Python Ethical Hacking - VULNERABILITY SCANNER(8)
Implementing Code To Discover XSS in Parameters
1. Watch the URL of the XSS reflected page carefully.
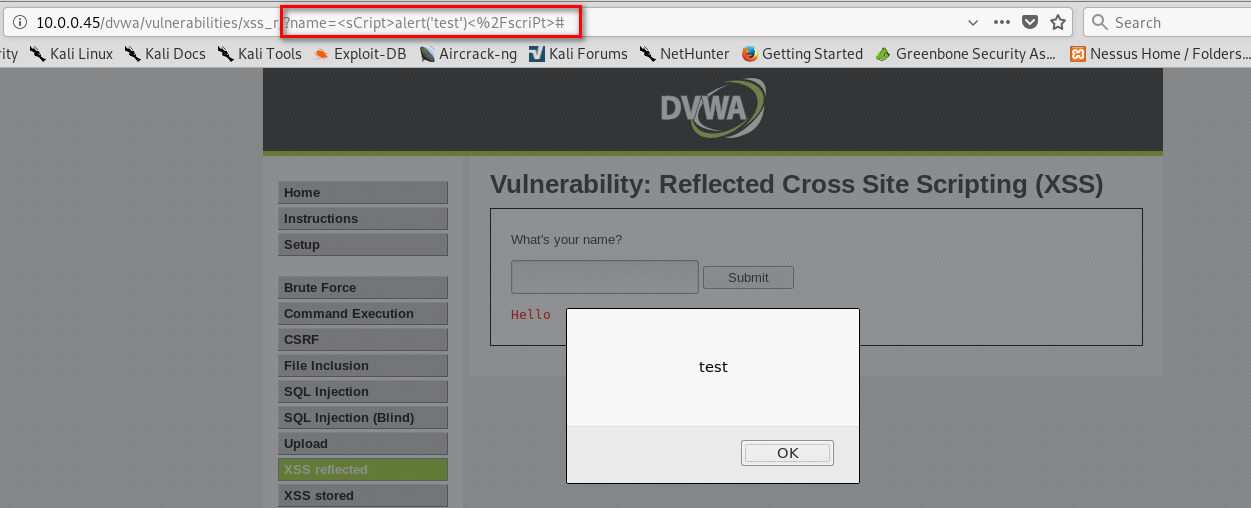
2. Add the test_xss_in_link method in the Scanner class.
#!/usr/bin/env python import requests
import re
from bs4 import BeautifulSoup
from urllib.parse import urljoin class Scanner:
def __init__(self, url, ignore_links):
self.session = requests.Session()
self.target_url = url
self.target_links = []
self.links_to_ignore = ignore_links def extract_links_from(self, url):
response = self.session.get(url)
return re.findall('(?:href=")(.*?)"', response.content.decode(errors='ignore')) def crawl(self, url=None):
if url == None:
url = self.target_url
href_links = self.extract_links_from(url)
for link in href_links:
link = urljoin(url, link) if "#" in link:
link = link.split("#")[0] if self.target_url in link and link not in self.target_links and link not in self.links_to_ignore:
self.target_links.append(link)
print(link)
self.crawl(link) def extract_forms(self, url):
response = self.session.get(url)
parsed_html = BeautifulSoup(response.content.decode(), features="lxml")
return parsed_html.findAll("form") def submit_form(self, form, value, url):
action = form.get("action")
post_url = urljoin(url, action)
method = form.get("method") inputs_list = form.findAll("input")
post_data = {}
for input in inputs_list:
input_name = input.get("name")
input_type = input.get("type")
input_value = input.get("value")
if input_type == "text":
input_value = value post_data[input_name] = input_value
if method == "post":
return requests.post(post_url, data=post_data)
return self.session.get(post_url, params=post_data) def run_scanner(self):
for link in self.target_links:
forms = self.extract_forms(link)
for form in forms:
print("[+] Testing form in " + link) if "=" in link:
print("[+] Testing " + link) def test_xss_in_link(self, url):
xss_test_script = "<sCript>alert('test')</scriPt>"
url = url.replace("=", "=" + xss_test_script)
response = self.session.get(url)
return xss_test_script in response.content.decode() def test_xss_in_form(self, form, url):
xss_test_script = "<sCript>alert('test')</scriPt>"
response = self.submit_form(form, xss_test_script, url)
return xss_test_script in response.content.decode()
3. Test this scanner.
#!/usr/bin/env python import scanner target_url = "http://10.0.0.45/dvwa/"
links_to_ignore = "http://10.0.0.45/dvwa/logout.php" data_dict = {"username": "admin", "password": "password", "Login": "submit"} vuln_scanner = scanner.Scanner(target_url, links_to_ignore)
vuln_scanner.session.post("http://10.0.0.45/dvwa/login.php", data=data_dict) # vuln_scanner.crawl()
forms = vuln_scanner.extract_forms("http://10.0.0.45/dvwa/vulnerabilities/xss_r/")
print(forms)
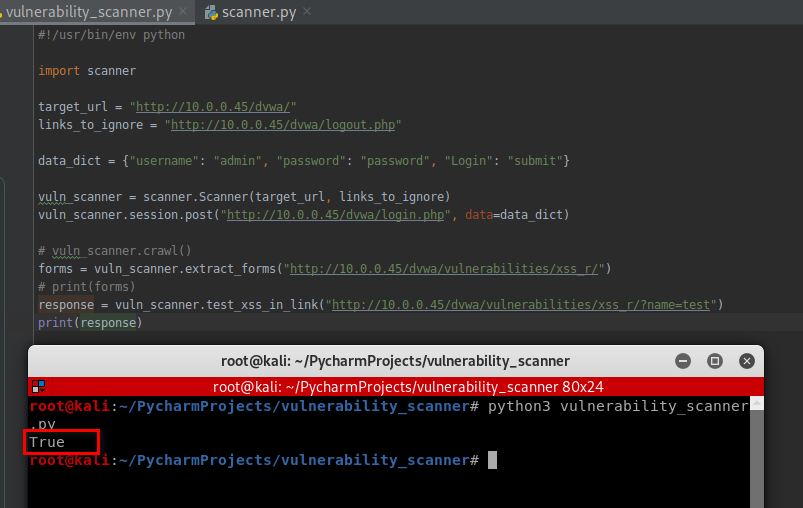
response = vuln_scanner.test_xss_in_link("http://10.0.0.45/dvwa/vulnerabilities/xss_r/?name=test")
print(response)
Test the web page - http://10.0.0.45/dvwa/vulnerabilities/xss_r/?name=test:
vuln_scanner.test_xss_in_link("http://10.0.0.45/dvwa/vulnerabilities/xss_r/?name=test")
It is vulnerable on XSS.
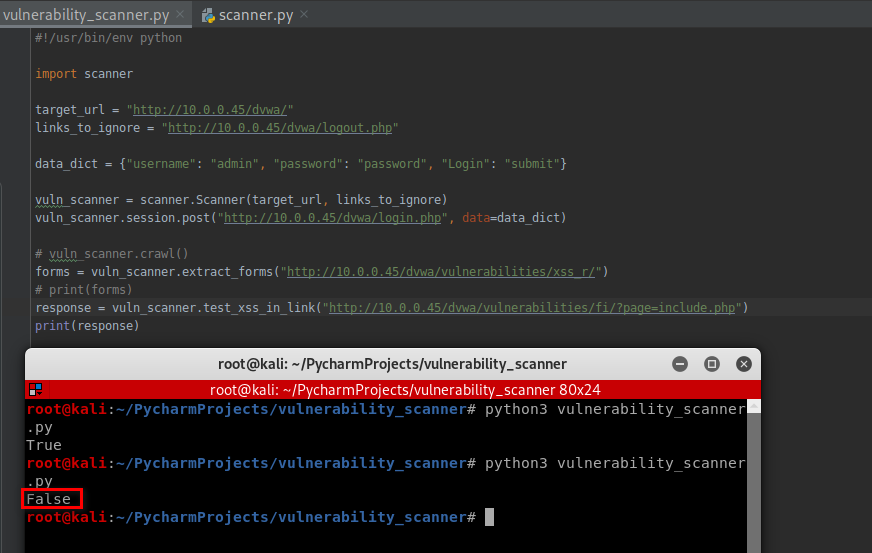
Test the web page - http://10.0.0.45/dvwa/vulnerabilities/fi/?page=include.php:
vuln_scanner.test_xss_in_link("http://10.0.0.45/dvwa/vulnerabilities/fi/?page=include.php")
It is not vulnerable on XSS.
Python Ethical Hacking - VULNERABILITY SCANNER(8)的更多相关文章
- Python Ethical Hacking - VULNERABILITY SCANNER(9)
Automatically Discovering Vulnerabilities Using the Vulnerability Scanner 1. Modify the run_scanner ...
- Python Ethical Hacking - VULNERABILITY SCANNER(7)
VULNERABILITY_SCANNER How to discover a vulnerability in a web application? 1. Go into every possibl ...
- Python Ethical Hacking - VULNERABILITY SCANNER(4)
Extracting & Submitting Forms Automatically Target website:http://10.0.0.45/dvwa/vulnerabilities ...
- Python Ethical Hacking - VULNERABILITY SCANNER(2)
VULNERABILITY_SCANNER How to discover a vulnerability in a web application? 1. Go into every possibl ...
- Python Ethical Hacking - VULNERABILITY SCANNER(3)
Polish the Python code using sending requests in a session Class Scanner. #!/usr/bin/env python impo ...
- Python Ethical Hacking - VULNERABILITY SCANNER(1)
HTTP REQUESTS BASIC INFORMATION FLOW The user clicks on a link. HTML website generates a request(cli ...
- Python Ethical Hacking - VULNERABILITY SCANNER(6)
EXPLOITATION - XSS VULNS EXPLOITING XSS Run any javascript code. Beef framework can be used to hook ...
- Python Ethical Hacking - VULNERABILITY SCANNER(5)
EXPLOITATION - XSS VULNS XSS - CROSS SITE SCRIPTING VULNS Allow an attacker to inject javascript cod ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
随机推荐
- Spark如何与深度学习框架协作,处理非结构化数据
随着大数据和AI业务的不断融合,大数据分析和处理过程中,通过深度学习技术对非结构化数据(如图片.音频.文本)进行大数据处理的业务场景越来越多.本文会介绍Spark如何与深度学习框架进行协同工作,在大数 ...
- 11、vue-路由
1.路由: 官方提供一个插件,构建单页面应用,主要实现得功能页面得切换.组件得跳转 2.vue中得路由:vue-router包,如果是脚手架进行搭建得,那么是不需要安装vue-router这个包得,因 ...
- vscode启动vue项目出错,给了管理员权限没用
今天在安装vue环境测试项目的时候, 发现vscode调用终端异常,语句无法运行,百度上给的解决方法是给管理员权限 给了以后发现没用,怎么试都没用,然后想到了,重启大法,然后问题就完美解决了
- spring boot actuator监控需要注意的点
1. /metrics接口提供的信息进行简单分类如下表: 分类 前缀 报告内容 垃圾收集器 gc.* 已经发生过的垃圾收集次数,以及垃圾收集所耗费的时间,适用于标记-清理垃圾收集器和并行垃圾收集器(数 ...
- Java 反射简介
本文部分内容参考博客.点击链接可以查看原文. 1. 反射的概念 反射是指在运行时将类的属性.构造函数和方法等元素动态地映射成一个个对象.通过这些对象我们可以动态地生成对象实例,调用类的方法和更改类的属 ...
- FastAPI 快速搭建一个REST API 服务
最近正好在看好的接口文档方便的工具, 突然看到这个, 试了一下确实挺方便 快速示例 from fastapi import FastAPI from pydantic import BaseModel ...
- day10,day11—基本数据类型语法
一.整形 1. base #在16进制中的位置 num = "b" v = int(num, base=16) print(v) #11 2. bit_length() # 1 1 ...
- 不就是语法和长难句吗—笔记总结Day3
♦5♦状语从句——结果状语从句 · so(+adj / adv)...that · such(+ n)...that ♦6♦状语从句——让步状语从句 · although · though · eve ...
- 二.httpRequest-httpResponse-JsonResponse对象
一.HttpRequest对象 HttpRequest在django.http这个模块中 它是用django创建 文档https://docs.djangoproject.com/en/1.11/r ...
- 十位大牛做出的web前端开发规范总结
Web前端作为开发团队中不可或缺的一部分,需要按照相关规定进行合理编写(一部分不良习惯可能给自己和他人造成不必要的麻烦).不同公司不同团队具有不同的规范和文档.下面是根据不同企业和团队的要求进行全面详 ...
