Python Ethical Hacking - NETWORK_SCANNER(1)
NETWORK_SCANNER
- Discover all devices on the network.
- Display their IP address.
- Display their MAC address.
Write the Python code using the scapy.all module.
Refer to: https://scapy.readthedocs.io/en/latest/installation.html
#!/usr/bin/env python import scapy.all as scapy def scan(ip):
scapy.arping(ip) scan("10.0.0.1/24")
ALGORITHM
Goal -> Discover clients on the network.
Steps:
1. Create arp request directed to broadcast MAC asking for IP.
Two main parts:
-> Use ARP to ask who has target IP.
-> Set destination MAC to broadcast MAC.
2. Send packet and receive a response.
3. Parse the response.
4. Print result.
Use the scapy module in this program.
https://scapy.readthedocs.io/en/latest/usage.html
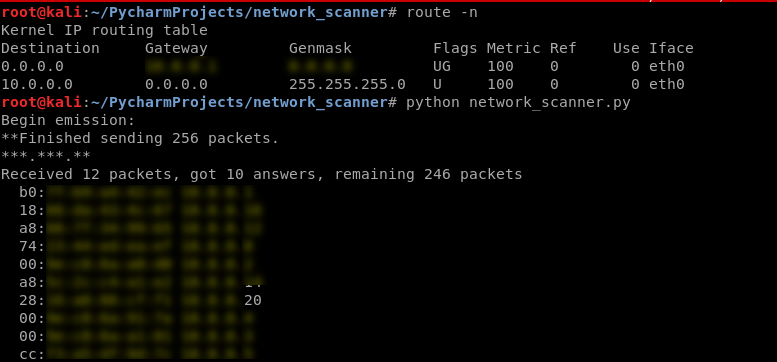
EX: Python Script to discover the clients on the network.
#!/usr/bin/env python import scapy.all as scapy def scan(ip):
arp_request = scapy.ARP(pdst=ip)
broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")
arp_request_broadcast = broadcast/arp_request
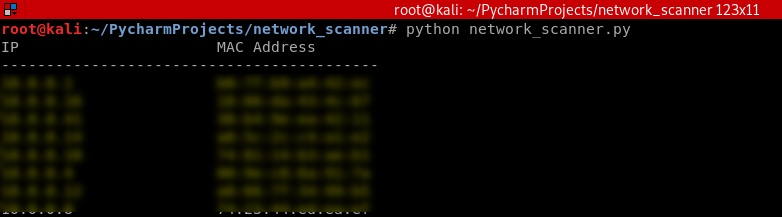
answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0] print("IP\t\t\tMAC Address\n------------------------------------------")
for element in answered_list:
print(element[1].psrc + "\t\t" + element[1].hwsrc) scan("10.0.0.1/24")
Execute the script and show the result.
Python Ethical Hacking - NETWORK_SCANNER(1)的更多相关文章
- Python Ethical Hacking - NETWORK_SCANNER(2)
DICTIONARIES Similar to lists but use key instead of an index. LISTS List of values/elements, all ca ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
- Python Ethical Hacking - ARP Spoofing
Typical Network ARP Spoofing Why ARP Spoofing is possible: 1. Clients accept responses even if they ...
- Python Ethical Hacking - MAC Address & How to Change(3)
SIMPLE ALGORITHM Goal -> Check if MAC address was changed. Steps: 1. Execute and read ifconfig. ...
- Python Ethical Hacking - MAC Address & How to Change(2)
FUNCTIONS Set of instructions to carry out a task. Can take input, and return a result. Make the cod ...
- Python Ethical Hacking - MAC Address & How to Change(1)
MAC ADDRESS Media Access Control Permanent Physical Unique Assigned by manufacturer WHY CHANGE THE M ...
- Python Ethical Hacking - The Lab and Needed Software
The Lab and Needed Software Attacker Machine - Kali Linux https://www.kali.org/ 1. Install the softw ...
- Python Ethical Hacking - Basic Concetion
What is Hacking? Gaining unauthorized access. Hackers? 1.Black-hat Hackers 2.White-hat Hackers 3.Gre ...
- Python Ethical Hacking - VULNERABILITY SCANNER(9)
Automatically Discovering Vulnerabilities Using the Vulnerability Scanner 1. Modify the run_scanner ...
随机推荐
- JavaSE基础之数组
数组 一.静态初始化 格式一 数据类型[] 变量名 = {元素1,元素2,元素3...}; 格式二 数据类型[] 变量名 = new 数据类型{元素1,元素2,元素3...}; 或者: 数据类型[] ...
- S7-200 PLC内部+5VDC电源的负载能力
S7-200 PLC内部+5VDC电源的负载能力 S7-200 CPU模块提供DC5V和24V电源:当有扩展模块时,CPU通过I/O总线为其提供5V电源,所有扩展模块的SV电源消耗之和不能超过该CPU ...
- 效率思维模式与Zombie Scrum
Scrum是由Ken Schwaber和Jeff Sutherland在20世纪90年代提出的概念,并在1995年首次正式确定.起初Scrum是为了解决产品和软件开发固有的复杂性,然而现在Scrum被 ...
- VMware Workstation 15密钥
在打开的VMware Workstation 15输入许可证密钥对话框里直接输入25位密钥,然后点击确定,如下图所示. 这里提供一个密钥: CG392-4PX5J-H816Z-HYZNG-PQRG2
- synchronized与锁升级
1 为什么需要synchronized? 当一个共享资源有可能被多个线程同时访问并修改的时候,需要用锁来保证数据的正确性.请看下图: 线程A和线程B分别往同一个银行账户里面添加货币,A线程从内存中读取 ...
- JAVA环境配置(WIN10之64位)
1.下载java开发工具包JDK,https://www.oracle.com/technetwork/java/javase/downloads/index.html进入首页, 点击下载页: 点击下 ...
- xeus-clickhouse: Jupyter 的 ClickHouse 内核
在科学计算领域,Jupyter 是一个使用非常广泛的集成开发环境,它支持多种主流的编程语言比如 Python, C++, R 或者 Julia.同时,数据科学最重要的还是数据,而 SQL 是操作数据最 ...
- Python实用笔记 (11)高级特性——迭代器
这些可以直接作用于for循环的对象统称为可迭代对象:Iterable. 可以使用isinstance()判断一个对象是否是Iterable对象: >>> from collectio ...
- SpringBoot项目部署到tomcat
SpringBoot部署到tomcat 一.修改maven.xml 1.添加<.packaging>war</.packaging>,打包为war包 <packaging ...
- python简易版微信或QQ轰炸
在讲解代码之前我们先来回忆一下,平时我们发送消息时,先打开微信或QQ的界面,在信息栏中输入你要发送的内容在点击发送或通过快捷键发送.如果要发送表情时,先打开微信或QQ的界面,在点击表情包中你要发送 ...
