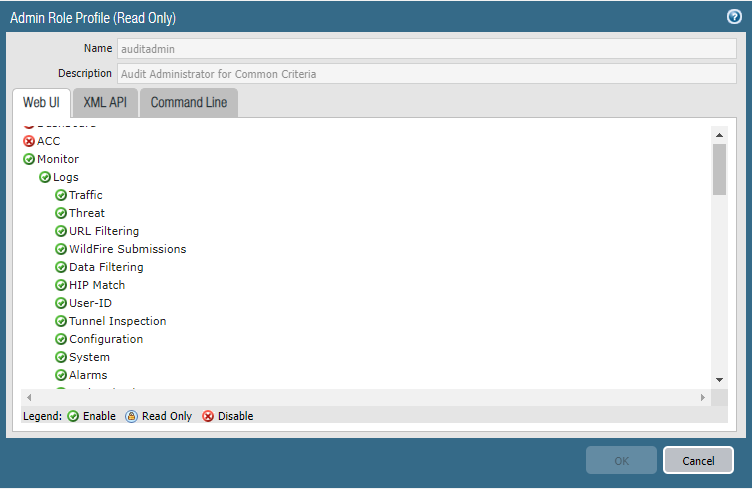
Create a new Role Profile(All function except Policies, Objects, Device, and Privacy.)
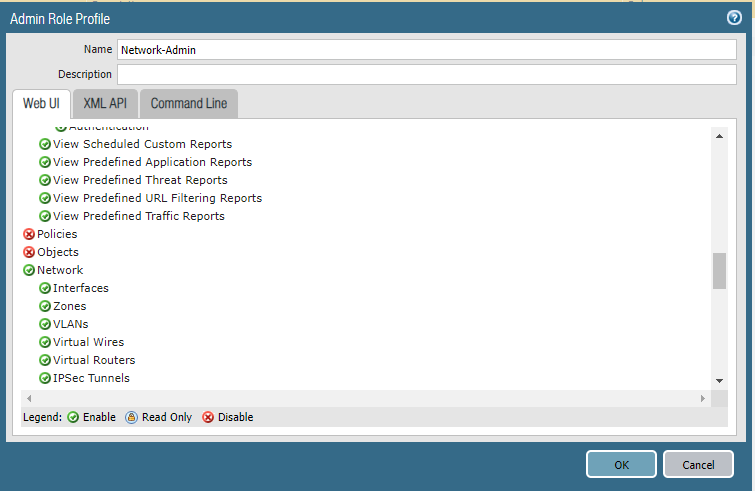
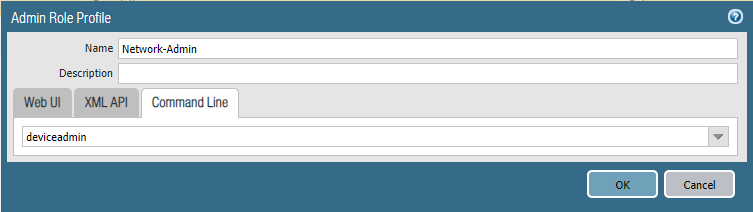
Add a new network administrator.

Cyber Security - Palo Alto Basic Introduction的更多相关文章
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(3)
LDAP Authentication and Remote Users and Groups Create Remote User Objects and LDAP Integration: sam ...
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(1)
Address Objects and Groups Creating address objects. Organizing address objects with address groups ...
- Cyber Security - Palo Alto Firewall Interface Types
Multiple options to integrate the Palo Alto Firewall into your: Network Layer 2 interfaces and VLAN ...
- Cyber Security - Palo Alto Security Policies(2)
Task 3 The SOC(Security Operation Center) monitoring team dashboard reported more 1,000 requests to ...
- Cyber Security - Palo Alto Security Policies(1)
Security policies: Enforcing network traffic by configuring rules of what is allowed or denied to co ...
- Cyber Security - Palo Alto Firewall V-Wires
Leveraging V-Wires Bridge two physical connections and apply security Policies without influencing a ...
- Cyber Security - Palo Alto Firewall Security Zones
Firewall Security Zones Zones: The foundational aspect of every Firewall. Police network traffic Enf ...
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(2)
Users Objects and Groups Creating local user objects. Creating local user groups. https://docs.paloa ...
- Palo Alto GlobalProtect上的PreAuth RCE
0x00 前言 SSL VPN虽然可以保护企业资产免受互联网被攻击的风险影响,但如果SSL VPN本身容易受到攻击呢?它们暴露在互联网上,可以可靠并安全地连接到内网中.一旦SSL VPN服务器遭到入侵 ...
随机推荐
- Android学习笔记菜单资源文件
创建菜单资源 menu_one.xml <?xml version="1.0" encoding="utf-8"?> <menu xmlns: ...
- VS Code WebApi系列——2、jwt结合数据库校验
Knowledge should be shared free. 我们都知道WebApi最重要的作用就是为外部服务提供相应的数据接口和服务,所以一般WebApi都会连接后台数据库,那么最重要的一件事就 ...
- Java容器相关知识点整理
结合一些文章阅读源码后整理的Java容器常见知识点.对于一些代码细节,本文不展开来讲,有兴趣可以自行阅读参考文献. 1. 思维导图 各个容器的知识点比较分散,没有在思维导图上体现,因此看上去右半部分很 ...
- post请求头的常见类型
1.application/json(JSON数据格式) xhr.setRequestHeader("Content-type","application/json; c ...
- Day7-微信小程序实战-天气预报小程序
前段时间在B站跟着一个视频,搞天气预报小程序 https://www.bilibili.com/video/BV1cJ411879s 但是因为这个调用的接口要money,太贵了就没买,就只是做了一些不 ...
- 黎活明8天快速掌握android视频教程--20_采用ContentProvider对外共享数据
1.内容提供者是让当前的app的数据可以让其他应用访问,其他应该可以通过内容提供者访问当前app的数据库 contentProvider的主要目的是提供一个开发的接口,让其他的应该能够访问当前应用的数 ...
- java 中的 自定义viewUtils框架
在前面学习的基础上,我们自己编写一个ViewUtils注解框架类,不清楚的原理看前面的源代码 package im.weiyuan.com.viewutils; import android.supp ...
- 尚学堂 208.Annotation注解和内置注解
208.Annotation注解和内置注解 override:这个注释的作用是标识某一个方法是否覆盖了它的父类的方法deprecated:表示果某个类成员的提示中出现了个词,就表示这个并不建议使用这个 ...
- Ajax 下载文件 文件被损坏
问题表现 Ajax 下载文件成功后,打开提示格式损坏,源代码如下: axios({ method: 'get', url: "/public/工作簿1.xlsx", // 静态资源 ...
- 基于flink和drools的实时日志处理
1.背景 日志系统接入的日志种类多.格式复杂多样,主流的有以下几种日志: filebeat采集到的文本日志,格式多样 winbeat采集到的操作系统日志 设备上报到logstash的syslog日志 ...
