Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(1)
Address Objects and Groups
- Creating address objects.
- Organizing address objects with address groups
- Limiting the human error and complexity thanks to address groups.

Add a new address:
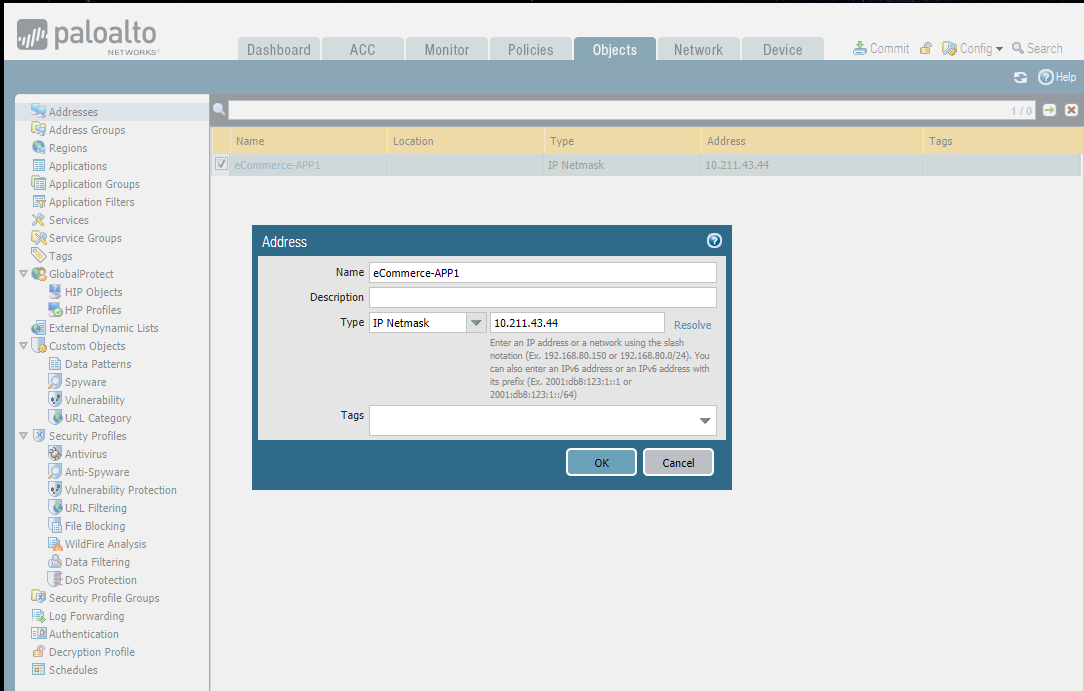
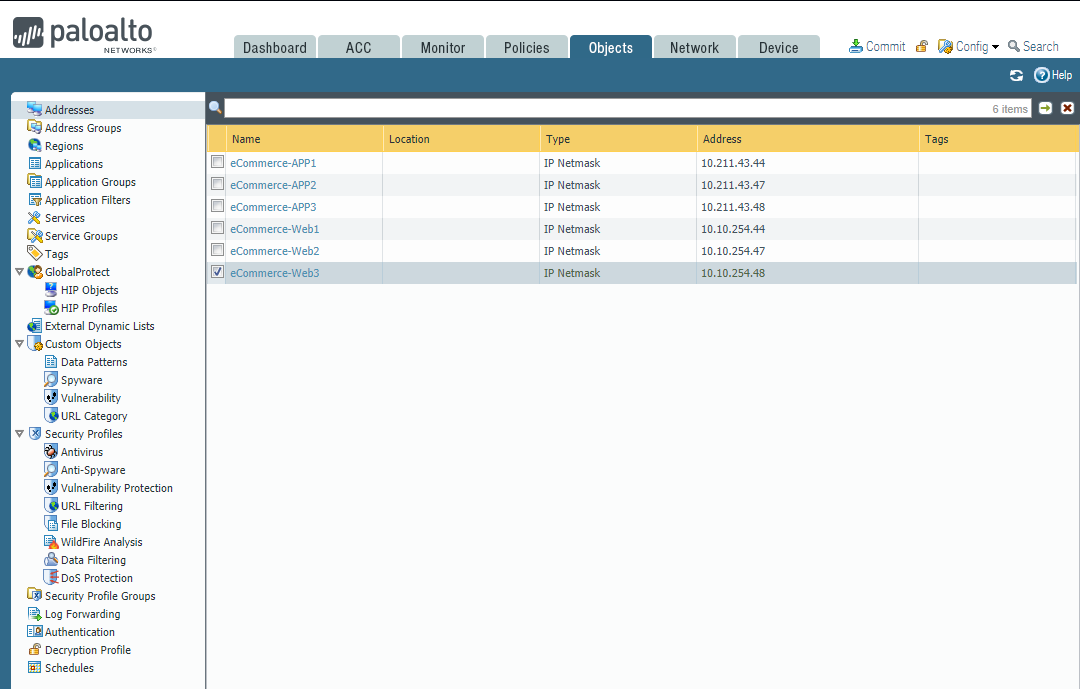
Add new Address Groups:


Service Objects and Groups
- Creating service objects.
- Organizing service objects with service groups
- Using service groups to avoid long and complex security policy tables.
Add services:
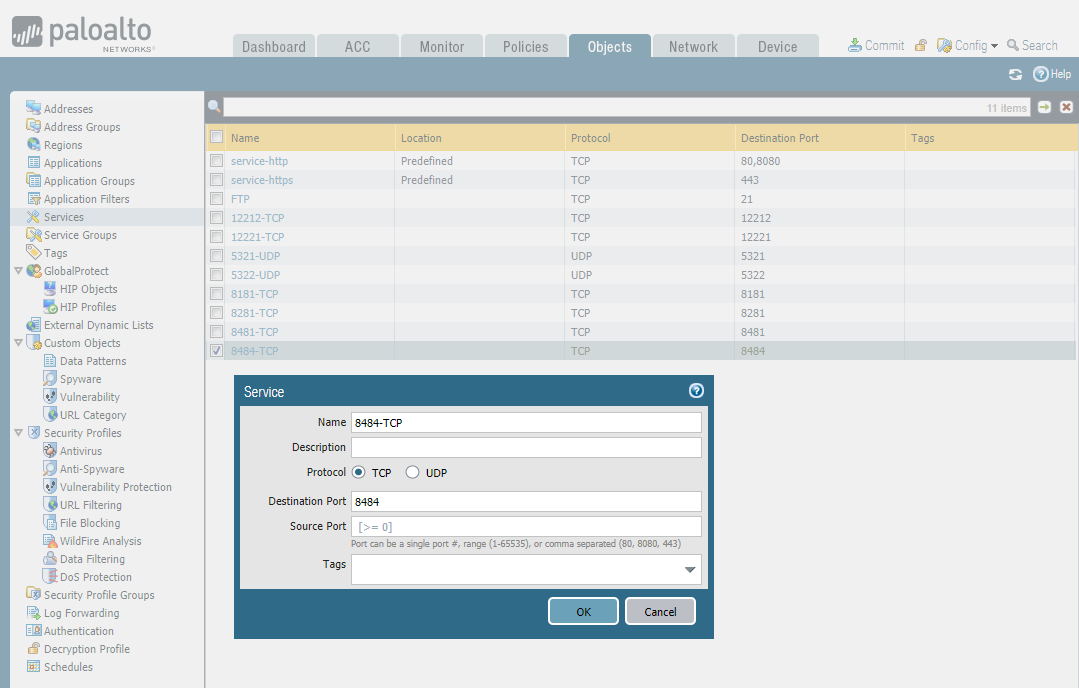
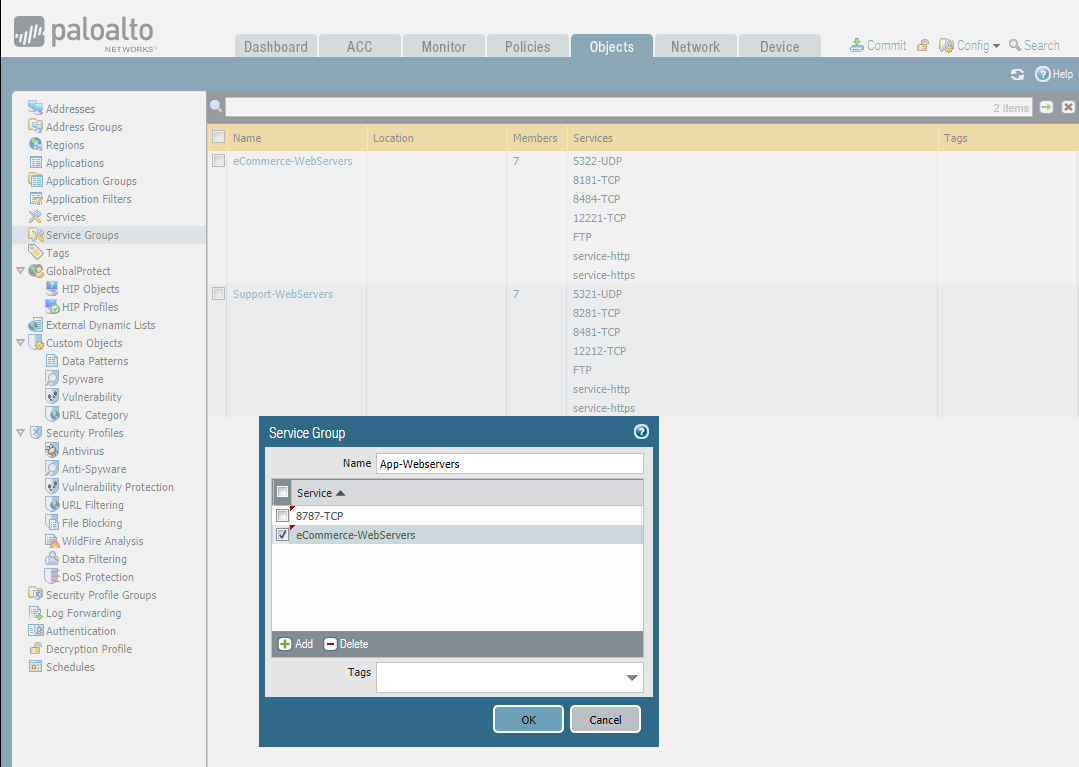
Add Service Groups:
Application Objects and Groups
- Creating application objects.
- Classify application objects in groups.

Add applications:
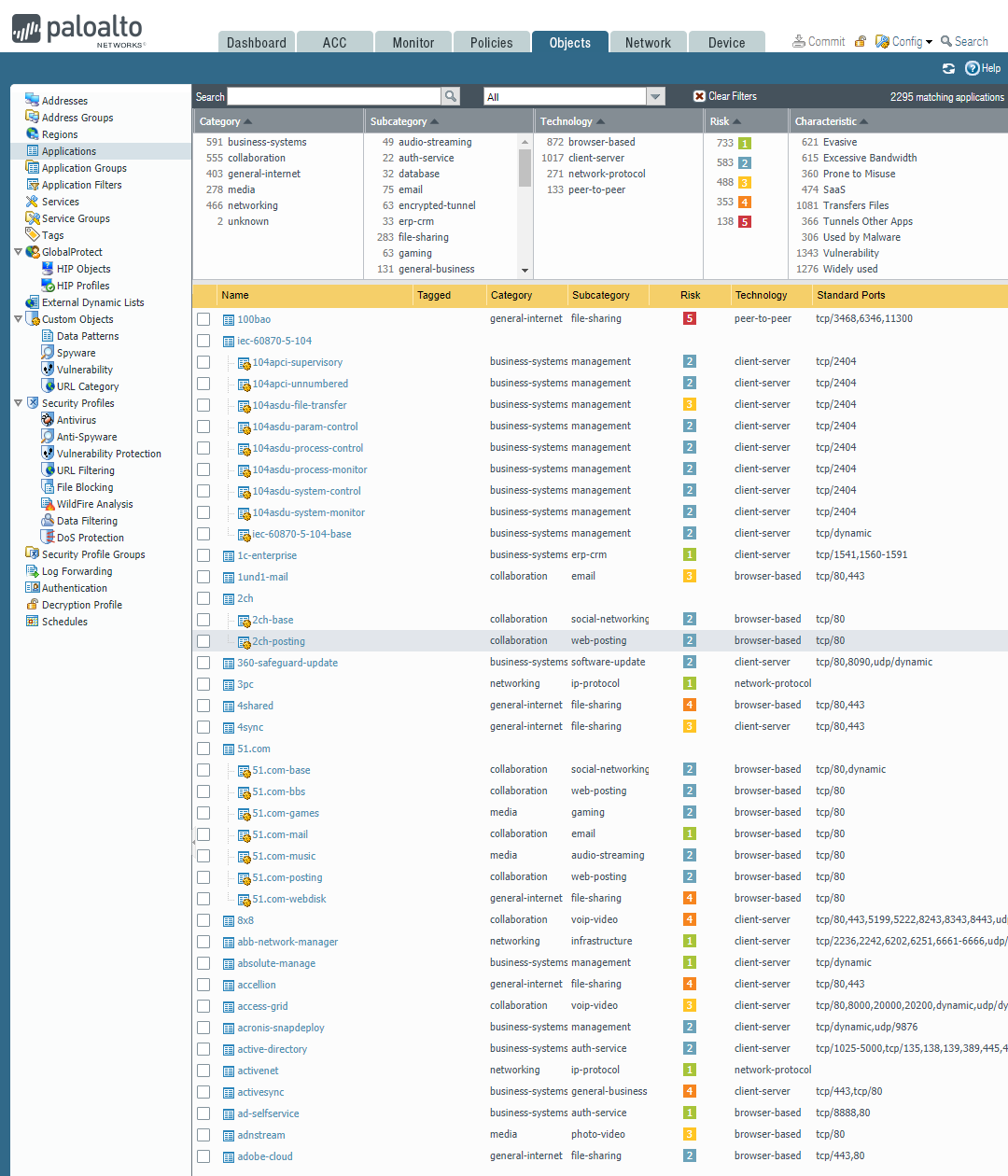
Add a new Clinical system:



Add a new application group:
Search the PAN Application Research Center before adding an application group. Identifying any required dependencies when applying application-specific rules and taking advantage of Palo Alto's application portal. https://applipedia.paloaltonetworks.com/

Then add the Youtube-Group.

Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(1)的更多相关文章
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(3)
LDAP Authentication and Remote Users and Groups Create Remote User Objects and LDAP Integration: sam ...
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(2)
Users Objects and Groups Creating local user objects. Creating local user groups. https://docs.paloa ...
- Cyber Security - Palo Alto Firewall Interface Types
Multiple options to integrate the Palo Alto Firewall into your: Network Layer 2 interfaces and VLAN ...
- Cyber Security - Palo Alto Firewall V-Wires
Leveraging V-Wires Bridge two physical connections and apply security Policies without influencing a ...
- Cyber Security - Palo Alto Firewall Security Zones
Firewall Security Zones Zones: The foundational aspect of every Firewall. Police network traffic Enf ...
- Cyber Security - Palo Alto Basic Introduction
Preparation of the Lab Environment: Download and Install Pan-OS from the following website https://d ...
- Cyber Security - Palo Alto Security Policies(1)
Security policies: Enforcing network traffic by configuring rules of what is allowed or denied to co ...
- Cyber Security - Palo Alto Security Policies(2)
Task 3 The SOC(Security Operation Center) monitoring team dashboard reported more 1,000 requests to ...
- Palo Alto GlobalProtect上的PreAuth RCE
0x00 前言 SSL VPN虽然可以保护企业资产免受互联网被攻击的风险影响,但如果SSL VPN本身容易受到攻击呢?它们暴露在互联网上,可以可靠并安全地连接到内网中.一旦SSL VPN服务器遭到入侵 ...
随机推荐
- 39 _ 队列5 _ 循环队列需要几个参数来确定 及其含义的讲解.swf
上面讲解都是循环队列,如果是链表实现的话就很简单,队列只有循环队列才比较复杂 此时队列中只存储一个有效元素3,当在删除一个元素的时候,队列为空,pFont向上移动,pFont等于pRear,但是此时p ...
- Plugns
Lombok Translation Rainbow Brackets
- 个人项目-Wc-Java
一.Github项目地址: https://github.com/Heiofungfming/xiaoming01 二.PSP表格 PSP2.1 任务内容 计划完成需要的时间(min) 实际完成需要的 ...
- shiro之redis频繁访问问题
目前安全框架shiro使用较为广泛,其功能也比较强大.为了分布式session共享,通常的做法是将session存储在redis中,实现多个节点获取同一个session.此实现可以实现session共 ...
- python+opencv检测图像清晰度
直接上代码,list_jian.txt为待检测图像路径列表 import cv2 import numpy as np import os for path in open("list_ji ...
- 【WPF】DataGrid多表头的样式设计
需求 在使用WPF开发时,使用DataGrid列表显示数据时,有些字段可以进行分组显示,用于更好的表达它们之间存在的某种关系,因此就考虑到要对DataGrid的表头进行扩展,可以显示多行表头,让这些有 ...
- express高效入门教程(5)
5.ejs模版 5.1.什么是模版引擎? 为了使用户界面与业务数据(内容)分离而产生的,它可以生成特定格式的文档,用于网站的模板引擎就会生成一个标准的HTML文档. 在后端开发中,处理数据的代码和展示 ...
- MyEclipse中项目利用不同版本JDK编译注意点
一.发现问题本地用jdk.1.6编译,可服务器上市jdk1.5,其他服务器甚至是jdk1.4,不少语法和特性不一样.该服务器的jdk版本一般不现实因为是还有许多其他项目只有将本地安装上jdk1.5. ...
- CSS选择器整理以及优先级介绍
一.基础选择器 选择器 名称 描述 兼容性 * 通配选择器 选择所有的元素 ie6+ E 元素选择器 选择指定的元素 ie6+ #idName id选择器 选择id属性等于idName的元素 ie6+ ...
- emacs-显示行号以及跳转到指定行
[显示行号]M+x display-line-number-mode <Return> [跳转行号]M+x goto-line 然后输入你想跳转到的行号 <Return> (在 ...
