Python Ethical Hacking - VULNERABILITY SCANNER(5)
EXPLOITATION - XSS VULNS
XSS - CROSS SITE SCRIPTING VULNS
- Allow an attacker to inject javascript code into the page.
- The code is executed when the page loads.
- The code is executed on the client machine, not the server.
Three main types:
1. Persistent/Stored XSS.
2. Reflected XSS.
3.DOM-based XSS
DISCOVERING XSS
- Try to inject javascript code into the pages.
- Test text boxes and URL parameters on the form
- http://target.com/page.php?something=something
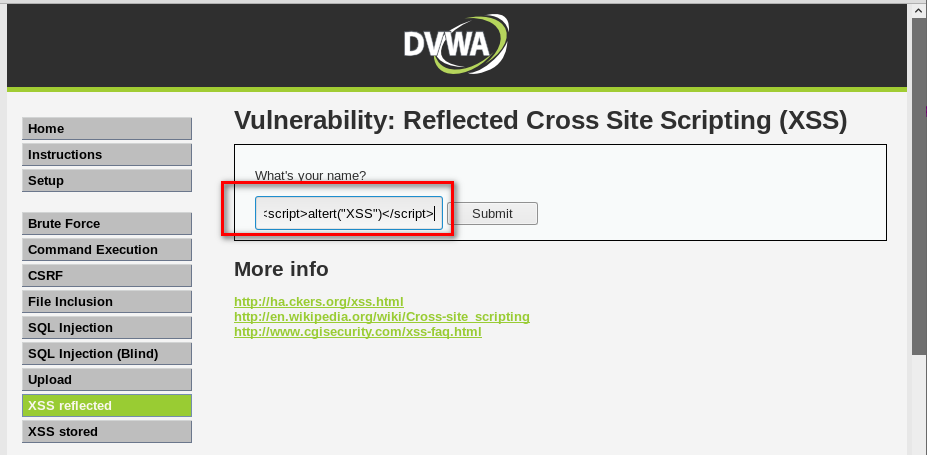
REFLECTED XSS
- None persistent, not stored.
- Only work if the target visits a specially crafted URL
- http://target.com/page.php?something=<script>altert("XSS")</script>
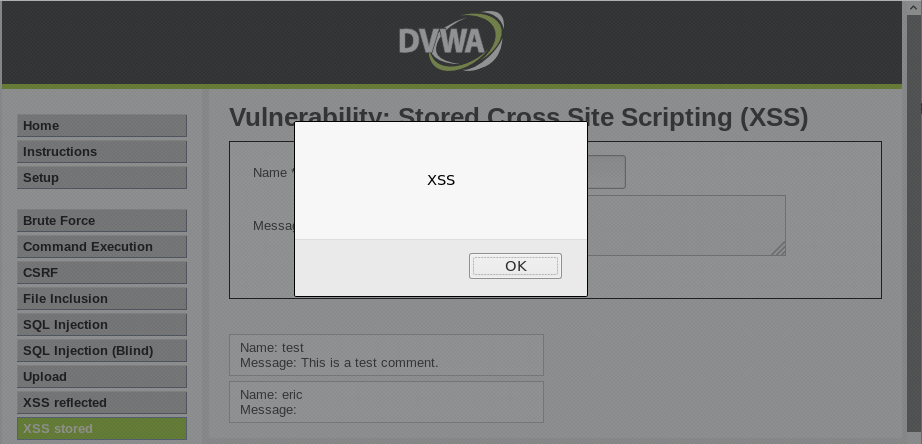
STORED XSS
- Persistent, stored on the page or DB.
- The injected code is executed every time the page is loaded.
Python Ethical Hacking - VULNERABILITY SCANNER(5)的更多相关文章
- Python Ethical Hacking - VULNERABILITY SCANNER(9)
Automatically Discovering Vulnerabilities Using the Vulnerability Scanner 1. Modify the run_scanner ...
- Python Ethical Hacking - VULNERABILITY SCANNER(7)
VULNERABILITY_SCANNER How to discover a vulnerability in a web application? 1. Go into every possibl ...
- Python Ethical Hacking - VULNERABILITY SCANNER(4)
Extracting & Submitting Forms Automatically Target website:http://10.0.0.45/dvwa/vulnerabilities ...
- Python Ethical Hacking - VULNERABILITY SCANNER(2)
VULNERABILITY_SCANNER How to discover a vulnerability in a web application? 1. Go into every possibl ...
- Python Ethical Hacking - VULNERABILITY SCANNER(8)
Implementing Code To Discover XSS in Parameters 1. Watch the URL of the XSS reflected page carefully ...
- Python Ethical Hacking - VULNERABILITY SCANNER(3)
Polish the Python code using sending requests in a session Class Scanner. #!/usr/bin/env python impo ...
- Python Ethical Hacking - VULNERABILITY SCANNER(1)
HTTP REQUESTS BASIC INFORMATION FLOW The user clicks on a link. HTML website generates a request(cli ...
- Python Ethical Hacking - VULNERABILITY SCANNER(6)
EXPLOITATION - XSS VULNS EXPLOITING XSS Run any javascript code. Beef framework can be used to hook ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
随机推荐
- Window下将nginx配置为开机自动启动
前两天看到公司window服务器上面有个nginx在跑,重启服务器后没有自动启动,需要手动运行nginx,甚是麻烦呀 上网找了一下关于将nginx配置为系统服务并且开机自动启动的解决方案,这里mark ...
- JDBC知识点总结
一:JDBC 概述 一.简介 1. JDBC(Java DataBase Connection,Java 数据库连接)是Java语言中用来规范客户端程序如何来访问数据库的应用程序 ...
- git 远程分支和tag标签的操作
git远程分支操作:1.创建远程分支git push --set-upstream origin develop:develop2在服务器创建远程分支devlop2,让本地的develop分支和dev ...
- 单元测试中使用mock最好不要使用easymock而应该使用powermock
视频参考汪文君powermock视频教程相当的经典
- android handle详解
我们来看一个简单的代码: package com.mly.panhouye.handlerdemo; import android.content.Intent; import android.os. ...
- Python3-json & pickle 序列化
JSON(JavaScript Object Notation, JS对象标记)是一中轻量级的数据交换格式,大部分语言都支持 Python3中的json提供了对json格式数据的序列化支持 json. ...
- 【转载】提高访问 github 的速度
原文地址:https://www.cnblogs.com/liuchao888/p/11733996.html 工具地址:http://tool.chinaz.com/dns?type=1&h ...
- Java笔试面试总结—try、catch、finally语句中有return 的各类情况
前言 之前在刷笔试题和面试的时候经常会遇到或者被问到 try-catch-finally 语法块的执行顺序等问题,今天就抽空整理了一下这个知识点,然后记录下来. 正文 本篇文章主要是通过举例的方式来阐 ...
- hive命令查询数据不显示表头解决办法
在hive命令行中查询数据如下: 表头未显示出来 解决办法: 修改hive安装包conf/hive-site.xml配置文件: <property> <name>hive.cl ...
- Flutter —快速开发的IDE快捷方式
老孟导读:这是老孟翻译的精品文章,文章所有权归原作者所有. 欢迎加入老孟Flutter交流群,每周翻译2-3篇付费文章,精彩不容错过. 原文地址:https://medium.com/flutter- ...
