Ethical Hacking - Web Penetration Testing(8)
SQL INJECTION
WHAT IS SQL?
- Most websites use a database to store data.
- Most data stored in it(usernames, passwords ..etc.)
- Web application reads, updates and inserts data in the database.
- Interaction with DB done using SQL.
WHY ARE THEY SO DANGEROUS
1. They are everywhere.
2. Give access to the database –> sensitive data.
3. Can be used to read local files outside www root.
4. Can be used to log in as admin and further exploit the system.
5. Can be used to upload files.
DISCOVERING SQLi in POST
- Try to break the page.
- Using ‘and’, ‘order by’ or “’”.
- Testing text boxes and URL parameters on the form.
http://target.com/page.php?something=something
Pre-Configure about Metasplitable2:

Following is a very useful error message.
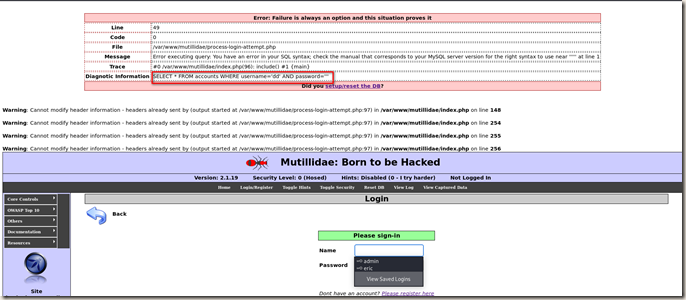
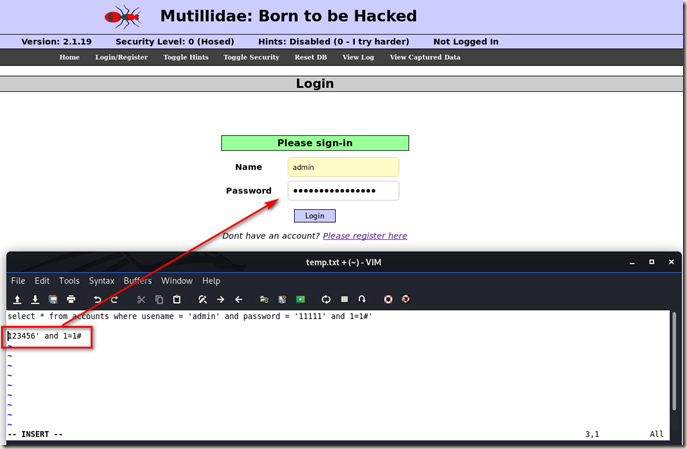
So let’s modify the input on password box. We can login with a wrong password now.
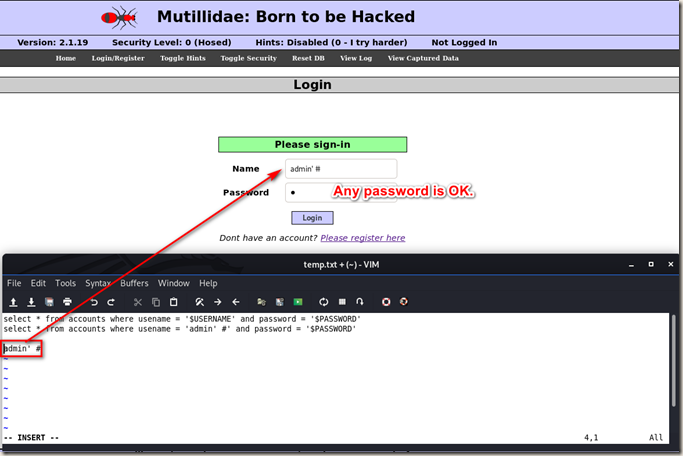
Bypassing Authentication.
Ethical Hacking - Web Penetration Testing(8)的更多相关文章
- Ethical Hacking - Web Penetration Testing(13)
OWASP ZAP(ZED ATTACK PROXY) Automatically find vulnerabilities in web applications. Free and easy to ...
- Ethical Hacking - Web Penetration Testing(10)
SQL INJECTION SQLMAP Tool designed to exploit SQL injections. Works with many DB types, MySQL, MSSQL ...
- Ethical Hacking - Web Penetration Testing(6)
REMOTE FILE INCLUSION Similar to local file inclusion. But allows an attacker to read ANY file from ...
- Ethical Hacking - Web Penetration Testing(1)
How to hack a website? An application installed on a computer. ->web application pen-testing A co ...
- Python Ethical Hacking - WEB PENETRATION TESTING(1)
WHAT IS A WEBSITE Computer with OS and some servers. Apache, MySQL ...etc. Cotains web application. ...
- Python Ethical Hacking - WEB PENETRATION TESTING(2)
CRAWING DIRECTORIES Directories/folders inside the web root. Can contain files or other directories ...
- Ethical Hacking - Web Penetration Testing(12)
XSS VULNS XSS - CROSS SITE SCRIPTING VULNS Allow an attacker to inject javascript code into the page ...
- Ethical Hacking - Web Penetration Testing(11)
SQL INJECTION Preventing SQLi Filters can be bypassed. Use a blacklist of commands? Still can be byp ...
- Ethical Hacking - Web Penetration Testing(9)
SQL INJECTION Discovering SQLi in GET Inject by browser URL. Selecting Data From Database Change the ...
随机推荐
- drf之框架基础
(一)drf基础 全称:django-rest framework 接口:什么是接口.restful接口规范(协议) CBV(基于FBV的基础上形成).CBV生命周期源码----基于restful规范 ...
- 错误 C2679二进制“没有找到接受“std::string”类型的右操作数的运算符(或没有可接受的转换
错误 C2679二进制“没有找到接受“std::string”类型的右操作数的运算符(或没有可接受的转换 严重性 代码 说明 项目 文件 行 禁止显示状态错误 C2679 二进制“<<”: ...
- vue学习第二天:Vue跑马灯效果制作
分析: 1. 给开始按钮绑定一个点击事件 2.在按钮的事件处理函数中,写相关的业务代码 3.拿到msg字符串 4.调用字符串的substring来进行字符串的截取操作 5.重新赋值利用vm实例的特性来 ...
- Mongodb 批量更新
>db.col.update({查询条件},{修改条件},{multi:true})
- 【秒懂Java】【第1章_初识Java】02_软件开发
通过上一篇文章<01_编程语言>,我们了解到 Java是众多编程语言中的其中一种 编程语言可以用来开发软件 因此,我们即将要学习的Java技术,是属于软件开发的范畴.那软件开发的前景如何呢 ...
- 4W字的后端面试知识点总结(持续更新)
点赞再看,养成习惯,微信搜索[三太子敖丙]关注这个互联网苟且偷生的工具人. 本文 GitHub https://github.com/JavaFamily 已收录,有一线大厂面试完整考点.资料以及我的 ...
- JavaScript中bool类型的转化
JavaScript 中 if() 圆括号中的表达式将被看做布尔值来处理.这时就涉及到一些转化的问题. 1.特殊值undefined和null变成false. 2.数字0和NaN变成false. 3. ...
- python中的守护线程
什么是守护线程:在后台运行,为其他线程提供服务的线程成为守护线程. 为什么要引入守护线程: thread模块不支持守护线程的概念,当主线程退出时,所有的子线程都将终止,不管它们是否仍在工作, 如果你不 ...
- python中的多任务--线程
什么是多任务? 简单地说,就是操作系统可以同时运行多个任务. 实现多任务有多种方式,线程.进程.协程. 多任务的概念:并行和并发 并发:指的是任务数多余cpu核数,通过操作系统的各种任务调度算法, 实 ...
- java语言进阶(七)_Lambda表达式
1 函数式编程思想概述 在数学中,函数就是有输入量.输出量的一套计算方案,也就是"拿什么东西做什么事情".相对而言,面向对象过分强调"必须通过对象的形式来做事情" ...
