Python Ethical Hacking - TROJANS Analysis(3)
BYPASSING ANTI-VIRUS PROGRAMS
AV programs detect viruses based on:
1. Code - compare files to huge databases of signatures.
->Use own code, obfuscation, useless operations, encode, pack ...etc
2. Behaviour - run a file in a sandbox and analyze it.
-> Run trusted operations before evil code.
->Delay execution of evil code.
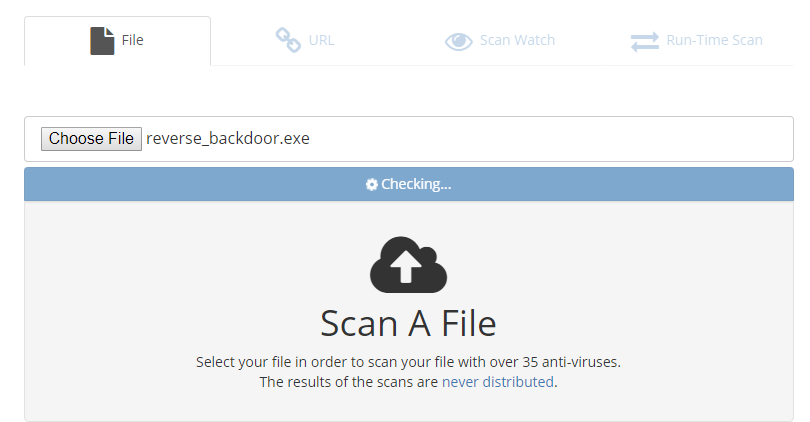
Scan the file on the following website:
NoDistribute - Online Virus Scanner Without Result Distribution
Using UPX to Package the executable program.
Download the file from https://github.com/upx/upx/releases/download/v3.95/upx-3.95-amd64_linux.tar.xz.
And extract to the /opt folder.
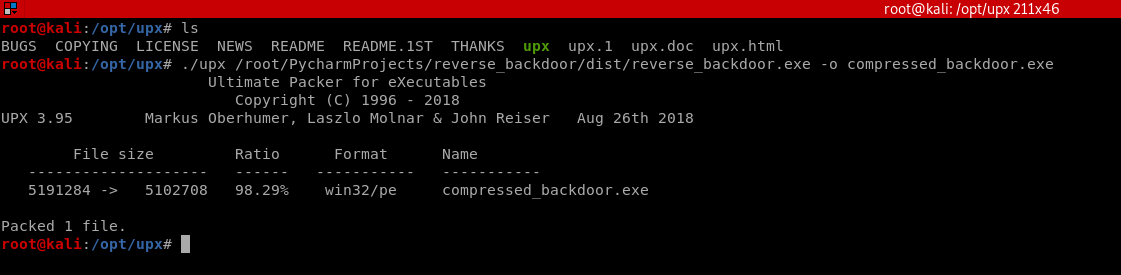
Compress the evil file through UPX.
./upx /root/PycharmProjects/reverse_backdoor/dist/reverse_backdoor.exe -o compressed_backdoor.exe
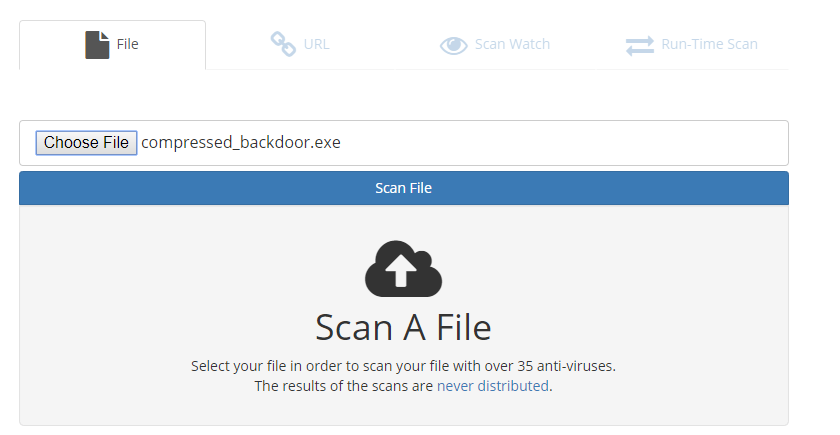
Scan the compressed_backdoor.exe file, the result is a little better.
Take your file Unique and delay to execute the evil code to let the AV program think your program is harmless.
Python Ethical Hacking - TROJANS Analysis(3)的更多相关文章
- Python Ethical Hacking - TROJANS Analysis(2)
DOWNLOAD & EXECUTE PAYLOAD A generic executable that downloads & executes files. Disadvantag ...
- Python Ethical Hacking - TROJANS Analysis(1)
TROJANS A trojan is a file that looks and functions as a normal file(image, pdf, song ..etc). When e ...
- Python Ethical Hacking - TROJANS Analysis(4)
Adding Icons to Generated Executables Prepare a proper icon file. https://www.iconfinder.com/ Conver ...
- Python Ethical Hacking - TROJANS Analysis(5)
Spoofing File Extention - A trick. Use the Kali Linux Program - Characters 1. Open the program. 2. F ...
- Python Ethical Hacking - Malware Analysis(1)
WRITING MALWARE Download file. Execute Code. Send Report. Download & Execute. Execute & Repo ...
- Python Ethical Hacking - Malware Analysis(4)
DOWNLOAD_FILE Download files on a system. Once packaged properly will work on all operating systems. ...
- Python Ethical Hacking - Malware Analysis(3)
Stealing WiFi Password Saved on a Computer #!/usr/bin/env python import smtplib import subprocess im ...
- Python Ethical Hacking - Malware Analysis(2)
Filtering Command Output using Regex #!/usr/bin/env python import smtplib import subprocess import r ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
随机推荐
- CSS中link和@import的区别
1.link属于HTML标签,而@import是CSS提供的 2.页面被加载时link会同时被加载:而@import引用的CSS会等到页面被加载完再加载 3.@import只在IE5以上才能识别,而l ...
- Windows 10 WSL 2.0安装并运行Docker
在Windows 10 2004版本,微软更新WSL到了2.0,WSL 2.0已经拥有了完整的Linux内核!今天来测试一下,是否可以安装docker! 一.开启WSL 以管理员运行Powershe ...
- Vmware的各版本KEY
算是之前收集到的备份一下在这里吧,顺便方便别人(ô‿ô) 应该是比较全的 VMware Workstation4.xx for WindowsZHDH1-UR90N-W844G-4PTN6G1NP0- ...
- PHP时间处理汇总
PHP时间处理汇总 1.求上个月的开始时间和结束时间 <?php header('Content-Type: text/html; charset=utf-8'); // 上个月的开始时间 $b ...
- Spring9——通过用Aware接口使用Spring底层组件、环境切换
通过用Aware接口使用Spring底层组件 能够供我们使用的组件,都是Aware的子接口. ApplicationContextAware:实现步骤: (1)实现Applic ...
- python+opencv实现图像缩放
x, y = img_.shape[0:2] img_ = cv2.resize(img_, (int(y/2), int(x/2))) 实现图像长宽缩小为原来的一半
- ref和out的使用及区别
1. ref的使用:使用ref进行参数的传递时,该参数在创建时,必须设置其初始值,且ref侧重于修改: 2. out的使用: 采用out参数传递时,该参数在创建时,可以不设置初始值,但是在方法中必须 ...
- 机器学习之KNN算法(分类)
KNN算法是解决分类问题的最简单的算法.同时也是最常用的算法.KNN算法也可以称作k近邻算法,是指K个最近的数据集,属于监督学习算法. 开发流程: 1.加载数据,加载成特征矩阵X与目标向量Y. 2.给 ...
- 正确卸载vs2015及以前版本方式
官网工具:https://github.com/Microsoft/VisualStudioUninstaller/releases 亲自测试过,很好用. (完)
- 12 . Kubernetes之Statefulset 和 Operator
Statefulset简介 k8s权威指南这样介绍的 "在Kubernetes系统中,Pod的管理对象RC.Deployment.DaemonSet和Job都面向无状态的服务.但现实中有很多 ...
