Ethical Hacking - GAINING ACCESS(24)
CLIENT SIDE ATTACKS - Detecting Trojan manually or using a sandbox
Analyzing trojans
- Check the properties of the file.
- The file type of a trojan is application(.exe) , even if it looks like jpg\PDF or other files.
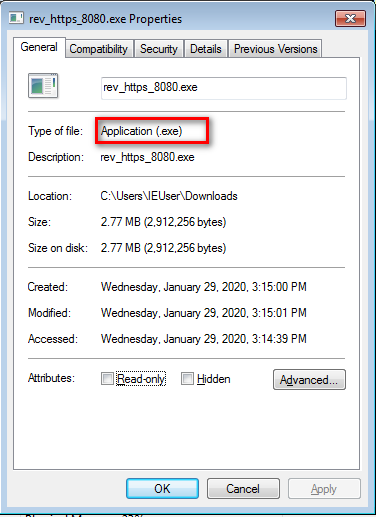
- Is it what it seems to be?
- Check Network Performance
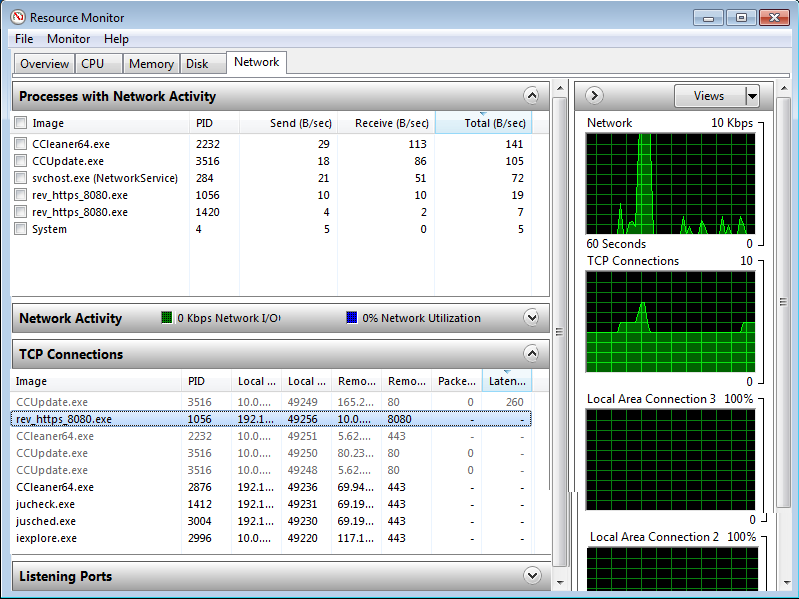
- Reverse DNS check (https://remote.12dt.com/)
- Run the file in a virtual machine and check resources.
- Use an online Sandbox service(https://www.hybrid-analysis.com/)

Ethical Hacking - GAINING ACCESS(24)的更多相关文章
- Ethical Hacking - GAINING ACCESS(1)
Gaining Access Introduction Everything is a computer Two main approaches (1)Server Side Do not requi ...
- Ethical Hacking - GAINING ACCESS(23)
CLIENT SIDE ATTACK - BeEF Framework Hooking targets using MITMF Tools: MITMF and BeEF Start BeEF and ...
- Ethical Hacking - GAINING ACCESS(17)
CLIENT SIDE ATTACKS - Backdooring exe' s Download an executable file first. VEIL - FRAMEWORK A backd ...
- Ethical Hacking - GAINING ACCESS(10)
CLIENT SIDE ATTACKS Use if server-side attacks fail. If IP is probably useless. Require user interac ...
- Ethical Hacking - GAINING ACCESS(6)
Server Side Attack Analysing scan results and exploiting target system. Go to the Analysis page and ...
- Ethical Hacking - GAINING ACCESS(22)
CLIENT SIDE ATTACKS - BeEf Framework Browser Exploitation Framework allowing us to launch a number o ...
- Ethical Hacking - GAINING ACCESS(21)
CLIENT SIDE ATTACKS - Trojan delivery method - using email spoofing Use gathered info to contract ta ...
- Ethical Hacking - GAINING ACCESS(20)
CLIENT SIDE ATTACKS - Spoofing backdoor extension Change the extension of the trojan from exe to a s ...
- Ethical Hacking - GAINING ACCESS(19)
Client-Side Attacks - Social Engineering Tool: The FAT RAT Just like Veil, it generates Undetectable ...
随机推荐
- k8s的两种网络方案与多种工作模式[flannel与calico]
k8s的两种网络方案与多种工作模式 1. Flannel: flannel有三种工作模式: 1. vxlan(隧道方案) 2. host-gw(路由方案) 2. udp(在用户态实现的数据封装解封装, ...
- npm设置为淘宝镜像地址
1. npm设置为淘宝镜像 $npm config set registry https://registry.npm.taobao.org 2. 检查一下 $npm config get regis ...
- SpringCloud教程第6篇:config(F版本)
一.简介 在分布式系统中,由于服务数量巨多,为了方便服务配置文件统一管理,实时更新,所以需要分布式配置中心组件.在Spring Cloud中,有分布式配置中心组件spring cloud config ...
- git 如何解决 (master|MERGING)
git 如何解决 (master|MERGING) git reset --hard head //回退版本信息 git pull origin master
- 基于 Angular Material 的 Data Grid 设计实现
自 Extensions 组件库发布以来,Data Grid 成为了使用及咨询最多的组件.最开始 Data Grid 的设计非常简陋,经过一番重构,组件质量有了质的提升. Extensions 组件库 ...
- 【String注解驱动开发】困扰了我很久的AOP嵌套调用终于解决了!
写在前面 最近在分析Spring源码时,在同一个类中写了嵌套的AOP方法,测试时出现:Spring AOP在同一个类里自身方法相互调用时无法拦截.哎,怎么办?还能怎么办呢?继续分析Spring源码,解 ...
- 吐血推荐,想进BAT必看
不必太纠结于当下,也不必太忧虑未来,人生没有无用的经历,当你经历过一些事情后,眼前的风景已经和从前不一样了.--村上春树 一.包含如下内容 ActiveMQ消息中间件面试专题 BAT80道面试题 BA ...
- DevOps研发模式下「产品质量度量」方案实践
在当今互联网环境下,需求变更越来越快,交付周期却越来越短, 怎么判断一个系统是否测试充分? 产品质量满足什么样的条件才能投产? 如何判断测试工作.研发团队工作的效率是高还是低? 这些问题不能靠感觉.拍 ...
- (1)RabbitMQ简介与安装
1.RabbitMQ简介 因为RabbitMQ是基于开源的AMQP协议来实现的,所以在了解MQ时候,首先我们来了解下AMQP协议.AMQP,即Advanced Message Queuing Prot ...
- STL初步学习(set)
2.set set可以看作一个集合,可以实现自动排序(升序)和去重 在许多题目中,都可以使用这个模板库,减少很多操作,例如P1923 第k小数,当然,这道题有很多奇奇怪怪的做法,分值都不同,之后会讲解 ...
