Ethical Hacking - NETWORK PENETRATION TESTING(1)
Pre--Connection-Attacks that can be done before connecting to the network.
Gaining Access - How to break Wi-Fi keys(WEP/WPA/WPA2)
Post-Connection-Attacks can be done after connecting to the network.
Detection&Security - detect and prevent the above attacks
Sniffing Basics - MAC Address
Each network card has a physical static address assigned by the card manufacturer called MAC address(Media Access Control)
This address is used between devices to identify each other and to transfer packets to the right place.
Each packet has a source MAC and a destination MAC.
We can change your MAC address value that is stored in the memory using a program called macchanger like so:
ifconfig [INTERFACE] down
macchanger -m [MAC] [INTERFACE]
ifconfig [INTERFACE] up
[INFTERFACE] = your wifi card name
[MAC] = the mac address you want to use
Install TP-Link TL-WDN5200 Driver on Kali Linux:
1. Check system information and network setting.
root@kali:~# uname -a
Linux kali 5.2.-kali2-amd64 # SMP Debian 5.2.-2kali1 (--) x86_64 GNU/Linux
root@kali:~# cat /etc/issue
Kali GNU/Linux Rolling \n \l root@kali:~# lsusb
Bus Device : ID 0bda:c811 Realtek Semiconductor Corp. .11ac NIC
Bus Device : ID 1d6b: Linux Foundation 2.0 root hub
Bus Device : ID 0e0f: VMware, Inc. Virtual USB Hub
Bus Device : ID 0e0f: VMware, Inc. Virtual Mouse
Bus Device : ID 1d6b: Linux Foundation 1.1 root hub
root@kali:~# lsusb -t
/: Bus .Port : Dev , Class=root_hub, Driver=uhci_hcd/2p, 12M
|__ Port : Dev , If , Class=Human Interface Device, Driver=usbhid, 12M
|__ Port : Dev , If , Class=Hub, Driver=hub/7p, 12M
/: Bus .Port : Dev , Class=root_hub, Driver=ehci-pci/6p, 480M
|__ Port : Dev , If , Class=Vendor Specific Class, Driver=, 480M
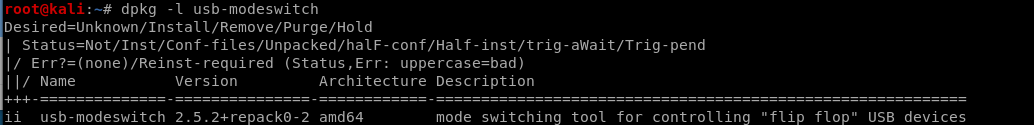
2. Check the usb-modeswitch installation status.
dpkg -l usb-modeswitch
3. Down load the driver code.
https://github.com/chenhaiq/mt7610u_wifi_sta_v3002_dpo_20130916
4.
I will continue after receive the ALFA AWUS1900 WiFi adapter.
Ethical Hacking - NETWORK PENETRATION TESTING(1)的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark WIreshark is a network protocol analyser that is designed to help network administa ...
- Ethical Hacking - NETWORK PENETRATION TESTING(14)
MITM - ARP Poisoning Theory Man In The Middle Attacks - ARP Poisoning This is one of the most danger ...
- Ethical Hacking - NETWORK PENETRATION TESTING(13)
Nmap Nmap is a network discovery tool that can be used to gather detailed information about any clie ...
- Ethical Hacking - NETWORK PENETRATION TESTING(12)
Post Connection Attacks Sophisticated attacks that can be used after connecting to the target AP. Ga ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
- Ethical Hacking - NETWORK PENETRATION TESTING(10)
WPA Craking WPA was designed to address the issues in WEP and provide better encryption. The main is ...
- Ethical Hacking - NETWORK PENETRATION TESTING(8)
WEP Cracking Basic case Run airdump-ng to log all traffic from the target network. airodump-ng --cha ...
- Ethical Hacking - NETWORK PENETRATION TESTING(7)
Gaining Access to encrypted networks Three main encryption types: 1. WEP 2.WPA 3.WPA2 WEP Cracking W ...
- Ethical Hacking - NETWORK PENETRATION TESTING(5)
Deauthentication Attacks Theory This attack is used to disconnect any device from any network within ...
随机推荐
- 嵌入式QT开发视频教程-供参考
免费嵌入式QT开发视频教程 https://pan.baidu.com/s/1bprhJ2Z QT初级到高级编程视频教程--丁林松.rarhttp://www.jisoupan.com/share/2 ...
- MongoDB快速入门教程 (4.1)
4.Mongoose使用 4.1.nodejs操作mongodb 文档地址:http://mongodb.github.io/node-mongodb-native/3.2/tutorials/cru ...
- vue基础入门(1)
1.vue初体验 1.1.vue简介 1.1.1.vue是什么? Vue (读音 /vjuː/,类似于 view) 是一套用于构建用户界面的渐进式框架,什么叫做渐进式呢?通俗的讲就是一层一层的,一步一 ...
- $.post 参数定义
//重置密码 function ResetPassword(id, accounts) { //alert("重置密码id-" + id + "-" + acc ...
- JavaScript基础有关构造函数、new关键字和this关键字(009)
1. 总是记得用new关键字来执行构造函数.前面提到,可以用构造函数创建JavaScript的对象,这个构造函数在使用的时候需要使用new关键字,但如果忘记写入new关键字,会怎么样?事实上这个函数还 ...
- windows 下搭建 MQTT 服务
1.首先搭建起MQTT服务 1.1安装mosquitto,mosquitto是开源的MQTT代理服务器,它的Windows安装包地址:https://mosquitto.org/download/ 1 ...
- 看看有哪些 Web 攻击技术.
一.前言 HTTP 协议具有无状态.不连接.尽最大努力的特点,对于 Web 网站的攻击基本也是针对 HTTP 协议的这些特点进行的.比如无状态的特点,就要求开发者需要自行设计开发"认证&qu ...
- Python 简明教程 --- 22,Python 闭包与装饰器
微信公众号:码农充电站pro 个人主页:https://codeshellme.github.io 当你选择了一种语言,意味着你还选择了一组技术.一个社区. 目录 本节我们来介绍闭包与装饰器. 闭包与 ...
- axure8.0实现tab切换
这两天帮忙做产品原型图,tab切换做一次忘一次,这次索性记录一下,免得下次再忘了. 1.在元件库中拉出来一个动态面板,双击动态面板,添加状态,添加完成之后,点击红色标注的地方,开始编辑每个面板状态: ...
- ATM + 购物车项目
''' 存放配置文件 ''' import os #获取项目根目录 BASE_PATH=os.path.dirname(os.path.dirname(__file__)) #获取用户目录 USER_ ...
