Ethical Hacking - NETWORK PENETRATION TESTING(12)
Post Connection Attacks
Sophisticated attacks that can be used after connecting to the target AP.
Gathering Information
Now that we are connected to a specific AP, we can gather more detailed info about the clients connected to this AP. There is a number of programs that can be used to do this, we shall talk about 3 programs starting with the simplest and quickest one.
· Netdiscover
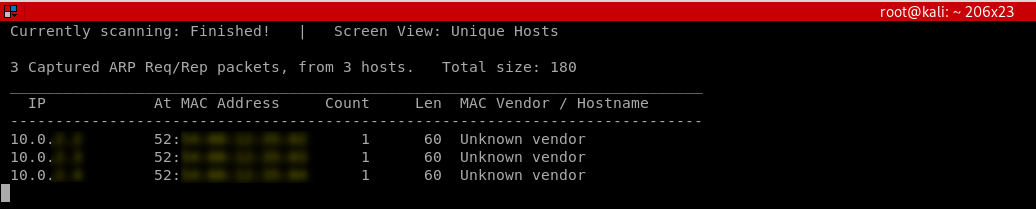
Netdiscover is a program that can be used to discover the connected clients to our current network, it's very quick but it does not show detailed information about the clients: IP, MAC address and some times the hardware manufacturer for the client's wireless card.
netdiscover -i [INTERFACE] -r [RANGE]
Netdiscover 0.5.1 [Active/passive ARP reconnaissance tool]
Written by: Jaime Penalba <jpenalbae@gmail.com>
Usage: netdiscover [-i device] [-r range | -l file | -p] [-m file] [-F filter] [-s time] [-c count] [-n node] [-dfPLNS]
-i device: your network device
-r range: scan a given range instead of auto scan. 192.168.6.0/24,/16,/8
-l file: scan the list of ranges contained into the given file
-p passive mode: do not send anything, only sniff
-m file: scan a list of known MACs and host names
-F filter: customize pcap filter expression (default: "arp")
-s time: time to sleep between each ARP request (milliseconds)
-c count: number of times to send each ARP request (for nets with packet loss)
-n node: last source IP octet used for scanning (from 2 to 253)
-d ignore home config files for autoscan and fast mode
-f enable fastmode scan, saves a lot of time, recommended for auto
-P print results in a format suitable for parsing by another program and stop after active scan
-L similar to -P but continue listening after the active scan is completed
-N Do not print header. Only valid when -P or -L is enabled.
-S enable sleep time suppression between each request (hardcore mode)
If -r, -l or -p are not enabled, netdiscover will scan for common LAN addresses.
· Autoscan
Autoscan is another program that can be used to discover the connected clients to our current network, it's not as quick as netdiscover, but it shows more detailed information about the connected devices and it has a graphical user interface.
Download autoscan from: https://sourceforge.net/projects/autoscan/files/AutoScan/autoscan-network%201.50/AutoScan-Network-1.50.pkg.zip/download
-> Install autoscan

->Chose the installation directory
->Complete the installation and set the Network Wizard.

Ethical Hacking - NETWORK PENETRATION TESTING(12)的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark WIreshark is a network protocol analyser that is designed to help network administa ...
- Ethical Hacking - NETWORK PENETRATION TESTING(14)
MITM - ARP Poisoning Theory Man In The Middle Attacks - ARP Poisoning This is one of the most danger ...
- Ethical Hacking - NETWORK PENETRATION TESTING(13)
Nmap Nmap is a network discovery tool that can be used to gather detailed information about any clie ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
- Ethical Hacking - NETWORK PENETRATION TESTING(10)
WPA Craking WPA was designed to address the issues in WEP and provide better encryption. The main is ...
- Ethical Hacking - NETWORK PENETRATION TESTING(8)
WEP Cracking Basic case Run airdump-ng to log all traffic from the target network. airodump-ng --cha ...
- Ethical Hacking - NETWORK PENETRATION TESTING(7)
Gaining Access to encrypted networks Three main encryption types: 1. WEP 2.WPA 3.WPA2 WEP Cracking W ...
- Ethical Hacking - NETWORK PENETRATION TESTING(5)
Deauthentication Attacks Theory This attack is used to disconnect any device from any network within ...
随机推荐
- Beta冲刺<5/10>
这个作业属于哪个课程 软件工程 (福州大学至诚学院 - 计算机工程系) 这个作业要求在哪里 Beta冲刺 这个作业的目标 Beta冲刺--第五天(05.23) 作业正文 如下 其他参考文献 ... B ...
- Python 网络爬虫实战:爬取 B站《全职高手》20万条评论数据
本周我们的目标是:B站(哔哩哔哩弹幕网 https://www.bilibili.com )视频评论数据. 我们都知道,B站有很多号称“镇站之宝”的视频,拥有着数量极其恐怖的评论和弹幕.所以这次我们的 ...
- 从零开始学习Prometheus监控报警系统
Prometheus简介 Prometheus是一个开源的监控报警系统,它最初由SoundCloud开发. 2016年,Prometheus被纳入了由谷歌发起的Linux基金会旗下的云原生基金会( C ...
- Redis安装过程jemalloc/jemalloc.h报错
问题: [root@localhost redis-3.0.0]# make cd src && make all make[1]: Entering directory `/data ...
- 弹性配置为构建提速 - CODING & 腾讯云 CVM 最佳实践
CODING 中提供了内置云主机用来执行持续集成(CI)中的构建计划,能够胜任大部分构建任务.但如果碰上了大型项目的构建,或者需要在本地服务器生成构建成果,单个计算资源就显得有点捉急了.针对这一部分需 ...
- Lens —— 最炫酷的 Kubernetes 桌面客户端
原文链接:https://fuckcloudnative.io/posts/lens/ Kubernetes 的桌面客户端有那么几个,曾经 Kubernetic 应该是最好用的,但最近有个叫 Lens ...
- Python3-算法-冒泡排序
冒泡排序 它重复地走访过要排序的数列,一次比较两个元素,如果他们的顺序错误就把他们交换过来,走访数列的工作是重复地进行直到没有再需要交换,也就是说该数列已经排序完成,这个算法的名字由来是因为越大的元素 ...
- Springboot在包含有参构造方法的类中使用@Value注解取值
我们在Springboot中经常使用@Value注解来获取配置文件中的值,像下面这样 @Component class A { @Value("${user.value}") pr ...
- 02 [掌握] redis详情命令
1,常用命令 keys * 获取所有的key select 0 选择第一个库 move myString 1 将当前的数据库key移动到某个数据库,目标库有,则不能移动 flushdb 清除指定库 r ...
- 程序员必备基础:Git 命令全方位学习
前言 掌握Git命令是每位程序员必备的基础,之前一直是用smartGit工具,直到看到大佬们都是在用Git命令操作的,回想一下,发现有些Git命令我都忘记了,于是写了这篇博文,复习一下~ https: ...
