Ethical Hacking - GAINING ACCESS(19)
Client-Side Attacks - Social Engineering
Tool: The FAT RAT
Just like Veil, it generates Undetectable Metasploit backdoors.
Uses a different method to evade AV programs.
Generates executable binary backdoors for:
- Windows
- Mac OS
- Linux
- Android
Install and initiate TheFatRat successfully.
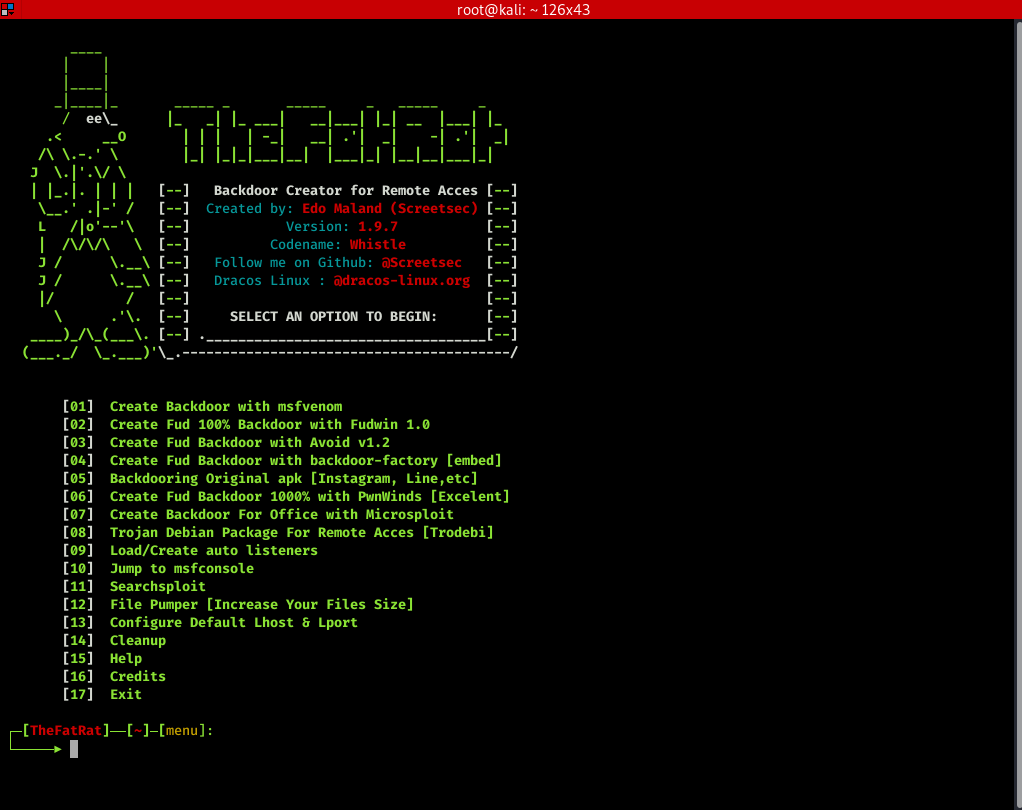
Generate a backdoor.
Ethical Hacking - GAINING ACCESS(19)的更多相关文章
- Ethical Hacking - GAINING ACCESS(1)
Gaining Access Introduction Everything is a computer Two main approaches (1)Server Side Do not requi ...
- Ethical Hacking - GAINING ACCESS(23)
CLIENT SIDE ATTACK - BeEF Framework Hooking targets using MITMF Tools: MITMF and BeEF Start BeEF and ...
- Ethical Hacking - GAINING ACCESS(17)
CLIENT SIDE ATTACKS - Backdooring exe' s Download an executable file first. VEIL - FRAMEWORK A backd ...
- Ethical Hacking - GAINING ACCESS(10)
CLIENT SIDE ATTACKS Use if server-side attacks fail. If IP is probably useless. Require user interac ...
- Ethical Hacking - GAINING ACCESS(6)
Server Side Attack Analysing scan results and exploiting target system. Go to the Analysis page and ...
- Ethical Hacking - GAINING ACCESS(24)
CLIENT SIDE ATTACKS - Detecting Trojan manually or using a sandbox Analyzing trojans Check the prope ...
- Ethical Hacking - GAINING ACCESS(22)
CLIENT SIDE ATTACKS - BeEf Framework Browser Exploitation Framework allowing us to launch a number o ...
- Ethical Hacking - GAINING ACCESS(21)
CLIENT SIDE ATTACKS - Trojan delivery method - using email spoofing Use gathered info to contract ta ...
- Ethical Hacking - GAINING ACCESS(20)
CLIENT SIDE ATTACKS - Spoofing backdoor extension Change the extension of the trojan from exe to a s ...
随机推荐
- Spring Boot 把 Maven 干掉了,拥抱 Gradle!
在国外某社交网站上有一个关于迁移 Spring Boot 迁移 Maven 至 Gradle 的帖子: 该贴子上也有很多人质疑:Maven 用的好好的,为什么要迁移至 Gradle? 虽然该贴子只是说 ...
- 套接字TCP控制台服务器程序代码示范
套接字TCP控制台服务器程序代码示范 https://blog.csdn.net/txwtech/article/details/90344081
- 005.OpenShift访问控制-权限-角色
一 Kubetcl namespace 1.1 namespace描述 Kubernetes namespace提供了将一组相关资源组合在一起的机制.在Red Hat OpenShift容器平台中,p ...
- 5种经典的Linux桌面系统
最近一直在准备Linux相关的PPT,对于一个老码农来说Linux系统自然是比较熟悉了,随口可以说出好几种Linux的版本,然而对于计算机初学者可能就知道windows操作系统.也许你告诉他你可以安装 ...
- RabbitMQ:五、高阶
存储机制 持久化的消息和非持久化的消息都可以被写入到磁盘. 持久化的消息一开始就会写入磁盘,如果可以,也会在内存中保存一部分以提高性能,当内存吃紧时会从内存中清楚. 非持久化的消息一般存储在内存中,内 ...
- Python 分布式缓存之Reids数据类型操作
目录 1.Redis API 2.String 操作 3.Hash 操作 4.List 操作 1.Redis API 1.操作模式 redis-py提供两个类Redis和StrictRedis用于实现 ...
- Spring IoC 默认标签解析
前言 本系列全部基于 Spring 5.2.2.BUILD-SNAPSHOT 版本.因为 Spring 整个体系太过于庞大,所以只会进行关键部分的源码解析. 本篇文章主要介绍 Spring IoC 容 ...
- 计算机网络之tcp与udp的区别
1.基于连接与无连接: 2.对系统资源的要求(TCP较多,UDP少):3.UDP程序结构较简单:4.流模式与数据报模式 :5.TCP保证数据正确性,可靠稳定,UDP可能丢包:6.TCP保证数据顺序,U ...
- 【转载】张一鸣:为什么 BAT 挖不走我们的人才?
很多企业失败的时候,总说是政策的变化.市场的变化.消费者需求的变化.技术发展的变化等等,导致了失败,其实这都是瞎说,归根结底还是人的原因,都是因为你招的人不行.可见,人才对于一个企业的重要性. 互联网 ...
- .net core docker容器编排部署(linux)
环境准备 需要一个linux操作系统:我这里用的是ubuntu 18.04,安装步骤就不说了,网上很多教程,当然也可以私信我. 既然需要用到docker,那么就安装个docker,apt instal ...
