Ethical Hacking - NETWORK PENETRATION TESTING(6)
Creating a fake access point (honeypot)
Fake access points can be handy in many scenarios, one example is creating an open AP, this will attract a lot of clients, many of which will automatically connect to it. Then we can sniff all the traffic created by the clients that connect to it, and since its open, the traffic will not be encrypted!
In order to do this, we need two cards:
1. One connected to the Internet.
2. WiFi card to broadcast as an access point.
Clients now send requests to the hacker's wifi card, the hacker sets up his machine so that every request coming from the wifi card is forwarded to the 2nd card that's connected to the Internet.
The response comes back from the 2nd card, through the hacker's machine to the wifi card which forwards it to the client that requested it.
Tool: Mana-Toolkit
Mana-Toolkit makes the whole progress very simple, it automatically creates a new AP and starts sslstrip/firelamp and even attempts to bypass HSTS which is used by Gmail and Facebook.
Mana has 3 main start scripts:
1. Start-noupstream: starts an AP with NO internet connection.
2.Start-nat-simple: this starts a regular AP using Internet connection in the upstream interface.
3.start-nat-full: starts AP with an Internet connection, it also starts sslstrip, sslsplit, firelamp and attempts to bypass HSTS.
apt-get install mana-toolkit
gvim /etc/mana-toolkit/hostapd-mana.conf
gvim /usr/share/mana-toolkit/run-mana/start-nat-simple.sh
bash /usr/share/mana-toolkit/run-mana/start-nat-simple.sh
The first ethernet card connects to the Internet.
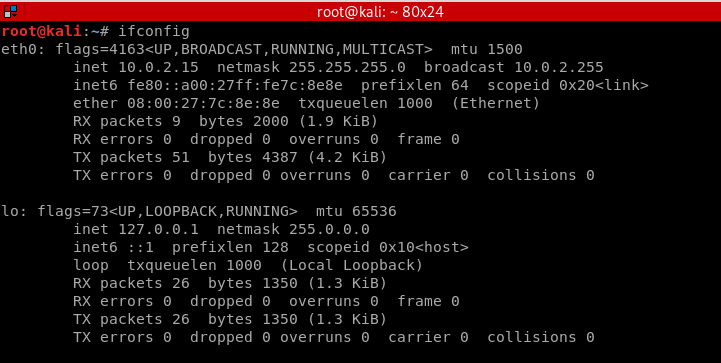
The second wifi card is ready for use.

Download and install Mana from https://github.com/sensepost/mana.
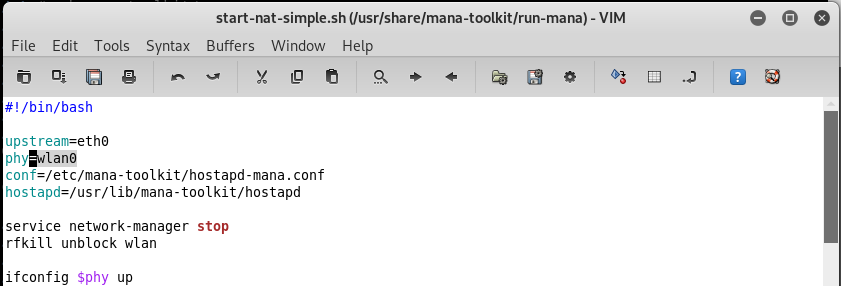
Modify the start-nat-simple.sh file.
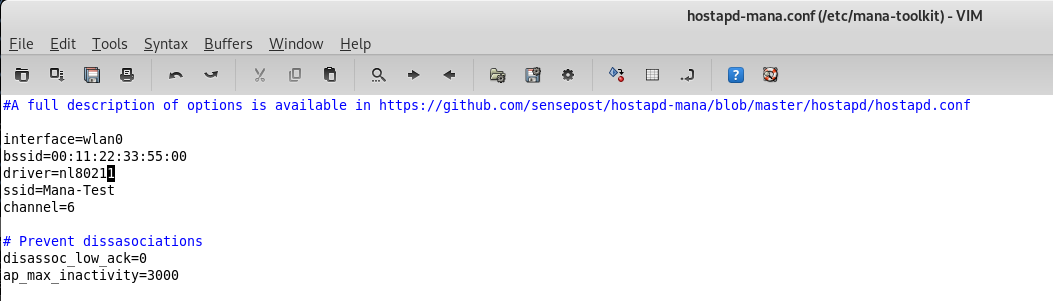
Modify the hostpad-mana.conf file.
Run mana script successfully.
bash start-nat-simple.sh
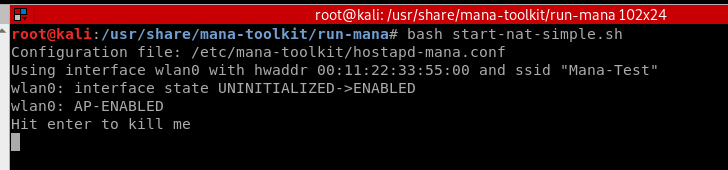
But it doesn't work well. Please see the detailed information:
https://www.slideshare.net/sensepost/improvement-in-rogue-access-points-sensepost-defcon-22
More information about hostpad setting:
https://github.com/sensepost/hostapd-mana/blob/master/hostapd/hostapd.conf
I will try Berate_ap or BetterCap later.
https://github.com/sensepost/berate_ap
https://www.bettercap.org/intro/
Ethical Hacking - NETWORK PENETRATION TESTING(6)的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark WIreshark is a network protocol analyser that is designed to help network administa ...
- Ethical Hacking - NETWORK PENETRATION TESTING(14)
MITM - ARP Poisoning Theory Man In The Middle Attacks - ARP Poisoning This is one of the most danger ...
- Ethical Hacking - NETWORK PENETRATION TESTING(13)
Nmap Nmap is a network discovery tool that can be used to gather detailed information about any clie ...
- Ethical Hacking - NETWORK PENETRATION TESTING(12)
Post Connection Attacks Sophisticated attacks that can be used after connecting to the target AP. Ga ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
- Ethical Hacking - NETWORK PENETRATION TESTING(10)
WPA Craking WPA was designed to address the issues in WEP and provide better encryption. The main is ...
- Ethical Hacking - NETWORK PENETRATION TESTING(8)
WEP Cracking Basic case Run airdump-ng to log all traffic from the target network. airodump-ng --cha ...
- Ethical Hacking - NETWORK PENETRATION TESTING(7)
Gaining Access to encrypted networks Three main encryption types: 1. WEP 2.WPA 3.WPA2 WEP Cracking W ...
- Ethical Hacking - NETWORK PENETRATION TESTING(5)
Deauthentication Attacks Theory This attack is used to disconnect any device from any network within ...
随机推荐
- Java容器相关知识点整理
结合一些文章阅读源码后整理的Java容器常见知识点.对于一些代码细节,本文不展开来讲,有兴趣可以自行阅读参考文献. 1. 思维导图 各个容器的知识点比较分散,没有在思维导图上体现,因此看上去右半部分很 ...
- 8.eclipse 安装 lombook插件
参考博客:https://www.liangzl.com/get-article-detail-129979.html
- java 加密与解密艺术二
首先需要明确的是RSA的密钥对不能手动指定,需要通过代码系统生成 接下来我们来介绍下生成密钥对 package com.weiyuan.test; import java.security.KeyPa ...
- struct2面试准备
二 工作流程1.客户端浏览器发出HTTP请求.2.根据web.xml配置,该请求被FilterDispatcher接收3.根据struts.xml配置,找到需要调用的Action类和方法, 并通过Io ...
- Spring—容器外的Bean使用依赖注入
认识AutowireCapableBeanFactory AutowireCapableBeanFactory是在BeanFactory的基础上实现对已存在实例的管理.可以使用这个接口集成其他框架,捆 ...
- MongoDB入门二
MongoDB配置 本地启动 c:\MongoDB\bin>mongod.exe --dbpath "C:\\MongoDB\data\db" --logpath " ...
- msf stagers开发不完全指北(二)
采用 Golang 开发stagers 上一篇文章 msf stagers开发不完全指北(一)中我们谈到如何采用 c 进行 msf 的 stagers 开发,这篇文章我们探讨一下如何使用 Golang ...
- 基于小程序请求接口 wx.request 封装的类 axios 请求
基于小程序请求接口 wx.request 封装的类 axios 请求 Introduction wx.request 的配置.axios 的调用方式 源码戳我 feature 支持 wx.reques ...
- JavaWeb项目在浏览器点击几次就阻塞了
问题描述 在学习JavaWeb项目时,通过IDE启动项目后,在浏览器点击几次页面中的链接就阻塞了,浏览器一直转圈圈无法加载,后台日志也没有输出. 第一次遇见这种情况,没有日志完全无法分析到底是什么问题 ...
- docker 容器与本机文件的拷贝操作
[把docker中容器时db002里面的my.cnf文件拷贝到根目录下] docker cp db002:/etc/mysql/my.cnf ~/root/ [把根目录下my.cnf文件拷贝到doc ...
