Cyber Security - Palo Alto Firewall Interface Types
Multiple options to integrate the Palo Alto Firewall into your:
- Network
- Layer 2 interfaces and VLAN interfaces
- Layer 3 interfaces
- Tap interfaces
- Loopback and tunnel interfaces
- HA interfaces
Type 1 - Layer 2 interfaces:
- Allows a Trunk interface to transmit
- Tagged VLAN's which can be assigned to VLAN interfaces
- Can be allocated in port channels (link aggregation with LACP)

Configure a Layer2 interface with Wired-VLAN20.
Add a layer2 subinterface.
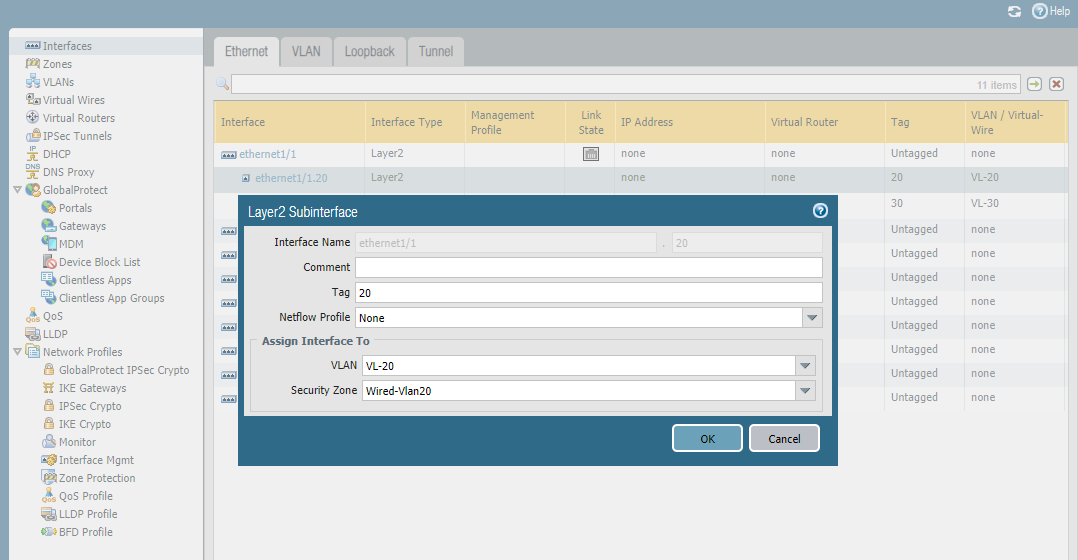
Add a Wireless-VLAN30 subinterface.

Type2 - Layer 3 interfaces:
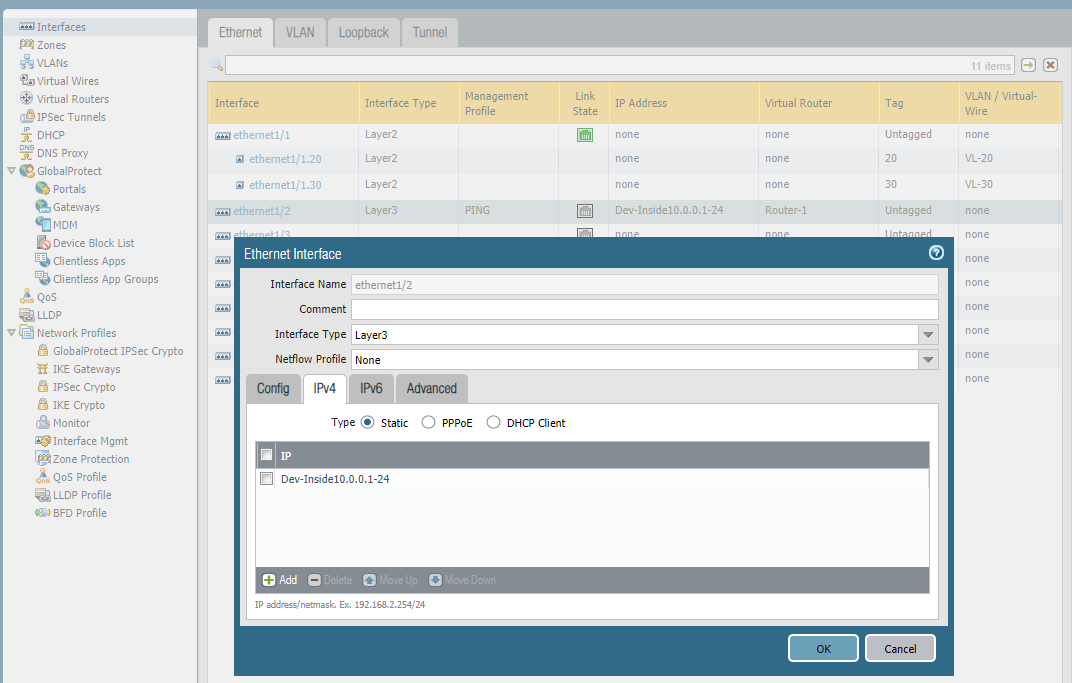
- Carries end-to-end Layer 3 traffic with an assigned IP address.
- Can be allocated in port channels(link aggregation with LACP)
- Can be sub-divided in L3 Subinterfaces.
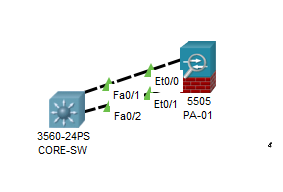
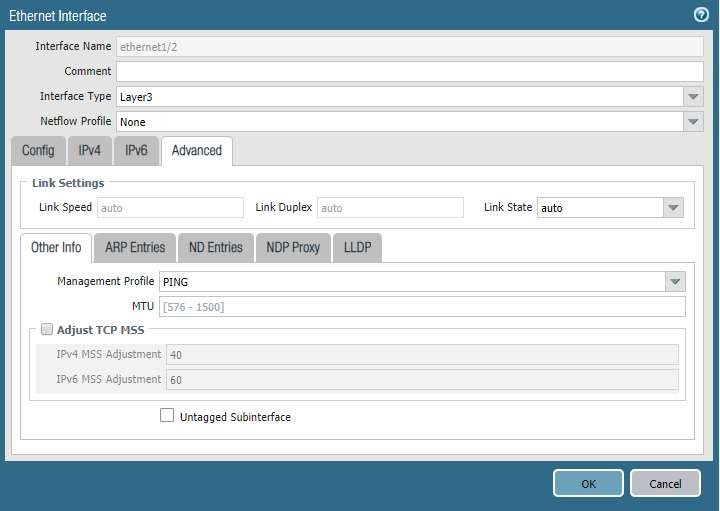
Add a layer3 interface.

Type3 - Tunnel and loopback interfaces:
- Used to logically assign attributes to tunnel entry/exit points
- Loopbacks: Create always-on logical interfaces for required applications.
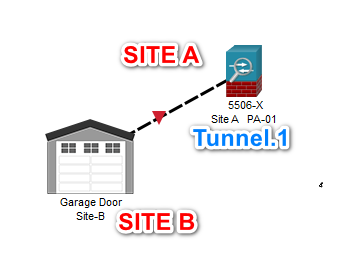
Configure a tunnel.
Confiture Loopback
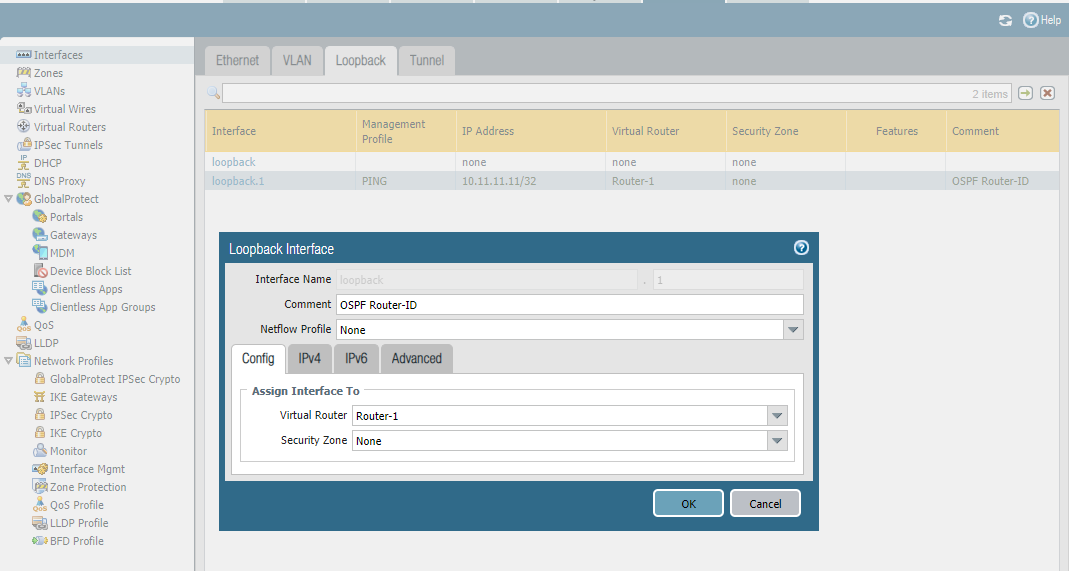


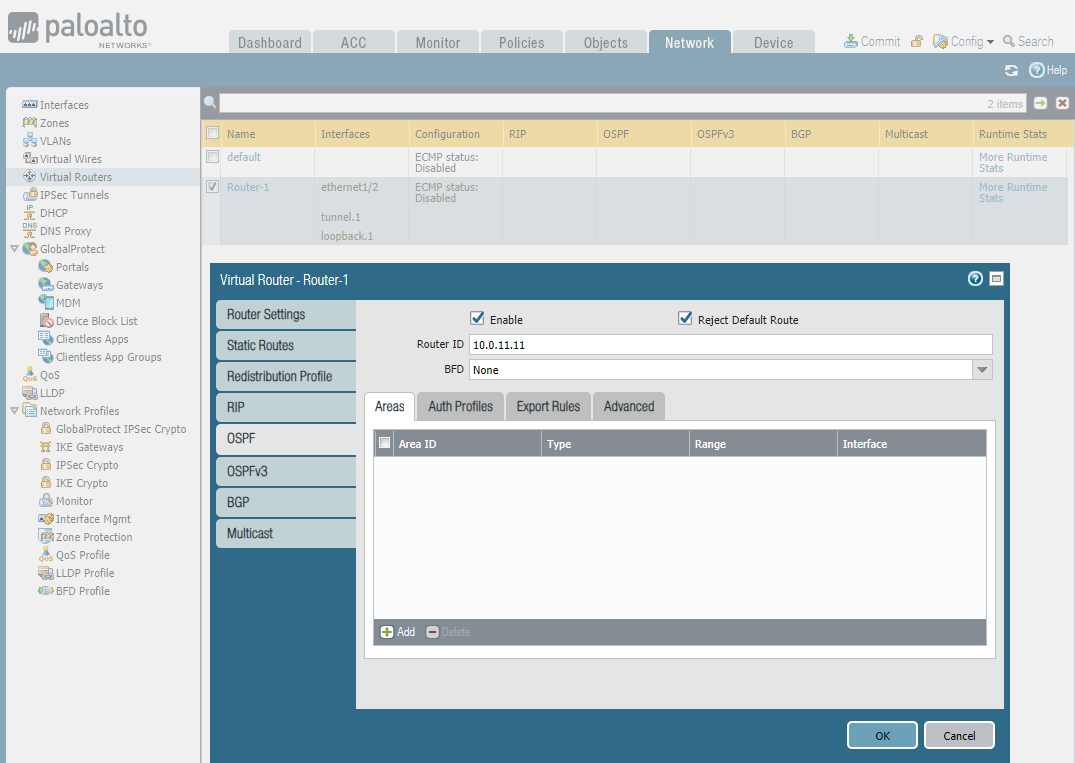
Configure Virtual Router
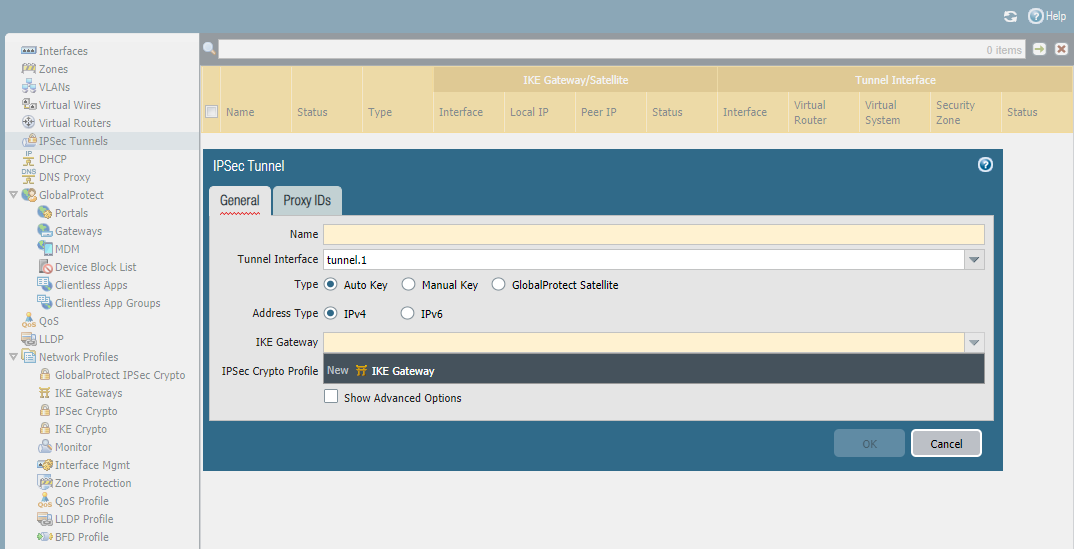
Configure IPsec Tunnels here.
Typer 4 - HA(High availability interfaces):
- Allows connectively between two Palo Alto Firewalls to establish a highly available Firewall setup
- HA links will carry required information to build the cluster, and sync routing/configuration across the members.

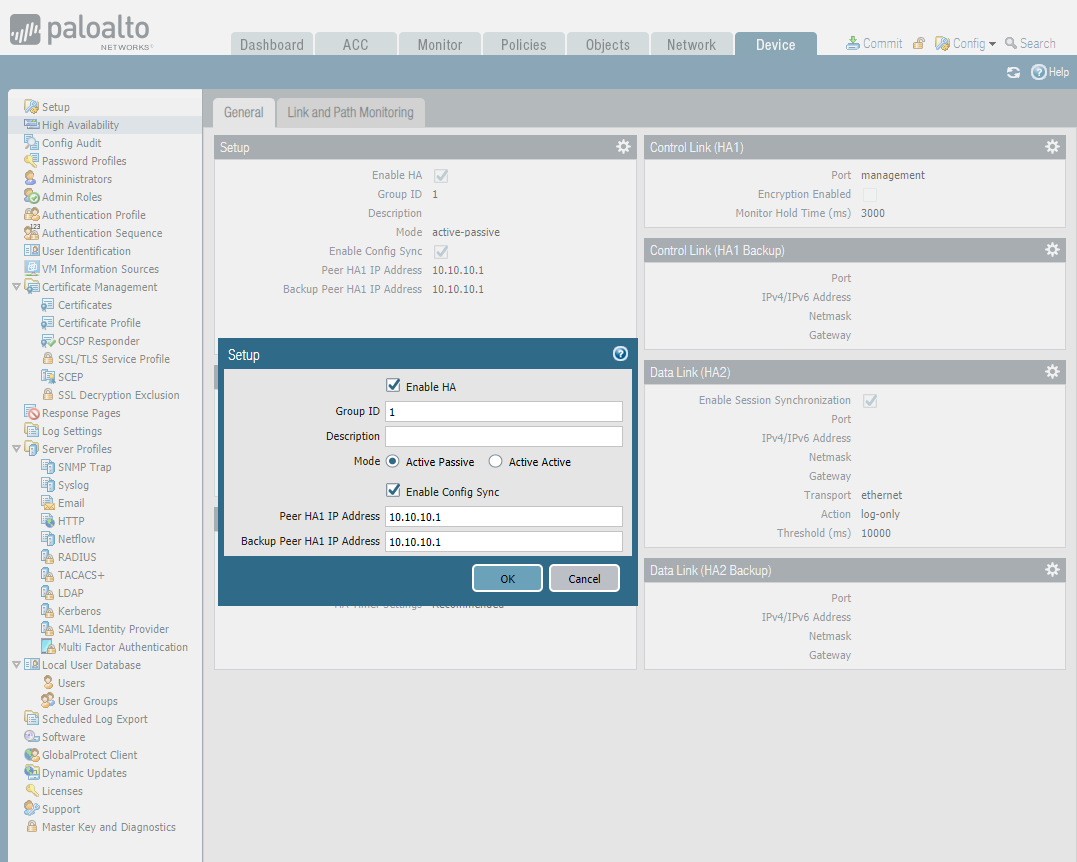
Configure HA interface.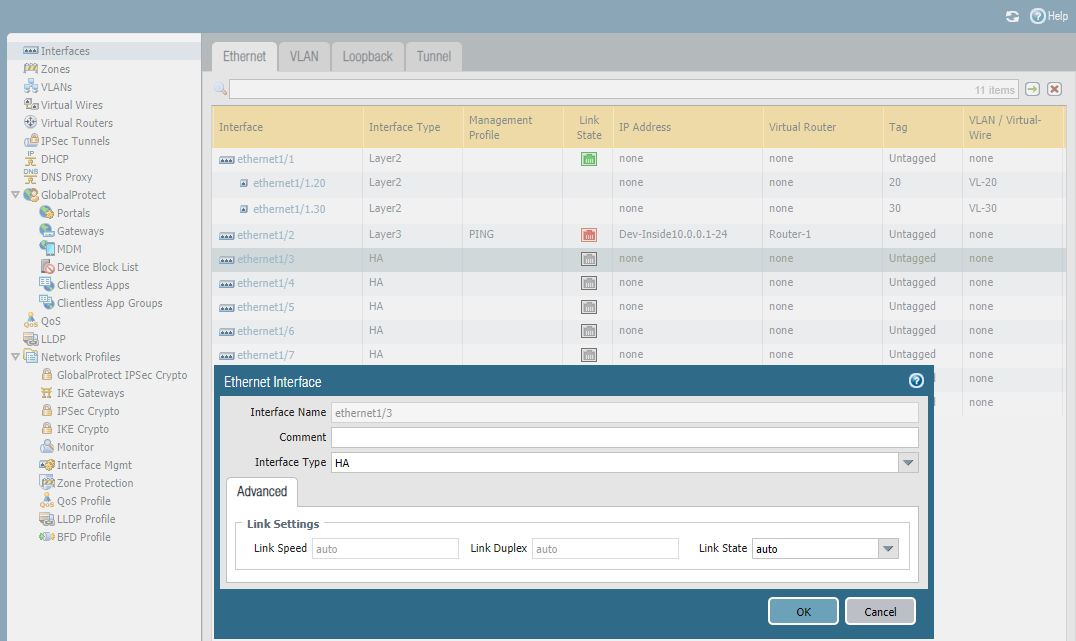
Enable HA setup.
Configure the Control Link.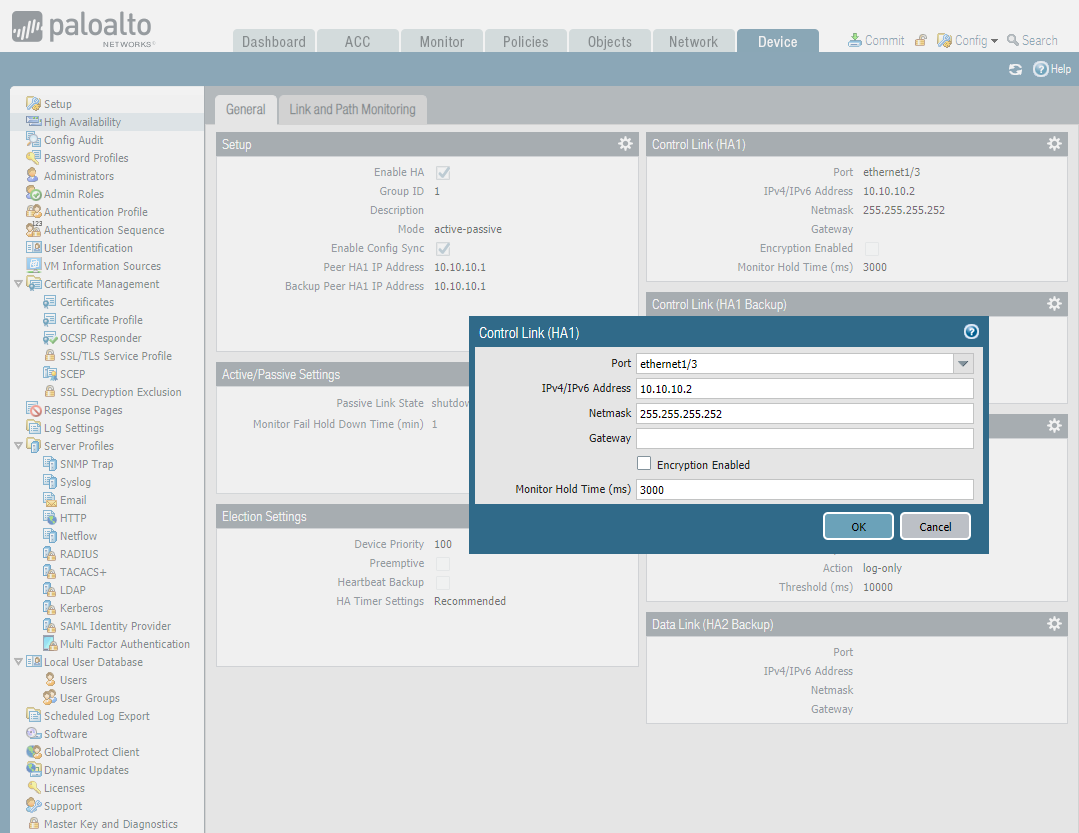
Cyber Security - Palo Alto Firewall Interface Types的更多相关文章
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(3)
LDAP Authentication and Remote Users and Groups Create Remote User Objects and LDAP Integration: sam ...
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(1)
Address Objects and Groups Creating address objects. Organizing address objects with address groups ...
- Cyber Security - Palo Alto Firewall V-Wires
Leveraging V-Wires Bridge two physical connections and apply security Policies without influencing a ...
- Cyber Security - Palo Alto Firewall Security Zones
Firewall Security Zones Zones: The foundational aspect of every Firewall. Police network traffic Enf ...
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(2)
Users Objects and Groups Creating local user objects. Creating local user groups. https://docs.paloa ...
- Cyber Security - Palo Alto Basic Introduction
Preparation of the Lab Environment: Download and Install Pan-OS from the following website https://d ...
- Cyber Security - Palo Alto Security Policies(2)
Task 3 The SOC(Security Operation Center) monitoring team dashboard reported more 1,000 requests to ...
- Cyber Security - Palo Alto Security Policies(1)
Security policies: Enforcing network traffic by configuring rules of what is allowed or denied to co ...
- Palo Alto GlobalProtect上的PreAuth RCE
0x00 前言 SSL VPN虽然可以保护企业资产免受互联网被攻击的风险影响,但如果SSL VPN本身容易受到攻击呢?它们暴露在互联网上,可以可靠并安全地连接到内网中.一旦SSL VPN服务器遭到入侵 ...
随机推荐
- scanf中的%[^\n]%*c格式
scanf中的%[^\n]%*c格式 (2011-02-19 16:12:38) 转载▼ 标签: 控制字符 空白字符 字符串 变量 整数 it 分类: C语言编程 文章转载自http://blog. ...
- 11、vue-路由
1.路由: 官方提供一个插件,构建单页面应用,主要实现得功能页面得切换.组件得跳转 2.vue中得路由:vue-router包,如果是脚手架进行搭建得,那么是不需要安装vue-router这个包得,因 ...
- python中那些鲜为人知的功能特性
经常逛GitHub的可能关注一个牛叉的项目,叫 What the f*ck Python! 这个项目列出了几乎所有python中那些鲜为人知的功能特性,有些功能第一次遇见时,你会冒出 what the ...
- PHP丨PHP基础知识之数据类型
PHP的数据类型主要有三大种:(细分的话8小种) 一.标量数据类型 标量数据类型包括以下几种: (1)BOOLEAN:布尔型 布尔变量是PHP变量中最简单的: 它保存一个TRUE或者FALSE值: 其 ...
- 算法题解:最小的K个数(海量数据Top K问题)
[本文版权归微信公众号"代码艺术"(ID:onblog)所有,若是转载请务必保留本段原创声明,违者必究.若是文章有不足之处,欢迎关注微信公众号私信与我进行交流!] 题目 输入 n ...
- 必知必会的8个Python列表技巧
原作者:Nik Piepenbreier 翻译&内容补充:费弗里 原文地址:https://towardsdatascience.com/advanced-python-list-techni ...
- JavaWeb网上图书商城完整项目--day02-4.regist页面提交表单时对所有输入框进行校验
1.现在我们要将table表中的输入的参数全部提交到后台进行校验,我们提交我们是按照表单的形式提交,所以我们首先需要在table表外面添加一个表单 <%@ page language=" ...
- NFC芯片选型及基本电路框架
RFID作为一项专业度较高的技术,在一些公司,可能还会专门招聘专业的RFID工程师.本篇阐述的涉及到的只是基本选型设计.电路框架,关于RFID天线调试.低功耗检卡调试等,后续再其他篇章会继续更新! N ...
- Spring Boot2+Resilience4j实现容错之Bulkhead
Resilience4j是一个轻量级.易于使用的容错库,其灵感来自Netflix Hystrix,但专为Java 8和函数式编程设计.轻量级,因为库只使用Vavr,它没有任何其他外部库依赖项.相比之下 ...
- FastAPI 快速搭建一个REST API 服务
最近正好在看好的接口文档方便的工具, 突然看到这个, 试了一下确实挺方便 快速示例 from fastapi import FastAPI from pydantic import BaseModel ...
